2014 Results: Threats and Windows Exploitation
Today we publish our report for the year, which includes information on various threats, as well as data on current trends in cyberattacks. Over the past year, we have recorded the emergence of many new various malicious programs for Windows, as well as the development of existing families. This is not only about Windows, but also about the mobile platforms Google Android and Apple iOS.

Our report also contains detailed information on closed vulnerabilities in various components of Windows and MS Office. Many of these vulnerabilities were used by cybercriminals in cyber attacks on users (the so-called 0day). Last year we released a separate press release dedicated to the famous BlackEnergy Trojan. It was distributed using the 0day vulnerability in Office.
The report includes the following information:
Over the past year, we have seen many exploits that were used by attackers to organize drive-by download attacks. Such attacks are very beneficial for them, because they allow you to install malicious programs on the user's computer in stealth mode (the so-called silently installing ). The report contains detailed information on the nature of such cyberattacks. Since Internet Explorer (IE) is one of the most common targets for cybercriminals, we have included in the report detailed information about its key security innovations, which were added by Microsoft last year and help the user protect himself from such attacks.
In the diagram below you can see the fact that Microsoft closed the largest number of vulnerabilities for IE among all other Windows components and its Office product for IE. Almost all of these vulnerabilities are of the type Remote Code Execution and can be used by attackers to organize drive-by download attacks. In the diagram, IE compares with components such as the kernel-mode driver for the Windows GUI subsystem win32k.sys, other kernel-mode drivers, the .NET Framework product, custom Windows components, and Office.
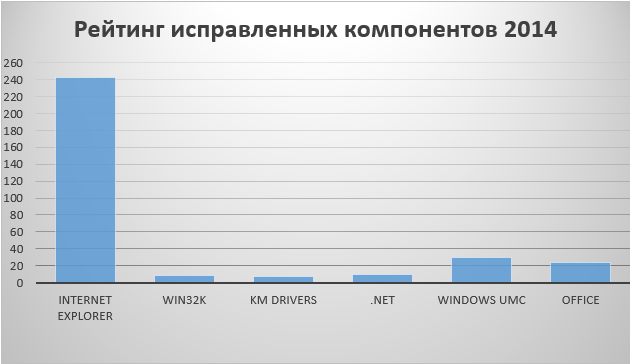
Attackers can remotely execute malicious code in a browser using a specially crafted web page. Such a web page contains special code called an exploit and is used to create the necessary conditions for the vulnerability to be triggered. Attackers typically use these exploits to install malware when they come across a vulnerable version of Windows. Such an attack is a drive-by download type and is a key trend in IE exploitation, as shown in the diagram below.
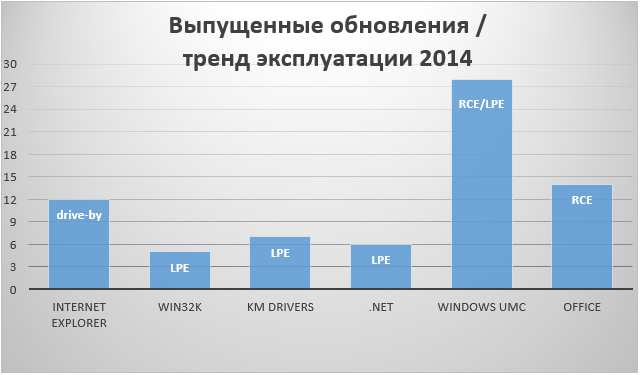
Our report includes detailed information on exploitation prevention mechanisms that Microsoft added to Windows and IE last year. A section describing these mechanisms contains information about Windows, Internet Explorer, and EMET. Such mechanisms can protect the user from exploiting a range of vulnerabilities. For example, the Out-of-date ActiveX control blocking function is very useful for blocking all exploits that use vulnerabilities in outdated versions of oracle Java and MS Silverlight plug-ins.
The report also contains a description of the popular Local Privilege Escalation (LPE) cyber attacks that are used by attackers to bypass the sandbox defense mechanisms of web browsers and launch malicious code with high privileges in the system or in kernel mode. Last year, few vulnerabilities were closed for the win32k.sys driver, which is the source of such vulnerabilities. Unfortunately, win32k.sys is still the main source of LPE vulnerabilities in Windows.
The full report can be downloaded here .

Our report also contains detailed information on closed vulnerabilities in various components of Windows and MS Office. Many of these vulnerabilities were used by cybercriminals in cyber attacks on users (the so-called 0day). Last year we released a separate press release dedicated to the famous BlackEnergy Trojan. It was distributed using the 0day vulnerability in Office.
The report includes the following information:
- Actual malware distribution vectors.
- The most active threats for Windows.
- Trends for Windows.
- Examples of threats for iOS.
- Information about Microsoft's closed vulnerabilities in Windows & Office.
- Statistics of closed vulnerabilities and their comparison since 2013
- A detailed description of the key operating mechanisms of Windows.
- Information about exploited in-the-wild vulnerabilities, including a special table for ASLR bypass vulnerabilities.
- Current exploitation and exploitation methods for Internet Explorer.
Over the past year, we have seen many exploits that were used by attackers to organize drive-by download attacks. Such attacks are very beneficial for them, because they allow you to install malicious programs on the user's computer in stealth mode (the so-called silently installing ). The report contains detailed information on the nature of such cyberattacks. Since Internet Explorer (IE) is one of the most common targets for cybercriminals, we have included in the report detailed information about its key security innovations, which were added by Microsoft last year and help the user protect himself from such attacks.
In the diagram below you can see the fact that Microsoft closed the largest number of vulnerabilities for IE among all other Windows components and its Office product for IE. Almost all of these vulnerabilities are of the type Remote Code Execution and can be used by attackers to organize drive-by download attacks. In the diagram, IE compares with components such as the kernel-mode driver for the Windows GUI subsystem win32k.sys, other kernel-mode drivers, the .NET Framework product, custom Windows components, and Office.

Attackers can remotely execute malicious code in a browser using a specially crafted web page. Such a web page contains special code called an exploit and is used to create the necessary conditions for the vulnerability to be triggered. Attackers typically use these exploits to install malware when they come across a vulnerable version of Windows. Such an attack is a drive-by download type and is a key trend in IE exploitation, as shown in the diagram below.

Our report includes detailed information on exploitation prevention mechanisms that Microsoft added to Windows and IE last year. A section describing these mechanisms contains information about Windows, Internet Explorer, and EMET. Such mechanisms can protect the user from exploiting a range of vulnerabilities. For example, the Out-of-date ActiveX control blocking function is very useful for blocking all exploits that use vulnerabilities in outdated versions of oracle Java and MS Silverlight plug-ins.
The report also contains a description of the popular Local Privilege Escalation (LPE) cyber attacks that are used by attackers to bypass the sandbox defense mechanisms of web browsers and launch malicious code with high privileges in the system or in kernel mode. Last year, few vulnerabilities were closed for the win32k.sys driver, which is the source of such vulnerabilities. Unfortunately, win32k.sys is still the main source of LPE vulnerabilities in Windows.
The full report can be downloaded here .
