How to improve network perimeter protection? Practical recommendations for Check Point and not only
- Tutorial

We continue the series of articles on the optimization of security settings for network perimeter protection (NGFW). I want to immediately note that these recommendations are suitable not only for Check Point owners. In fact, if you look at the threats are the same for everyone, it’s just that each NGFW vendor decides (or does not solve) in his own way. Before that, we published a mini course “ Check Point to Maximum ”, where we showed how dangerous the default settings are. These were general recommendations. Now we wanted to describe more specific steps for the possible strengthening of perimeter protection. This article is only advisory in nature! Do not blindly follow this instruction without first analyzing the possible consequences for your network!
Trends in cyber attacks
Before making recommendations, it is necessary to understand, and what threatens us? From what to defend? To do this, I suggest using the Check Point report for 2018 (CYBER ATTACK TRENDS ANALYSIS). Naturally there is a lot of marketing, but there is also very useful information. For example, statistics on the types of virus files that were received via the Web (http / https) and Email (smtp):
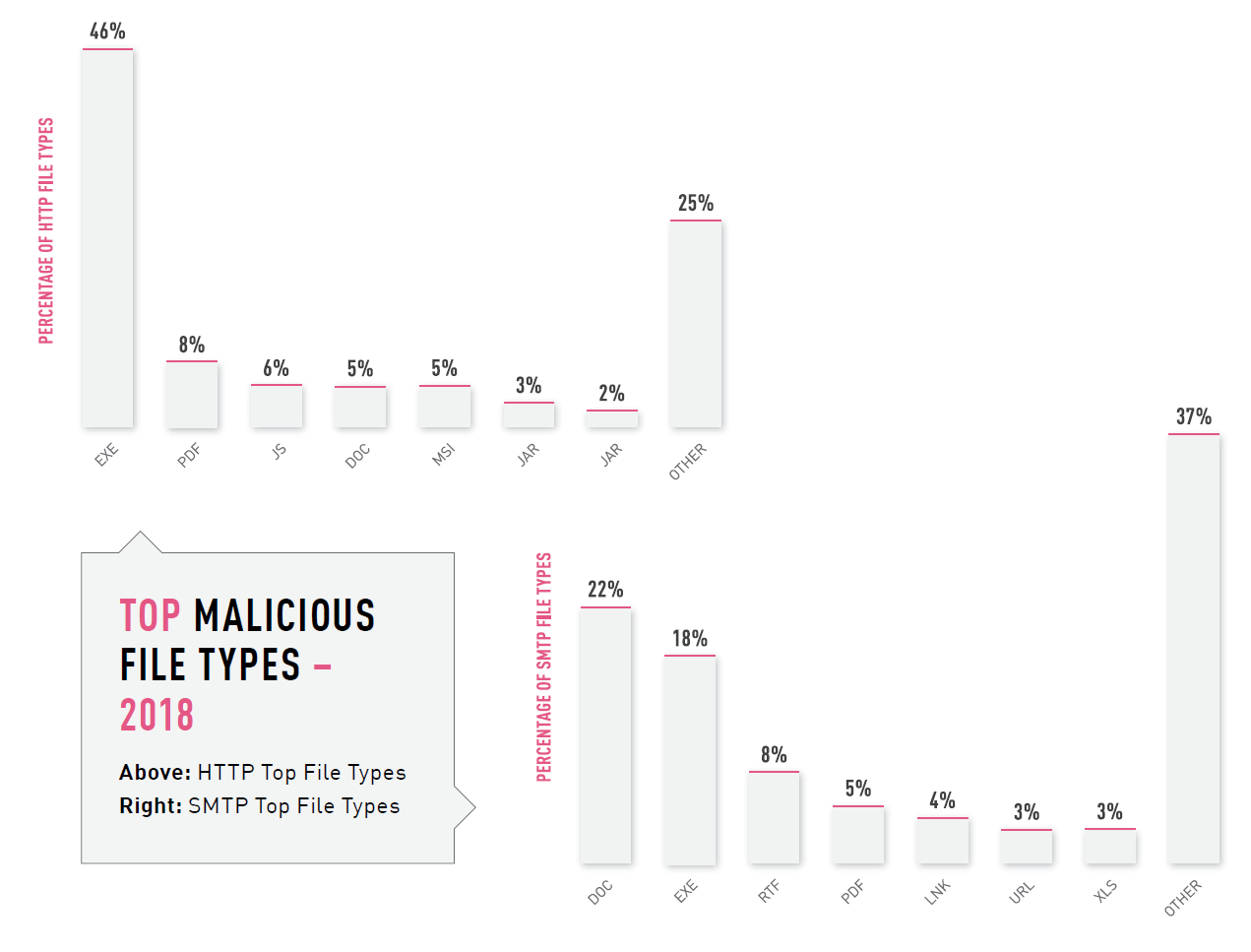
From this picture you can get very important information. Web and Email are still two main attack vectors. And if you look at the statistics, you can see that SMTP prevailed in the first half of the year, and HTTP dominated in the second half of the year.
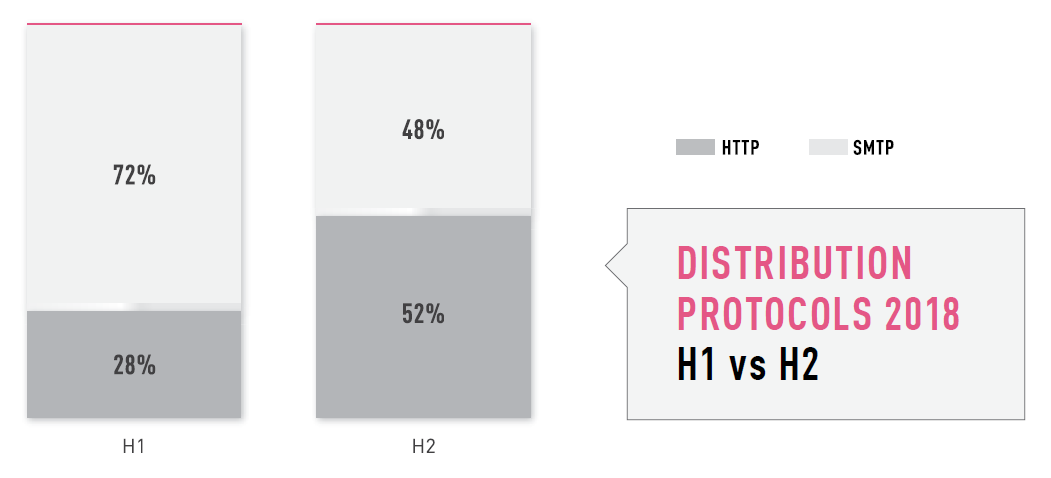
Let's see how we can increase the protection for each attack vector (i.e., Web and Email).
Immediately make a reservation that these measures will certainly not be enough to provide comprehensive protection. However, according to statistics, we can significantly improve the security of our network .
Enhancing protection against malicious Web traffic.
Back in the course “ Check Point for Maximum ”, I showed a few tricks to improve security for Web traffic. The most important points:
- Enable HTTPS inspection ;
- Use Content Awareness Blade ;
- Enable Deep scan in the Anti-Virus settings ;
- Use IPS to check files .
However, most of the recommendations were of a general nature. Now we have information about the most relevant threats. Let's try to apply our knowledge in practice.
1) Content Blocking (Content Awareness)
As we saw from the image above, the .exe format is most often found among the virus files that users receive via the Web. Already 46% ! Do these files need your users? In Lesson 2 “Check Point for Maximum” I already showed how to use the Content Awareness blade. If you still had doubts about this blocking, then take another look at the statistics. Having blocked this type of files you “simplify” the life of your NGFW by 46% (in terms of checking files). You just need to add one rule:
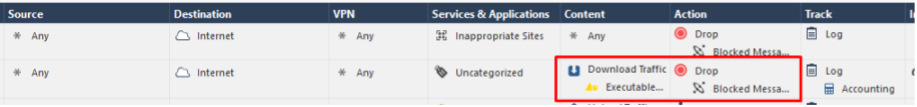
Why check for what you obviously do not need and hope that your antivirus or sandbox will not fail?
If you use another solution (not Check Point), then perhaps there is no such functionality as Content Awareness, however, you will probably be able to block various types of files using antivirus. This is a more resource-intensive way, but it's better than nothing.
With the rest of the file types is not so simple. Doc and Pdf are most likely needed by the majority and it is not possible to block them. The same applies to the rest of the files (JS, Jar), if you block them, then there will be problems with the display of web pages. The only way out in this case is to check them VERY carefully.
2) Turn on Deep Scan for the most dangerous file types.
In the 4th lesson “Check Point for maximum” I showed that with the default settings the Anti-Virus shows very bad results. And this is absolutely true for all vendors. Almost everyone has the option of “quick” check and more “deep”. By default, of course, “fast” is used, for the purpose of optimization. For Check Point, the “deep” scan option is called " deep scan " and it can be enabled for different file types. The first thing that comes to mind is to enable it for all file types (currently there are about 90 file types). And so it can be done! If you have a very rich company. It takes a very powerful iron for this option. You can find a compromise - enable deep scan for the most dangerous files:
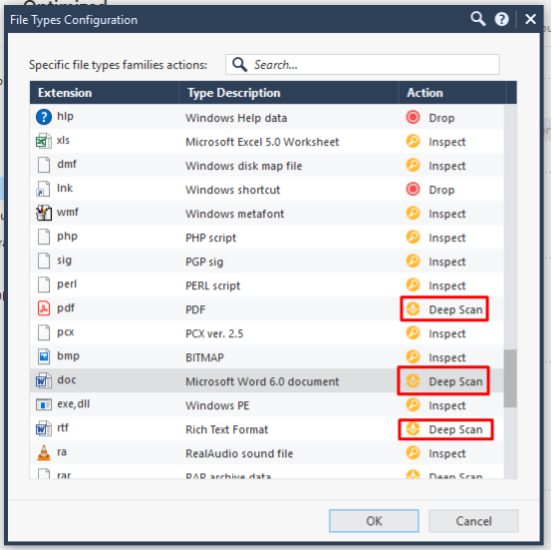
From the statistics we have the following files:pdf, doc, javascript, jar . But I would add at least: xls, zip, rar, 7zip, rtf, swf . And of course, you need to block password-protected archives.
If you do not have Check Point, then check the possibility of using such options. It is very important.
3) Include the necessary IPS signatures
Again, going back to the “Check Point to Maximum” course, in Lesson 6, I showed the importance of IPS for checking files. IPS can find exploits in documents! The biggest torment with IPS is choosing the signatures you need. In the same place, I showed a few tricks to work with them (or more precisely, with categories). But now we have additional information. We definitely need signatures associated with such files as pdf, doc, javascript and jar . It is quite simple to do this; it is enough to use the search by signatures:
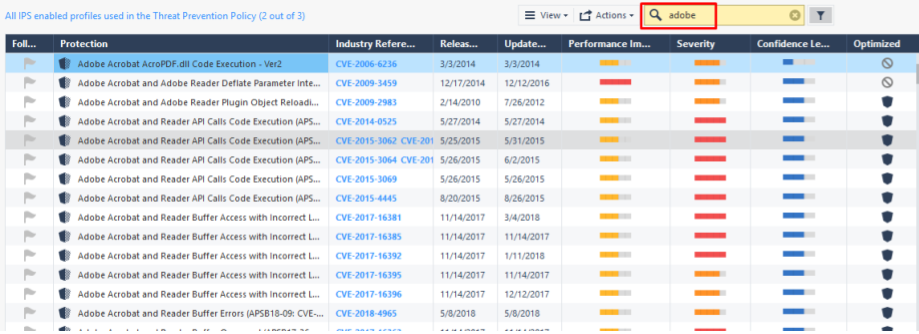
(In the case of pdf, do not forget that there may be other viewers, for example Foxit).
Or again, using categories in filters:
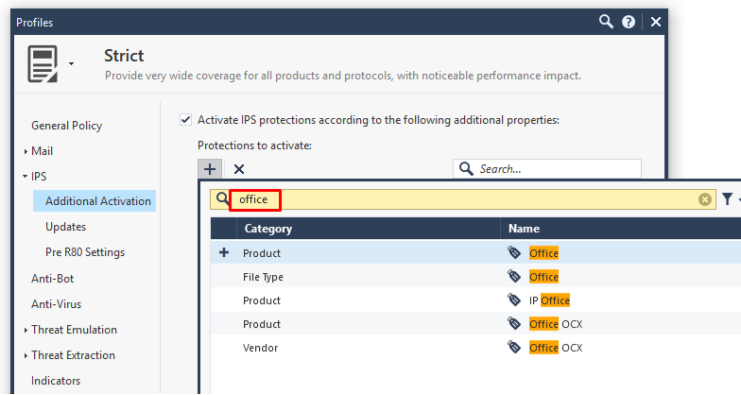
Now we will scan incoming files not only with the help of Anti-Virus, but also with the help of IPS.
If you are not using Check Point, then try also to include relevant signatures (all that concerns office documents, archives, javascript and jar).
4) Threat Emulation and Threat Extraction
Antivirus and IPS are good, but this is a signature analysis, the main drawback of which is that it works only with known threats. What to do with the unknown (0-day)? For this and come up with a "sandbox". At Check Point, this technology is called SandBlast and is implemented using such blades as:
Threat Emulation - file emulation. Currently more than 65 file types are supported. Be sure to enable emulation for the above voiced list ( pdf, doc, javascript and jar ) plus my recommendations ( xls, zip, rar, 7zip, rtf, swf ):
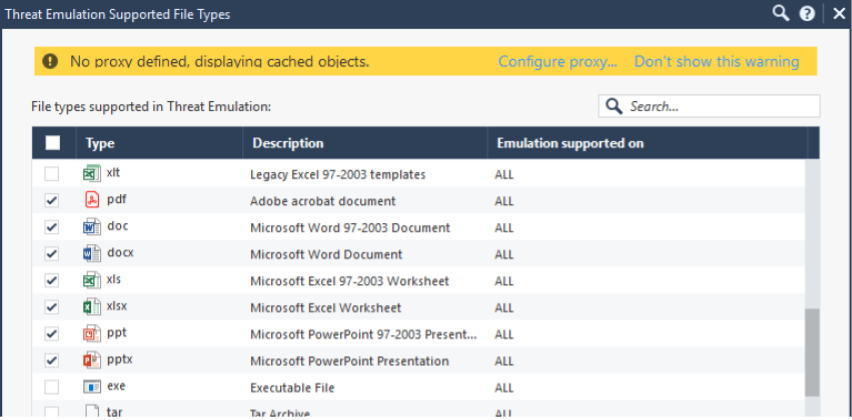
Threat Emulation will allow you to check the files before they are downloaded. This is a very important feature, because not every solution can work in the Prevent mode for web traffic.
Threat extraction- clear active content. Cleaning can be performed by converting a file to pdf, or by “cutting out” all active content (scripts, macros, url, etc.). Currently, Threat Extraction supports about 45 types of files. And the advantages of using this blade, I told in 3 parts of the course Check Point SandBlast . Look, there is a demonstration of work. It is highly advisable to use Threat Extraction for cleaning pdf and doc. And the best way is to choose the “conversion to pdf”, this is the “100 pood” method. With xls, it doesn't always roll, because the document may be badly affected, so use a customized policy for Threat Extraction.
Unfortunately, currently, Threat Extraction for Web traffic only works when using a special browser extension -SandBlast Agent for Browsers . However, in the next release ( Gaia R80.30 ), it will be possible to clean and convert files, even without additional extensions.
If you are not using Check Point, then I also recommend trying out the sandbox functionality. Almost all vendors have a trial mode. I'm pretty sure that after switching on your “catch rate” will increase significantly.
We strengthen the protection against malicious email
With web traffic more or less sorted out (although in fact everything is more complicated). Now let's move on to another popular attack vector, Email. In almost all companies, mail protection receives the most attention. Let's see what we can do with NGFW solutions at the perimeter of the network.
1) MTA mode
The first thing you need to do is switch the Check Point Gateway to MTA (Mail Transfer Agent) mode. This will allow for a more comprehensive scan of email messages, especially if you use SMTPS (in this case, without the MTA function, your gateway will simply not be able to check for this traffic).
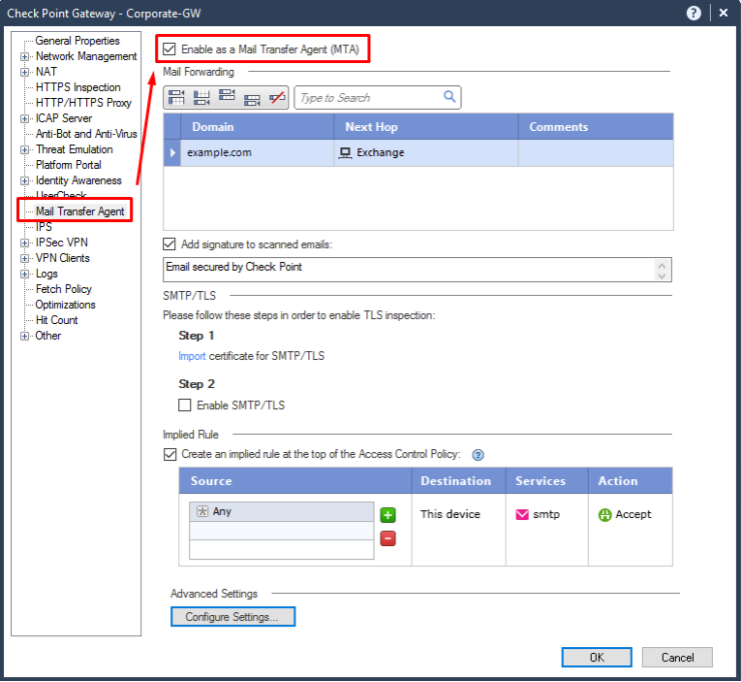
If you are not using Check Point and your NGFW does not support MTA, then read the article further - there is no point. You simply will not be able to perform additional checks. Most likely in this case, you use a separate solution to protect mail.
2) Upgrade to R80.20
This is another important point. In the release of the Gaia R80.20, the MTA functionality (and not only) has undergone significant changes. This also applies to mailing reporting. By default, several new dashboards are available at once:
You no longer have to go into the command line to monitor and trashlshuting. In addition, since version R80.20, the MTA functionality has been moved to a separate tab in the Threat Prevention profile settings:
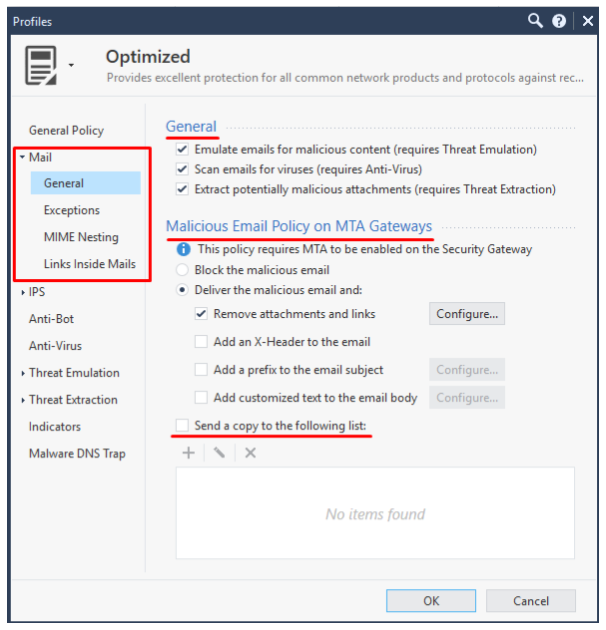
The most important points:
- Now mail attachments can be checked not only by the sandbox (in MTA mode). At first, the files and links in the email will be scanned by the antivirus engine. This is very beneficial in terms of device performance, because if the file is a known malware, it will be dropped, without being sent to the sandbox.
- Now all blocked emails can be sent to a dedicated email and thus organize some sort of quarantine. This is useful in case you need access to a blocked email.
As far as I know, currently, a dedicated team has been formed at Check Point that deals exclusively with MTA functionality. So, additional improvements are just around the corner (R80.30 is already in the EA program).
3. Make a separate Threat Prevention rule for MTA
Another important point. There should be different profiles for web traffic and email. The rule should look like this:
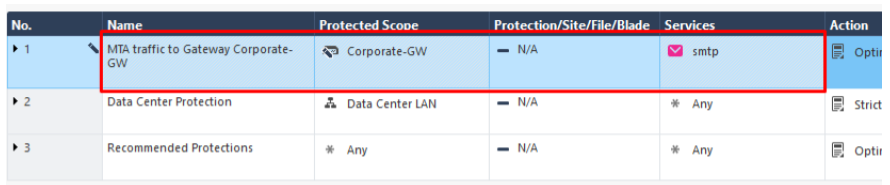
If you use R80.20, this rule is created automatically when you turn on the MTA.
4. Email Antivirus
As mentioned above, at 80.20 we have the opportunity to use the anti-virus “engine” to check attachments and hyperlinks. It perfectly correlates with our needs. If you look at the statistics at the very beginning, you can see that in addition to classic documents, exe files and url pose a threat .
First of all, you need to block absolutely all unnecessary types of files that can be sent as attachments (not only exe). Easier to say what to leave: pdf, doc, xls, ppt. zip, rar, 7zip and other popular office file formats. But various scripts, Linux archives, executable files should be blocked.
Also do not forget about checking the url in the content of the letter:
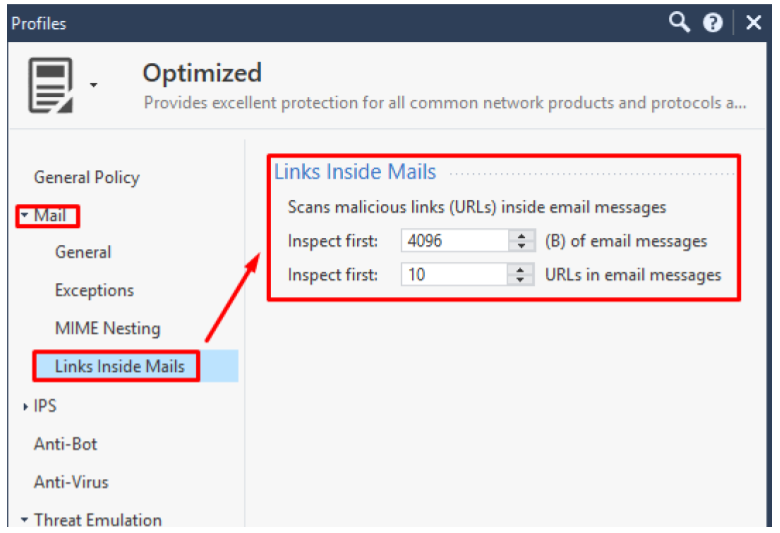
For all types of files that we allow, of course, you need to configure a deep scan.
5. Threat Emulation и Threat Extraction
Mail is the main vector for targeted attacks, i.e. attacks, which are prepared. Most often it is in such attacks that the zero-day (0-day) vulnerabilities are used. And here the signature analysis is powerless. Therefore, if you decide to use a sandboxed solution, then email is the first place to use it. For all allowed (in antivirus) files, we must use the sandbox functionality. This concerns not only Check Point solutions.
In terms of setting Threat Emulation for Email, everything is identical, as for the Web. Just make sure that you enable emulation for all files that are allowed (by antivirus). Again, if you look at our statistics, the most dangerous file types are doc, pdf, rtf, xls.
Also, be sure to use Threat Extraction to clear active content.
In this case, for documents such as pdf and doc, be sure to configure the conversion to pdf. In this case, you do not have to rely on Threat Emulation. Moreover, with a positive verdict, the user will be able to download the original file (in 95% of cases no one needs the original).
General recommendations
The main principle of network perimeter protection is to minimize the attack area. For this we have a large set of mechanisms:
- Restrict allowed ports to the firewall level;
- Restrict the applications used in the corporate network;
- Restrict access to malicious resources;
- Disallow unwanted content type (executable files, etc.);
- Enable SSL inspection to see the whole picture.
Without these steps, all other actions are useless. Having reduced the attack area, we should make maximum use of signature analysis methods, such as:
- Antivirus;
- IPS;
- Anti-Bot,
- Anti-Spam.
And after that we can move on to heavier tools, such as a sandbox:
- Threat Emulation;
- Threat Extraction.
Such a consistent approach will significantly enhance network perimeter protection. The approach is universal and relevant for almost all NGFW solutions.
Additional materials
If you are interested in this topic, then at least the following resources are recommended:
- Check Point to maximum
- Check Point Security Check List
- Protection against targeted (0-day) attacks using Check Point SandBlast ( part 1 , part 2 , part 3 )
Soon we plan to launch a small course, with a demonstration of all this functionality. So stay tuned! ( vk , telegram ).
