Life without DDoS
DDoS attacks are happening more and more often - in recent years they have come first in the list of network threats for corporate clients and telecom operators. Protection from them is an urgent problem not only for every Internet business, but also for many other companies that use web resources. Typically, such attacks are designed to disable critical applications and owner resources. Today means protecting customers from such attacks is a necessary element in the arsenal of any major data center operator.
The growth of cybercrime entailed the widespread use of DDoS attacks with all the ensuing consequences. DDoS(Distributed Denial of Service) - simultaneous attack of a system from a large number of computers - usually aims to impede or make it impossible for users to access a website or Internet service. The simplicity of conducting DDoS attacks makes this method available even for an ordinary programmer who does not have much experience in such activities. And the “DDoS service” is quite inexpensive: according to Arbor Networks, an attack that can "put" a small company’s website for a week will cost about $ 150 .

How common is this phenomenon? A recent report from Arbor Networks notes that data centers and clouds have become a major target for DDoS attacks. Last year, about 70% of respondents using data center services reported having encountered DDoS attacks. At the same time, a large number of attacks with a capacity of over 100 Gbit / s were recorded. Such "events" are already too expensive for an ordinary attacker; they are usually organized by "customers", more often - for political purposes. A significant part of the recorded incidents was aimed at the failure of applications - such attacks are now regularly observed.
For the year 2014two thirds of the data center were attacked in the world. 44% of data centers suffered financial losses from DDoS attacks. At the same time, DDoS attacks reached a capacity of 400 Gb / s. Also, 29% of cloud services suffered from cybercriminals.
The difficulty in identifying cybercriminals committing DDoS attacks sometimes creates a sense of impunity. In Russia, "rousing a competitor" has become a kind of national sport. If you type “order a DDoS attack” in the search engine, you can get about a dozen links: many websites explain how to order it, how much it costs, etc. Today, resources of even large Russian companies are subjected to massive attacks. Suffice it to recall a series of DDoS attacks on the websites of leading Russian banks, including Alfa-Bank, Gazprombank, VTB, Sberbank and the Central Bank of Russia. And with the onset of the Ukrainian crisis, the number of DDoS attacks on the resources of Russian organizations has grown significantly. The need to protect information resources from DDoS attacks is no longer a private problem and becomes national in nature.
Often DDoS attacks are carried out using botnets. According to Kaspersky Lab, in Russia in the first quarter of 2015 their number increased compared to the previous similar period and amounted to almost 1,400. Russia ranked fourth in the ranking of countries whose web resources were most often targeted by the organizers of DDoS attacks. In total, in the first quarter of 2015, cybercriminals carried out more than 23 thousand DDoS attacks using botnets on resources in 76 countries. Although criminals do not limit their arsenal of DDoS attacks to botnets alone, this tool remains one of the most common and dangerous.
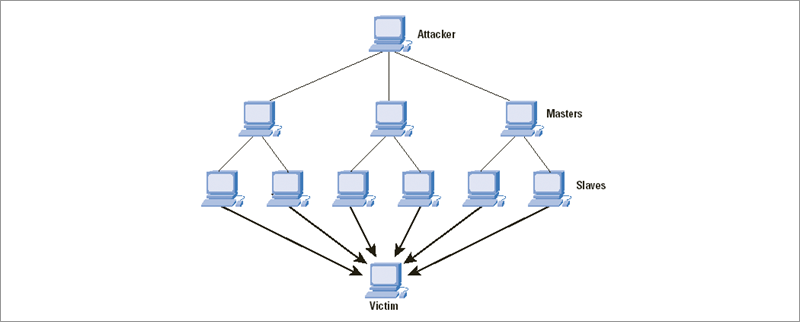
The mechanisms of suppressing information resources are used today for a variety of purposes, including political ones and as instruments of competition or blackmail. Their victims are online stores, tour operators, state enterprises, online media, social networks, financial sector companies, and providers of Internet access services. In such circumstances, preventive protection against DDoS attacks becomes mandatory. After all, the consequence of such attacks can be serious material or reputation damage - lost profits, outflow of customers, deterioration of the company's image. Therefore, countering DDoS attacks remains a hot issue for companies from the banking, telecommunications, public sectors and a number of organizations from various industries and different types of activities.
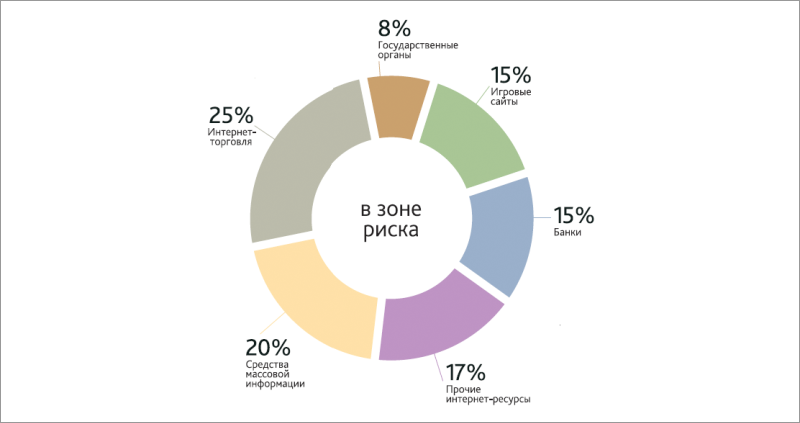
Organizations and industries most at risk of DDoS attacks (according to MFI-Soft)
DDoS attacks can be aimed at “clogging” communication channels, saturating their bandwidth, which complicates user access to a web resource. For such attacks, various types of floods are used: UDP, ICMP and other falsified packet streams. The power of attacks can be hundreds of Gbps - this can disrupt the operation of even a fairly large data center.
System resources can become the target of a DDoS attack, which leads to a decrease in its performance. For example, protocol-level attacks target hardware limitations of equipment or vulnerabilities of various protocols. Firewalls, load balancers are clogged with spurious packets, as a result of which network systems do not have time to process legitimate traffic. Or software vulnerabilities are used, which allows attackers to change the configuration and parameters of the system. Sometimes such attacks lead to the inoperability of an application or the OS as a whole. In recent years, this type of attack has become dominant.
When building a network security system, it is important to consider modern threats and especially targeted and DDoS attacks. If the data center operator does not have sufficient experience and special technical means to combat this phenomenon, a DDoS attack may cause the inaccessibility of its network devices and the IT infrastructure of its customers. The implementation of DDoS attack protection services in the data center is a guarantee of stable and reliable operation of applications and customer resources.
Since autumn 2012, the SAFEDATA company’s DDoS Protection service provides protection and reflection of various DDoS attacks based on the Perimeter software and hardware complex”From MFI-Soft, a Russian developer of solutions for protecting communication networks. “Perimeter” is a carrier-class system, one of the most high-performance solutions in the market of DDoS protection systems, and it can be extended.
The availability of web services and their uninterrupted operation is guaranteed in accordance with the SLA concluded with the client.
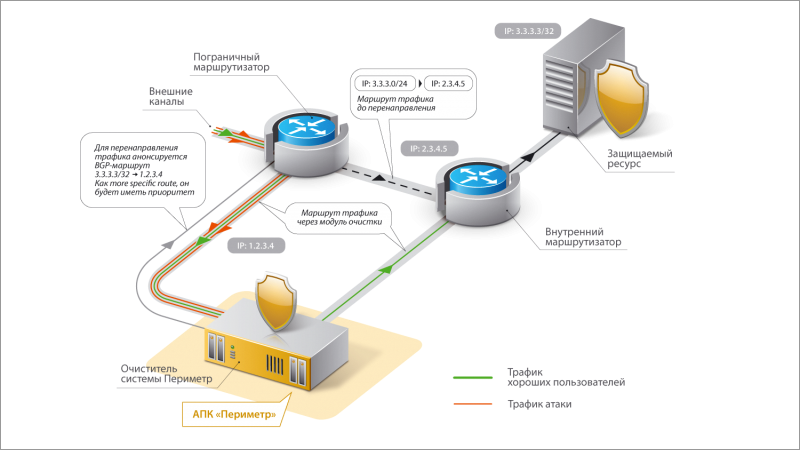
The principle of operation of the APK “Perimeter” on the border router.
The system monitors network traffic in real time, identifying malicious activity and allowing you to suppress complex DDoS attacks. After all, DDoS attacks are constantly being improved, and attackers can change the principle of impact on the attacked server during an attack.
The "perimeter" provides traffic monitoring, filtering, helps detect network attacks of various types, warns of network anomalies and suppresses them. Protected traffic is monitored for anomalies: if detected, the client is informed of a possible DDoS attack. The use of such a complex allows the telecom operator or the owner of the data center to maintain the quality of the services provided, the continuity of business processes, as well as reduce the risks of financial and reputational threats to customers.
To detect traffic anomalies, the system real-time analyzes traffic passing through routers, filters it, and high-performance traffic filtering methods are used at the TCP / IP stack level and at the application level (HTTP, DNS, SIP, etc.). To filter network traffic and suppress attacks at the application level, the system interacts with operator equipment, such as routers or firewalls.

The “Perimeter” cleans the traffic from spurious packets, without interfering with the access of legitimate users, allows for reliable protection, implements filters sufficient to repel any DDoS attacks. The complex can be used both by large projects and organizations to protect their own resources, and by Internet / hosting providers, data centers and other operators to protect customer resources. It is important that the "Perimeter" is the decision of the Russian manufacturer, therefore, there is a guarantee of confidentiality and protection of the operator’s commercial information, round-the-clock Russian-language service support. Finally, such a solution, made on the basis of domestic developments, meets the requirements of local regulators.
This article uses the materials of the company "MFI-Soft", describing the capabilities of the "Perimeter" system.
Our previous posts:
- Overview and testing of IBM FlashSystem 820 storage systems
- Personal data: dura lex, sed lex
- SAFEDATA data center: three in one. Chronicles of Migration
The growth of cybercrime entailed the widespread use of DDoS attacks with all the ensuing consequences. DDoS(Distributed Denial of Service) - simultaneous attack of a system from a large number of computers - usually aims to impede or make it impossible for users to access a website or Internet service. The simplicity of conducting DDoS attacks makes this method available even for an ordinary programmer who does not have much experience in such activities. And the “DDoS service” is quite inexpensive: according to Arbor Networks, an attack that can "put" a small company’s website for a week will cost about $ 150 .

How common is this phenomenon? A recent report from Arbor Networks notes that data centers and clouds have become a major target for DDoS attacks. Last year, about 70% of respondents using data center services reported having encountered DDoS attacks. At the same time, a large number of attacks with a capacity of over 100 Gbit / s were recorded. Such "events" are already too expensive for an ordinary attacker; they are usually organized by "customers", more often - for political purposes. A significant part of the recorded incidents was aimed at the failure of applications - such attacks are now regularly observed.
For the year 2014two thirds of the data center were attacked in the world. 44% of data centers suffered financial losses from DDoS attacks. At the same time, DDoS attacks reached a capacity of 400 Gb / s. Also, 29% of cloud services suffered from cybercriminals.
DDoS in Russia
The difficulty in identifying cybercriminals committing DDoS attacks sometimes creates a sense of impunity. In Russia, "rousing a competitor" has become a kind of national sport. If you type “order a DDoS attack” in the search engine, you can get about a dozen links: many websites explain how to order it, how much it costs, etc. Today, resources of even large Russian companies are subjected to massive attacks. Suffice it to recall a series of DDoS attacks on the websites of leading Russian banks, including Alfa-Bank, Gazprombank, VTB, Sberbank and the Central Bank of Russia. And with the onset of the Ukrainian crisis, the number of DDoS attacks on the resources of Russian organizations has grown significantly. The need to protect information resources from DDoS attacks is no longer a private problem and becomes national in nature.
Often DDoS attacks are carried out using botnets. According to Kaspersky Lab, in Russia in the first quarter of 2015 their number increased compared to the previous similar period and amounted to almost 1,400. Russia ranked fourth in the ranking of countries whose web resources were most often targeted by the organizers of DDoS attacks. In total, in the first quarter of 2015, cybercriminals carried out more than 23 thousand DDoS attacks using botnets on resources in 76 countries. Although criminals do not limit their arsenal of DDoS attacks to botnets alone, this tool remains one of the most common and dangerous.

The mechanisms of suppressing information resources are used today for a variety of purposes, including political ones and as instruments of competition or blackmail. Their victims are online stores, tour operators, state enterprises, online media, social networks, financial sector companies, and providers of Internet access services. In such circumstances, preventive protection against DDoS attacks becomes mandatory. After all, the consequence of such attacks can be serious material or reputation damage - lost profits, outflow of customers, deterioration of the company's image. Therefore, countering DDoS attacks remains a hot issue for companies from the banking, telecommunications, public sectors and a number of organizations from various industries and different types of activities.

Organizations and industries most at risk of DDoS attacks (according to MFI-Soft)
Data Center Protection - Customer Peace of Mind
DDoS attacks can be aimed at “clogging” communication channels, saturating their bandwidth, which complicates user access to a web resource. For such attacks, various types of floods are used: UDP, ICMP and other falsified packet streams. The power of attacks can be hundreds of Gbps - this can disrupt the operation of even a fairly large data center.
System resources can become the target of a DDoS attack, which leads to a decrease in its performance. For example, protocol-level attacks target hardware limitations of equipment or vulnerabilities of various protocols. Firewalls, load balancers are clogged with spurious packets, as a result of which network systems do not have time to process legitimate traffic. Or software vulnerabilities are used, which allows attackers to change the configuration and parameters of the system. Sometimes such attacks lead to the inoperability of an application or the OS as a whole. In recent years, this type of attack has become dominant.
When building a network security system, it is important to consider modern threats and especially targeted and DDoS attacks. If the data center operator does not have sufficient experience and special technical means to combat this phenomenon, a DDoS attack may cause the inaccessibility of its network devices and the IT infrastructure of its customers. The implementation of DDoS attack protection services in the data center is a guarantee of stable and reliable operation of applications and customer resources.
Since autumn 2012, the SAFEDATA company’s DDoS Protection service provides protection and reflection of various DDoS attacks based on the Perimeter software and hardware complex”From MFI-Soft, a Russian developer of solutions for protecting communication networks. “Perimeter” is a carrier-class system, one of the most high-performance solutions in the market of DDoS protection systems, and it can be extended.
The availability of web services and their uninterrupted operation is guaranteed in accordance with the SLA concluded with the client.
How it works?

The principle of operation of the APK “Perimeter” on the border router.
The system monitors network traffic in real time, identifying malicious activity and allowing you to suppress complex DDoS attacks. After all, DDoS attacks are constantly being improved, and attackers can change the principle of impact on the attacked server during an attack.
The "perimeter" provides traffic monitoring, filtering, helps detect network attacks of various types, warns of network anomalies and suppresses them. Protected traffic is monitored for anomalies: if detected, the client is informed of a possible DDoS attack. The use of such a complex allows the telecom operator or the owner of the data center to maintain the quality of the services provided, the continuity of business processes, as well as reduce the risks of financial and reputational threats to customers.
To detect traffic anomalies, the system real-time analyzes traffic passing through routers, filters it, and high-performance traffic filtering methods are used at the TCP / IP stack level and at the application level (HTTP, DNS, SIP, etc.). To filter network traffic and suppress attacks at the application level, the system interacts with operator equipment, such as routers or firewalls.

The “Perimeter” cleans the traffic from spurious packets, without interfering with the access of legitimate users, allows for reliable protection, implements filters sufficient to repel any DDoS attacks. The complex can be used both by large projects and organizations to protect their own resources, and by Internet / hosting providers, data centers and other operators to protect customer resources. It is important that the "Perimeter" is the decision of the Russian manufacturer, therefore, there is a guarantee of confidentiality and protection of the operator’s commercial information, round-the-clock Russian-language service support. Finally, such a solution, made on the basis of domestic developments, meets the requirements of local regulators.
This article uses the materials of the company "MFI-Soft", describing the capabilities of the "Perimeter" system.
Our previous posts:
- Overview and testing of IBM FlashSystem 820 storage systems
- Personal data: dura lex, sed lex
- SAFEDATA data center: three in one. Chronicles of Migration
