When AES (☢) = ☠ - cryptobinary focus

Corkami's reverse engineering specialist Ange Albertini was jokingly asked whether it would be possible to generate a JPEG image that would again turn into a valid JPEG after processing with the AES cipher. Ange accepted the challenge , and based on the results of the study, published a presentation explaining how this is done with different formats.
“You don’t even need to know AES or JPEG, it’s too complicated,” Albertini writes. “We just play with Lego blocks.”
AES is a block cipher that completely changes the ciphertext as a result of changing at least one byte in the original text. It seems that there is no way to control the contents of the ciphertext.
A file of a certain format usually starts with a signature (for JPG the signature is \ xFF or \ xD8), after which several sections follow, among them there are necessary sections, and there are optional sections, followed by a file end marker. After the marker, you can add arbitrary content (junk).
A block cipher has several modes (CBC, OFB, CFD, etc.), for which parameter IV applies, which provides for the selection of external data for use in the encryption process. Although this data is assumed to be random, in practice, we can slip such data that fragment A at the beginning of the source text will always turn into fragment B in the ciphertext. Thus, we can control the contents of the first block, that is, the signature of the file format.
We can also use the decrypt function to decrypt arbitrary text. If we need a ciphertext of a certain type (a certain picture), then we simply decrypt it first with the X key, and then we will encrypt the result with the same X key to get the desired text. We will embed this data in junk after the end of file marker.
The action algorithm looks something like this.
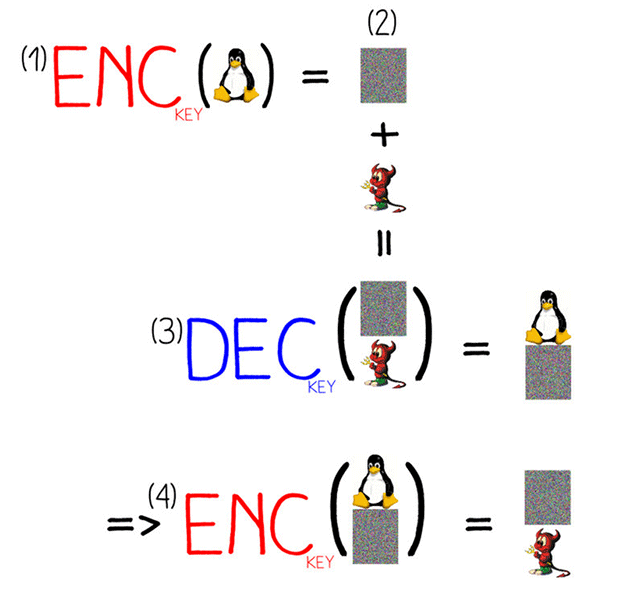
Albertini managed to encrypt PDF to PDF and JPG to JPG, PNG to PNG and FLV to FLV, as well as ZIP to PNG using this method. See relevant file examples and code here .
