Biometric system on a mobile phone
 I work in the field of biometric technologies and I want to describe one of the solutions, which claims to be firmly included in our everyday life in the near future. We are talking about a bimetric user authentication system that can be used on any modern smartphone, and which is designed to conveniently (!) And reliably distinguish access to various mobile services, both banking, medical, and any other applications.
I work in the field of biometric technologies and I want to describe one of the solutions, which claims to be firmly included in our everyday life in the near future. We are talking about a bimetric user authentication system that can be used on any modern smartphone, and which is designed to conveniently (!) And reliably distinguish access to various mobile services, both banking, medical, and any other applications.Recently, an increasing number of companies are using the capabilities of the Internet to provide their services. Typically, the architecture of such applications is the use of thin client technology, which involves the centralized storage of client data and providing access to them only upon special request. A client using a remote terminal (this can be a regular laptop, tablet or smartphone) and a special program or a standard web browser can view and change information on a remote server.
To ensure the security of the transmitted data, SSL is usually used.(Secure Sockets Layer). In addition, if the system is an application, access to it can be protected by login and password. To increase security, an EDS (Digital Signature) can be used - a binary data sequence formed by a cryptographic algorithm.
Unfortunately, often, customers store access data directly on a laptop or smartphone, and if it is lost or stolen, third parties can easily access services. Another disadvantage of passwords or EDS is the low usability - the need to remember the password or store the EDS file on a separate medium. That is why now biometric technologies are beginning to enter the access security market .
Biometric characteristics are unique to each person and with proper use they are very difficult to fake. Today, the most widely used biometric characteristics are fingerprints, DNA, iris, face and voice. From the perspective of the identification problem described above when using a mobile phone, the most suitable technologies are face and voice biometrics. And there are several arguments for this:
- voice and face samples are easy to obtain “at home”, absolutely no special skills are required for this;
- To obtain voice and face samples, some special equipment is not required - the photo is taken using the camera, and the voice is recorded through the microphone of the smartphone;
- face photography and voice recording are simple and understandable things for any person, so the technology is easily perceived.
It should be noted that more recently, biometric identification systems by voice and face had significantly worse performance (identification accuracy, size of the biometric model, etc.), compared with, for example, fingerprint biometrics. However, over the past few years, significant successes have been achieved in the development of automatic classification methods and machine learning, which made it possible to bring the performance characteristics of these modalities closer to others:
| Biometric sign | Test | Test conditions | Frr | Far |
|---|---|---|---|---|
| Fingerprints | FVC 2006 | heterogeneous population, including manual workers and the elderly | 2.2% | 2.2% |
| Face | MBE 2010 | police photo base | 4.0% | 0.1% |
| Voice (LLC "MDG") | NIST 2012 | text independent recognition | 3% | 1% |
| Iris | ICE 2006 | controlled lighting, wide range of quality | 1.1% | 0.1% |
OnePass Mobile Authentication Solution
The OnePass bimodal access solution we are working on is a multi-factor user authentication that includes 3 main components:
- face image verification;
- verification by static passphrase;
- presence detector.
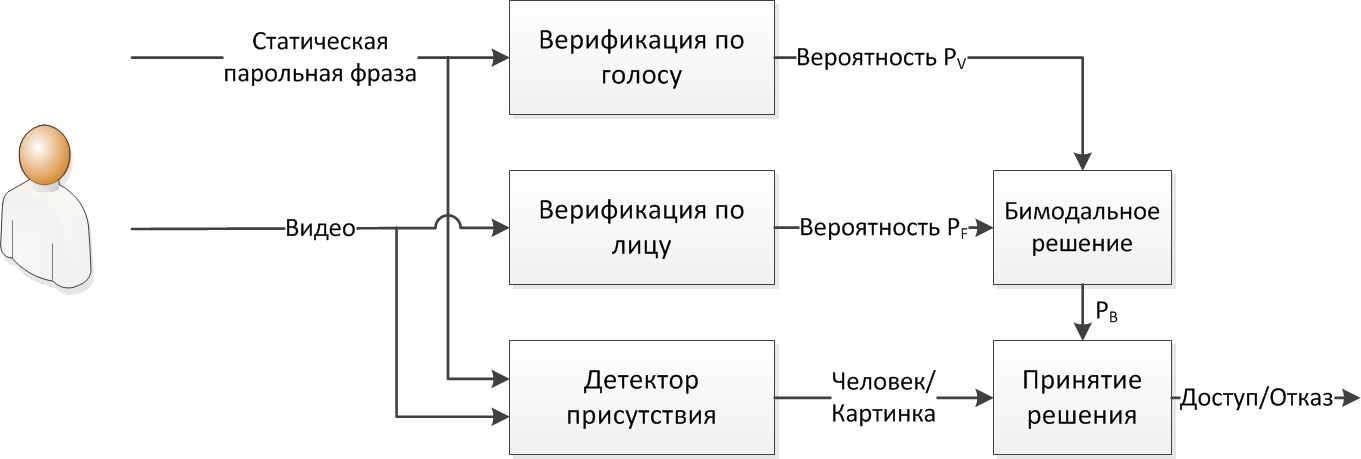
Voice verification is based on the use of a fixed passphrase. At the registration stage in OnePass, the system offers the user a short password or a hint, for example, "Say your last name and first name." The phrase must be repeated 3 times - this is how maximum reliability is achieved and the pronunciation variability is evaluated. At the verification stage, a password also appears on the screen, which is enough to say only once. Using the hint allows you not to store or remember the password.
Verification by face is carried out "on the fly" - at the time the user pronounces the password phrase. In this case, the image of the user's face is displayed on the screen of a laptop or smartphone, which facilitates the positioning of the camera. For registration and verification one image is enough.
A bimodal solution is a generalization of the results obtained during voice and facial verification. The result of processing these modules is the mathematical likelihood of similarity between P Voice and P Face of the user's reference sample with the input audio / video stream. Based on these values, the bimodal probability of verification is calculated.
Presence detectorallows you to determine whether a live person or his image is in front of the camera. The basic principle of operation is based on recording the image of the user's face in the process of pronouncing a voice password by him and determining changes in facial characteristics of the face. Generally speaking, this algorithm deserves special attention because it protects the “Achilles heel” of biometric systems - namely, from hacking attempts using a photograph or video recording. This direction, which is closely related to biometrics and is known in the West under the term Liveness detection. In the future I will tell you more about him.
Decision-makingon user access in OnePass is a logic diagram that takes into account the results of all modules of the authentication system. A positive decision (providing access) is made when all of the following conditions are met:
- The likelihood of user similarity with the standard according to the results of bimodal verification is greater than the threshold value.
- A face detector decided that a live person was in front of the device, not a dummy or photograph.
- Voice presence detector (if used) has decided that the voice belongs to the System Client.
The OnePass solution for the mobile platform has an interface that works in two modes: registration and verification of the Client. We tried to make them as convenient and fast as possible:
- face verification is done by pressing a single button (hence the name of the OnePass solution); for the convenience of positioning the face, the image is mirrored from the camera to the screen;
- voice verification starts automatically in parallel with face verification, voice recording also ends automatically;
- in the process of pronouncing a passphrase, a user’s presence is detected based on an analysis of facial facial changes;
- all data is processed in parallel, which allows you to get the result immediately after pronouncing the passphrase;
- the presence of a voice password hint does not require its storage or remembering
Bimodal Authentication Reliability
An accurate assessment of the reliability of the application is very important, because the degree of user confidence in the system, as well as the potential loss of the Client when breaking the biometric system, will depend on the probability of a system error.
The main indicators of the reliability of a biometric system are errors of the 1st and 2nd kind: False Rejection Rate (FRR) and False Acceptance Rate (FAR). A little more information can be found here: Criteria for assessing the reliability of biometric systems .
We tested the reliability of the solution not only on well-known speech and facial databases ( YOHO , RSR2015 , FERET , MOBIO), but also the databases provided by our customers, one of which was a major US bank. For testing we used smartphones Samsung Galaxy Note II, S3 and S4.
To evaluate the accuracy of any biometric system, it is customary to use characteristic curves: ROC (Receiver Operating Characteristic) or DET (Detection error tradeoff), which establish the relationship between FRR and FAR errors. For the OnePass bimodal solution, we got the following DET curve:
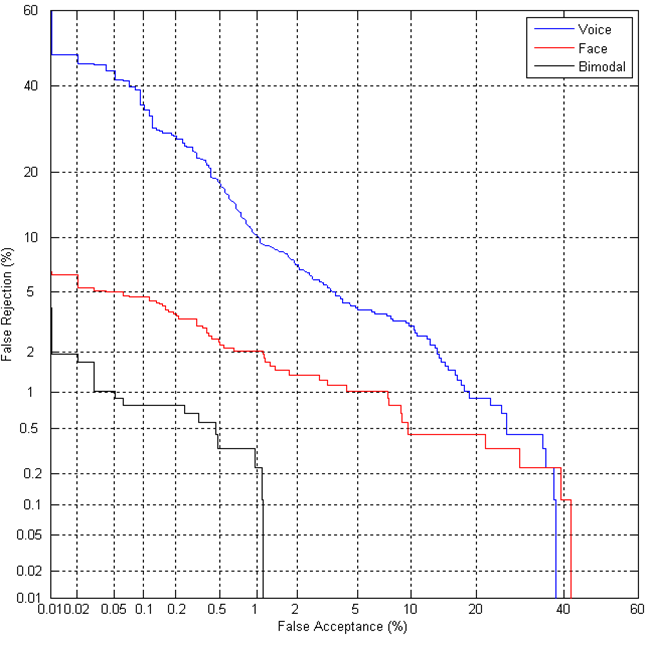
Next, we tested the entire system (the bimodal solution and the module for determining the presence of a living user) in two scenarios:
- The attacker does not have a record / image of the Client
- The attacker has a record / image of the Client
The result is presented in the table:
| Bimodal Verification Threshold | False Deviation Error (FR) | False Skip Error (FA), Attacker Does Not Have Client Record / Image | False Pass Error (FA), Attacker Has Client Record / Image |
|---|---|---|---|
| 0.3 | 1.85% | 0.129% | 8.00% |
| 0.5 | 2.08% | 0.021% | 7.99% |
| 0.7 | 3.63% | 0.004% | 7.86% |
To summarize, these are very good indicators for a biometric system that works in real conditions, especially taking into account the hacking scenario using photography. OnePass is currently undergoing tests at a U.S. bank to protect access to online banking, and the results shown meet customer expectations. Due to the combination of bimodal authentication and liveness detection, the solution meets the opposite requirements of business and security services and has good prospects for expanding the scope.
