A short story about BlackHat Europe 2014

Last week, one of the landmark annual events in the world of practical information security ended - BlackHat Europe 2014. About how it went, what I remember, and a couple of photos - under the cut.
If BlackHat USA is traditionally held in Las Vegas, it is hard to imagine a place for holding a conference in Europe than a cozy capital of freedom of morals and unshakable cultural values. This year was no exception, and BlackHat Europe was held in the glorious city of Amsterdam, within the walls of the Amsterdam RAI conference center.
The conference is divided into two parts: the first two days are trainings, and two more days are allotted to the most interesting.
This time we had nothing to do with the trainings, so we will mainly focus on the remembered moments during the two days of reports.

The first day as a keynote was discovered by a living legend of modern cryptography and infosec in general - Adi Shamir (for a second, he is still an “S” in the familiar RSA abbreviation).
Usually, keynote-reports are built around general analytics of processes occurring in a particular area, global trends and fashion trends.
But Professor Shamir, after a short excursion into the history of high-profile hacks of various cryptosystems and the history of personal achievements (and these two stories overlap in many respects), recalling the recent leak of NSA toolkit descriptions and one of his last works , he went directly to the story of a curious concept of a two-way channel interactions.

Given:
- An ordinary-looking multi-storey building with an ordinary office infrastructure functioning inside.
- The building is completely isolated from the outside world, no communication lines and even its own internal energy supply.
- Inside, entered in some way, there is Trojan software.

A recipe was suggested in the best traditions of spy movies and paranoid nightmares. As a communicating element, an ordinary multifunctional network device was chosen (one of those that print, scan and manage through the network). Namely, for the delivery of information to the building, a scanning process was initiated, and from a distance of a kilometer or less, the room in which the MFP was located was illuminated with a powerful laser that encodes bits of information, respectively, by radiation and pauses between flashes.
The cunning malware could easily decode the striped image resulting from scanning in a room with such a laser strobe. The return channel was implemented by the same scanner by starting and stopping the scanning process and registering radiation from the lamp using a quadcopter camera hovering in front of the building.
As a result, the report was saturated with all kinds of technological tricks and saturated with the hacker spirit by 100%, which set a very cheerful mood for the speakers who followed it.
Then Jose Selvi toldabout the technique of circumventing HSTS in MitM conditions by substituting responses from the NTP server and “rewinding” the time on the client host forward, up to the expiration of the period during which the browser is required to use a secure connection. In principle, the vector lay on the surface, and there is not much new in NTP-spoofing, but the author presented a demo of a working NTP-spoofer (and it is always nice to see a working combat tool). And, among other things, he provided some information on how NTP clients in various operating systems behave. On Windows, it turned out to be the most secure implementation against this type of attack.

Following us was a reportfrom Alberto Garcia Illera and Javier Vazquez Vidal - crazy dudes from Spain. Alberto was previously seen talking about the weaknesses of the transport systems on Zeronights 0x02. This time, he and his colleague gutted a smart electricity meter and demonstrated the vulnerabilities of the embedded platform on which it was built, and the architectural weaknesses of the networks that integrate such devices with which attackers can potentially compromise the entire energy metering system and, of course, not to pay the bills. The report was full of technical details about the rich inner world of the smart counter and contained all the components of a classic hackstory: the process of reverse engineering an unknown piece of iron, bypassing factory methods of protection, dumping and subsequent reverse and modification of firmware.
The afternoon was marked by the coolest report from Balint Seeber about SDR in general and specific cases of using Software Defined Radio for good and fun for the sake of. From games with RDS, ADS-B, paging systems and radio buttons on tables in restaurants to such crazy things as establishing communications and programming a spacecraft that has been hanging in orbit for 15 years . Balint is a visualization specialist, SDR fan and evangelist at Ettus, one of the very enthusiasts who, using the cup of a radio telescope, created this miracle.
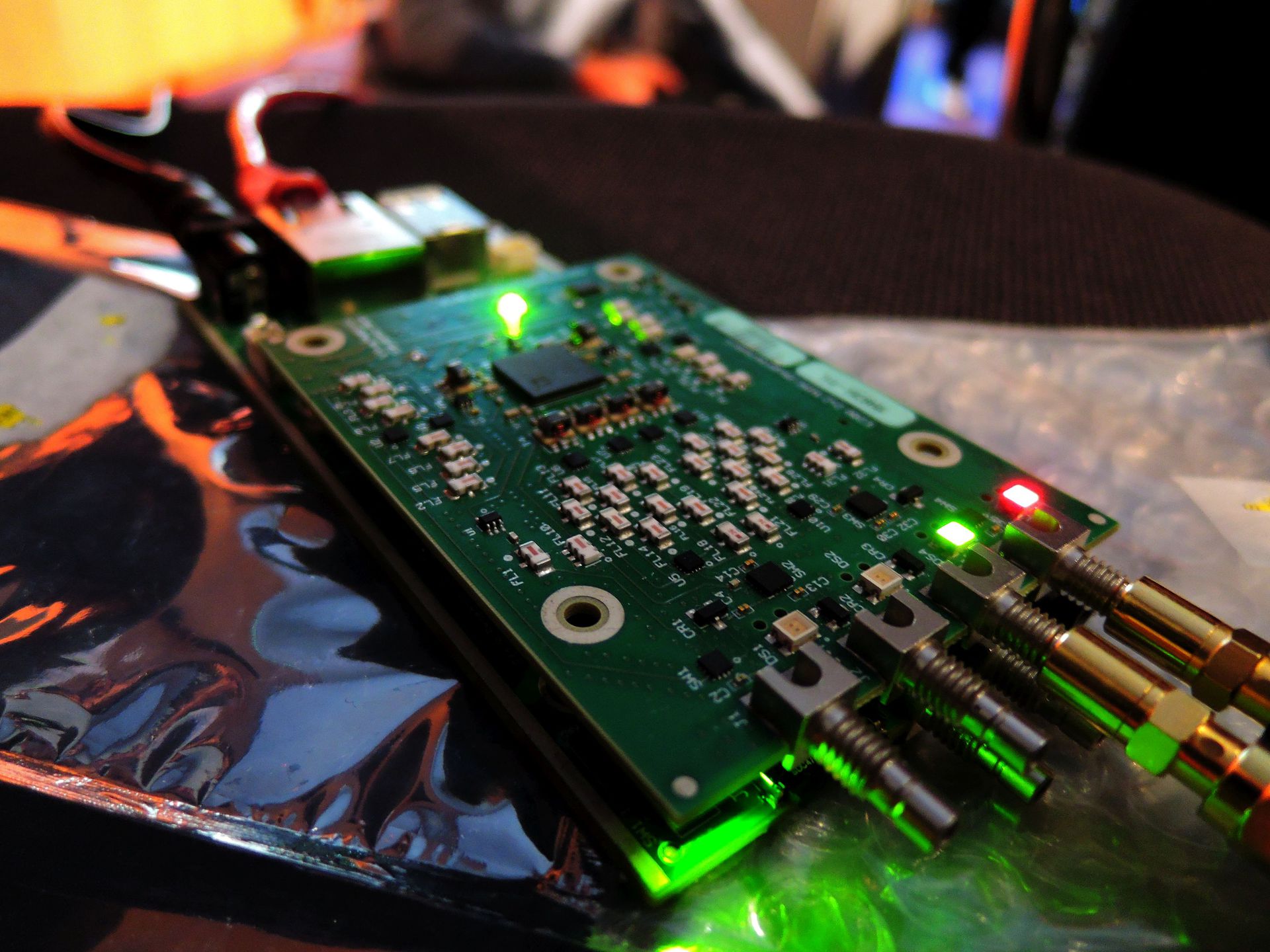
The new USRP, the e310, the most portable SDR platform from Ettus, was also introduced in action. With its help, for the duration of the report, a fully functional local GSM network was deployed on OpenBTS and Asterisk, which made it possible to ask questions by directly calling or writing an SMS to the speaker’s short number.
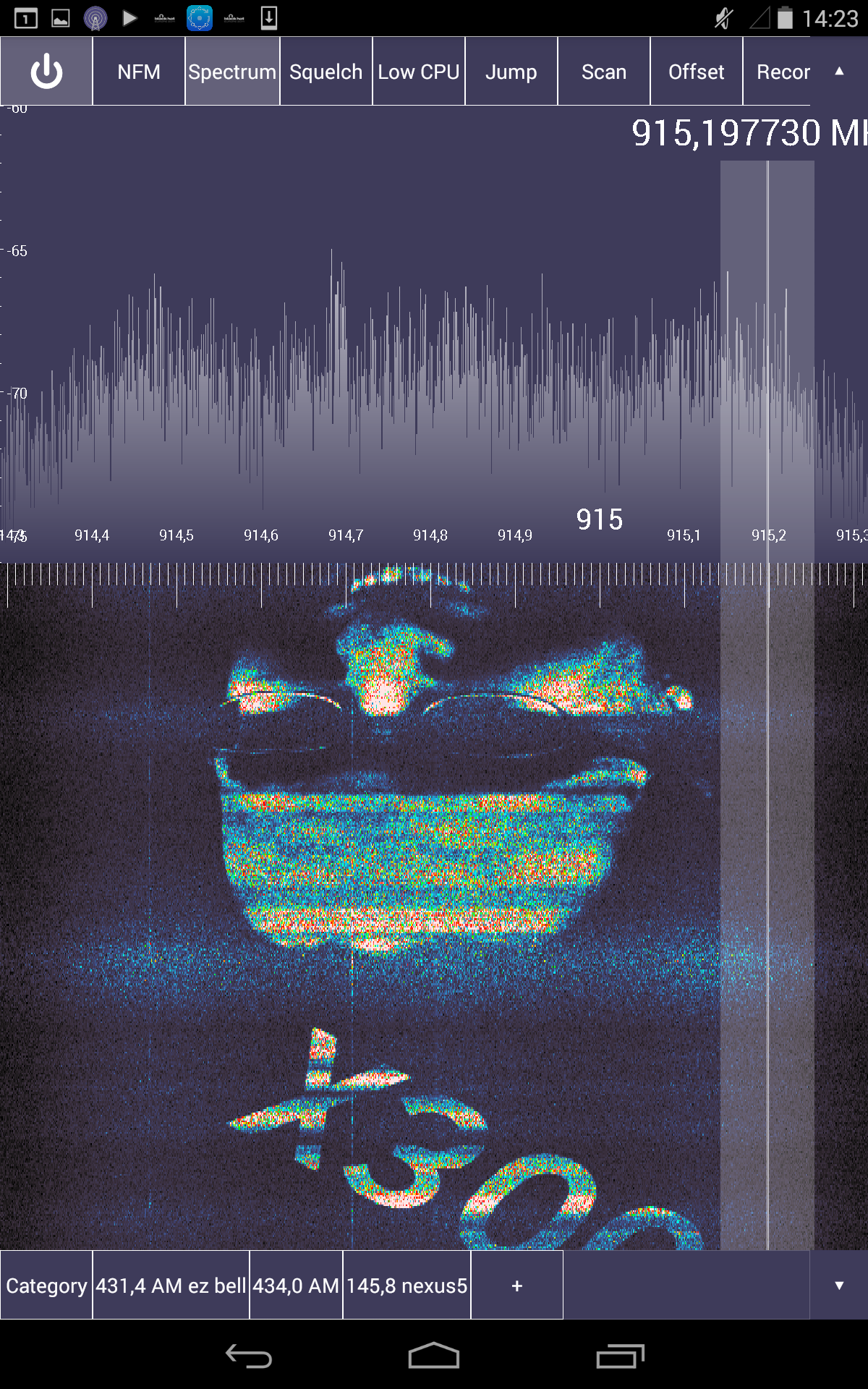
To enhance the amusement of the public, during a performance at a frequency of 915 MHz, a sample was played in a loop, the waterfall spectrogram of which represented various graphic images.
The next report was noted by our compatriots Alexey Osipov and Olga Kochetova, telling how you can entertain yourself with an ATM, if you expand its functionality using Raspberry PI. The issues of research methods for the functioning of the internal components of modern ATM, intercomponent interaction were disclosed in detail, and attack vectors on them were demonstrated.

The first day we closed with Alexander Bolshevoy (@ dark_k3y) with a report on a number of vulnerabilities in the FDT / DTM components detected during our study, and on the study itself, which included the development of a number of special software and hardware tools for analyzing industrial protocols and searching for vulnerabilities .

The next day of reports was remembered by a story from a man- (self) XSS, Ashar Javed.

Ashar told about his methodology for searching for cross-site scripting (XSS) vulnerabilities in WYSIWYG editors, about how he, following it, “managed to detect vulnerabilities in almost all popular visual text editors”, and about the specifics of subsequent communication with vendors.
The report from Gregory Pickett about Software Defined Networks was extremely informative , and the presented tools for working with openflow, I am sure, will find their application.
And finally, Oren Hafif lit up with an attempt to identify a new type of web vulnerability - Reflected File Download.

An inconspicuous handful of vulnerabilities with elements of social engineering that could not be exploited individually. But under certain circumstances, lining up in a chain, they can lead to RCE on the client side.
In conclusion, you may not even mention separately that Blackhat Europe turned out to be rich in content, there is even an opinion that this year the local event surpassed its older American brother in terms of reports. And, of course, BH is not only reports, but also live communication, a lot of interesting new contacts, fresh views from the outside, a huge useful experience and a source of new ideas.
Full list of reports with descriptions and materials of
UPD: Ashar Javed's work was criticized without groundfor manipulating facts and wishful thinking. In particular, the use of self-xss vectors, which nullifies the practical value of such finds.
