ATM Raspberry Pi Attack
What they just don’t do with ATMs: they are torn out of the wall, tied with a cable to the car, drilled, blown up and cut ( sometimes in the State Duma building). According to EAST statistics , criminals are less likely to use skimming, preferring trapping and physical sabotage. Security professionals are also worried about another new trend - virus attacks on ATMs. Here and Trojan.Skimer, and Backdoor.Ploutus, and a completely fresh malware Tyupkin, and other "applications", known and not so. Malvar is loaded into the computer of the ATM, usually from external media, and is used for unauthorized payment of money or interception of card data. Another attack method was described by Positive Technologies experts Olga Kochetova and Alexei Osipov at a computer security conference.Black Hat Europe 2014 , held in October in Amsterdam.
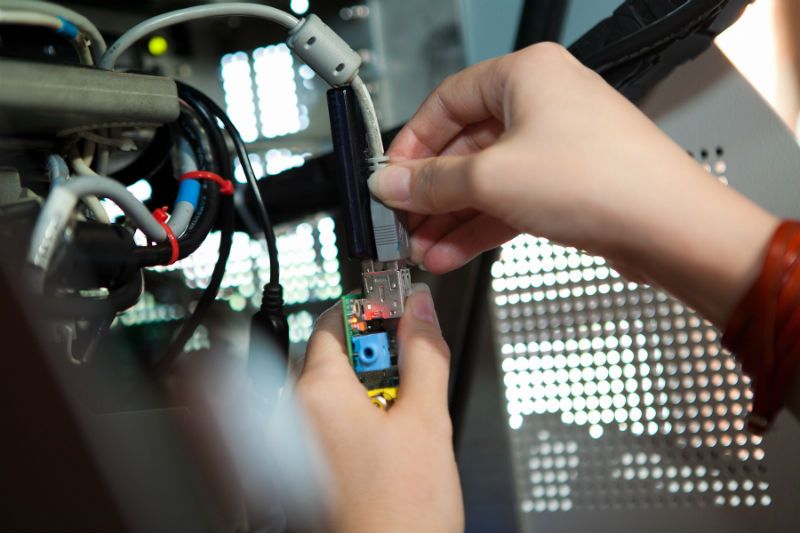
To test the security of the test ATM that survived the three Positive Hack Days forums, the popular miniature Raspberry Pi controller was chosen. The device easily hides inside the case and does not attract the attention of technical personnel, who, for example, change paper in built-in printers and therefore have the keys to the service area.
It’s not so difficult to find documentation describing the interfaces of ATMs, and Alexey Lukatsky wrote about this five years ago in his “Information Security Myths”. ATM equipment and payment terminals, regardless of manufacturer, have a common API for accessing and managing various modules and runs on the Windows platform in accordance with the unified standard of “extensions for financial services” (XFS).
Knowing the API, you can gain control over the host computer of the ATM and directly control various peripheral devices installed inside the ATM cabinet, such as a card reader, a keypad for entering a PIN code, a touch screen, a banknote dispenser, etc. Do not forget about operating system vulnerabilities ATM systems, and Windows has them in store for many years to come .
Weakness
Before installing the Raspberry Pi and connecting the device to the Ethernet, USB or RS-232 ports, you need to open the ATM. At the top of the ATM is a service area. This is where the computer that controls the ATM devices, network equipment (including poorly protected GSM / GPRS modems) is located. The service area is practically not controlled, as it is used by service personnel for various operations. To get access to it is much easier than to the safe with money located below. It can be opened with keys that are simple to manufacture or with very simple improvised means.
But just opening is not enough - you need to do it quickly and quietly.
At the Black Hat conference, Positive Technologies researchers demonstrated how long it would take for attackers to install the microcomputer in the ATM service area to use it as a sniffer — a PIN interceptor and a credit card number — or a hardware skimmer that does not leave marks on the appearance of an ATM. It took two minutes to unlock the ATM case, integrate the microcomputer, disguise it and connect it to the Internet.
In preparation for the performance, the Raspberry Pi was programmed to control ATM peripheral modules. A Wi-Fi adapter was connected to the microcomputer, to which you could connect from any device, for example, from a smartphone. Commands for dispensing money to the dispenser were sent through a specially implemented web interface. As an example, the issuance of several banknotes was shown, and after some refinement of the sent code, the ATM immediately parted with all the banknotes . By the way, in each cassette of a typical ATM, from two to three thousand notes are placed, and there are usually four of these cassettes for several denominations.

Needless to say, during the experiment, the ATM issued banknotes without leaving any entries in its computer, and although the built-in video camera of the ATM worked, but, like other devices inside the captured ATM, it was controlled using Raspberry Pi.
Is it possible to defend oneself
ATM security is not easy. Much depends on the attack scenario. For example, the Research Center “Protection” of the Ministry of Internal Affairs recommends that manufacturers use a smoke generator, an ultrasonic barrier and a xenon strobe, while British LINK experts prohibit standard locks for access to the service area and use webcams more actively.
However, the main problem, according to our researchers, is the ability to install any device or program into the ATM (up to Angry Birds), which is caused by an abundance of critical vulnerabilities in operating systems. The situation could be changed by the joint work of manufacturers of banking equipment on a new open specification that would ensure safe interaction and effective authentication of ATM components: so that anyone who wants to get the key to the service area could not easily connect anything to the system.
