Remote code execution in Microsoft JET Database Engine

Lucas Leong (Trend Micro), a Zero Day Initiative project participant, revealed details about the existence of a critical vulnerability in Windows that allows remote execution of arbitrary code in the context of the current process. Successful exploitation of the problem will require the participation of a user who must open a malicious file or follow the link.
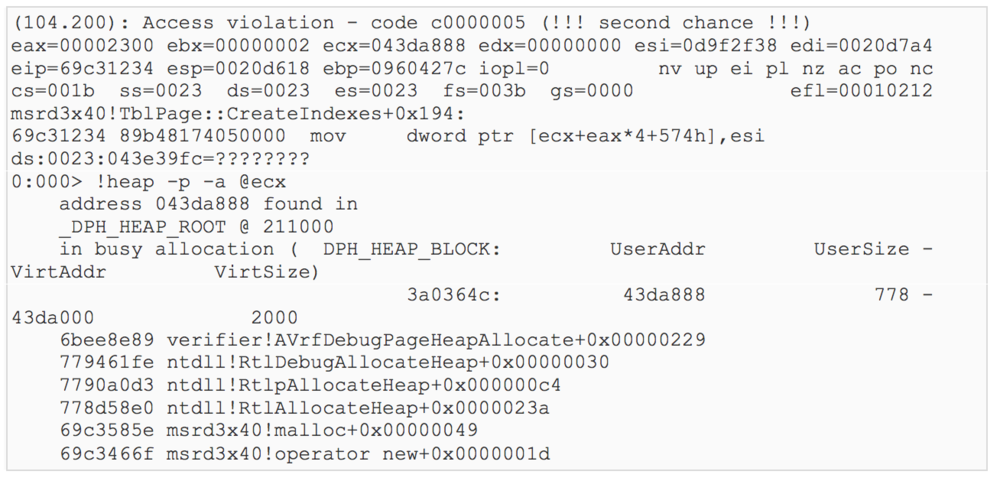
The vulnerability is detected in the Microsoft JET Database Engine DBMS and represents the ability to write beyond the out-of-bounds OOB write buffer and manifests itself when opening a JET (Joint Engine Technology) data source through the OLE DB interface.
OLE DB (Object Linking and Embedding, Database, OLEDB) is a set of COM interfaces that allow applications to work in a unified way with data from different sources and data storages.
To cause this vulnerability, the user will need to open a specially crafted file containing data stored in the Microsoft JET Database Engine DBMS format. Different applications use this database format. Exploiting this vulnerability may allow code execution at the current process level.
Published on github by PoCthis vulnerability, which affects the entire line of modern operating systems from Microsoft: Windows 7, Windows 8.1, Windows 10, and Windows Server Edition 2008 to 2016.
A curious fact is that the details of the vulnerability were provided to Microsoft on May 8, May 14, Microsoft confirmed the presence bug According to the ZDI policy, after a 120-day wait (4 months), they published a vulnerability. Microsoft is currently preparing a fix, which is expected to be included in the planned October updates.
Attackers can exploit this vulnerability extremely successfully in phishing attacks, implementations of APT vectors, and watering hole attacks. It is recommended that you apply policies for using trusted files until a patch is released.
