Abstract on the materials of the course ICND1 100-101
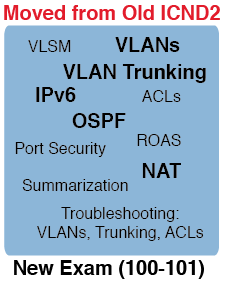
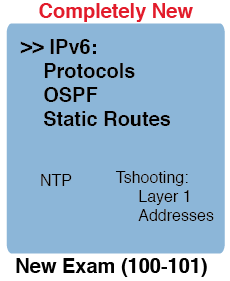

Based on the results of the survey, I publish a compendium based on the materials of the ICND1 100-101 course.
What topics are there: the TCP / IP network model, OSI model, Ethernet (cable types), HDLC. By IPv4 addressing: class networks, private addresses, network traffic transfer methods. VLANs, CDP, comparison of routing protocols, NAT, IPv6, ACLs. Very briefly, mainly data here, and not an explanation of the principles of work.
There is not much: explanations of the operation and configuration of routing protocols, switching in networks, explanations, for example, how to determine whether the IP address belongs to a particular subnet (such questions are often encountered), there are no classless networks, VLSM, IOS, troubleshooting in the network (troubleshooting).
TCP / IP Network Model
| TCP / IP original | TCP / IP updated | Protocol Examples | Package Name |
| Application | Application | HTTP, POP3, SMTP | |
| Transport | Transport | TCP, UDP | Segment (UDP - Datagram) |
| Internet | Network | IP | Packet |
| Link | Data link | Ethernet, Point-to-Point Protocol (PPP), T1 | Frame |
| Physical |
| Level name | Protocols | Devices |
| Application (L7) | Telnet, HTTP, FTP, SMTP, POP3, VoIP, SNMP | Hosts, Firewalls |
| Presentation (L6) | ||
| Session (L5) | ||
| Transport (L4) | TCP, UDP | Hosts, Firewalls |
| Network (L3) | IP | Router |
| Data Link (L2) | Ethernet (IEEE 802.3), HDLC | LAN switch, wireless access point, cable modem, DSL modem |
| Physical (L1) | RJ-45, Ethernet (IEEE 802.3) | LAN hub, LAN repeater, cables |
(Please do not take pizzas with sausages with you).
Ethernet technology, medium and maximum segment length
| Ethernet | Cable type | Maximum length, m. |
| 10 BASE-T | UTP CAT3 or better, 2 pairs | 100 |
| 100 BASE-TX | UTP CAT5 or better, 2 pairs | 100 |
| 100 BASE-FX | Multimode fiber | 400 |
| 1000 BASE-CX | STP | 25 |
| 1000 BASE-T | UTP CAT5e or better, | 100 |
| 1000 BASE-SX | Multimode fiber | 275, 550 |
| 1000 BASE-LX | Multimode fiber | 550 |
| 1000 BASE-LX | Singlemode fiber | 10000 (in the book for exam 100-101, 5 km are indicated. - a lot of them) |
| Transmits on Pins 1.2 | Transmits on Pins 3.6 |
| PC NICs | Hubs |
| Routers | Switchesches |
| Wireless Access Point (Ethernet interface) | - |
If there is no auto-negotiation, according to the IEEE standard, the duplex transmission parameters are selected as follows:
- If the speed is 10 or 100 Mbps, then half-duplex transmission is used
- If the speed is 1000 Mbps, then duplex transmission is used.
Interfaces operating at speeds above 1 Gbit / s always use duplex transmission.
When using duplex transmission, there are no collisions.
WANs
HDLCOne of the data link layer control protocols in High-Level Data Link Control is a high-level data link control protocol.
By modifying the standard protocol specification, Cisco created a proprietary version of it by adding the Protocol Type field to identify the type of packet contained within the frame:
Bytes
| 1 | 1 | 1 | 2 | Var | 2 |
| Flag | Address | Control | Type | Data | FCS |
IPv4 Addressing
Class networks| Class | First octet range | Valid Network Numbers | Hosts per network | Number of networks |
| reserved | 0 | |||
| A | 1 - 126 | 1.0.0.0 - 126.0.0.0 | 16 777 214 | 126 |
| reserved | 127 | |||
| B | 128 - 191 | 128.0.0.0 - 191.255.0.0 | 65,534 | 16 384 |
| C | 192 - 223 | 192.0.0.0 - 223.255.255.0 | 254 | 2 097 152 |
| D (multicast) | 224 - 239 | |||
| E (experimental) | 240 - 255 |
| Address class | Reserved Address Space |
| A | 10.0.0.0 through 10.255.255.255 |
| B | 172.16.0.0 through 172.31.255.255 |
| C | 192.168.0.0 through 192.168.255.255 |
Unicast traffic (single-purpose packet transmission) is used primarily for services of a "personal" nature. Each subscriber can request personal video content at any time convenient for him.
Broadcast traffic (broadcast packet transmission) uses a special IP address to send the same data stream to all subscribers of a given IP network. For example, such an IP address can end in 255, for example 192.0.2.255, or have 255 in all four fields (255.255.255.255).
Multicasttraffic (multicast packet transmission) is used to transmit video streaming when it is necessary to deliver video content to an unlimited number of subscribers without overloading the network. This is the most commonly used type of data transmission in IPTV networks when a large number of subscribers watch the same program. Multicast traffic uses a special class of destination IP addresses, for example, addresses in the range 224.0.0.0 - 239.255.255.255. These can be class D IP addresses.
Applications, their port numbers, and protocols
| Port number | Protocol | application |
| 20 | TCP | FTP data |
| 21 | TCP | FTP control |
| 22 | TCP | Ssh |
| 23 | TCP | Telnet |
| 25 | TCP | SMTP |
| 53 | UDP, TCP | DNS |
| 67, 68 | UDP | DHCP |
| 69 | UDP | TFTP |
| 80 | TCP | HTTP (WWW) |
| 110 | TCP | Pop3 |
| 161 | UDP | SNMP |
| 443 | TCP | SSL |
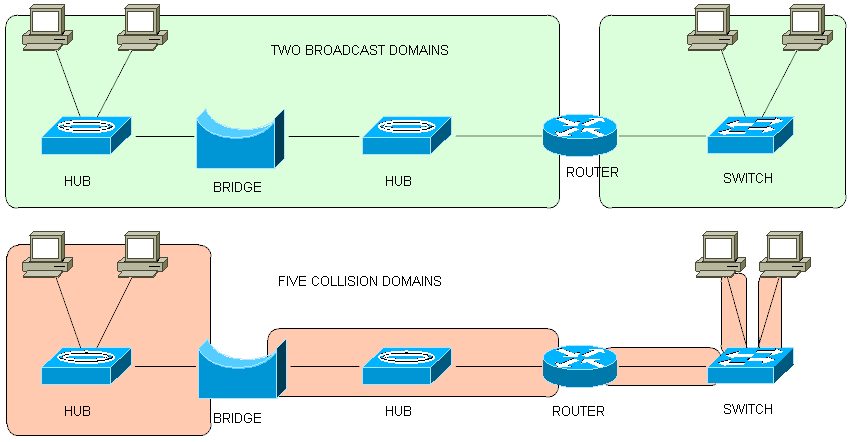
Cisco 2960 Catalyst. Switch LEDs
| room | Title | Description |
| 1 | SYST (system) | General state of the system (green - the power is on and the switch is functioning normally, IOS is loaded, orange - POST (Power on Self Test) has ended with errors and IOS has not been booted, not lit - the power is off) |
| 2 | RPS (redundant Power Supply) | Auxiliary power supply status |
| 3 | STAT (status) | The status for each port (blinks green - the connection is working, data is being transmitted through the interface, lights up green - the connection is working, but the data is not transmitted, blinks orange - the interface is administratively down or was dynamically disconnected for some reason, turned off - the connection is not working) |
| 4 | DUPLX (duplex) | Lights up green - the port is operating in full duplex mode; off - in half duplex mode |
| 5 | Speed | Flashing green - 1 Gb / s, Steady green - 100 Mb / s, Off - 10 Mb / s |
| 6 | Mode | Mode button |
| 7 | Port | The indicators indicate different states depending on which mode is selected by the Mode button. |
| RAM (Working Memory and Running Configuration) | Flash (Cisco IOS Software) | ROM (Bootstrap Program) | NVRAM (Startup Configuration) |
Virtual LANs
In a local network, all devices are in the same broadcast domain.Trunking protocols
- ISL (Inter-Switch Link). The protocol was created by Cisco many years before the IEEE organization developed its own. The protocol provides for the encapsulation of each source Ethernet frame in the ISL header and trailer. Currently, some modern devices no longer support this protocol. (Cisco Catalyst 2960).
- 802.1Q. Designed by IEEE. Both protocols tag each VLAN ID frame. But the 802.1Q protocol does not encapsulate the original frame. Instead, you can insert a 4-byte additional VLAN header into the Ethernet header of the original frame.
| DA | SA | Tag | Type | Data | FCS |
| Type | Priority | Flag | VLAN ID (12 bits) |
VLAN IDs:
1-1005 - normal range1006 - 4094 - extended range
802.1Q does not add a header to frames in its own (native) VLAN.
Both protocols support multiple instances of STP.
Trunking Administrative Mode Options (parameters of the administrative mode of the trunk connection, determined using the switchport mode command)
| Options | Description |
| access | Prevents the use of a trunk connection. The port always acts as a non-trunk (in network access mode) |
| trunk | Trunk always used |
| dynamic desirable | Initiates the transmission of channel mode negotiation messages and responses to negotiation messages in order to dynamically determine whether to start using a trunk connection, and also defines encapsulation in a trunk connection |
| dynamic auto | Passively awaiting receipt of a message for negotiation of a trunk connection, after which the switch responds and negotiates whether to use a trunk connection, and in the case of a positive response, negotiates the type of trunk connection |
| Access | Dynamic auto | Trunk | Dynamic desirable | |
| Access | Access | Access | Do not use | Access |
| Dynamic auto | Access | Access | Trunk | Trunk |
| Trunk | Do not use | Trunk | Trunk | Trunk |
| Dynamic desirable | Access | Trunk | Trunk | Trunk |
Cisco's Device Discovery Protocol can be a useful tool for checking the information in the network diagram, as well as filling in missing information about devices and network topology. Show cdp
group commands
| Command | Description |
| show cdp neighbors [type number] | Displays one summary line with information about each neighboring device or only about the neighboring device that is connected to a specific interface, if this interface is specified |
| show cdp neighbors detail | Displays a large amount of information about each neighboring device (approximately 15 lines), presenting each neighboring device separately |
| show cdp entry name | Displays the same information as show cdp neighbors detail, but only for one specified neighboring device (case-sensitive) |
| Line status | Protocol Status | Interface Status | Cause |
| Administrativerative down | Down | disabled | The shutdown command is applied on the interface |
| Down | Down | notconnect | The cable is not connected, faulty, the pinout is incorrect, device speeds do not match, the device at the other end of the cable is turned off or its interface is stopped (power-off, shutdown, err-disabled) |
| Up | Down | notconnect | Practically not found |
| Down | Down (err-disabled) | err-disabled | The interface is blocked using Port security has disabled the interface |
| Up | Up | connected | Works |
| Violation Mode | Destruction of non-compliant traffic | Destruction of all traffic after violation occurs | Setting the interface to err-disabled as a result of violation | Increase in counter values in connection with the detection of each new violation |
| shutdown | Yes | Yes | Yes | Yes |
| restrict | Yes | Not | Not | Yes |
| protect | Yes | Not | Not | Not |
internal (IGP) - Internal Gateway Protocols - used inside one autonomous system (AS - autonomous system, network under a single administrative control belonging to one organization)
external (EGP) - Exterior Gateway Protocols - used between autonomous Systems
IGP Routing Protocol Algorithms
- distance-vector (Bellman-Ford) (DV)
- taking into account the state of the channel (link-state, LS)
- balanced hybrid (extended distance vector)
IGP Protocol Comparison
| Property | Rip-1 | Rip-2 | EIGRP | OSPF | IS-IS |
| Classless, supports VLSM masks, forwards the mask in route announcements | Not | Yes | Yes | Yes | Yes |
| Algorithm | DV | DV | advanced DV | LS | LS |
| Supports manual summation | Not | Yes | Yes | Yes | Yes |
| Branded | Not | Not | Yes (but RFC came out in 2013) | Not | Not |
| Routing table updates are forwarded to the multicast address | Not | Yes | Yes | Yes | - |
| Convergence | Slow | Slow | Quickly | Quickly | Quickly |
| IGP | Metrics | Description |
| Rip-2 | Hop count | The number of routers (transit devices) between this router and the destination network |
| OSPF | Cost | The sum of the costs of all channels along the packet route, usually based on the bandwidth value |
| EIGRP | Composite bandwidth and delay | It is calculated based on the bandwidth of the “slowest” channel on the route and cumulative delay for such a route |
| Characteristic | Rip-2 | OSPF | EIGRP |
| Metrics | Hop count | Cost | Composite bandwidth and delay |
| Does periodic route announcements | Yes (every 30 sec.) | Not | Not |
| Full or partial announcements are sent | Full | Partial | Partial |
| Destination of routing announcements | 224.0.0.9 | 224.0.0.5 and 224.0.0.6 | 224.0.0.10 |
| Maximum metric value (“infinite metric”) | 16 | 2 ^ 24 - 1 | 2 ^ 32 - 1 |
| Is load balancing supported on non-equal channels (i.e. channels with different metrics) | Not | Not | Yes |
| Route type | Administrative distance |
| Connected | 0 |
| Static | 1 |
| BGP (external routes) | 20 |
| EIGRP (internal routes) | 90 |
| IGRP | 100 |
| OSPF | 110 |
| IS-IS | 115 |
| Rip | 120 |
| EIGRP (external routes) | 170 |
| BGP (internal routes) | 200 |
| Unusable | 255 |
Списки управления доступом
Типы списков
Standard Numbered ACLs (1-99) – стандартные нумерованные
Extended Numbered ACLs (100-199) – расширенные нумерованные
Additional ACL Numbers (1300-1999 standard, 2000-2699 extended) — дополнительные
Named ACLs – именованные
Improved Editing with Sequence Numbers – расширенное редактирование с порядковыми номерами
Стандартные списки управления доступом
access-list access-list-number {deny | permit} source [source-wildcard]
Standard lists should be located near the receiver of packages, so as not to accidentally drop the necessary packages.
Standard lists allow checking only the sender address in a packet.
The list is searched sequentially, the packet is processed according to the first matching rule (first-match logic).
The default action if the package is not matched to any of the list commands is a ban.
Using the access control list on the selected interface of the router taking into account the desired direction using the interface configuration mode command:
ip access-group number {in | out}
Advanced access control lists
Fields that can only be checked using extended lists: recipient IP address, portions of the recipient IP address specified with an inverted mask, protocol type, sender port, recipient port, TCP streams, TOS bytes over IP, priority IP packet.
The access-list command should use the tcp keyword to check TCP port numbers, udp to check UDP port numbers. The ip keyword does not provide port number verification.
Parameters indicating the port of the sender and receiver are positional. Their location in the command determines whether the parameter is used to check the port of the sender or recipient:
packet filtering based on the port number of the recipient
access-list 101 permit tcp 172.16.1.0 0.0.0.255 172.16.3.0 0.0.0.255 eq 21
packet filtering based on sender port number
access-list 101 permit tcp 172.16.3.0 0.0.0.255 eq 21 172.16.1.0 0.0.0.255
access-list access-list-number {deny | permit}
{tcp | udp} source source-wildcard [operator [port]] destination destination-wildcard [operator [port]] [established] [log]
Extended lists should be placed as close to the sender as possible.
Named Lists A
command for configuring a named standard or advanced access control list with switching to access control list configuration mode
ip access-list {standard | extended} name
Access control list configuration mode command to enter information about mapping criteria and actions related to a named access control list that maps to TCP segments
{deny | permit} source [source wildcard] [log]
{deny | permit} tcp source source-wildcard [operator [port]] destination destination-wildcard [operator [port]] [log]
Editing ACLs using sequence numbers
Deleting a row with sequence number 20:
no 20
Insert a new first line with number 5:
5 deny 10.0.0.1
Before making changes to the access control list, delete it in the interface in which it is set ( no ip access-group ).
If the lists are created in a text editor (as recommended), then it may be convenient to start each file with the no access-list number command, followed by the configuration commands in the access control list. In this case, after each editing of the file, it is enough to copy and paste the contents of the entire file, using the first line, the entire existing access control list will be deleted, and the remaining instructions will recreate the new list.
NAT Network Address Translation. Network Address Translation
NAT Addressing Terms
| Term | Value |
| Inside local | IP Address Assigned to a Host on a Private Enterprise Network |
| Inside global | To represent an internal node when a packet is forwarded through an external network. The NAT router changes the sender address in the packet from internal local to internal global. |
| Outside global | The real IP address assigned to a node located outside the enterprise network, usually on the Internet. |
| Outside local | NAT can translate external IP addresses. When a NAT router forwards a packet from the internal network to the external, using NAT to change the external address, the IP address representing the external host as the destination IP address in the packet header is called the external local address. |
Translation NAT (PAT) Congestion Allows NAT translation to support multiple clients with just a few public IP addresses.
NAT dynamic translation table with congestion
| Inside local | Inside global |
| 10.1.1.1:1024 | 200.1.1.2:1024 |
| 10.1.1.2:1024 | 200.1.1.2:1025 |
| 10.1.1.3:1025 | 200.1.1.2:1026 |
1. Using an Interface Subcommand
ip nat inside
2. Using the interface subcommand
ip nat outside
3. Configure static transformations using the global configuration command
ip nat inside source static inside-local inside-global
Configuring dynamic address translation
1. Using an interface subcommand
ip nat inside
2. Using the interface subcommand
ip nat outside
3. Configure the ACL corresponding to packets arriving at the internal interfaces for which NAT translation should be applied.
4. Using the global configuration command, set the pool of registered addresses:
ip nat pool name first-address last-address mask subnet-maskip nat source list acl-number pool pool-name
Configuring NAT Congestion (PAT)
Same steps as in p. 1-4 to configure dynamic translation
5. ip nat source list acl-number interface type number overload
IPv6
IPv6 Routing Protocols| Routing protocol | Defined | Remarks |
| RIPng (RIP Next Generation) | RFC | Reference to “Star Trek: the Next Generation.” |
| OSPFv3 (OSPF version 3) | RFC | IPv4 uses OSPFv2 |
| EIGRPv6 (EIGRP for IPv6) | Cisco | Cisco owns EIGRP rights, but also publishes it as informational RFCs |
| MP BGP-4 (Multiprotocol BGP version 4) | RFC | BGP version 4 was created highly extensible, IPv6 support was added as an addition to MP BGP-4 |
| A type | First hexadecimal character |
| Global unicast | 2 or 3 |
| Unique local | Fd |
| Multicast | Ff |
| Link-local | FE80 |
| Set by IANA, RIR or ISP (P bits) | Set by Local Engineer (S bits) | (I bits) |
| Global routing prefix | Subnet | Interface id |
Пример: 2001:DB8:1111:4::1
Unique Local Unicast
| 8 bits | 40 bits | 16 bits | 64 bits |
| Fd | Global ID (Pseudo-Random) | Subnet | Interface id |
| Subnet id | |||
Пример: FD00:1:1:0001::1
Link-local
| 10 bits | 54 bits | 64 bits |
| FE80 / 101111111010 | All 0 | Interface id |
| Use of address | IPv6 | IPv4 |
| All channel IP nodes | FF02 :: 1 | Broadcast Subnet Address |
| All channel routers | FF02 :: 2 | Not |
| OSPF Messages | FF02 :: 5, FF02 :: 6 | 224.0.0.5, 224.0.0.6 |
| RIP Messages (Version 2 and NG) | FF02 :: 9 | 224.0.0.9 |
| Сообщения протокола EIGRP | FF02::A | 224.0.0.10 |
| Агенты пересылки протокола DHCP (маршрутизаторы, осуществляющие пересылку служебных сообщений серверу DHCP) | FF02::1:2 | Нет |
::1 (аналог 127.0.0.1)Формат адреса с идентификатором интерфейса и EUI-64
:: (unknown, все нули)
| 48 bits | 16 bits | 64 bits | ||
| Subnet Prefix | Subnet | Interface ID | ||
| 1st Half of MAC Invert 7th Bit, 1st Byte (Reading Left to Right) | FFFE | 2nd Half of MAC | ||
| Defined by Configuration | Calculated by Router Using EUI-64 | |||
1. Odom U. CCENT / CCNA ICND1 100-101 Official Cert Guide, 2013
2. Odom U. Official Guide to Preparing for the Certification Exams CCENT / CCNA ICND1, 2nd ed .: Per. from English - M .: LLC “I.D. Williams, 2009, i.e. this is to the old 640-822,
3. Odom U. Official Guide to Preparing for the Certification Exams CCNA ICND2, 2nd ed .: Per. from English - M .: LLC “I.D. Williams, 2009, i.e. this is to the old 640-816 and 640-802,
4. Laemmle T. CCNA Cisco Certified Network Associate, Study Guide, 7th edition, 2011
5. Transmission of Unicast, Broadcast and Multicast traffic.
6. KDPV taken from here
Useful links:
Expand
1. Networks for the smallest
2. Brief notes on Cisco CCNA (part of ICND1)
3. Missing (top 10 useful commands that did not fall into the CCNA course)
4. GNS3 1.0 beta Early Release is now available to everyone
5. Preparing yourself for CCNA: practical tips
6. Step-by-step instruction “How to pass the Cisco exam?”
7. Do you know static routing well?
2. Brief notes on Cisco CCNA (part of ICND1)
3. Missing (top 10 useful commands that did not fall into the CCNA course)
4. GNS3 1.0 beta Early Release is now available to everyone
5. Preparing yourself for CCNA: practical tips
6. Step-by-step instruction “How to pass the Cisco exam?”
7. Do you know static routing well?
