4G Security: Capturing USB Modem and SIM Card via SMS

Telecom operators are actively promoting fast and cheap 4G communications. But only a few know how protected it is. Positive Technologies experts in the process of researching the security of 4G communications managed to find vulnerabilities in USB modems that allow taking control of the computer to which the modem is connected, as well as the subscriber’s account on the mobile operator’s portal. In addition, attacks on the SIM card using binary SMS allow you to intercept and decrypt the subscriber’s traffic, or simply block the specified SIM card.
Reports on the results of the study were presented in November at the ZeroNights conference in Moscow (Kirill Nesterov, Alexey Osipov, Timur Yunusov) and the PacSec conferencein Tokyo (Sergey Gordeychik, Alexander Zaitsev). In this publication, we summarize the main ideas of the study, which also involved Dmitry Sklyarov, Gleb Gritsay, Dmitry Kurbatov, Sergey Puzankov and Pavel Novikov.
A few words about the objectives of this work. It’s not just about the security of trendy smartphones, through which we read our friends on social networks. GSM digital mobile communications are now used in many critical infrastructures, including industrial control systems (SCADA). Another example from everyday life that no one would like to meet with is the theft of money from bank accounts. Meanwhile, many probably saw such small antennas at ATMs - here, too, GSM:

A modern modem for wireless communication is a computer on which a well-known operating system (usually Linux or Android) is installed and a number of special applications with sufficiently wide capabilities. There are vulnerabilities in this software and data transfer protocols that have already been exploited in recent years - for example, to unlock the modem and untie it from the operator. One of the protection against such hacking was the transfer of many services to the Web - however, this provided only new opportunities for attacks.
For our study, we took six different lines of USB modems with 30 different firmware. Looking ahead - only three firmware failed to be cracked.
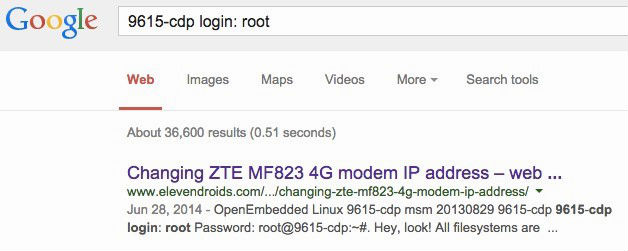
What did you manage to do with the rest? First, we identify the "piece of iron." The documentation and search engines help us with this. In some cases, Google helps even more - you can immediately find the password for telnet access:
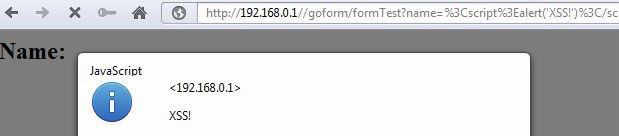
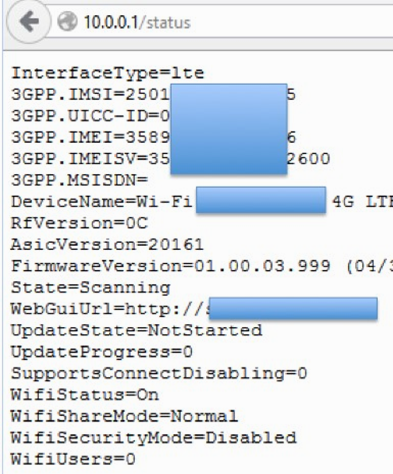
However, for external communications we do not need telnet, but http. We connect the modem to the computer and study it as a separate network node with web applications. We find the possibility of an attack through the browser (CSRF, XSS, RCE). In this way, we make the modem tell us about itself various useful data:
In addition to revealing data, on the attacked modem you can:
- Change DNS settings (which allows you to intercept traffic);
- Change the settings of the SMS center (SMS interception or manipulation);
- Change the password on the self-service portal via SMS (which allows you to withdraw money from your account by subscribing to a third-party service);
- Block the modem by typing the wrong PIN and PUK codes;
- Remotely “update” the modem firmware.
You can develop an attack and further - get to the computer to which the USB modem is connected. One of the options for such an attack: a USB keyboard driver is installed on the captured modem, after which the computer perceives the modem as an input device. From this “imaginary keyboard” a reboot command is sent to the computer from an external drive, the role of which is played by the same modem. Thus, a bootkit can be installed on the “mother” computer, allowing you to remotely control the computer. How it works, you can watch the video:
The best thing a user can do to protect against such attacks is not to stuff anything into their USB ports. Understanding at the same time that even USB-modems, which from the outside seem to be just a small and harmless communication device, belong to the expression “what’s horrible”.
The second part of our study concerned SIM cards. The fact that Simka itself is also a computer with its own OS, file system and multifunctional applications has been demonstrated by many other researchers. So, in May this year, at the Positive Hack Days conference, encryption specialist Karsten Noel showed that SIM cards (TARS) are protected in different ways. Some can be hacked by selecting DES-keys, and some respond to external commands without any protection at all - and tell a lot about themselves.
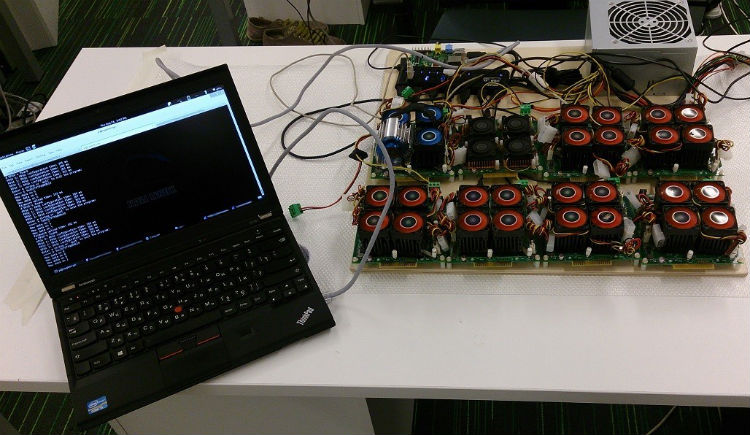
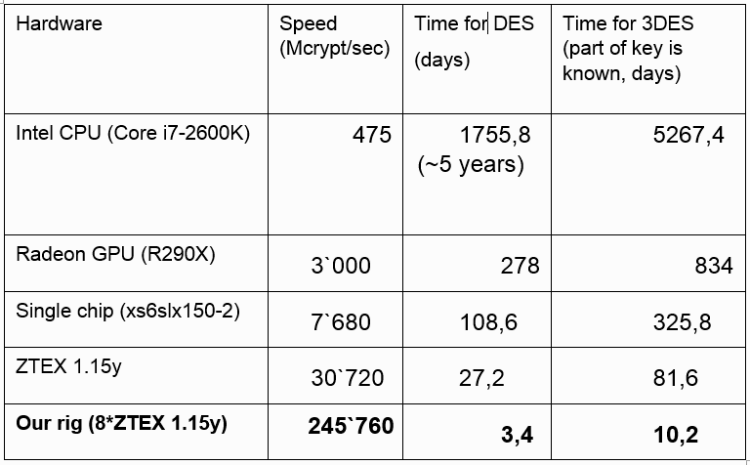
To select the keys in our study, we used a set of programmable gate arrays (FPGAs), which came into fashion a couple of years ago for mining the digital currency Bitcoin, and after the fall in popularity of this entertainment, they became much cheaper. Our board of eight modules * ZTEX 1.15y for 2 thousand euros counts at a speed of 245.760 Mcrypt / sec, which allows you to pick up a DES key in 3 days.
After that, we can send commands to famous TARs and manage them. In particular, the card manager Card manager allows us to upload our java application to SIM card.
Another interesting TAR is the File system, where TMSI (mobile phone identifier on the mobile network) and Kc (traffic encryption key) are stored. Access to them allows us using binary SMS:
- Decrypt subscriber traffic without key selection;
- Change subscriber (receive his calls and SMS);
- Track subscriber movements;
- If there is a PIN code protecting the file system, you can block the subscriber (three incorrect PIN codes and 10 incorrect PUK codes, after which the card is blocked).
In conclusion - a simple statistic. In this study, more than a hundred SIM cards of various operators were used. The described vulnerabilities are affected by 20% of them, that is, every fifth SIM card.
At the same time, it is hardly possible to give any protection tips for end users: attacks occur at a rather low technical level, so manufacturers of SIM cards and operators should solve security issues here. The Western IT press, by the way, already describes this study in the news as "the possibility of breaking into millions of SIM cards and USB modems ."
PS This was not the only study of Positive Technologies experts presented at ZeroNights'14. At the same conference, Artem Shishkin and Mark Ermolov talked about mechanisms for bypassing the Windows PatchGuard protection system in Windows 8: some details of the study can be found here , details will be presented in one of our next posts.
