CryptoBot ransomware virus passes its victims via Twitter
Ransomware viruses that encrypt user files, requiring money for decryption, have been terrorizing the Internet for years. However, this October they raged in earnest - obviously, having made a new evolutionary leap in the field of automation. At the beginning of the month, employees of the largest Australian broadcaster ABC, as well as postal and other public services of the country, were subjected to massive cryptolocker infection. In the middle of the month, more than 100,000 Americans were infected with a cryptographic virus through advertising banners that appeared on YouTube videos.
Well, in the last days of October there was an activation of a dangerous ransomware in the Russian segment of the Internet. Users receive a malicious file in the mail, which is 2.5 kb obfuscated JavaScript (MD5 ea834605f6bee2d4680aae0936655a30). When launched, the trojan downloads from the Internet and launches additional components:
The virus description is present on Virustotal , the deobfuscated version of the script is also given in the comments. You may notice that the file was repeatedly uploaded to the resource on October 29 and 30, 2014:
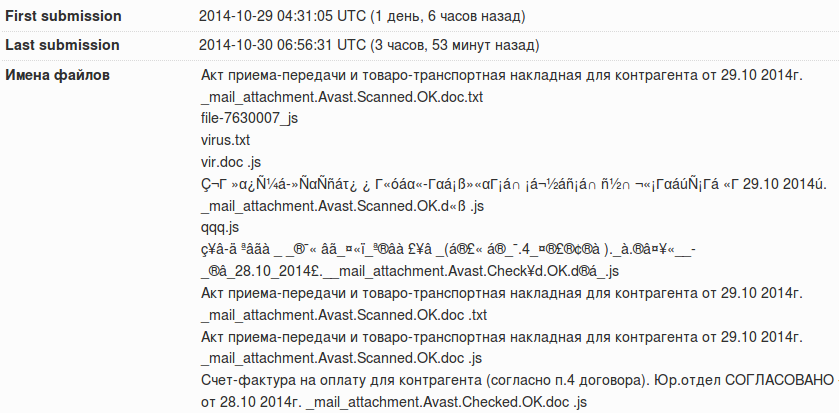
But here are the names of the infected files that come in the mail - basically they represent business documents, moreover, supposedly checked by antivirus (Avast.Scanned.OK)
After the user opens the attached file and launches a malicious script, he is informed that his documents, photos, databases, and other important files “were encrypted using the cryptographic algorithm RSA-1024”.

Next, the user is offered detailed instructions for saving their digital assets, which boils down to the following set of actions:
- Your files are encrypted. Send us an email with KEY and UNIQUE within 24 hours.
- We found KEY.PRIVATE and UNIQUE.KEY on our PC, took a couple of encrypted files - sent them to paycrypt@gmail.com
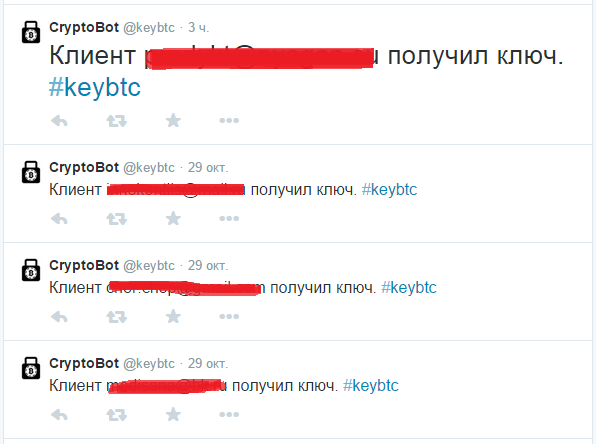
- After a while, you get an answer with guarantees, instructions and cost. Visit our twitter. See that everyone gets the keys. After payment you will receive a decryption key, software and decryption instructions.
The most interesting in this instruction is paragraph 3, which indicates a Twitter account that publicly discloses information about the email addresses of the victims of the attacks. This not only allows monetization to continue (for example, by sending spam to the addresses of victims, some of which indicated business email addresses), but can also significantly damage the reputation of the victims.
In particular, some researchers have already begun analyzing the list of victims - among them there were many IT companies, including those that themselves are involved in information security.
As in most email attacks, in this case we used versions of malware that at the time of the attack were not detected by most antiviruses. In this regard, Positive Technologies experts advise against opening letters with obscure attachments - even from familiar recipients. And at the infrastructure level, in addition to anti-virus solutions, it is recommended to use specialized sandboxes to check incoming mail, as well as restrict the receipt of mail attachments containing executable code, including in archives.
