What's inside a reader for two-factor authentication?

Due to the fact that one of the banks is finally moving to a system of SMS codes instead of scratch cards, I had to go to their office to connect SMS.
As practice shows, authorization in Internet banking via SMS is not always safe: they can also steal a number.
Therefore, I decided to find out if the bank provides a hardware token or, as they call it, a hardware password generator. It turned out that they provide. Of course, not for free.
It so happened that earlier I already had a token of another bank, which looked like a keychain with a button.
But he was alone, and the bank was far away, and to satisfy his curiosity (and what is inside?), And then, in the event of a breakdown, to go for fifteen hundred kilometers was not optimistic.
And here - the bank is nearby, the token is not very expensive, one is possible and
Alas, there will be no revelations.
(Carefully, traffic!)
Hereinafter, by clicking on the picture, you can open a full-size photo, so be careful with traffic!
When I first came for a token, they handed me this calculator: The card is inserted on top. After inserting the card, you need to select the operating mode (A or B - they differ in transaction limits), then enter your pin, and then enter the key that is sent by the Internet bank. After entering the key, the device will issue a response key. That's the whole algorithm of work. On the reverse side, the generator looks like this: It was not possible to open without damaging the device case, the entire perimeter was glued: Unscrew the screws and look at the usual keyboard:


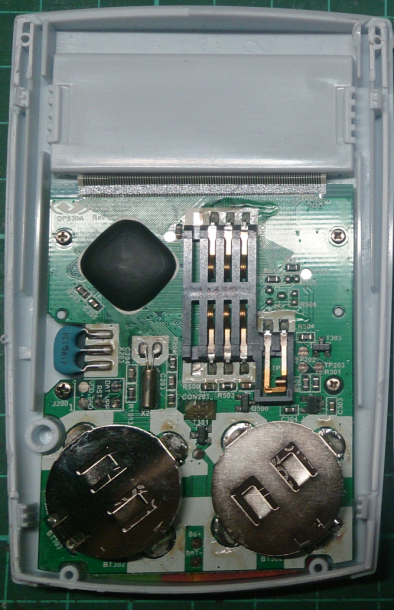
Here, in fact, all the intestines. Under the compound that closes the microcircuit, it’s useless to climb without special tools, so you can only guess which controller is on board.
A slight lyrical digression.
Already an up-to-date story about the issuance of a token / reader
Before opening this token, I took care of getting the second one. And here there are interesting details.
Upon receiving the first token, I informed the bank employee that I did not need SMS authorization. To which they answered "Yeah," and the SMS that this type of authorization is turned on still came. Arriving home, I was convinced that both the token and SMS work. This, of course, did not suit me, so I would have to go to the bank again anyway.
In my second visit to the bank, I again said that I needed a token (the old one was irretrievably destroyed) and that I needed to turn off SMS authorization. There were no problems with disabling SMS. A couple of clicks in the program, and I received an SMS that SMS was disabled.
With the connection of the new token, questions arose. Apparently, the system in the bank was launched recently, and not all employees are aware of what and how it works there.
What logic should be? A client arrives, asks to get him a new generator. What should be done? Probably untie the old one and after that tie the new one. But, judging by what the employee told me, not a token is attached, but a card (yes, I forgot to mention, the card must be chip-linked, their tokens do not work with non-chip-cards). Upon some thought, the employee decided to simply attach a new token, deciding that the old token will be untied. The token became attached, which I checked on the spot via mobile Internet.
And then ... And then I came home and, of course, the first thing I decided to use the old token. And what would you think? Of course, the key to it quietly earned. So now I have two tokens.Therefore, after registering the token in the system in case of its inoperability, do not throw out the token! You can try to revive him, and then your money cried! I believe that only exterminatus will help the physical destruction of the device . Apparently, the system either does not know how to untie tokens, or it needs to be done very cleverly. Dear representatives of the bank, for sure you are reading this article and have recognized your devices! Please draw conclusions !
Upon receiving the first token, I informed the bank employee that I did not need SMS authorization. To which they answered "Yeah," and the SMS that this type of authorization is turned on still came. Arriving home, I was convinced that both the token and SMS work. This, of course, did not suit me, so I would have to go to the bank again anyway.
In my second visit to the bank, I again said that I needed a token (the old one was irretrievably destroyed) and that I needed to turn off SMS authorization. There were no problems with disabling SMS. A couple of clicks in the program, and I received an SMS that SMS was disabled.
With the connection of the new token, questions arose. Apparently, the system in the bank was launched recently, and not all employees are aware of what and how it works there.
What logic should be? A client arrives, asks to get him a new generator. What should be done? Probably untie the old one and after that tie the new one. But, judging by what the employee told me, not a token is attached, but a card (yes, I forgot to mention, the card must be chip-linked, their tokens do not work with non-chip-cards). Upon some thought, the employee decided to simply attach a new token, deciding that the old token will be untied. The token became attached, which I checked on the spot via mobile Internet.
And then ... And then I came home and, of course, the first thing I decided to use the old token. And what would you think? Of course, the key to it quietly earned. So now I have two tokens.
Yes, now, in fact, about the second token, which is in the title photo.
He is a different company. Bank employees told me that it seems to work more reliably than white, which has a lot of defects. It is more compact, and it has a tweeter that works when you press the buttons.
The first token is not collapsible, and therefore the batteries in it are not supposed to be changed.
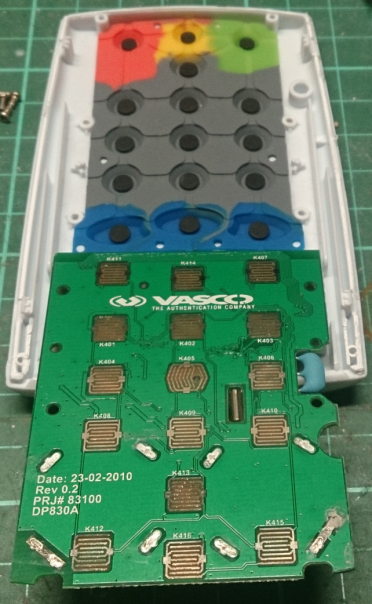
Here is the second one with front and rear views: Of course, since I now have two tokens, in one you can distort the batteries and see if it will work adequately after that. So, both tokens work without problems again even after changing the batteries. A black token is a little trickier than white. It is necessary to remove the front sticker-keyboard, under which you will find the screws that secure the front panel-PCB to the case:



We turn them off and get two halves of the device: The main board is larger: And now a little personal reasoning. The white calculator looks pretty clumsy. It is bad that the design is not collapsible and you can not change the batteries. Not washed flux on the board is also not very good. Why do we need a quartz watch, if the key is apparently stored in the controller firmware, it is not clear. The manufacturer’s website does not shine with the volume of information. I did not find purchase prices for such tokens. The black copy is a development of another company . The board looks better, and in general the device leaves more positive impressions. I also did not find prices. I'm not a security expert, but from articles in Wikipedia

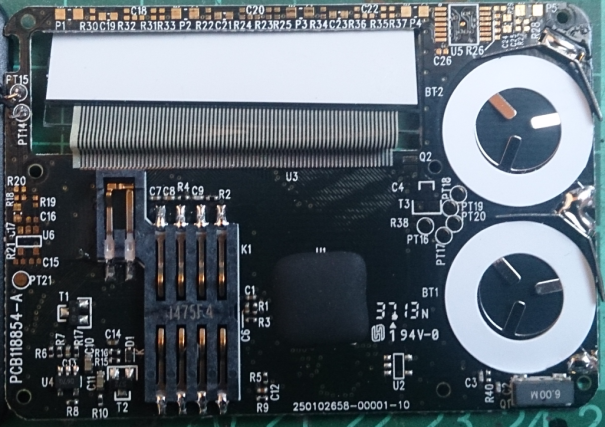
it turns out that since the batteries do not affect the operation of the device, and in one of the tokens there is no watch quartz, then authorization of the OATH type is used .
UPD .: I sprinkle ashes on my head. As Cobolorum and farcaller correctly note, this is not a token, but only a reader and key generation is carried out in the card itself, and not in the reader. So do not panic if you lose such a reader. The main thing is not to lose the card.
I will be glad to any comments and additions!
I ask you to inform about all the errors noticed in PM.
