How I searched for viruses ...
Well, I’ll say right away that it’s not the viruses themselves, but their activity, but nevertheless I discovered a lot of new things about where my computers, phones and tablet “go”.
And it was evening, there was nothing to do ... It was raining, the Internet suspiciously slowed down, although it seems to be 8 megabits and everything should “fly”. My home equipment park, which is connected to the World Wide Web, is small - a stationary computer, laptop, tablet, satellite tuner with Linux, 3 smartphones and a dead little serovka-cheonchik with debian and xen (it also has five constantly working virtual OCs). Not much is not small, but to constantly maintain, update and check for viruses, all this economy takes money (licensed software) and time, which is always absent. And at some point, it was decided to completely abandon antiviruses, otherwise buy them, update them ... Yes, and subjectively everything slows them down ...
More than a year has passed since I refused antiviruses. Everything works, everything is fine, But ... "Do you drive a hamster? “But he is!”
I am a web programmer, so on the server I configured dns for myself (bind9), in which I created the .dev zone for development (it’s very convenient, see [tyts] ), and turned it on for one, let it be just in case. The address of my local DNS server is distributed by the DHCP ADSL modem as the main DNS server on the network.
And then one day I decided to look at what is written there in the DNS server logs. It turned out that one of the home computers constantly knocks do not understand where:
I definitely didn’t go there, then it’s someone else. Virus prevention was carried out, and the malware was indeed found and “cured”. There would be an end to the fairy tale, but I did not stop there. I wanted to more deeply and conveniently analyze the accumulated logs of the DNS server, maybe something else was happening besides my will and desires.
And bingo - they counted me (as in that cartoon). I watch advertisements and all counters persistently consider me. Of course, it’s no secret that on most sites a variety of traffic counters, metrics and advertisements are installed, from different advertising platforms, there are even LIKE social. networks that I don’t even know. And why, so that they would consider me, show annoying advertising, why what I do not need? Something needs to be done with this.
Two problems need to be solved - to analyze the logs in a convenient form, and block unnecessary sites (counters, ads, etc.), because putting advertising cutter on all computers was somehow not an option, and I also did not want to do the Internet through a proxy. There are a lot of ways to block a lot, but for myself, I chose to substitute the real DNS IP address with my local one. That is, local DNS configurations.
With the first paragraph I thought there would be no problems. All the good is written before us. A wonderful bash script was found - one that can show the most visited sites by sorting out the logs and a Ruby Bind log analyzer project that converts logs to a mysql database and it was also stated that it has a web interface for viewing results. Also, in hot pursuit, a resource was foundhttp://pgl.yoyo.org/adservers/ on which everything seems to be on, and lists of domains that you can safely prohibit, and a description of how to do this, but ... I don’t know how in bind8, but bind9 strongly cursed at what was offered on that site an empty zone, and browsers frantically did not complete the process of loading the page, trying to load counters and ads onto the page, not understanding where the dog was digging.
The first script did not fit right away because The logs were for half a year, there was no rotation of logs, and everything else did not include a parameter to save the time of access to the DNS server. The second Bind log analyzer, in which it was possible to configure the log analysis, but managed to launch the web interface so much less. I had to bike.
So, about the bike. Called statdnslog, lies on the githuband consists of two parts: utilities and WEB interface.
Utilities are able to:
- parse log files of queries to DNS Bind9;
- save the received data to the database (mysql);
- create prohibition lists based on lists from pgl.yoyo.org (for example);
- adding new DNS to the list of prohibitions from your list (text file with DNS enumerations);
- generate DNS settings templates for BIND9.
WEB interface:
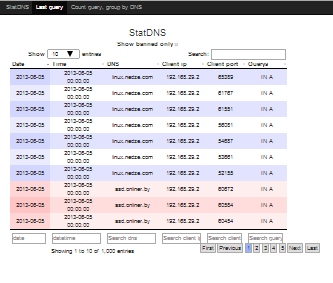
- displays statistics sorted by date (by default, the most visited are at the top) and other fields;
- Shows the most visited DNS and how many times visited;
- highlight in color (red) in the general list of visited DNS, DNS from the list of prohibited.
By the way, I’ll say that redefining DNS will not save you from anything and this is not a means of protection. Protection can be antiviruses, firewalls, proxies with a traffic analyzer and other specialized means of protection, but in the case of analyzing DNS traffic, it is warned, it means it is armed, and who, where and when it goes from family, is visible.
Once again the link to github: https://github.com/mcdir/statdnslog
Website: http://statdns.nedze.com/
Demo version of the WEB interface: http://demo.statdns.nedze.com/
Additional material
Logging DNS BIND9 logging Clause - http://www.zytrax.com/books/dns/ch7/logging.html
How to enable named / bind / DNS full logging -http://stackoverflow.com/questions/11153958/how-to-enabled-named-bind-dns-full-logging
Bind Logs - Top DNS Queries http://www.pablumfication.co.uk/2010/09/03 / bind-logs-top-dns-queries /

And it was evening, there was nothing to do ... It was raining, the Internet suspiciously slowed down, although it seems to be 8 megabits and everything should “fly”. My home equipment park, which is connected to the World Wide Web, is small - a stationary computer, laptop, tablet, satellite tuner with Linux, 3 smartphones and a dead little serovka-cheonchik with debian and xen (it also has five constantly working virtual OCs). Not much is not small, but to constantly maintain, update and check for viruses, all this economy takes money (licensed software) and time, which is always absent. And at some point, it was decided to completely abandon antiviruses, otherwise buy them, update them ... Yes, and subjectively everything slows them down ...
More than a year has passed since I refused antiviruses. Everything works, everything is fine, But ... "Do you drive a hamster? “But he is!”
I am a web programmer, so on the server I configured dns for myself (bind9), in which I created the .dev zone for development (it’s very convenient, see [tyts] ), and turned it on for one, let it be just in case. The address of my local DNS server is distributed by the DHCP ADSL modem as the main DNS server on the network.
And then one day I decided to look at what is written there in the DNS server logs. It turned out that one of the home computers constantly knocks do not understand where:
01-Nov-2013 23:11:03.128 queries: info: client 192.168.1.11#63500: query: yfp2lvdyye86s78.pp.ua IN A + (192.168.1.1)
01-Nov-2013 23:11:04.138 queries: info: client 192.168.1.11#63500: query: yfp2lvdyye86s78.pp.ua IN A + (192.168.1.1)
01-Nov-2013 23:11:09.867 queries: info: client 192.168.1.11#58461: query: yfp2lvdyye86s78.free IN A + (192.168.1.1)
01-Nov-2013 23:11:15.390 queries: info: client 192.168.1.11#52119: query: yfp2lvdyye86s78.ce.ms IN A + (192.168.1.1)
01-Nov-2013 23:11:21.006 queries: info: client 192.168.1.11#50737: query: yfp2lvdyye86s78.net IN A + (192.168.1.1)
01-Nov-2013 23:11:26.512 queries: info: client 192.168.1.11#54267: query: 35pa1j6h47e1l7v.tk IN A + (192.168.1.1)
I definitely didn’t go there, then it’s someone else. Virus prevention was carried out, and the malware was indeed found and “cured”. There would be an end to the fairy tale, but I did not stop there. I wanted to more deeply and conveniently analyze the accumulated logs of the DNS server, maybe something else was happening besides my will and desires.
And bingo - they counted me (as in that cartoon). I watch advertisements and all counters persistently consider me. Of course, it’s no secret that on most sites a variety of traffic counters, metrics and advertisements are installed, from different advertising platforms, there are even LIKE social. networks that I don’t even know. And why, so that they would consider me, show annoying advertising, why what I do not need? Something needs to be done with this.
Two problems need to be solved - to analyze the logs in a convenient form, and block unnecessary sites (counters, ads, etc.), because putting advertising cutter on all computers was somehow not an option, and I also did not want to do the Internet through a proxy. There are a lot of ways to block a lot, but for myself, I chose to substitute the real DNS IP address with my local one. That is, local DNS configurations.
With the first paragraph I thought there would be no problems. All the good is written before us. A wonderful bash script was found - one that can show the most visited sites by sorting out the logs and a Ruby Bind log analyzer project that converts logs to a mysql database and it was also stated that it has a web interface for viewing results. Also, in hot pursuit, a resource was foundhttp://pgl.yoyo.org/adservers/ on which everything seems to be on, and lists of domains that you can safely prohibit, and a description of how to do this, but ... I don’t know how in bind8, but bind9 strongly cursed at what was offered on that site an empty zone, and browsers frantically did not complete the process of loading the page, trying to load counters and ads onto the page, not understanding where the dog was digging.
The first script did not fit right away because The logs were for half a year, there was no rotation of logs, and everything else did not include a parameter to save the time of access to the DNS server. The second Bind log analyzer, in which it was possible to configure the log analysis, but managed to launch the web interface so much less. I had to bike.
So, about the bike. Called statdnslog, lies on the githuband consists of two parts: utilities and WEB interface.
Utilities are able to:
- parse log files of queries to DNS Bind9;
- save the received data to the database (mysql);
- create prohibition lists based on lists from pgl.yoyo.org (for example);
- adding new DNS to the list of prohibitions from your list (text file with DNS enumerations);
- generate DNS settings templates for BIND9.
WEB interface:
- displays statistics sorted by date (by default, the most visited are at the top) and other fields;
- Shows the most visited DNS and how many times visited;
- highlight in color (red) in the general list of visited DNS, DNS from the list of prohibited.
By the way, I’ll say that redefining DNS will not save you from anything and this is not a means of protection. Protection can be antiviruses, firewalls, proxies with a traffic analyzer and other specialized means of protection, but in the case of analyzing DNS traffic, it is warned, it means it is armed, and who, where and when it goes from family, is visible.
Once again the link to github: https://github.com/mcdir/statdnslog
Website: http://statdns.nedze.com/
Demo version of the WEB interface: http://demo.statdns.nedze.com/
Additional material
Logging DNS BIND9 logging Clause - http://www.zytrax.com/books/dns/ch7/logging.html
How to enable named / bind / DNS full logging -http://stackoverflow.com/questions/11153958/how-to-enabled-named-bind-dns-full-logging
Bind Logs - Top DNS Queries http://www.pablumfication.co.uk/2010/09/03 / bind-logs-top-dns-queries /
