New round of import substitution. Where to run and what to do?
What is import substitution in IT
Very briefly run through the main issues for synchronization.
1. What is domestic software and hardware?
From a legal point of view, Russian products are those whose Russian origin was confirmed at the Ministry of Digital Development and at the Ministry of Industry and Trade respectively by inclusion in their registers.
Since the end of 2017, according to the resolution of the Government of the Russian Federation No. 1594, the EurAsEC countries do not fall under the definition of “foreign”, but as long as there is no register of Eurasian software, it is impossible to use, for example, Belarusian software as import-substituting.
Immediately make a reservation that the post is more - about software.
2. Is it really made in the Russian Federation from scratch?
In some cases, yes. For example, solutions from Kaspersky or Abbyy.
In others, free software (OSS) is taken as a basis, and its own developments are applied to it. This can include, for example, the majority of Russian operating systems, MoiOffice Mail and Yandex Browser. This is not necessarily a bad thing. For example, Nutanix and Zimbra initially followed this path. The main thing is to be sure that the manufacturer has not organized the “assembly” for a single project and plans to support the decision in the future.
Sometimes there are funny cases. The solution was developed in Russia, but sold through a foreign company. In this case, in order to get into the register, it is necessary to organize a separate Russian company and make fork of the product for the Russian market. The advantage of such solutions is operational technical support of the third level, which is used to working according to Western standards.
3. And if this software is not enough?
The registry of domestic software contains operating systems (OS) based on the Linux kernel. Each of these operating systems has its own repository. Since formally, applications are included in the OS, as well as Windows services, they are considered Russian, and the OS manufacturer is responsible for their support.
4. Are there alternatives?
There are STR, which I have already spoken. But there are nuances.
- If you need budget money for the introduction of open source software, then you will need to agree on the use of open source software, and you will have to prove that it corresponds to the vision of the Ministry of Communications .
- In some cases there may be problems with accounting, with the statement of the balance and the purchase of support for an empty space.
- There will be difficulties with certification of information security requirements (more on that later).
5. Who and why do we need to deal with import substitution?
In the first place - to government agencies, and soon - to companies with state participation. The task of import substitution is set for them by the state for obvious reasons:
- Redistribution of funds (so that maximum funds remain in the country).
- Protection from potential bookmarks.
- Support for Russian manufacturers.
- Protection from sanctions.
For state institutions, the fact of confirmation of the Russian origin of programs and equipment is particularly important. For commercial organizations, the question of abandoning imported commercial software is also worth it, but for several other reasons:
- Sanction risks. And on both sides. On the one hand, for example, Rusal has recently come under sanctions, and the US government is seriously considering a total ban on reciprocal trade. On the other hand, our Government is also famous for (a) symmetrical "answers to Chamberlain". While commercial organizations manage to purchase and use software under the lease scheme through a cloud provider, but no one knows how long it will last.
- Saving. The dollar is growing, and with it - deductions to foreign suppliers. At the same time, support for open-source projects, domestic forkostroenie and development are being developed under sanctions. There are more IT professionals who are ready to work with the Linux environment not in companies for 10 users, but in large organizations with dozens and hundreds of subsidiaries and granddaughters. That is, the transition to open source is perceived no longer as “jumping into the water and trying to swim out,” but as “those two have succeeded, which means we will succeed.”
To call such a transition for commercial organizations import substitution is incorrect, but the approaches to the implementation of projects for the care of imported proprietary software will be the same.
A bit of history
In 2015, we evaluated the FZ-188, which prohibits buying software at a competition if it has a domestic counterpart.
Since then there have been a few changes:
- The registry of the Russian software has appeared and is replenished. The registry is accompanied by the Ministry of Communications and Mass Media (now the Ministry of Digital Development, Communications and Mass Communications). Now there are more than 4,600 names of domestic programs. True, the classification leaves much to be desired. For example, Yandex.Browser falls into the categories “General purpose application software” (800 points in the same place) and “Office applications” (200 points). That is, to find the software of the desired category can only be searched. Criteria for admission to the registry, by the way, you can see here .
- There is a “war” with varying success between government agencies trying to circumvent the restrictions of the Federal Law-188 and purchase foreign software using the item “justification of the impossibility of compliance ...” and domestic software suppliers. The first come up with all the new justification. The second ones file a complaint with the FAS and cancel the competition .
- Products from the Eurasian Economic Union are equated in priorities with those that are in the registry of domestic software. That is, the Kazakh antivirus is the brother of the Russian antivirus. But if you suddenly found a fork of Linux made in Armenia, then do not rush to install it: the EAEU currently does not have its own registry, so it is not clear which software is local and which is not local. That is, until the registry is in place, it is impossible to prove that the software belongs to the EAEU.
- A Resolution of the Government of the Russian Federation No. 968 dated September 26, 2016 was issued , requiring to exclude suppliers of foreign equipment from the competition ( according to the list ) if two or more domestic suppliers participate in the competition. The relevant register is maintained by the Ministry of Industry and Trade.
- And the main topic of the second half of this article is Order No. 334 of the Ministry of Communications and Mass Media “On approval of guidelines for the transfer of federal executive bodies and state extra-budgetary funds to the use of domestic office software, including previously purchased office software”. Then there were changes to the order, and more recently - its expansion to new organizations.
Certification of information security requirements
Certification of an automated system for information security requirements is needed in cases where this system is a GIS, or it is working with personal data.
It would seem, what have the import substitution? If you have not yet certified systems and you plan to engage in import substitution, then this should be taken into account in order not to perform certification twice. Projects are logical to combine. But, more importantly, the possibility of certification must be worked out in advance - at the planning stage of the transition to domestic software. This is especially true of the operating system.
Will you use a certified OS, or limit your attachment to IB.
Is there a complete set of attachments of protection suitable for your threat model for this operating system?
Example: if you use a username and password to enter an operating system that is not FSTEC-certified and which does not need a password protection software, then from the point of view of regulators you do not have the requirement to enter a password, and you can enter the OS under any role.
Attachment protection may reduce solution stability. The creators of the OS do not like them very much, so they usually organize the certification themselves using the “correct” crutches of safety.
For a separate certification, FSTEC, in fact, needs to maintain a separate product line and update its certificates every six months. At least. Naturally, open-source communities do not seek to lobby and pay for such certification. Therefore, there are commercial companies that provide a certificate and support. And the easiest way to keep such a branch is the manufacturer of the domestic OS.
Transition plan
Together with order No. 334, the Ministry of Communications and Mass Media proposed a typical plan for switching to domestic software for federal executive bodies and state extra-budgetary funds.
If in 2015, it just became harder to purchase new software, now they are expecting a replacement from the government agencies already in use. On the one hand, these are “recommendations”, on the other hand, the Ministry of Communications and Mass Media controls both the execution of the submitted plan, and partially the budgets for informatization.
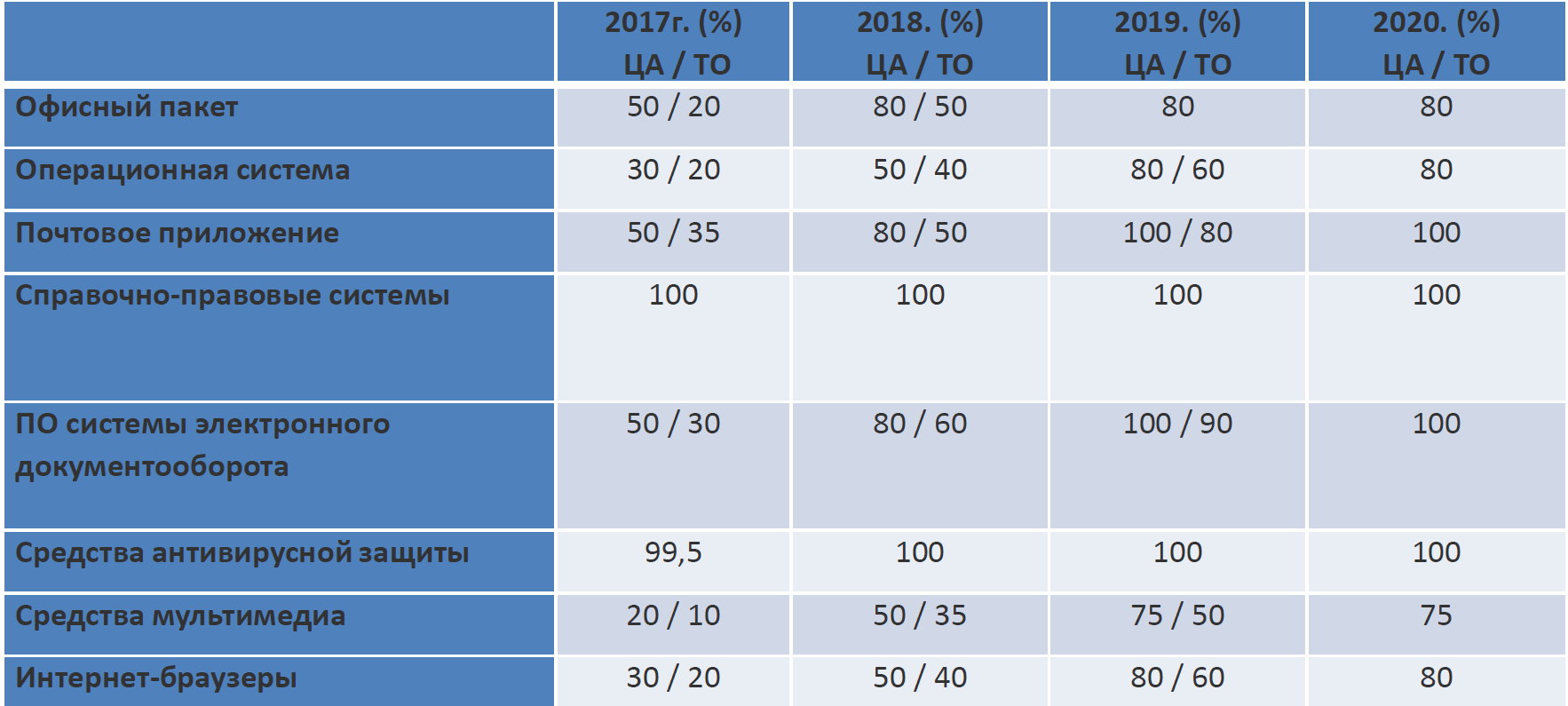
Central Asia - central office, MOT - territorial office.
Just a month ago, a similar order was issued under number 335 for executive authorities of the constituent entities of the Russian Federation and local governments of municipalities of the Russian Federation. It numbers a little smaller .
But let's look not at the numbers, but at the names. Despite the name "office software", this includes the operating system.
In the Ministry of Communications, they simply reflected the list of software that is guaranteed to be used in any government body. There are virtually no personnel and financial systems. Often they lie in a protected segment, where the processing of Pers. data. Perhaps a subtle hint that this problem can be left for later by including in the remaining 20%.
Let's go through the list. Reference and legal now - almost everyone: the Guarantor, the Consultant or the Code, the antivirus - Kaspersky, the document flow - also from one of the domestic manufacturers. The rest is built into the system or you need to install an external one. An interesting point: the OS is considered in the number of pieces per company. And 80%, which, according to the results, should become domestic, include both client and server in any convenient proportion.
It would seem, thanks, state. Where to run is clear, there is a plan, there is a list of software in the registry, even money may be allocated in the budget for such activity. But there are difficulties:
- You have employees who need some of the departmental portals with electronic signatures. For example, government procurement. Do you know who still uses ActiveX here? Never guess. In general, you need an imported Windows operating system.
- In some workplaces, software that works exclusively with Windows is most likely installed for you.
- Even worse, if the developer of your workflow did not bother with a full-fledged web client. Only thick client under Windows. Only hardcore.
Then you can:
- Decide that the “problem” employees will fall into those same 20% of the allowed unsubstituted licenses and replace the rest.
- Or write a letter to the regulator about the fact that you have tasks that cannot be solved on domestic software in principle. Most likely, you will meet.
- Combined scenario when access to problematic software is temporarily (Hey, the creators of public procurement!) Through terminal access.
But I also saw strange situations. For example, installing a second OS on the same jobs. There are one Windows and one domestic Linux. The user at boot can choose the OS. True, in fact, in the domestic OS, he does not go at all.
An even more lazy scenario is when “just rolling” even the purchase of licenses. The fact of procurement is there, and the imported software purchased earlier goes into the category of “trophy” and continues to be used.
As far as I know (value judgment), some are not fined. Again, a value judgment is that we have already seen how such laws are implemented. Most likely, everything goes to the fact that they will come later with checks. View purchased licenses, contests played, implemented projects. That is, the risks are still very high.
There is a plan. Now we need a plan for the implementation of the plan
We proceed to the practical part. The task is to minimize the risks and get to the goal (implementation of the Government / Ministry of Communications and Mass Media) plan with minimal losses (functionality, nerves, peer relations). Therefore, the algorithm is as follows:
- Analyze which programs are used in the field. The analysis should include both automated data collection from workplaces (good old MS MAP, for example), and a survey of technical support and contracting organizations. Support may forget something, but MS MAP will not find web services and will not tell how much the found software is needed by users. Here it is desirable to collect information on the existing periphery. Not all scanners and printers are compatible with Linux. Everything needs to be tested. Some will have to be replaced.
- Assemble the departments of information security, IT and business applications and understand who has what limiters. I know a case when the chosen VPN solution for the OS just didn’t fall into the ready deployment. It is worth thinking about this in advance and the three departments.
- Immediately you should think about how to sweeten the pill. The fact is that once the entire stack is changing, starting with the OS, then we need to take advantage of the situation and deliver them a different new domestic or open source software. For example, in state-owned companies they are very happy about the allowed messengers. Previously, there was no, but now there is.
- Try to determine the operating system. If you fail to do this step, there will be more than one stand.
- Make a list of application software and write to vendors with questions about compatibility (someone may have a separate line, someone is expected to have a patch with Linux support, someone has a ready set of settings for WINE (Windows Call Handler Emulator).
- Assemble a test stand and start driving real projects on it. At this stage, it may become clear that some critical functionality is lost, for example, the schemes of engineers are not converted into the selected office suite. You need to test everything and everyone. Vendors usually help on large installations themselves, we repeatedly ordered patches.
- Implement a pilot after testing. We need real feedback from a small number of active users with different specifics of work. 10 people will be enough. Here is our example after one of the pilots: new shortcuts have been added to the desktop, and the names of the old ones have been changed, the graphic editor has been replaced, the file resource mounting scheme has been redone, the errors of WINE with some applications have been fixed.
- Following the pilot, collect images of jobs and prepare for replication.
- Organize training.
- And only now - implement.
When choosing a software stack, remember that you can take ready-made programs from the OS repository, or you can purchase the appropriate Russian software. Examples:
| Component | According to the os repository | Specialized in |
| Office suite | Libreoffice | Moyofis standard |
| Mail application | Dovecot + postfix / exim thunderbird client | My office post / communigate pro |
| Internet browser | Firefox / chromium | Yandex. Browser |
| On the electronic document management system | Jboss | Csed 3.0 (croc) |
But back to what can be done now.
The fact that it did not take off on the tests can be sorted out in one of several ways:
- Go to the web client (if it exists and works with something other than IE).
- Try running in WINE.
- Leave unchanged and include in the share of licenses, which can not be replaced.
- Write to the Ministry of Communications about the problem and get "good" to save the software.
- Choose an analogue and prepare a project for replacing sewing with compatible soap.
- Use terminals, VDI or client virtualization.
Finally - a few tips on what should not be missed:
- Informing employees about the project. Users will howl, scream and kill. The sooner and more fully you inform them and convince them that the project is inevitable, the better.
- Training IT staff. Otherwise, get ready to break the phone technical support. And no instructions will help.
- Conversion of office documents templates. None of the options for replacing MS Office (whether Libre Office or MyOffice) displays documents created in MS Office one-on-one. So be sure to select a person who pre-organizes the publication of new document templates with your “caps” and will be on the pickup during the global migration to patch holes like “I have no time, but your ... shows ...”
- Configuration of workstations. In the project, you can almost not affect the server infrastructure. The only service that you need to replace, except for mail, is MS AD group policies. Without this, after detecting another error and finding a way to solve it, you will have to work with each computer individually.
- Terminal access. In the course of the project, it will surely appear that you have forgotten about some important application with several users. Terminal access is an opportunity to extinguish the fire and move the solution to a later time when everything is settled.
Links
- Old FZ-188 analysis .
- Order No. 334 Ministry of Communications .
- Decree No. 658 on centralized procurement - the latest changes in the field concern the fact that some products are recommended to be purchased centrally. Perhaps they want to do something similar to SaaS - possible domestic clouds.
- Register of domestic software .
- Register of equipment Minpromtorg .
- An example of the project of import substitution, which we implement .
- My mail is ADonin@croc.ru
