Another 0day vulnerability discovered in Adobe Flash Player

Information security researchers from Kaspersky Lab Costin Raiu and Anton Ivanov discovered a critical vulnerability in Adobe Flash Player. Vulnerable versions of the software Adobe Flash Player 21.0.0.242 and earlier versions for the platforms Windows, Mac, Linux and Chrome OS.
According to the researchers, the vulnerability they found since the spring of this year has been exploited by the StarCruft APT group of cybercriminals. Hackers continue to carry out two hacking operations - they are called Operation Daybreak and Operation Erebus. The first of them was launched in March 2016, during which a previously unknown 0day-exploit for Adobe Flash Player was used, and the target of the attack was high-ranking victims. In the second, the attackers used the exploit for the CVE-2016-4117 vulnerability, and it is likely that they would use another exploit for the CVE-2016-0147 zero-day vulnerability, the patch for which was released in April.
ScarCruft victims have been found in several countries, including Russia, Nepal, South Korea, China, India, Kuwait and Romania.
The patch for the vulnerability discovered by experts is scheduled for Thursday, June 16. At the same time, the researchers promised to provide more information about the detected security issues in Adobe Flash Player.
As a temporary measure until the patch is released, Positive Technologies experts recommend that users turn off Adobe Flash in browsers, and if necessary, use it only for trusted sites.
To prevent the effects of an attack on a Windows platform, you can use the Enhanced Mitigation Experience Toolkit (EMET).
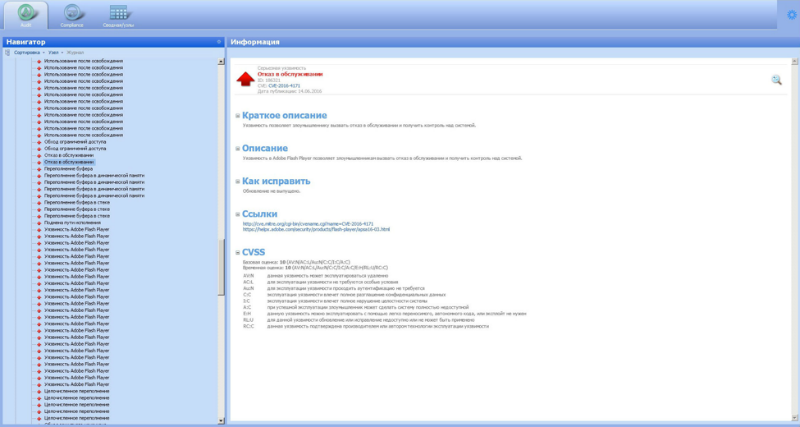
Positive Technologies experts recommend that users of corporate IT systems use specialized tools to counter complex attacks using new vulnerabilities. For example, the MaxPatrol SIEM systemalready able to detect the specified vulnerability Adobe Flash Player:
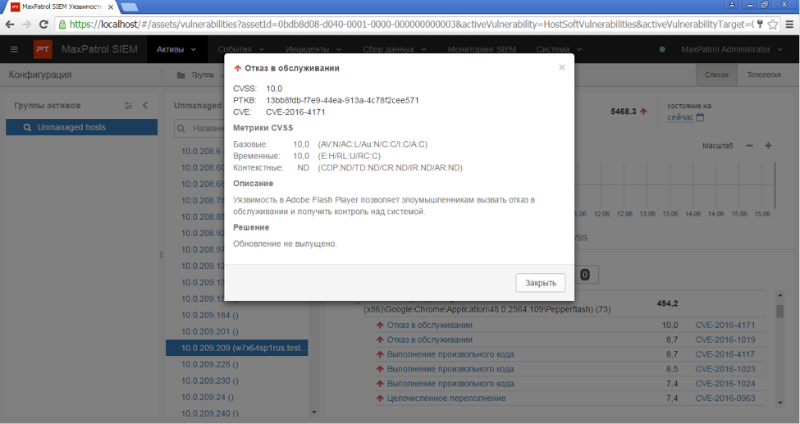
MaxPatrol SIEM uses Scanless Vulnerability Detection technology, which allows you to determine the current picture of vulnerabilities without having to re-scan. Simply update the vulnerability database.
In addition, to prevent problems associated with the exploitation of this vulnerability, you can use the MaxPatrol 8 security and compliance monitoring system .