Anniversary Edition Intercepter-NG 1.0
After 10 years of development (this is exactly what hit the project), finally the Intercepter-NG version index reached 1.0 . By tradition, the release of updates for Windows occurs once a year, and the anniversary release is really a success. I would like to thank all the people who for all these years provided assistance in testing, gave a detailed feedback and ideologically inspired. We begin the review with trifles and in the end we will consider the most delicious Intercepter-NG 1.0 feature.

1. In RAW Mode, it became possible to export selected packages to a .pcap file. When Autosave is enabled, packets containing authorization data will be written in a separate .pcap.
2. In the Extra SSL Ports field, which refers to SSL MiTM, you can now drive several ports separated by commas.
3. When LDAP Relay attack on a domain controller with a language other than English can specify a desired group to add the user to peer configuration, for example, instead of Domain Admins indicate Russian analog Domain Administrators .
4. A bug has been fixed in the NTLMv2SSP hash handler, which did not allow to correctly select the password.
5.Numerous improvements in Bruteforce Mode. Added: SSL support for HTTP, UTF8 support for LDAP bruteforce, VNC, Vmware Auth Daemon and RDP protocols. RDP brute force runs on Windows 7/8/2008/2012. NLA and logins / passwords in any language are supported. RDP Security Layer is not supported.
6. The option "Inject Reverse Shell" has been added to HTTP Injections. This is a Forced Download with a backlink payload to the built-in shell interceptor.
7. Numerous improvements and changes in general. Now spoofing is disabled by default.
FATE mode combines two new features: FAke siTE and FAke updaTE.
The key goal of FAke siTE is to obtain authorization data from any web resource, bypassing SSL and other protection mechanisms. This is achieved by cloning the authorization page and creating a template that will be hosted on the built-in pseudo-web server. How it works is demonstrated in the video at the end of the post. By default, the interceptor includes one template for accounts.google.com, because the original page requires you to fill in the login field, and then with the password. This template has been slightly modified so that both fields are active at the same time. Before the attack, you must specify the domain on which the template will be hosted. After the start of the attack, a redirect to the selected domain is injected into the target’s traffic and subsequently the interceptor will automatically conduct DNS spoofing to the required addresses. As a result, the selected authorization page will open in the browser. The website cloning process is also demonstrated in the video using mail.yandex.ru as an example.
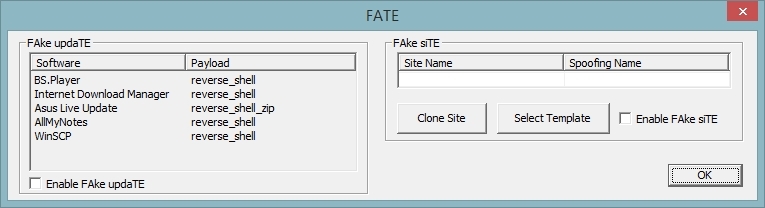
Fans of linux are familiar with a tool called Evilgrade, which allows you to exploit the automatic update mechanism and implement an arbitrary payload. In fact, this vector is greatly overestimated, firstly, the impressive list of supported applications in Evilgrade is largely outdated, and secondly, most of the most popular applications check for updates in a safe way. Nevertheless, everyone heard about loud omissions in the mechanisms for updating large vendors and this will probably happen in the future, so the analogue of Evilgrade appeared in Intercepter-NG, but the list of supported software is very modest. If desired, you can add your own templates, their structure can be found in misc \ FATE \ updates. Send software that is updated openly, we will replenish the database.
Many years ago, I really liked the network security scanner from the Chinese Xfocus team called X-Scan. Light weight, convenient design, good functionality. In the mid-2000s, he allowed me to do a lot, but in the future its development stopped and in the current realities it is of little use. For this reason, I wanted to create its modern analogue, but somehow it didn’t work out ... until recently. By old love, it was under this name that Intercepter-NG had its own network scanner, which came to replace the primitive port scanner from previous versions. So what does he know how.
1. Scan open ports and heuristically determine the following protocols: SSH, Telnet, HTTP \ Proxy, Socks4 \ 5, VNC, RDP.
2.Detect SSL on an open port, read banners and various web headers.
3. If a proxy or socks is detected, check their openness to the outside.
4. Check passwordless access to VNC servers, check SSL on HeartBleed. Read version.bind from DNS.
5. Check the database for scripts on the web server that are potentially vulnerable to ShellShock. Check the database list of directories and files for 200 OK, as well as a list of directories from robots.txt.
6. Determine the OS version via SMB. If you have anonymous access, get local time, uptime, a list of shared resources and local users. For found users, automatic password guessing starts.
7.Determine the built-in list of SSH users by measuring response time. For found users, automatic password guessing starts. If enumeration does not produce a result (it does not work on all versions), enumeration starts only for root.
8. Automatic bruteforce for HTTP Basic and Telnet. Given the features of the telnet protocol, false alarms are possible.
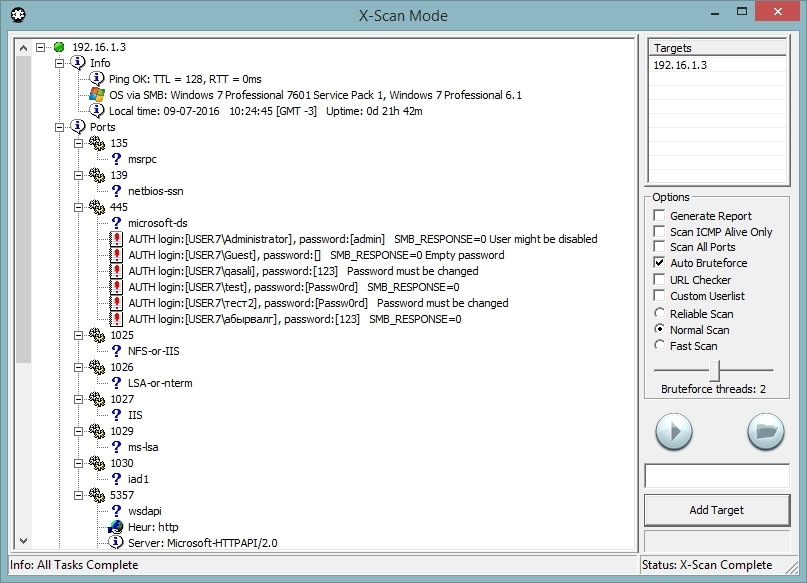
You can scan any goals, both on the local network and on the Internet. You can specify a list of ports for the scan: 192.168.1.1:80,443 or the range 192.168.1.1:100-200. You can specify the address range for the scan: 192.168.1.1-192.168.3.255.
For a more accurate result, only 3 hosts can be scanned at a time. Literally at the last moment, checks for data from SSL certificates were added, for example, if the word Ubiquiti is found and at the same time port 22 is open, then the ubnt user SSH brute force is launched. The same thing for a pair of Zyxel glands with admin. For the first release of the scanner, the functionality is enough and it is well debugged. Send your ideas and wishes.
ps: in the near future will appear the first version of the manual in Russian.

1. In RAW Mode, it became possible to export selected packages to a .pcap file. When Autosave is enabled, packets containing authorization data will be written in a separate .pcap.
2. In the Extra SSL Ports field, which refers to SSL MiTM, you can now drive several ports separated by commas.
3. When LDAP Relay attack on a domain controller with a language other than English can specify a desired group to add the user to peer configuration, for example, instead of Domain Admins indicate Russian analog Domain Administrators .
4. A bug has been fixed in the NTLMv2SSP hash handler, which did not allow to correctly select the password.
5.Numerous improvements in Bruteforce Mode. Added: SSL support for HTTP, UTF8 support for LDAP bruteforce, VNC, Vmware Auth Daemon and RDP protocols. RDP brute force runs on Windows 7/8/2008/2012. NLA and logins / passwords in any language are supported. RDP Security Layer is not supported.
6. The option "Inject Reverse Shell" has been added to HTTP Injections. This is a Forced Download with a backlink payload to the built-in shell interceptor.
7. Numerous improvements and changes in general. Now spoofing is disabled by default.
FATE
FATE mode combines two new features: FAke siTE and FAke updaTE.
The key goal of FAke siTE is to obtain authorization data from any web resource, bypassing SSL and other protection mechanisms. This is achieved by cloning the authorization page and creating a template that will be hosted on the built-in pseudo-web server. How it works is demonstrated in the video at the end of the post. By default, the interceptor includes one template for accounts.google.com, because the original page requires you to fill in the login field, and then with the password. This template has been slightly modified so that both fields are active at the same time. Before the attack, you must specify the domain on which the template will be hosted. After the start of the attack, a redirect to the selected domain is injected into the target’s traffic and subsequently the interceptor will automatically conduct DNS spoofing to the required addresses. As a result, the selected authorization page will open in the browser. The website cloning process is also demonstrated in the video using mail.yandex.ru as an example.

Fans of linux are familiar with a tool called Evilgrade, which allows you to exploit the automatic update mechanism and implement an arbitrary payload. In fact, this vector is greatly overestimated, firstly, the impressive list of supported applications in Evilgrade is largely outdated, and secondly, most of the most popular applications check for updates in a safe way. Nevertheless, everyone heard about loud omissions in the mechanisms for updating large vendors and this will probably happen in the future, so the analogue of Evilgrade appeared in Intercepter-NG, but the list of supported software is very modest. If desired, you can add your own templates, their structure can be found in misc \ FATE \ updates. Send software that is updated openly, we will replenish the database.
X-scan
Many years ago, I really liked the network security scanner from the Chinese Xfocus team called X-Scan. Light weight, convenient design, good functionality. In the mid-2000s, he allowed me to do a lot, but in the future its development stopped and in the current realities it is of little use. For this reason, I wanted to create its modern analogue, but somehow it didn’t work out ... until recently. By old love, it was under this name that Intercepter-NG had its own network scanner, which came to replace the primitive port scanner from previous versions. So what does he know how.
1. Scan open ports and heuristically determine the following protocols: SSH, Telnet, HTTP \ Proxy, Socks4 \ 5, VNC, RDP.
2.Detect SSL on an open port, read banners and various web headers.
3. If a proxy or socks is detected, check their openness to the outside.
4. Check passwordless access to VNC servers, check SSL on HeartBleed. Read version.bind from DNS.
5. Check the database for scripts on the web server that are potentially vulnerable to ShellShock. Check the database list of directories and files for 200 OK, as well as a list of directories from robots.txt.
6. Determine the OS version via SMB. If you have anonymous access, get local time, uptime, a list of shared resources and local users. For found users, automatic password guessing starts.
7.Determine the built-in list of SSH users by measuring response time. For found users, automatic password guessing starts. If enumeration does not produce a result (it does not work on all versions), enumeration starts only for root.
8. Automatic bruteforce for HTTP Basic and Telnet. Given the features of the telnet protocol, false alarms are possible.

You can scan any goals, both on the local network and on the Internet. You can specify a list of ports for the scan: 192.168.1.1:80,443 or the range 192.168.1.1:100-200. You can specify the address range for the scan: 192.168.1.1-192.168.3.255.
For a more accurate result, only 3 hosts can be scanned at a time. Literally at the last moment, checks for data from SSL certificates were added, for example, if the word Ubiquiti is found and at the same time port 22 is open, then the ubnt user SSH brute force is launched. The same thing for a pair of Zyxel glands with admin. For the first release of the scanner, the functionality is enough and it is well debugged. Send your ideas and wishes.
ps: in the near future will appear the first version of the manual in Russian.
Site: sniff.su
Mirror: github.com/intercepter-ng/mirror
Mail: intercepter.mail@gmail.com
Twitter: twitter.com/IntercepterNG
Forum: intercepterng.boards.net
Blog: intercepter-ng.blogspot.ru
