Comparison of desktop encryption software
Most recently, we conducted a comparison of mobile (for Android) encryption applications. It is time for a similar review, but for desktop programs.

In order for all three programs to be in the same weight category, it was decided to compare only proprietary software, that is, software with closed source code. The program CyberSafe Top Secret will be compared Folder Lock program and PGP Desktop. I think many people are familiar with the latest program. But Folder Lock was also chosen not by chance - it won a gold award in comparison of ten encryption programs .
The main features of the Folder Lock program are as follows:
It would seem that the program has enough features, especially for personal use. Now let's look at the program in work. At the first start, the program asks to set a master password, which is used to authenticate the user in the program (Fig. 1). Imagine this situation: you have hidden files, and someone else launched the program, looked at which files are hidden and got access to them. Agree, not very good. But if the program asks for a password, then “someone” will not be able to do anything - in any case, until he picks up or recognizes your password.

Fig. 1. Setting a master password at first launch
First, let's see how the program hides files. Go to Lock Files, then either drag and drop files (Fig. 2) and folders to the main program area or use the Add button . As shown in fig. 3, the program allows you to hide files, folders and drives.
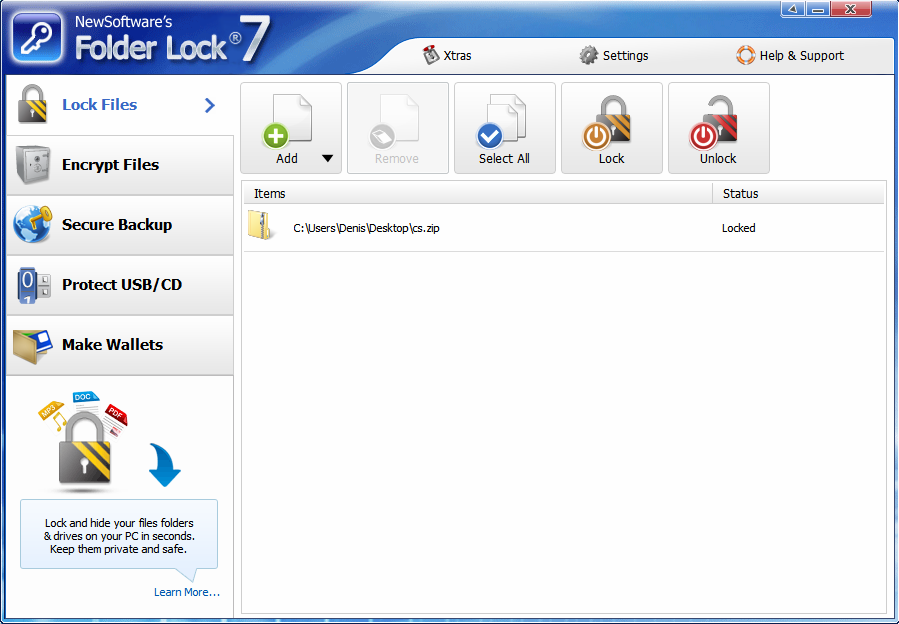
Fig. 2. Drag the file, select it and click the Lock button

. 3. Add button.
Let's see what happens when we press the Lock button . I tried to hide the file C: \ Users \ Denis \ Desktop \ cs.zip. The file disappeared from Explorer, Total Commander and other file managers, even if the display of hidden files is turned on. The file hiding button is called Lock , and the Lock Files section. However, you would need to name these UI elements Hide and Hide Files respectively. Because in fact, the program does not block access to the file, but simply “hides” it. Look at the pic. 4. I, knowing the exact file name, copied it to the cs2.zip file. The file was copied quietly, there were no access errors, the file was not encrypted - it was unpacked, as usual.
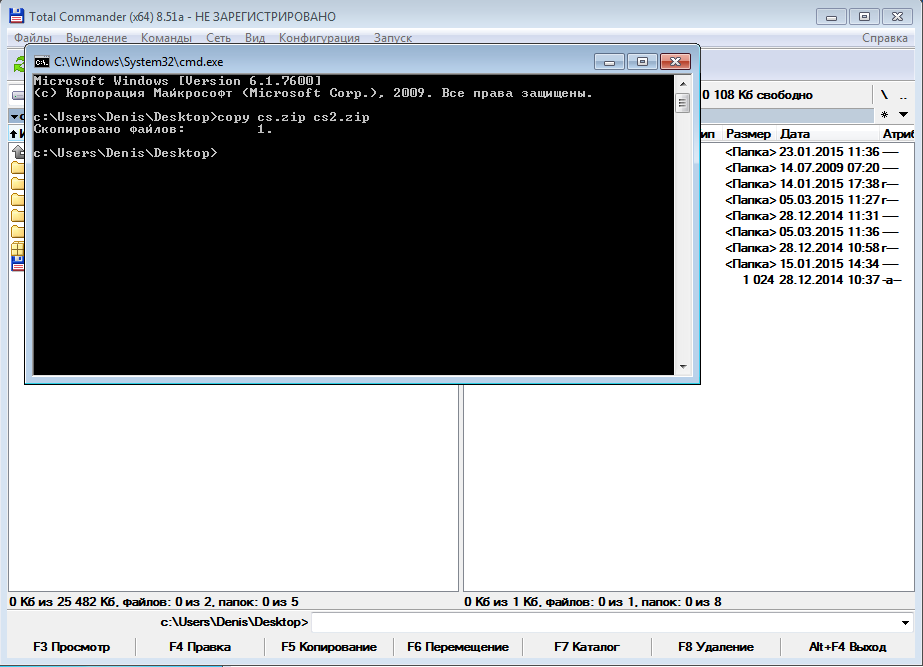
Fig. 4. Copying a hidden file.
The hiding function itself is stupid and useless. However, if you use it together with the file encryption function - to hide the safes created by the program - then the efficiency of its use will increase.
Under Encrypt FilesYou can create lockers. A safe is an encrypted container that, after mounting, can be used as a regular disk - encryption is not simple, but transparent. The same technique is used by many other encryption programs, including TrueCrypt, CyberSafe Top Secret, etc.

Fig. 5. Encrypt Files Section
Click Create Locker, in the window that appears, enter a name and select the location of the safe (Fig. 6). Next, you need to enter a password to access the safe (Fig. 7). The next step is the choice of the file system and the size of the safe (Fig. 8). The size of the safe is dynamic, but you can set its maximum limit. This saves disk space if you don’t use the safe to the eyeballs. If you wish, you can create a fixed-size safe, which will be shown in the "Performance" section of this article.
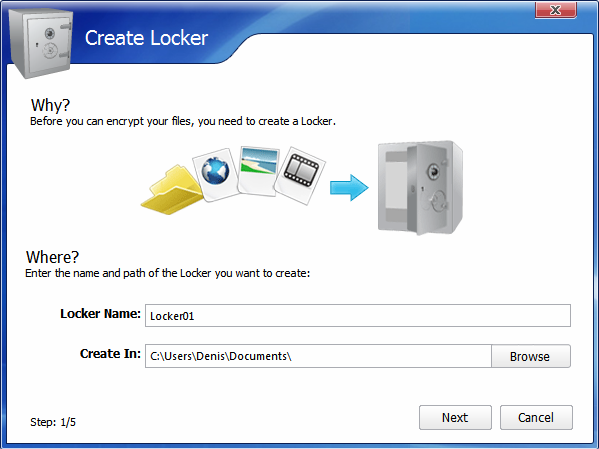
Fig. 6. Name and location of the safe
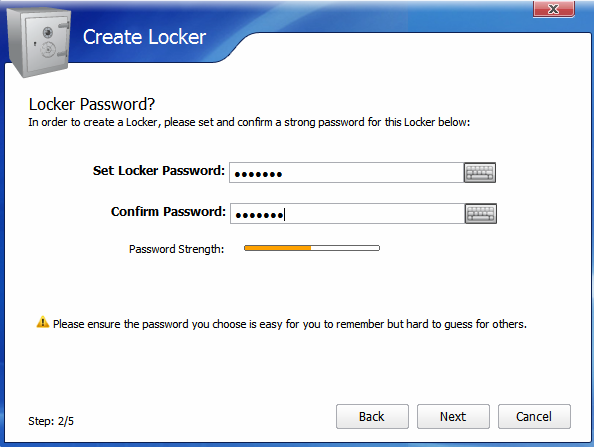
Fig. 7. Password to access the safe

Fig. 8. File system and safe size
After that, you will see the UAC window (if it is enabled), in which you will need to click Yes, then a window with information about the created safe will be displayed. In it, you need to click the Finish button, after which the Explorer window will open, displaying the mounted container (media), see Fig. 9.

Fig. 9. The virtual disk created by the program
Return to the Encrypt Files section and highlight the created safe (Fig. 10). The Open Locker button allows you to open a closed safe; Close Locker allows you to close an open safe; the Edit Options button calls up the menu containing the delete / copy / rename / change password commands. Backup Online Buttonallows you to back up the safe, and not just anywhere, but to the cloud (Fig. 11). But first, you have to create a Secure Backup Account , after which you will receive up to 2 TB of disk space, and your safes will automatically synchronize with online storage, which is especially useful if you need to work with the same safe on different computers.

Fig. 10. Operations on the safe

Fig. 11. Creating a Secure Backup Account
Nothing happens just like that. The rates for storing your safes can be found at secure.newsoftwares.net/signup?id=en. For 2 TB you have to pay $ 400 per month. 500 GB will cost $ 100 per month. To be honest, it is very expensive. For $ 50-60 you can rent a whole VPS with 500 GB “on board”, which you can use as storage for your safes and even create your own website on it.
Please note: the program can create encrypted partitions, but unlike the PGP Desktop program, it cannot encrypt entire disks. Under Protect USB / CDYou can protect your USB / CD / DVD-ROM drive, as well as email attachments (Fig. 12). However, this protection is not carried out by encrypting the medium itself, but by writing to the corresponding medium a self-decrypting safe. In other words, a truncated portable version of the program will be written to the selected medium, allowing you to "open" the safe. As such, this program does not have mail client support either. You can encrypt the attachment and attach it (already encrypted) to the message. But the attachment is encrypted with a regular password, not PKI. I think it makes no sense to talk about reliability.
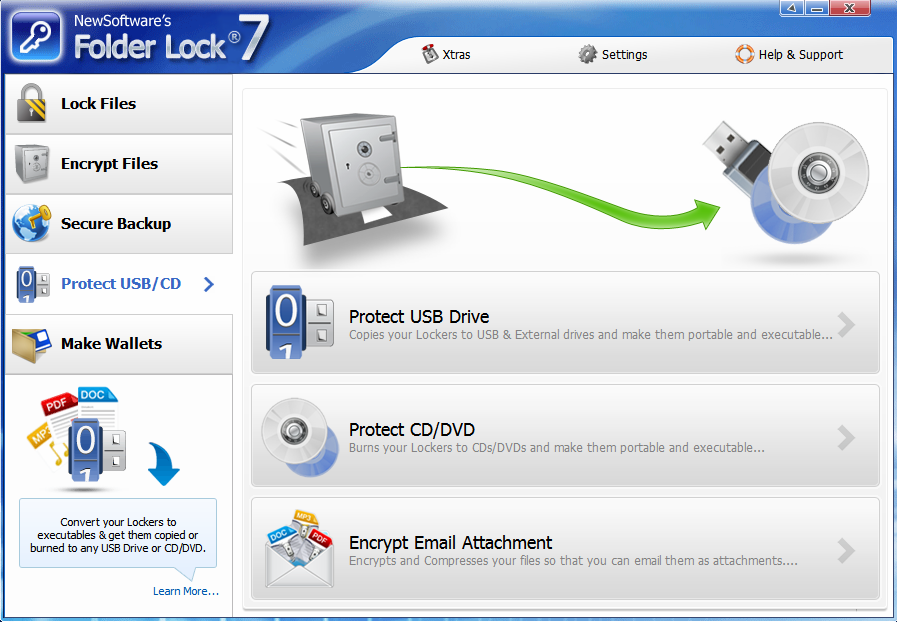
Fig. 12. Protect USB / CD
Section Make Wallets Sectionallows you to create wallets containing information about your credit cards, bank accounts, etc. (fig. 13). All information, of course, is stored in encrypted form. I can say with all responsibility that this section is useless, since the function of exporting information from the wallet is not provided. Imagine that you have many bank accounts and you have entered information about each of them into the program - account number, bank name, account holder, SWIFT code, etc. Then you need to provide account information to a third party to transfer money to you. You will have to manually copy each field, paste it into a document or email. Having an export function would greatly facilitate this task. As for me, it’s much easier to store all this information in one common document,
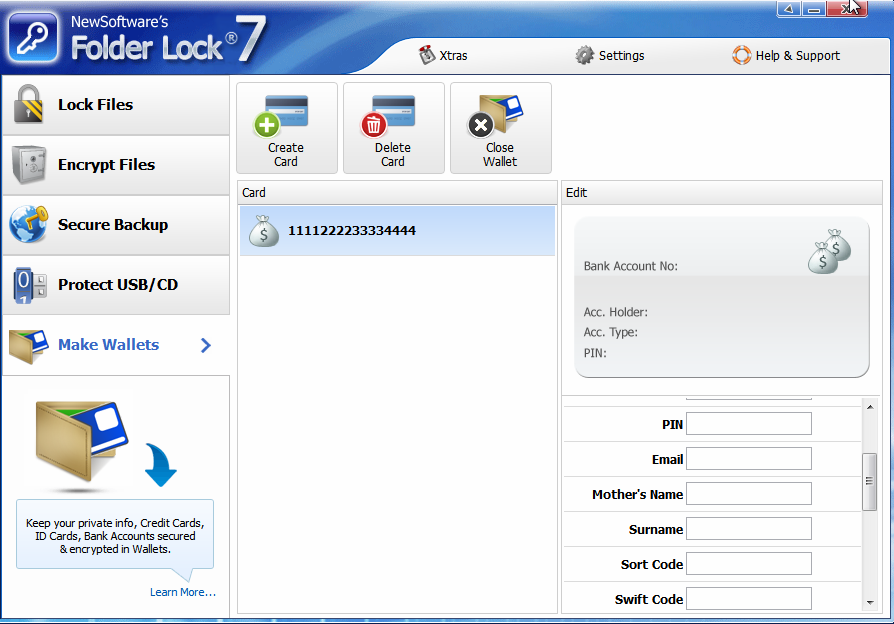
Fig. 13. Wallets
Benefits of the Folder Lock program:
The disadvantages of the program:
Symantec's PGP Desktop is a suite of encryption programs that provides flexible, multi-level encryption. The program differs from CyberSafe TopSecret and Folder Lock in its tight integration into the system shell. The program is embedded in the shell (Explorer), and its functions are accessed through the Explorer context menu (Fig. 14). As you can see, the context menu has the functions of encryption, file signature, etc. The function of creating a self-decrypting archive is quite interesting - according to the principle of a self-extracting archive, only instead of unpacking the archive is also decrypted. However, the programs Folder Lock and CyberSafe also have a similar function.

Fig. 14. Context menu PGP Desktop
Also, access to the program functions can be obtained through the system tray (Fig. 15). CommandOpen PGP Desktop opens the main window of the program (Fig. 16).
Fig. 15. The program in the system tray
Fig. 16. PGP Desktop window
Sections of the program:
Fig. 17. Self-decrypting archive
As for virtual disks, I especially liked the opportunity to create a virtual disk of dynamic size (Fig. 18), as well as the choice of an algorithm other than AES. The program allows you to select the drive letter to which the virtual disk will be mounted, and also allows you to automatically mount the disk at system startup and unmount when idle (by default after 15 minutes of inactivity).
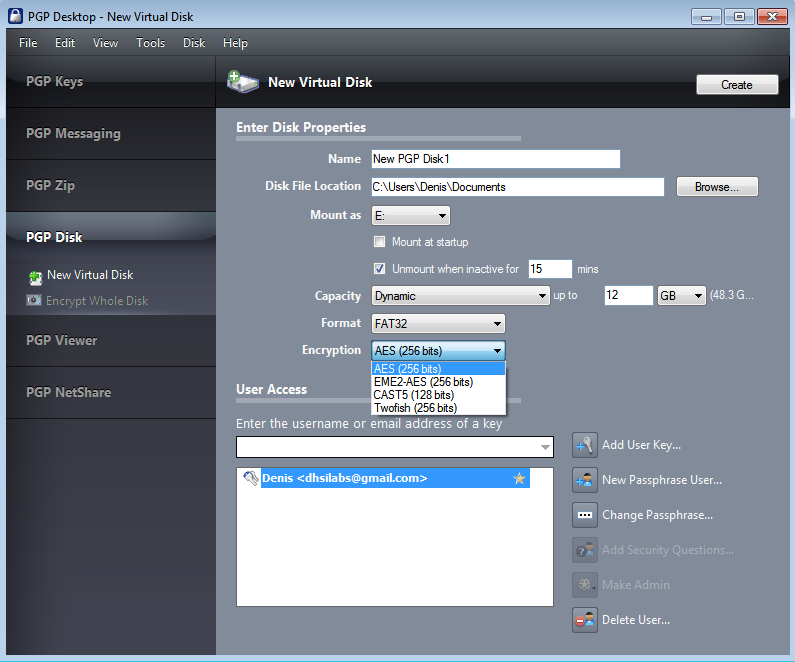
Fig. 18. Creating a virtual disk.
The program tries to encrypt everything and everything. It monitors POP / SMTP connections and offers to protect them (Fig. 19). The same goes for instant messaging clients (Figure 20). It is also possible to protect IMAP connections, but it must be separately included in the program settings.
Fig. 19. Detected SSL / TLS-connection
Fig. 20. PGP IM in action
It is a pity that PGP Desktop does not support popular modern programs like Skype and Viber. Who is using AOL IM now? I think there are few of them.
Also, when using PGP Desktop, it is difficult to configure mail encryption, which works only in interception mode. But what if encrypted mail has already been received, and PGP Desktop was launched after receiving the encrypted message. How to decrypt it? You can, of course, but you have to do it manually. In addition, already decrypted letters in the client are no longer protected. And if you configure the client for certificates, as is done in the CyberSafe Top Secret program, then the letters will always be encrypted.
The interception mode also does not work very well, because a message about mail protection appears every time on every new mail server, and gmail has a lot of them. The mail protection window will get bored very quickly.
The stability of the program also does not differ (Fig. 21).
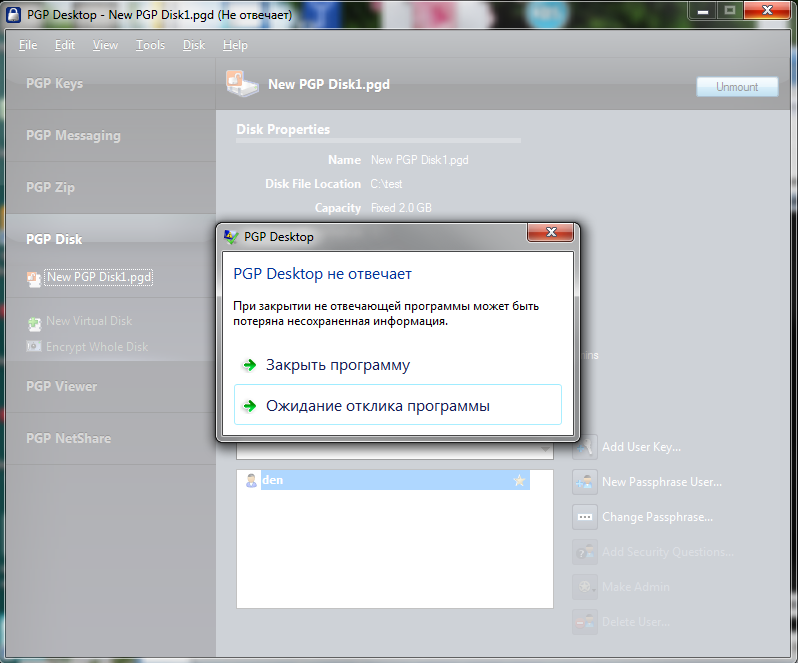
Fig. 21. PGP Desktop freezes ...
Also, after installing it, the system worked more slowly (subjectively) ...
Advantages of PGP Desktop:
The disadvantages of the program:
As in the previous review , there will not be a detailed description of the CyberSafe Top Secret program, since a lot has already been written about it in our blog (Fig. 22).

Fig. 22. CyberSafe Top Secret program
However, we still pay attention to some points - the most important. The program contains tools for managing keys and certificates, and the presence of CyberSafe's own key server allows the user to publish his public key on it, as well as obtain public keys of other company employees (Fig. 23).
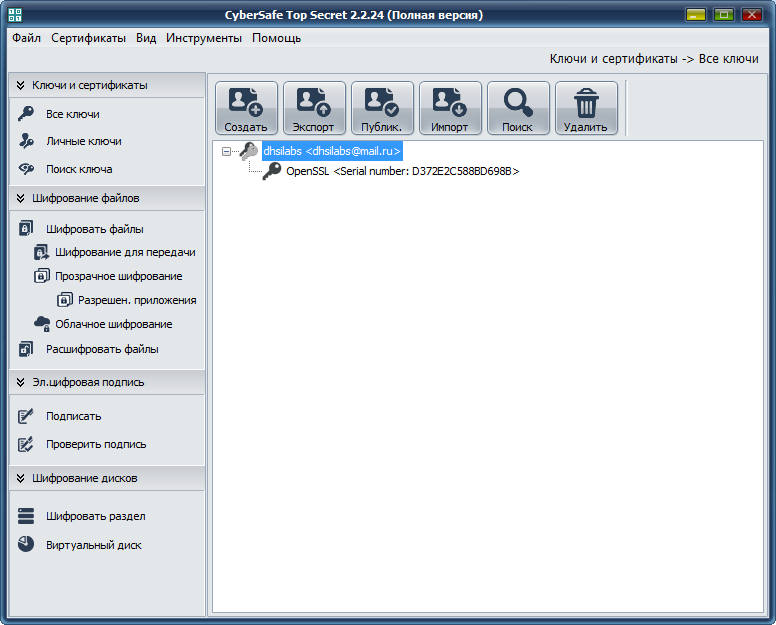
Fig. 23. Key management
The program can be used to encrypt individual files, which was shown in the article “Electronic Signature: Practical Use of the CyberSafe Enterprise Software Product in an Enterprise. Part one". As for encryption algorithms, the CyberSafe Top Secret program supports GOST algorithms and the certified cryptographic provider CryptoPro, which allows it to be used in government institutions and banks.
Also, the program can be used to transparently encrypt a folder (Fig. 24), which allows it to be used as a replacement for EFS . And, considering that the CyberSafe program turned out to be more reliable and faster (in some scenarios) than EFS, then it is not only possible to use, but also necessary.

Fig. 24. Transparent encryption of the C: \ CS-Crypted folder
The functionality of the CyberSafe Top Secret program resembles the functionality of the PGP Desktop program - if you notice, the program can also be used to encrypt e-mail messages, as well as to electronically sign files and verify this signature (section Digital Signature , see Figure 25).
Fig. 25. Section El. digital signature
Like PGP Desktop, CyberSafe Top Secret can create virtual encrypted disks and encrypt hard drive partitions completely. It should be noted that the CyberSafe Top Secret program can only create virtual disks of a fixed size, unlike the Folder Lock and PGP Desktop programs. However, this drawback is neutralized by the possibility of transparent encryption of the folder, and the size of the folder is limited only by the amount of free space on the hard disk.
Unlike PGP Desktop, CyberSafe Top Secret does not know how to encrypt a system hard drive; it is limited only to encrypting external and internal non-system drives.
But CyberSafe Top Secret has the ability to cloud backup, and, unlike Folder Lock, this feature is absolutely free, or rather, the cloud backup function can be configured for any service - both paid and free. You can read more about this feature in the article “Encryption of backups on cloud services” .
Two important features of the program should also be noted: two-factor authorization and a system of trusted applications. In the program settings, you can either set password authentication or two-factor authentication (Fig. 26).

Fig. 26. Application settings
On the Allowed tab . applicationsYou can identify trusted applications that are allowed to work with encrypted files. By default, all applications are trusted. But for greater security, you can specify applications that are allowed to work with encrypted files (Fig. 27).

Fig. 27. Trusted Applications
CyberSafe Top Secret Benefits:
Now about the shortcomings of the program. The program has no special flaws, but since the task was to honestly compare the programs, the flaws still have to be found. If you really find fault, sometimes in the program (very, very rarely) non-localized messages like “Password is weak” “slip through”. Also, while the program is not able to encrypt the system drive, but such encryption is not always and not everyone needs it. But all this is trivial in comparison with PGP Desktop freezing and its cost (but you still do not know about it).
When working with PGP Desktop, I had the impression (right after installing the program) that the computer began to work more slowly. If not for this “sixth sense,” this section was not in this article. It was decided to measure the performance of CrystalDiskMark . All tests are carried out on a real machine - no virtual machines. The configuration of the laptop is as follows - Intel 1000M (1.8 GHz) / 4 GB RAM / WD WD5000LPVT (500 GB, SATA-300, 5400 RPM, 8 MB / Windows 7 64-bit buffer). The car is not very powerful, but what it is.
The test will be performed as follows. We launch one of the programs and create a virtual container. The container options are as follows:
After that, the program closes (of course, the virtual disk is unmounted) - so that nothing would interfere with the test of the next program. The next program starts, a similar container is created in it and the test is performed again. To make it easier for you to read the test results, you need to talk about what CrystalDiskMark results mean:
During the test, all programs except CrystalDiskMark were closed. I chose the test size of 1000 MB and set 2 passes, so as not to force my hard drive again (as a result of this experiment, his temperature rose from 37 to 40 degrees already).
Let's start with a regular hard drive, so that there is something to compare. The performance of the C: drive (and this is the only partition on my computer) will be considered the reference. So, I got the following results (Fig. 28).

Fig. 28. Hard drive performance
Now let's start testing the first program. Let it be Folder Lock. In fig. 29 shows the parameters of the created container. Please note: I use a fixed size. The program results are shown in Fig. 30. As you can see, there is a significant decrease in performance compared to the standard. But this is normal - because the data is encrypted and decrypted on the fly. Performance should be lower, the question is how much.
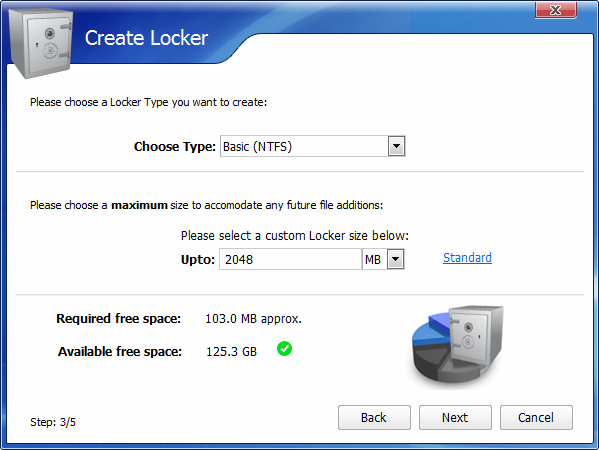
Fig. 29. Parameters of the Folder Lock container
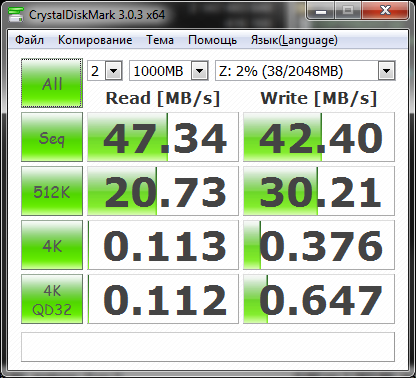
Fig. 30. Results of the Folder Lock program
The next program is PGP Desktop. In fig. 31 - parameters of the created container, and in fig. 32 - results. My feelings were confirmed - the program really works more slowly, which was confirmed by the test. But only during the work of this program not only the virtual disk, but even the whole system “slowed down”, which was not observed when working with other programs.
Fig.
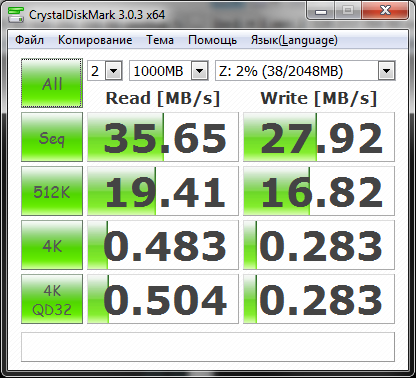
Figure 31. PGP Desktop container options 32. PGP Desktop program results It
remains to test the program CyberSafe Top Secret. As usual, first - the container parameters (Fig. 33), and then the program results (Fig. 34).
Fig.
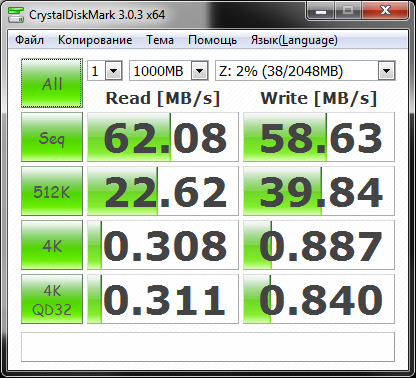
Fig. 33. Parameters of the container CyberSafe Top Secret Fig. 34. CyberSafe Top Secret Program Results
I think the comments will be superfluous. In terms of productivity, the places were distributed as follows:
Since we tested proprietary software, we need to consider another important factor - price. The Folder Lock app will cost $ 39.95 for one installation and $ 259.70 for 10 installations. On the one hand, the price is not very high, but the functionality of the program, frankly, is small. As already noted, the functions of hiding files and wallets are of little use. The Secure Backup function requires an additional fee, therefore, giving almost $ 40 (if you put yourself in the place of an ordinary user, not a company) just for the ability to encrypt files and create self-decrypting safes is expensive.
The program PGP Desktopwill cost $ 97. And mind you, this is just the starting price. The full version with a set of all modules will cost about $ 180-250 and this is only a license for 12 months. In other words, every year you will have to pay $ 250 for using the program. As for me, this is too much.
The CyberSafe Top Secret program is the golden mean, both in terms of functionality and price. For an ordinary user, the program will cost only $ 50 (a special anti-crisis price for Russia, for other countries the full version will cost $ 90). Please note, the full version of Ultimate is worth so much .
Table 1 contains a comparative table of the functions of all three products, which can help you choose exactly your product.
Table 1. Programs and Features
Considering all the factors described in this article (functionality, performance and price), the winner of this comparison is the CyberSafe Top Secret program. If you have any questions, we will be happy to answer them in the comments.

The choice of programs to compare
In order for all three programs to be in the same weight category, it was decided to compare only proprietary software, that is, software with closed source code. The program CyberSafe Top Secret will be compared Folder Lock program and PGP Desktop. I think many people are familiar with the latest program. But Folder Lock was also chosen not by chance - it won a gold award in comparison of ten encryption programs .
Folder Lock Overview
The main features of the Folder Lock program are as follows:
- AES encryption, 256-bit key length.
- Hiding files and folders.
- File encryption (by creating virtual disks - safes) "on the fly."
- Online backup.
- Create secure USB / CD / DVDs.
- Encryption of email attachments.
- Creating encrypted “wallets” that store information about credit cards, accounts, etc.
It would seem that the program has enough features, especially for personal use. Now let's look at the program in work. At the first start, the program asks to set a master password, which is used to authenticate the user in the program (Fig. 1). Imagine this situation: you have hidden files, and someone else launched the program, looked at which files are hidden and got access to them. Agree, not very good. But if the program asks for a password, then “someone” will not be able to do anything - in any case, until he picks up or recognizes your password.

Fig. 1. Setting a master password at first launch
First, let's see how the program hides files. Go to Lock Files, then either drag and drop files (Fig. 2) and folders to the main program area or use the Add button . As shown in fig. 3, the program allows you to hide files, folders and drives.

Fig. 2. Drag the file, select it and click the Lock button

. 3. Add button.
Let's see what happens when we press the Lock button . I tried to hide the file C: \ Users \ Denis \ Desktop \ cs.zip. The file disappeared from Explorer, Total Commander and other file managers, even if the display of hidden files is turned on. The file hiding button is called Lock , and the Lock Files section. However, you would need to name these UI elements Hide and Hide Files respectively. Because in fact, the program does not block access to the file, but simply “hides” it. Look at the pic. 4. I, knowing the exact file name, copied it to the cs2.zip file. The file was copied quietly, there were no access errors, the file was not encrypted - it was unpacked, as usual.

Fig. 4. Copying a hidden file.
The hiding function itself is stupid and useless. However, if you use it together with the file encryption function - to hide the safes created by the program - then the efficiency of its use will increase.
Under Encrypt FilesYou can create lockers. A safe is an encrypted container that, after mounting, can be used as a regular disk - encryption is not simple, but transparent. The same technique is used by many other encryption programs, including TrueCrypt, CyberSafe Top Secret, etc.

Fig. 5. Encrypt Files Section
Click Create Locker, in the window that appears, enter a name and select the location of the safe (Fig. 6). Next, you need to enter a password to access the safe (Fig. 7). The next step is the choice of the file system and the size of the safe (Fig. 8). The size of the safe is dynamic, but you can set its maximum limit. This saves disk space if you don’t use the safe to the eyeballs. If you wish, you can create a fixed-size safe, which will be shown in the "Performance" section of this article.

Fig. 6. Name and location of the safe

Fig. 7. Password to access the safe

Fig. 8. File system and safe size
After that, you will see the UAC window (if it is enabled), in which you will need to click Yes, then a window with information about the created safe will be displayed. In it, you need to click the Finish button, after which the Explorer window will open, displaying the mounted container (media), see Fig. 9.

Fig. 9. The virtual disk created by the program
Return to the Encrypt Files section and highlight the created safe (Fig. 10). The Open Locker button allows you to open a closed safe; Close Locker allows you to close an open safe; the Edit Options button calls up the menu containing the delete / copy / rename / change password commands. Backup Online Buttonallows you to back up the safe, and not just anywhere, but to the cloud (Fig. 11). But first, you have to create a Secure Backup Account , after which you will receive up to 2 TB of disk space, and your safes will automatically synchronize with online storage, which is especially useful if you need to work with the same safe on different computers.

Fig. 10. Operations on the safe

Fig. 11. Creating a Secure Backup Account
Nothing happens just like that. The rates for storing your safes can be found at secure.newsoftwares.net/signup?id=en. For 2 TB you have to pay $ 400 per month. 500 GB will cost $ 100 per month. To be honest, it is very expensive. For $ 50-60 you can rent a whole VPS with 500 GB “on board”, which you can use as storage for your safes and even create your own website on it.
Please note: the program can create encrypted partitions, but unlike the PGP Desktop program, it cannot encrypt entire disks. Under Protect USB / CDYou can protect your USB / CD / DVD-ROM drive, as well as email attachments (Fig. 12). However, this protection is not carried out by encrypting the medium itself, but by writing to the corresponding medium a self-decrypting safe. In other words, a truncated portable version of the program will be written to the selected medium, allowing you to "open" the safe. As such, this program does not have mail client support either. You can encrypt the attachment and attach it (already encrypted) to the message. But the attachment is encrypted with a regular password, not PKI. I think it makes no sense to talk about reliability.

Fig. 12. Protect USB / CD
Section Make Wallets Sectionallows you to create wallets containing information about your credit cards, bank accounts, etc. (fig. 13). All information, of course, is stored in encrypted form. I can say with all responsibility that this section is useless, since the function of exporting information from the wallet is not provided. Imagine that you have many bank accounts and you have entered information about each of them into the program - account number, bank name, account holder, SWIFT code, etc. Then you need to provide account information to a third party to transfer money to you. You will have to manually copy each field, paste it into a document or email. Having an export function would greatly facilitate this task. As for me, it’s much easier to store all this information in one common document,

Fig. 13. Wallets
Benefits of the Folder Lock program:
- Attractive and intuitive interface that will appeal to novice users who speak English.
- Transparent encryption "on the fly", the creation of virtual encrypted drives, which you can work with like regular drives.
- Possibility of online backup and synchronization of encrypted containers (safes).
- Ability to create self-decrypting containers on USB / CD / DVD-ROM drive.
The disadvantages of the program:
- There is no support for the Russian language, which will complicate the work of the program for users who are not familiar with the English language.
- The dubious functions are Lock Files (which simply hides, but does not “lock” files) and Make Wallets (ineffective without exporting information). Honestly, I thought that the Lock Files function would provide transparent encryption of the folder / file on the disk, as CyberSafe Top Secret or the EFS file system do .
- Inability to sign files, verify digital signatures.
- When you open the safe, it does not allow you to select the drive letter that will be assigned to the virtual drive that corresponds to the safe. In the program settings you can select only the order in which the program will assign a drive letter - ascending (from A to Z) or descending (from Z to A).
- There is no integration with email clients, there is only the ability to encrypt the attachment.
- The high cost of cloud backup.
PGP Desktop
Symantec's PGP Desktop is a suite of encryption programs that provides flexible, multi-level encryption. The program differs from CyberSafe TopSecret and Folder Lock in its tight integration into the system shell. The program is embedded in the shell (Explorer), and its functions are accessed through the Explorer context menu (Fig. 14). As you can see, the context menu has the functions of encryption, file signature, etc. The function of creating a self-decrypting archive is quite interesting - according to the principle of a self-extracting archive, only instead of unpacking the archive is also decrypted. However, the programs Folder Lock and CyberSafe also have a similar function.

Fig. 14. Context menu PGP Desktop
Also, access to the program functions can be obtained through the system tray (Fig. 15). CommandOpen PGP Desktop opens the main window of the program (Fig. 16).

Fig. 15. The program in the system tray

Fig. 16. PGP Desktop window
Sections of the program:
- PGP Keys - key management (both own and imported from keyserver.pgp.com).
- PGP Messaging - Manage messaging services. During installation, the program automatically detects your accounts and automatically encrypts AOL Instant Messenger communications.
- PGP Zip - encrypted archive management. The program supports transparent and opaque encryption. This section also implements opaque encryption. You can create an encrypted Zip archive (PGP Zip) or a self-decrypting archive (Fig. 17).
- PGP Disk is an implementation of the transparent encryption function. The program can either encrypt the entire partition of the hard disk (or even the entire disk) or create a new virtual disk (container). There is also a function Shred Free Space, which allows you to wipe free space on the disk.
- PGP Viewer - here you can decrypt PGP messages and attachments.
- PGP NetShare is a tool for "sharing" folders, while the "balls" are encrypted using PGP, and you have the opportunity to add / remove users (users are identified based on certificates) who have access to the "ball".

Fig. 17. Self-decrypting archive
As for virtual disks, I especially liked the opportunity to create a virtual disk of dynamic size (Fig. 18), as well as the choice of an algorithm other than AES. The program allows you to select the drive letter to which the virtual disk will be mounted, and also allows you to automatically mount the disk at system startup and unmount when idle (by default after 15 minutes of inactivity).

Fig. 18. Creating a virtual disk.
The program tries to encrypt everything and everything. It monitors POP / SMTP connections and offers to protect them (Fig. 19). The same goes for instant messaging clients (Figure 20). It is also possible to protect IMAP connections, but it must be separately included in the program settings.

Fig. 19. Detected SSL / TLS-connection

Fig. 20. PGP IM in action
It is a pity that PGP Desktop does not support popular modern programs like Skype and Viber. Who is using AOL IM now? I think there are few of them.
Also, when using PGP Desktop, it is difficult to configure mail encryption, which works only in interception mode. But what if encrypted mail has already been received, and PGP Desktop was launched after receiving the encrypted message. How to decrypt it? You can, of course, but you have to do it manually. In addition, already decrypted letters in the client are no longer protected. And if you configure the client for certificates, as is done in the CyberSafe Top Secret program, then the letters will always be encrypted.
The interception mode also does not work very well, because a message about mail protection appears every time on every new mail server, and gmail has a lot of them. The mail protection window will get bored very quickly.
The stability of the program also does not differ (Fig. 21).

Fig. 21. PGP Desktop freezes ...
Also, after installing it, the system worked more slowly (subjectively) ...
Advantages of PGP Desktop:
- A full-fledged program used to encrypt files, sign files and verify electronic signatures, transparent encryption (virtual disks and encryption of the entire partition), email encryption.
- Key server support keyserver.pgp.com.
- Ability to create self-decrypting archives.
- The ability to encrypt the system hard drive.
- PGP NetShare Feature.
- The possibility of overwriting free space.
- Close integration with Explorer.
The disadvantages of the program:
- The lack of support for the Russian language, which will complicate the work with the program for users who do not know English.
- Unstable program operation.
- Poor program performance.
- There is support for AOL IM, but there is no support for Skype and Viber.
- Already decrypted letters remain unprotected on the client.
- Mail protection only works in interception mode, which will quickly bother you, since the mail protection window will appear every time for each new server.
CyberSafe Top Secret
As in the previous review , there will not be a detailed description of the CyberSafe Top Secret program, since a lot has already been written about it in our blog (Fig. 22).

Fig. 22. CyberSafe Top Secret program
However, we still pay attention to some points - the most important. The program contains tools for managing keys and certificates, and the presence of CyberSafe's own key server allows the user to publish his public key on it, as well as obtain public keys of other company employees (Fig. 23).

Fig. 23. Key management
The program can be used to encrypt individual files, which was shown in the article “Electronic Signature: Practical Use of the CyberSafe Enterprise Software Product in an Enterprise. Part one". As for encryption algorithms, the CyberSafe Top Secret program supports GOST algorithms and the certified cryptographic provider CryptoPro, which allows it to be used in government institutions and banks.
Also, the program can be used to transparently encrypt a folder (Fig. 24), which allows it to be used as a replacement for EFS . And, considering that the CyberSafe program turned out to be more reliable and faster (in some scenarios) than EFS, then it is not only possible to use, but also necessary.

Fig. 24. Transparent encryption of the C: \ CS-Crypted folder
The functionality of the CyberSafe Top Secret program resembles the functionality of the PGP Desktop program - if you notice, the program can also be used to encrypt e-mail messages, as well as to electronically sign files and verify this signature (section Digital Signature , see Figure 25).

Fig. 25. Section El. digital signature
Like PGP Desktop, CyberSafe Top Secret can create virtual encrypted disks and encrypt hard drive partitions completely. It should be noted that the CyberSafe Top Secret program can only create virtual disks of a fixed size, unlike the Folder Lock and PGP Desktop programs. However, this drawback is neutralized by the possibility of transparent encryption of the folder, and the size of the folder is limited only by the amount of free space on the hard disk.
Unlike PGP Desktop, CyberSafe Top Secret does not know how to encrypt a system hard drive; it is limited only to encrypting external and internal non-system drives.
But CyberSafe Top Secret has the ability to cloud backup, and, unlike Folder Lock, this feature is absolutely free, or rather, the cloud backup function can be configured for any service - both paid and free. You can read more about this feature in the article “Encryption of backups on cloud services” .
Two important features of the program should also be noted: two-factor authorization and a system of trusted applications. In the program settings, you can either set password authentication or two-factor authentication (Fig. 26).

Fig. 26. Application settings
On the Allowed tab . applicationsYou can identify trusted applications that are allowed to work with encrypted files. By default, all applications are trusted. But for greater security, you can specify applications that are allowed to work with encrypted files (Fig. 27).

Fig. 27. Trusted Applications
CyberSafe Top Secret Benefits:
- Support for GOST encryption algorithms and a certified cryptographic provider CryptoPro, which allows you to use the program not only to individuals and commercial organizations, but also to government agencies.
- Support for transparent folder encryption, which allows you to use the program as a replacement for EFS. Given that the program provides the best level of performance and security , such a replacement is more than justified.
- The ability to sign files electronically and the ability to verify the signature of the file.
- A built-in key server that allows you to publish keys and access other keys that have been published by other company employees.
- The ability to create a virtual encrypted disk and the ability to encrypt the entire partition.
- Ability to create self-decrypting archives.
- Possibility of free cloud backup that works with any service - both paid and free.
- Two-factor user authentication.
- A system of trusted applications that allows access to encrypted files only to specific applications.
- The CyberSafe application supports the AES-NI instruction set, which has a positive effect on program performance (this fact will be demonstrated later).
- The CyberSafe driver allows you to work over the network, which makes it possible to organize corporate encryption .
- Russian-language interface of the program. For English-speaking users, it is possible to switch to English.
Now about the shortcomings of the program. The program has no special flaws, but since the task was to honestly compare the programs, the flaws still have to be found. If you really find fault, sometimes in the program (very, very rarely) non-localized messages like “Password is weak” “slip through”. Also, while the program is not able to encrypt the system drive, but such encryption is not always and not everyone needs it. But all this is trivial in comparison with PGP Desktop freezing and its cost (but you still do not know about it).
Performance
When working with PGP Desktop, I had the impression (right after installing the program) that the computer began to work more slowly. If not for this “sixth sense,” this section was not in this article. It was decided to measure the performance of CrystalDiskMark . All tests are carried out on a real machine - no virtual machines. The configuration of the laptop is as follows - Intel 1000M (1.8 GHz) / 4 GB RAM / WD WD5000LPVT (500 GB, SATA-300, 5400 RPM, 8 MB / Windows 7 64-bit buffer). The car is not very powerful, but what it is.
The test will be performed as follows. We launch one of the programs and create a virtual container. The container options are as follows:
- The size of the virtual disk is 2048 MB.
- File System - NTFS
- Drive letter Z:
After that, the program closes (of course, the virtual disk is unmounted) - so that nothing would interfere with the test of the next program. The next program starts, a similar container is created in it and the test is performed again. To make it easier for you to read the test results, you need to talk about what CrystalDiskMark results mean:
- Seq - sequential write / sequential read test (block size = 1024KB);
- 512K - random write / random read test (block size = 512KB);
- 4K is the same as 512K, but the block size is 4 Kb;
- 4K QD32 - random write / read test (block size = 4K, Queue Depth = 32) for NCQ & AHCI.
During the test, all programs except CrystalDiskMark were closed. I chose the test size of 1000 MB and set 2 passes, so as not to force my hard drive again (as a result of this experiment, his temperature rose from 37 to 40 degrees already).
Let's start with a regular hard drive, so that there is something to compare. The performance of the C: drive (and this is the only partition on my computer) will be considered the reference. So, I got the following results (Fig. 28).

Fig. 28. Hard drive performance
Now let's start testing the first program. Let it be Folder Lock. In fig. 29 shows the parameters of the created container. Please note: I use a fixed size. The program results are shown in Fig. 30. As you can see, there is a significant decrease in performance compared to the standard. But this is normal - because the data is encrypted and decrypted on the fly. Performance should be lower, the question is how much.

Fig. 29. Parameters of the Folder Lock container

Fig. 30. Results of the Folder Lock program
The next program is PGP Desktop. In fig. 31 - parameters of the created container, and in fig. 32 - results. My feelings were confirmed - the program really works more slowly, which was confirmed by the test. But only during the work of this program not only the virtual disk, but even the whole system “slowed down”, which was not observed when working with other programs.

Fig.

Figure 31. PGP Desktop container options 32. PGP Desktop program results It
remains to test the program CyberSafe Top Secret. As usual, first - the container parameters (Fig. 33), and then the program results (Fig. 34).

Fig.

Fig. 33. Parameters of the container CyberSafe Top Secret Fig. 34. CyberSafe Top Secret Program Results
I think the comments will be superfluous. In terms of productivity, the places were distributed as follows:
- CyberSafe Top Secret
- Folder lock
- PGP Desktop
Price and conclusions
Since we tested proprietary software, we need to consider another important factor - price. The Folder Lock app will cost $ 39.95 for one installation and $ 259.70 for 10 installations. On the one hand, the price is not very high, but the functionality of the program, frankly, is small. As already noted, the functions of hiding files and wallets are of little use. The Secure Backup function requires an additional fee, therefore, giving almost $ 40 (if you put yourself in the place of an ordinary user, not a company) just for the ability to encrypt files and create self-decrypting safes is expensive.
The program PGP Desktopwill cost $ 97. And mind you, this is just the starting price. The full version with a set of all modules will cost about $ 180-250 and this is only a license for 12 months. In other words, every year you will have to pay $ 250 for using the program. As for me, this is too much.
The CyberSafe Top Secret program is the golden mean, both in terms of functionality and price. For an ordinary user, the program will cost only $ 50 (a special anti-crisis price for Russia, for other countries the full version will cost $ 90). Please note, the full version of Ultimate is worth so much .
Table 1 contains a comparative table of the functions of all three products, which can help you choose exactly your product.
Table 1. Programs and Features
| Function | Folder lock | PGP Desktop | CyberSafe Top Secret |
| Виртуальные зашифрованные диски | Да | Да | Да |
| Шифрование всего раздела | Нет | Да | Да |
| Шифрование системного диска | Нет | Да | Нет |
| Удобная интеграция с почтовыми клиентами | Нет | Нет | Да |
| Шифрование сообщений электронной почты | Да (ограничено) | Да | Да |
| Шифрование файлов | Нет | Да | Да |
| ЭЦП, подписание | Нет | Да | Да |
| ЭЦП, проверка | Нет | Да | Да |
| Прозрачное шифрование папки | Нет | Нет | Да |
| Саморасшифровывающиеся архивы | Да | Да | Да |
| Облачное резервное копирование | Да (платно) | Нет | Да (беплатно) |
| Система доверенных приложений | Нет | Нет | Да |
| Поддержка сертифицированного криптопровайдера | Нет | Нет | Да |
| Поддержка токенов | Нет | Нет (поддержка прекращена) | Да (при установке КриптоПро) |
| Собственный сервер ключей | Нет | Да | Да |
| Двухфакторная аутентификация | Нет | Нет | Да |
| Сокрытие отдельных файлов | Да | Нет | Нет |
| Сокрытие разделов жесткого диска | Да | Нет | Да |
| Бумажники для хранения платежной информации | Да | Нет | Нет |
| Поддержка шифрования ГОСТ | Нет | Нет | Да |
| Русский интерфейс | Нет | Нет | Да |
| Последовательная чтение/ запись (DiskMark), Мб/с | 47/42 | 35/27 | 62/58 |
| Стоимость | 40$ | 180-250$ | 50$ |
Considering all the factors described in this article (functionality, performance and price), the winner of this comparison is the CyberSafe Top Secret program. If you have any questions, we will be happy to answer them in the comments.
