Modernizing the Active Directory Environment
For the first time, Microsoft Active Directory (AD) was released with Windows 2000. At that time, its main task was to provide centralized authorization and authentication of PC users and Windows servers, as well as expanding the capabilities of the directory service for organizations using directory-supported applications (for example, Microsoft Exchange).
Nowadays, much has changed in the use and management of AD, including recommendations from Microsoft on improving the organization of work, as well as the style of corporate management of the system. Many regulatory requirements were created that influenced the development of AD. To keep up to date, organizations should reconsider their approach to Active Directory and modernize it. This will facilitate management and increase system performance.
Let's look at the value of improving AD, as well as areas that you should focus on to create a modern infrastructure.
Changes in AD
Both technology and the business world have changed since the first release of Active Directory. Almost every organization was affected by such changes in the service:
Each of these changes plays a separate role in the need to upgrade Active Directory.
Changing Microsoft Recommendations and New System Features
Like AD itself, Microsoft’s recommendations for managing the system have changed significantly. Let's look at two principles that are no longer used, but were characteristic of earlier versions of the system.
Empty forest root domains
Microsoft initially recommended that organizations create empty AD root domains (Figure 1), as it was believed that the first forest domain was of particular importance and should always remain empty. Microsoft has long since rejected this advice and now recommend creating only the necessary domains so as not to complicate the system and not overload it with additional security requirements. However, many still create AD forests with two or more domains and an unused root directory.

Fig. 1. Using an empty root domain
Domain as a security boundary
Earlier, Microsoft recommended avoiding the increase in the number of forests, since there were difficulties in terms of integrating them into each other in terms of security and administration. In addition, the Active Directory domain was considered a security frontier. This made it possible in the forest of two domains to easily separate the users and resources of domains A and B.
Then came a series of articles demonstrating how easy it is for an administrator of one domain to control the resources of another domain within the same forest, after which Microsoft changed its recommendations and urged that the forest, and not the domain, be considered the security boundary. If you want to isolate users or resources in a specific domain, you should build a separate forest. Thus, now organizations usually have many forests, for example, separate the development forest from the production forest, or even from a special Internet-oriented forest. As a result of this separation, companies faced difficulties in administering multiple forests.
Other recommendations have changed due to the development of AD itself. System improvements included delegation of access rights, reporting, expandability (in Windows 2000 there was a limit on 5000 group members), recoverability (snapshot function and recycle bin) and automation (AD administration on Microsoft PowerShell). The new approach has significantly improved the protection, management and recovery of Active Directory.
Administration Model Changes
Another area in which changes have occurred is the administration method. Previously, a small group of administrators was responsible for all aspects related to the system, from infrastructure to content that eventually ends up in the directory. With the growing importance of AD for the IT infrastructure, its administration model has become more complicated. Now in organizations, many people are involved in working with AD: one person is responsible for managing users, user groups and their properties, another for data related to applications, a third for security, etc. This necessitates improving the protection and separation of data in AD by applying a role-based approach to directory management, reviewing the structure, namely the distribution and protection of organizational units.
Changing the Role of AD
Previously, the role of Active Directory in most organizations was very modest. Ee was used to provide centralized login and security for Windows PC users, or as an alternative or to replace systems with Windows NT 4 Security Account Manager (SAM) or Novell NetWare. Over time, AD has become the focus of most events taking place in IT organizations (Fig. 2), providing such functions:
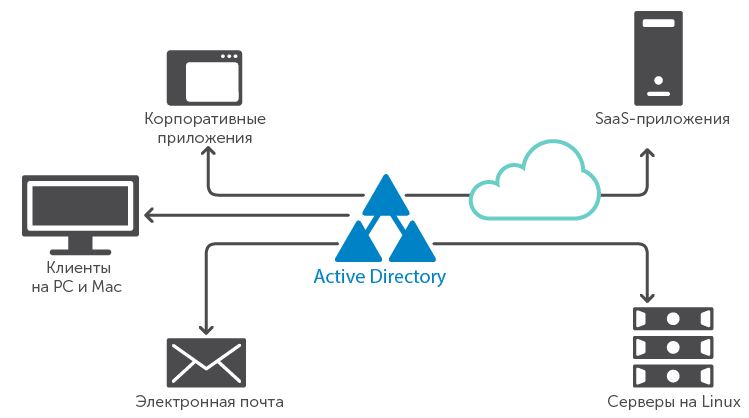
Fig. 2. Active Directory at the center of many IT resources.
In many organizations, AD has become a paramount element of the infrastructure, its security and management are given as much attention as most critical business platforms. In particular, organizations are developing a hybrid approach to the provision of IT services, in which one part of the applications is located in the company's data centers, and the other is stored “on the clouds” of external provider companies. Most often, these two environments are brought together by authentication and providing access through integration through AD. Without a well-protected and well-managed AD, a hybrid approach is more in the way of business than it helps.
Unfortunately, sometimes AD does not receive enough attention from IT staff. This has many manifestations, from insufficient attention to change management in AD, to the assumption that since "everything works this way, you can not strain." This approach does not benefit IT departments, since integration both in general and with cloud solutions plays a very important role.
Changes in the legislative framework
Since the first releases of Active Directory, the difficulties associated with ensuring that IT operates in accordance with current legislation have increased. Now organizations are dealing with many complex regulatory acts, and often it is AD that acts as the main tool for working with them.
The need for monitoring and reporting on the use of Active Directory has increased significantly. Compliance with regulatory acts and its maintenance at the proper level requires the use of more complex processes for managing AD and verifying related activities. Now it is simply unacceptable not to know who and why made each of the changes to the directory system. Ignoring AD-related activities could compromise the integrity of corporate data. Changes should not be allowed out of control, given the importance of this system in matters of authentication and authorization, as well as to ensure proper protection of the most sensitive data. A competent modern approach to managing AD is required to ensure compliance with regulations and security.
Key Steps in Upgrading AD
Many organizations have used Active Directory for many years without changes, so now the structure and practice of working with it require updating. Here are the main areas of application for modernization:
Restructuring AD
Restructuring AD is becoming more common, it is a great way to remake the directory to the current and future needs of the organization. Simply changing organizational units can greatly affect the management and protection of AD. It so happened that the structure of organizational units focused on the structure of the business, for example, on the departments of the company or their geographical location. This approach did not always fit the rest of the catalog needs. For example, in the interests of group policy, you can divide user PCs into organizational units by the type of OS version used, as shown in Fig. 3, but if all PCs are part of the same IT group, this solution will complicate the delegation of rights and administration of the group.
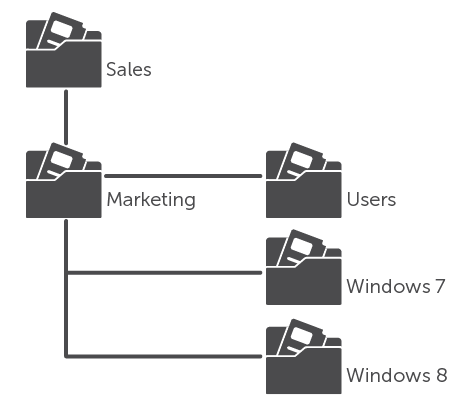
Fig. 3. Organizational unit structure optimized for group policy instead of delegation.
The design of a modern catalog system is striving for a middle ground. To create such an AD structure, it is crucial to take into account the various needs of the organization.
The restructuring of AD itself can take several forms. Sometimes you need to reduce the number of domains and forests to improve data management and protection. In other situations, for security reasons, it may be necessary to split some resources into separate forests (we are talking about resources available to clients). Sometimes you just want to start all over again and build a beautiful AD structure, removing all unnecessary elements. This approach can be extremely inefficient, as it will require additional time to migrate users and resources from the old to the new AD environment.
For any reconstruction, AD will be useful to pay attention to the tools of various developers that will help make the move "painless." This is especially important when transferring data from a poorly documented system to a more structured one, since it is not always possible to predict the progress of the transfer.
Streamlining Management and Administration
Another area for improving AD is directory management and administration. Usually, the first thing they do is reduce the number of administrators with unlimited access throughout AD. The point is to create a less privileged management model in which administrators have access rights that only allow changes to parts of the system for which they are responsible. These sites may be:
These areas have different models of delegation of rights. And if it is not very critical who controls the infrastructure elements of the system, then the data security model inside it is clearly of paramount importance. Therefore, you need to control the management of AD servers and their associated infrastructure, as well as the creation, reading, updating and deletion of data in AD itself.
Membership in AD groups can open access to everything from server administrator rights to financial data. Therefore, you need to carefully monitor access to these groups and regularly conduct certification of access rights.
Protecting Active Directory and its data
In terms of modernization, it is worth considering delegation - control over who can modify AD objects and their properties. This topic is closely related to ensuring that only authorized users modify objects in it. Too often, organizations provide access to solve immediate problems, and do not cancel it when it is no longer needed.
To manage delegation in Active Directory, you must create a role-based framework to provide access to its objects and their attributes. AD is currently creating role-based templates for each (or at least for each mission-critical) task that administrators must perform, for example, to change membership in privileged groups or change user attributes.
Achieving Compliance, Maintaining and Confirming
Once control over the data arriving in Active Directory has been achieved, you need to constantly check the actions performed on this data. Such audits must meet both internal (for the IT department) and external (for the audit organizations) requirements. Although Microsoft Windows Server and Active Directory initially had the ability to audit events that occurred, it can be practically meaningless, since in loaded environments it contains too much data and quickly overflows.
You must have a clear audit aggregator and the ability to analyze to identify unwanted changes, unauthorized use of AD and corporate resources, as well as tracking user activity across all IT systems. An audit of the system provides a history of changes associated with it and made within it, for example, the time it takes for users to enter the network and the most frequently launched applications.
After establishing control over changes in the entire IT environment, it is important to pay close attention to the critical tasks associated with AD, including changes to its infrastructure and data that can affect the integrity of the directory.
Using change control and auditing as feedback tools to track authorized and unauthorized changes, you can get a complete picture of the changes happening in AD. The latest version implements the possibility of such a review, thanks to which you can always see who and what has access.
Ensuring AD Availability and Resiliency
High availability is another aspect of today's use of Active Directory. Fortunately, AD can become a reliable and flexible part of the IT infrastructure if the work of all its other components is well-established, namely:
Most, if not all, of these tools can be monitored using standard or AD-specific monitoring tools. With the increasing role of AD in organizations, regular monitoring of its performance is becoming increasingly important. It may include the creation of synthetic transactions of typical AD operations, for example, authentication and search, which can confirm that AD servers respond to ping and that processes running on them proceed successfully.
In addition to monitoring availability, it is also important to have good backups and a disaster recovery plan. Now there are many tools for backup and recovery, including at the facility level, allowing you to restore everything from minor changes in the directory system to significant failures. There are three types of recovery associated with AD.

Table 1. Types of AD recovery
As more organizations have begun to use virtualization technology to launch the AD infrastructure, its recovery from failures is becoming more and more popular, and the collapse of an entire forest or server is now less common. Nevertheless, it is important to have a plan of action in the most undesirable situations and suitable tools for reforestation in a minimum of time.
Implementing AD Leadership
After upgrading your AD infrastructure, it is important to provide reliable management for smooth operation. Clear rules for using, expanding, and managing the system must be made You should also create a description of all the key components of AD that affect its operation.
Guidance should include the following elements:
This list of recommendations is just the tip of the iceberg. Active Directory Infrastructure Management must have well-documented standards of conduct in a variety of situations.
Conclusion
Over time, the role of Active Directory has grown dramatically and has become critical for many organizations. For the correct operation of the system, regardless of whether it is used for authentication and authorization of Windows PCs, Linux servers or Java applications, it is necessary to maintain high level of control, availability and efficiency, protection and audit.
By upgrading AD, you can achieve all of these criteria using both the latest versions of Windows Server and software from other developers. In any case, good management and protection are important for the smooth operation of Active Directory.
Nowadays, much has changed in the use and management of AD, including recommendations from Microsoft on improving the organization of work, as well as the style of corporate management of the system. Many regulatory requirements were created that influenced the development of AD. To keep up to date, organizations should reconsider their approach to Active Directory and modernize it. This will facilitate management and increase system performance.
Let's look at the value of improving AD, as well as areas that you should focus on to create a modern infrastructure.
Changes in AD
Both technology and the business world have changed since the first release of Active Directory. Almost every organization was affected by such changes in the service:
- Microsoft recommendations regarding the organization of work of AD;
- own standards for each user;
- increasing the role of AD in organizations;
- Strengthening regulatory requirements for security and access control for sensitive data.
Each of these changes plays a separate role in the need to upgrade Active Directory.
Changing Microsoft Recommendations and New System Features
Like AD itself, Microsoft’s recommendations for managing the system have changed significantly. Let's look at two principles that are no longer used, but were characteristic of earlier versions of the system.
Empty forest root domains
Microsoft initially recommended that organizations create empty AD root domains (Figure 1), as it was believed that the first forest domain was of particular importance and should always remain empty. Microsoft has long since rejected this advice and now recommend creating only the necessary domains so as not to complicate the system and not overload it with additional security requirements. However, many still create AD forests with two or more domains and an unused root directory.

Fig. 1. Using an empty root domain
Domain as a security boundary
Earlier, Microsoft recommended avoiding the increase in the number of forests, since there were difficulties in terms of integrating them into each other in terms of security and administration. In addition, the Active Directory domain was considered a security frontier. This made it possible in the forest of two domains to easily separate the users and resources of domains A and B.
Then came a series of articles demonstrating how easy it is for an administrator of one domain to control the resources of another domain within the same forest, after which Microsoft changed its recommendations and urged that the forest, and not the domain, be considered the security boundary. If you want to isolate users or resources in a specific domain, you should build a separate forest. Thus, now organizations usually have many forests, for example, separate the development forest from the production forest, or even from a special Internet-oriented forest. As a result of this separation, companies faced difficulties in administering multiple forests.
Other recommendations have changed due to the development of AD itself. System improvements included delegation of access rights, reporting, expandability (in Windows 2000 there was a limit on 5000 group members), recoverability (snapshot function and recycle bin) and automation (AD administration on Microsoft PowerShell). The new approach has significantly improved the protection, management and recovery of Active Directory.
Administration Model Changes
Another area in which changes have occurred is the administration method. Previously, a small group of administrators was responsible for all aspects related to the system, from infrastructure to content that eventually ends up in the directory. With the growing importance of AD for the IT infrastructure, its administration model has become more complicated. Now in organizations, many people are involved in working with AD: one person is responsible for managing users, user groups and their properties, another for data related to applications, a third for security, etc. This necessitates improving the protection and separation of data in AD by applying a role-based approach to directory management, reviewing the structure, namely the distribution and protection of organizational units.
Changing the Role of AD
Previously, the role of Active Directory in most organizations was very modest. Ee was used to provide centralized login and security for Windows PC users, or as an alternative or to replace systems with Windows NT 4 Security Account Manager (SAM) or Novell NetWare. Over time, AD has become the focus of most events taking place in IT organizations (Fig. 2), providing such functions:
- authentication and authorization for non-Windows systems (for example, Linux servers, Mac desktops and laptops);
- Authentication and authorization across multiple platforms, such as Microsoft SharePoint websites, Java application servers, NAS (NAS), and administration tools like HP Integrated Lights-Out (iLO) or Integrated Dell Remote Access Controller (iDRAC );
- authorization of access to large arrays of corporate data (including sensitive data) through AD security groups;
- White pages for corporate catalogs and organizational charts;
- Authentication for applications located in the cloud using the software as a service (SaaS) model. This relatively new direction in the use of AD has led to a decrease in security and requires much more attention to infrastructure than the “set up and forget” approach used earlier in many IT departments when working with AD.

Fig. 2. Active Directory at the center of many IT resources.
In many organizations, AD has become a paramount element of the infrastructure, its security and management are given as much attention as most critical business platforms. In particular, organizations are developing a hybrid approach to the provision of IT services, in which one part of the applications is located in the company's data centers, and the other is stored “on the clouds” of external provider companies. Most often, these two environments are brought together by authentication and providing access through integration through AD. Without a well-protected and well-managed AD, a hybrid approach is more in the way of business than it helps.
Unfortunately, sometimes AD does not receive enough attention from IT staff. This has many manifestations, from insufficient attention to change management in AD, to the assumption that since "everything works this way, you can not strain." This approach does not benefit IT departments, since integration both in general and with cloud solutions plays a very important role.
Changes in the legislative framework
Since the first releases of Active Directory, the difficulties associated with ensuring that IT operates in accordance with current legislation have increased. Now organizations are dealing with many complex regulatory acts, and often it is AD that acts as the main tool for working with them.
The need for monitoring and reporting on the use of Active Directory has increased significantly. Compliance with regulatory acts and its maintenance at the proper level requires the use of more complex processes for managing AD and verifying related activities. Now it is simply unacceptable not to know who and why made each of the changes to the directory system. Ignoring AD-related activities could compromise the integrity of corporate data. Changes should not be allowed out of control, given the importance of this system in matters of authentication and authorization, as well as to ensure proper protection of the most sensitive data. A competent modern approach to managing AD is required to ensure compliance with regulations and security.
Key Steps in Upgrading AD
Many organizations have used Active Directory for many years without changes, so now the structure and practice of working with it require updating. Here are the main areas of application for modernization:
- restructuring AD;
- optimization of management and administration;
- protection of AD and its data;
- providing and maintaining system flexibility;
- ensuring availability and recoverability of AD;
- Implementation of AD guidelines.
Restructuring AD
Restructuring AD is becoming more common, it is a great way to remake the directory to the current and future needs of the organization. Simply changing organizational units can greatly affect the management and protection of AD. It so happened that the structure of organizational units focused on the structure of the business, for example, on the departments of the company or their geographical location. This approach did not always fit the rest of the catalog needs. For example, in the interests of group policy, you can divide user PCs into organizational units by the type of OS version used, as shown in Fig. 3, but if all PCs are part of the same IT group, this solution will complicate the delegation of rights and administration of the group.

Fig. 3. Organizational unit structure optimized for group policy instead of delegation.
The design of a modern catalog system is striving for a middle ground. To create such an AD structure, it is crucial to take into account the various needs of the organization.
The restructuring of AD itself can take several forms. Sometimes you need to reduce the number of domains and forests to improve data management and protection. In other situations, for security reasons, it may be necessary to split some resources into separate forests (we are talking about resources available to clients). Sometimes you just want to start all over again and build a beautiful AD structure, removing all unnecessary elements. This approach can be extremely inefficient, as it will require additional time to migrate users and resources from the old to the new AD environment.
For any reconstruction, AD will be useful to pay attention to the tools of various developers that will help make the move "painless." This is especially important when transferring data from a poorly documented system to a more structured one, since it is not always possible to predict the progress of the transfer.
Streamlining Management and Administration
Another area for improving AD is directory management and administration. Usually, the first thing they do is reduce the number of administrators with unlimited access throughout AD. The point is to create a less privileged management model in which administrators have access rights that only allow changes to parts of the system for which they are responsible. These sites may be:
- Infrastructure outside AD: servers and services that support it, for example, domain controllers, domain name system (DNS) and directory system schema;
- data inside AD: any data, from the properties of user accounts to the key groups to which users belong.
These areas have different models of delegation of rights. And if it is not very critical who controls the infrastructure elements of the system, then the data security model inside it is clearly of paramount importance. Therefore, you need to control the management of AD servers and their associated infrastructure, as well as the creation, reading, updating and deletion of data in AD itself.
Membership in AD groups can open access to everything from server administrator rights to financial data. Therefore, you need to carefully monitor access to these groups and regularly conduct certification of access rights.
Protecting Active Directory and its data
In terms of modernization, it is worth considering delegation - control over who can modify AD objects and their properties. This topic is closely related to ensuring that only authorized users modify objects in it. Too often, organizations provide access to solve immediate problems, and do not cancel it when it is no longer needed.
To manage delegation in Active Directory, you must create a role-based framework to provide access to its objects and their attributes. AD is currently creating role-based templates for each (or at least for each mission-critical) task that administrators must perform, for example, to change membership in privileged groups or change user attributes.
Achieving Compliance, Maintaining and Confirming
Once control over the data arriving in Active Directory has been achieved, you need to constantly check the actions performed on this data. Such audits must meet both internal (for the IT department) and external (for the audit organizations) requirements. Although Microsoft Windows Server and Active Directory initially had the ability to audit events that occurred, it can be practically meaningless, since in loaded environments it contains too much data and quickly overflows.
You must have a clear audit aggregator and the ability to analyze to identify unwanted changes, unauthorized use of AD and corporate resources, as well as tracking user activity across all IT systems. An audit of the system provides a history of changes associated with it and made within it, for example, the time it takes for users to enter the network and the most frequently launched applications.
After establishing control over changes in the entire IT environment, it is important to pay close attention to the critical tasks associated with AD, including changes to its infrastructure and data that can affect the integrity of the directory.
Using change control and auditing as feedback tools to track authorized and unauthorized changes, you can get a complete picture of the changes happening in AD. The latest version implements the possibility of such a review, thanks to which you can always see who and what has access.
Ensuring AD Availability and Resiliency
High availability is another aspect of today's use of Active Directory. Fortunately, AD can become a reliable and flexible part of the IT infrastructure if the work of all its other components is well-established, namely:
- AD Server Replication and Replication Topology
- Domain Name System (DNS);
- Microsoft file replication service
- virtual machine and hardware resources.
Most, if not all, of these tools can be monitored using standard or AD-specific monitoring tools. With the increasing role of AD in organizations, regular monitoring of its performance is becoming increasingly important. It may include the creation of synthetic transactions of typical AD operations, for example, authentication and search, which can confirm that AD servers respond to ping and that processes running on them proceed successfully.
In addition to monitoring availability, it is also important to have good backups and a disaster recovery plan. Now there are many tools for backup and recovery, including at the facility level, allowing you to restore everything from minor changes in the directory system to significant failures. There are three types of recovery associated with AD.

Table 1. Types of AD recovery
As more organizations have begun to use virtualization technology to launch the AD infrastructure, its recovery from failures is becoming more and more popular, and the collapse of an entire forest or server is now less common. Nevertheless, it is important to have a plan of action in the most undesirable situations and suitable tools for reforestation in a minimum of time.
Implementing AD Leadership
After upgrading your AD infrastructure, it is important to provide reliable management for smooth operation. Clear rules for using, expanding, and managing the system must be made You should also create a description of all the key components of AD that affect its operation.
Guidance should include the following elements:
- instructions for all types of data located in the system;
- Recommendations for expanding the AD schema: when and how it should be expanded, as well as when you can and should use existing attributes to store application-related data;
- recommendations for delegating rights in AD;
- recommendations for using security groups;
- standard tools, application programming interfaces (APIs) and ports used in AD;
- AD Querying Instructions.
This list of recommendations is just the tip of the iceberg. Active Directory Infrastructure Management must have well-documented standards of conduct in a variety of situations.
Conclusion
Over time, the role of Active Directory has grown dramatically and has become critical for many organizations. For the correct operation of the system, regardless of whether it is used for authentication and authorization of Windows PCs, Linux servers or Java applications, it is necessary to maintain high level of control, availability and efficiency, protection and audit.
By upgrading AD, you can achieve all of these criteria using both the latest versions of Windows Server and software from other developers. In any case, good management and protection are important for the smooth operation of Active Directory.
