Conference DEFCON 22. Andrew "Zoz" Brooks. Don't screw it up! Part 1
- Transfer
So, our today's topic is disobedience and disobedience. Disobedience is what makes hackers what we are. Our job is to use things in a way that they are not intended for or which is not allowed. Sometimes the best way to show that things can be done better is to break the rules. But there is a greater way - a violation of unjust laws.
Henry Toro, in his essay “Civil Disobedience,” wrote: “Unfair laws exist, will we obey them obediently, or will we try to change them, while continuing to obey them, or will we break them right away”?

I was inspired by the fact that I was given the opportunity to talk about this, because the most prominent practitioner in the prosecution of disobedience in our country is the secret police. Such unrepentant criminals, like the former NSA director Michael Hayden, were engaged in telephone wiretaping during Bush’s time, or National Intelligence director James Klepper, who repeatedly lied to Congress - they neglect the law when it is necessary for their own affairs. They tell us that the end justifies the means so that we too can play this game. We are obliged to apply civil disobedience where there is a wrong law that introduces the United States into a state of constant surveillance in the name of the fight against terrorism, which is also related to this country, as public health problems are associated with the bubonic plague of the 14th century. This is worse than a crime, it's just stupid. Therefore, we must not allow the spying state to prevent us from doing the right things.
Think of the DCSS crypto wars, which are designed to protect media tycoons from hackers playing their legally purchased DVDs on laptops running Linux. They came up with a DVD encryption code that was hindering this, which was completely illegal. This is a perfect example of a law that is worse than a criminal one, it is stupid, because it can only hurt people who legitimately use media resources.
Of course, hackers are obliged to shove a stick in the asses of the people responsible for these laws, making illegal T-shirts, ties, games or illegal Minesweeper for Windows (laughter in the hall).

Of course, in our time there are more or less trivial injustices to be disobedient. Starting with violations of the crappy user agreements EULA and ending with the use of technology to counter the truly tyrannical and oppressive regimes that exist on earth today.
"Give a man a mortar" - for this today there is a corresponding application. The fact is that using technology to push the boundaries is what people at this conference are doing. In fact, in most cases, you have no idea whether what you are doing is legal or illegal. No one except the Congressional Research Service dared to state that they did not know the exact number of federal laws in force in the region at a given time. So even a good lawyer will not say whether his client is doing something illegal or not.
Keep in mind that laws in this and other countries are interpreted in terms of historical precedents. It also matters when you are accused of something. Forget about deliberate disobedience, because people constantly break the law without knowing it, so be careful.

Here is one of my favorite examples of DefCon. This slide shows an example of disobedience, but a good one. DefCon is full of such examples.
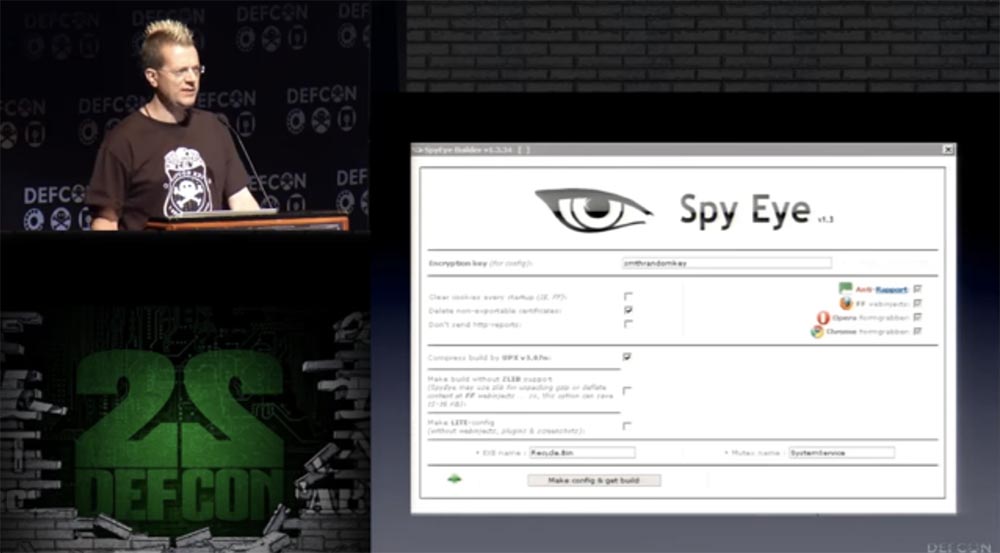
I think we can agree that breaking into other people's bank accounts is illegal. One of my favorite moments at DefCon was a meeting with a guy who hacked into the database of “Nigerian scammers,” got their bank account details and got some money back from them.
Leakage and drain of information from government agencies and similar types of disobedience are currently in vogue and, I think, useful to society. Much of what has been leaked in the media lately comes down to controlling the Internet. People with much more money and power than those who are present in this room are trying to block it for the lower classes. Disobedience is part of such resistance to the control and pressure of the authorities. Blocking the Internet, the end of the free flow of information, regardless of the wealth of power and whatever that information carries is the end of the Internet.

Therefore, we must refuse to be obedient. If you are going to deliberately disobey, there is only one rule that is worth adhering to, and whoever was on the Hacker Jeopardy team knows these three words very well: “Fuck It Up”! - “Don't screw it up!”
Another reason that inspired me to this presentation was Snowden’s information leaks published last year. I would like to share some thoughts on this and invite the community to take part in the discussion. This is a conversation for all who did not have free time to get acquainted with all these leaks. If everyone present knows what I'm going to say, I will be very happy, but this is probably not the case.
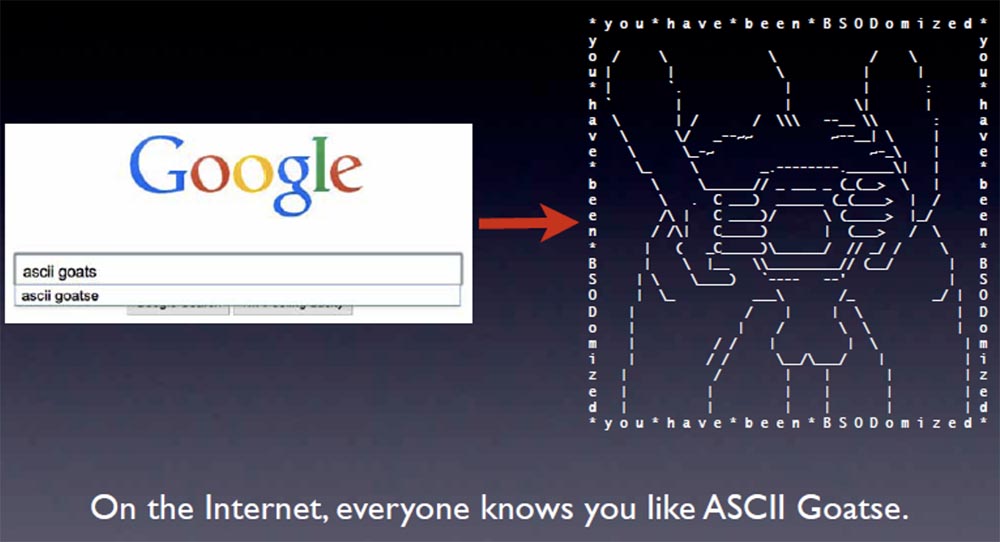
Remember the good old days, when the Internet has not yet switched to the "kitty" humor? Now everyone on the Internet knows what an ASCII goatse is (laughter in the hall). Google even kindly offers this drawing.
But in reality, the good old days were not so good. I do not consider myself to be an old school, because I started to be engaged in our business only in the early 90s. It took a quarter of a century to understand how the early Internet was underestimated, and the changes that occurred, no matter how slow, were useful. You should not listen to those who say that then everything was better. It was definitely worse, because now we have a business model of the entire Internet, we have accumulated stocks of information, there is monitoring and tracking of all the crap.
But the real “game changer” is the repository. This is the NSA data center in Blafdale, Utah. And your “shit” is not just vulnerable, as long as it is transmitted over the network, it will accumulate there forever.
I was seriously pissed off by Keith Alexander when he came to DefCon 20 because he came here and said: “oh, you guys are so smart, right? Then come and work with me! ” He thinks that it is enough to wear jeans and a T-shirt to convince us that he is a good guy, even if his agency is preventing people from being who they are, preventing the birth of a new generation of hackers.

Think if someone walked here, in our community, with a tape recorder in their hands, shoving it all the time in the face while recording, and recording everything you said, then it would be difficult for you to accept this person as part of your community. You will probably completely stop communicating with this person, but this is what is actually happening now - they collect all the information about us so that they can be used against us. We always assumed that they were doing this, and expected something similar from them, but thanks to our friend Snowden, we now know for sure that they did exactly what we expected from them, and even more. "Collect everything and use everything"! - that's what they do.
You must remember that the government always uses reservations. When they say: “we do not do this!”, This means that we force our foreign partners to do this, and then pass on the results to us. When they say: “we do not collect data under this program”, this means that we collect it under another program.
But we now have a million ways to spoil the existing order of things. If everything you do makes you an “interesting” person, they can come back and find other “interesting things” to hang them on you. And technology is not to blame. We find errors all the time, but their number directly depends on the “error” that is between the chair and the keyboard. People say that they have nothing to hide, we have heard this before a million times. But everyone has something to hide, right? Everyone has always had something to hide, now or in the past, and this is the source of many problems. So people who can do all sorts of tricky things should not screw up when faced with two related groups - organized crime and the federal forces.
Consider what is Tradecraftor spy things. Tradecraft means technology and methods, and here I am going to throw a few stones in the garden of our friends from the CIA. I will laugh at them later, but they spend a lot of time thinking about ways that they might not mess up. The best way to analyze the work of the CIA is to review their operational activities, those operations where they screwed up.
They spend a lot of time analyzing where they failed. You can download and read the Tradecraft manual created by the CIA - the picture on the next slide is taken from there. I will go over the positions shown in this picture:
All these things are reviewed when we analyze our own operations, after having screwed up somewhere. There are a number of activities you can do to counteract bias.
For example, if something interesting happens, this is a great opportunity to switch from analysis to performing a practical operation. The analysis should include the following principles:
Follow these principles when conducting operations and look for points in their applications.
On the opposite side is the OPSEC. Many people in our society are in favor of operational security. Basically, it means preventing the leakage of information, which can lead to the advantage of the other party. The next slide shows a poster from the time of the Second World War confirming this rule: “Enemy ears are listening!”.

By the way, on the topic of "old school" - if I showed this photo to someone under the age of 25, he would surely ask why this is Gandhi's enemy? The laughter in the hall, in the center of the slide, is not a portrait of Gandhi, but the Emperor of Japan, Hirohito.
I can’t wait until finally everyone will get an education from Wikipedia or IMDB. The government uses your tax dollars to release literature to help you with OPSEC, so you need to carefully check this literature. You need to understand what information is relevant.

The government teaches that the bad guys want to get the information that we own in order to hit us. OPSEC confronts this by helping to look at the world with its own eyes in order to develop measures and ways to confront these bad guys.
The process of operational security is as follows:
If you find it difficult to see the text on a slide, you can watch it on the DVD disc of this DefCon conference. OPSEC does not end with the operation itself, it covers all of your initial and all subsequent explanations and studies. "Remember this all the time!" This is not something that can be done once and then forget, OPSEC is working 24 hours a day, 7 days a week.
The next slide shows my version of the seven deadly sins, seven things that can make you screw up.

What makes you a candidate for arrest? Confidence that they will never find you. “I use a standalone computer” is all nonsense, you can never rely on one tool.
This is followed by excessive trust. In the states of total surveillance, for example, in East Germany, one in 66 people was a government informant. Do not you think that this ratio is similar to the hacker community? Emmanuel Goldstein estimated that every fifth person was a “informer” in the GDR. This is probably a high frontier, but talk, for example, with Chelsea Manning. I bet she regrets her model of trust in society.
The perception of insignificance of one’s guilt, the conviction that your guilt is insignificant and therefore your “pranks” do not bother anyone. “No one cares if I simply damage this website.” Remember that all this may be recorded in your personal file.
The fourth "sin" is associative guilt. I visited the “wrong” chat, came to the wrong conference, got in touch with the wrong people. You are worried about exposing where you are and where you came from. This is something that the government can consciously use against you. It does not just collect personal information that identifies you, it saves the “fingerprints” of the pages you visited through the browser, the unique identifiers of your mobile devices, and possibly your location in the future.
There are too many documents confirming that this is happening. Those people who really struggle with the state and do serious business know about it. "Your chatter can kill your friends."

Home computers and personal cell phones should never be used for operational purposes pursued by government services. Identity documents must never be transported without an owner. Details of a military operation should never be discussed by telephone or with family members. You can and should even do things you don’t like to do, just as you don’t like to abstain from alcohol. If you commit at least one of these sins - you are caught. Use Tradecraft analysis techniques to avoid mistakes.
One of the tools you can use to stop these damn things is tools. But tools can also make your situation even worse. A computer is a tool that helps you mess things up a billion times faster than you could do it yourself.
They create a false sense of trust. They provoke the sin of self-confidence, and this is the probability of spoiling everything. Stupid to use the tool is even worse than not using it at all. This is one of my favorite pictures - it's not a saw, but a cutter from a stream of water supplied under a pressure of 15,000 PSI. It's just water, but it cuts steel, although it seems so safe.

Here is the first tool - VPN. Don't mess with it! Will you be safe if you use an insecure network? When it comes to tools, ask yourself 2 questions: should I use it and how should I use it? What do you get from VPN ? You get traffic encryption, but only between you and the VPN itself , but not between the VPN and some remote location.
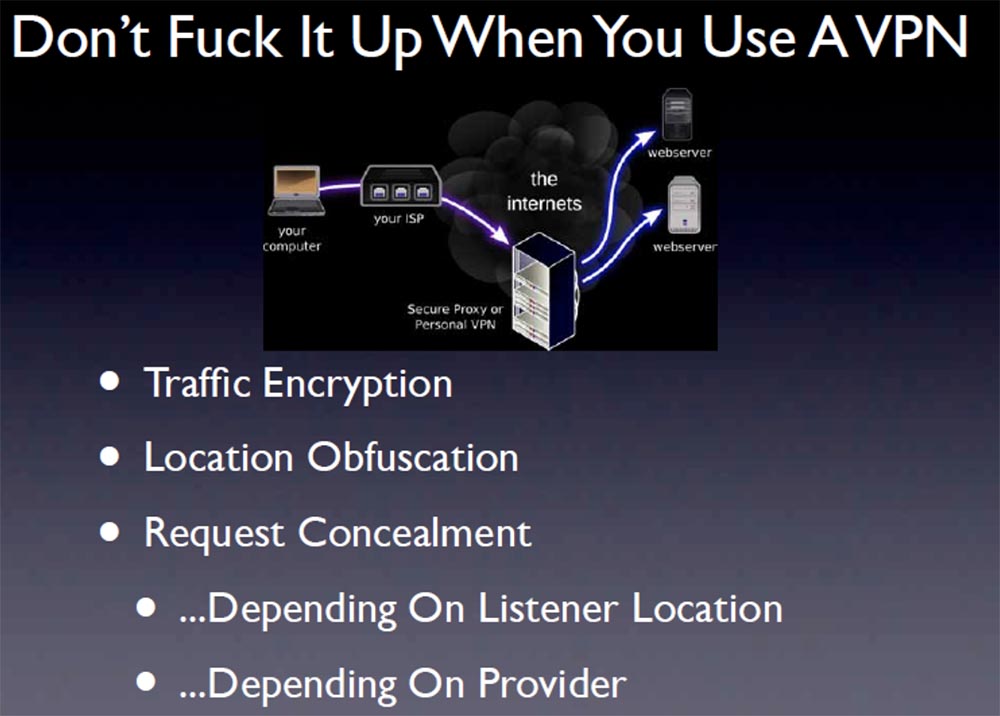
You can confuse your tracks and hide your location from a remote server. The provider may not know exactly where you are. But you can receive from him some kind of request that will establish a connection between you and the VPN. So it really depends on where the “listener” is and how the network provider behaves. This is one hot proxy, so anyone who controls both ends of the network, such as a government agency, can very easily make a traffic correlation and get information about your location. This changes the degree of trust in the VPN provider , with whom you probably have a financial relationship, because it is very easy to track how and to whom you pay for services. Think about it. VPN providersreally very different in relation to the fulfillment of the promise. Many of them say they do not save session logs. You should know their journaling policies, but this will not clarify the whole story to you, especially if they are not located in the United States, because they can start keeping a journal at any time they want. For example, when they receive a prescription from the national security agency, which by law can claim all the data.
Therefore, the fact that they do not record your activity now does not mean that they will not do this in the future if you are interested in the special services.
If you plan to hide behind a VPN , then you better see how the VPN clients differaccording to the degree of "catching you on the hook." Information leaks from them, I saw it with my own eyes. Activate a VPN , run Wire shock or a packet sniffer on another computer and you will see what data is “leaking” from the computer you are going to use for hidden operations.
Do you think all your traffic goes through VPN or not? If these security-related little things require too much effort from you, then “bullying” the Internet is not your business; instead, you should work for the government.
Here is a simple test for laziness. Open SSH connection, start VPNand see how it falls. If the network remains open, your data is still “leaking”.
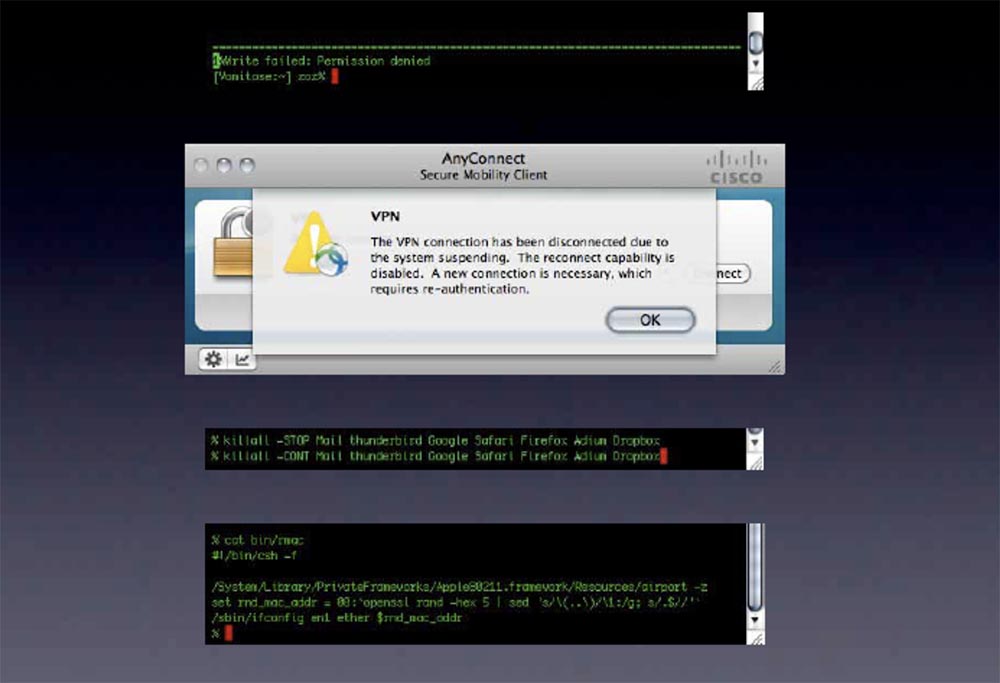
If existing connections are allowed, the “leaked” data may be associated with your real IP. In addition, many VPN clients are not designed to work with mobile devices. Every time you put your computer into sleep mode, the tunnel is broken and after you wake up the computer, you must restore the connection. When this happens, every damn application on your computer “calls home” and tries to reconnect immediately before the VPN itself reconnects, thereby revealing your IP.
Mail clients - browsers with open tabs just love to reload them. These browsers run java scripts in the background and constantly interact with the server. Therefore, despite the fact that you are using a VPN, you are exposed.
So before closing the VPN, be sure to turn off all these processes and they will not work in the background. Of course, it’s hard to keep this in mind and it’s difficult to perform manual checks, so try to automate this process.
Another thing related to this topic is the use of random MAC addresses . Canadian government was exposed in illegal tracking of people using MAC addressesmobile devices using airport wifi networks. So they could follow the movements of people at different airports. I try to randomize my MAC addresses , but often this is not too inconvenient.
So, should you use VPN ? What are the advantages of a virtual private network and what disadvantages does it have? If you go against the “big guys” that monitor both sides of the VPN , you can simply track your traffic. Even in itself, using a VPN makes you interesting for special services. This image is from the 2008 Top Secret XKeyscore Spyware Guide .

This is not a real-time traffic processor, but a database miner. This is a set of filters for saved stolen data. People often tell me that I must be on their list. Well, yes, I use VPN , especially when traveling, so I'm definitely on some list.
The next slide shows the secret tool CES / SSC / AAD VPN “Surge” , or “VPN - Splash” version of March 2011.

It identifies the network, intercepts and stores VPN data . The Birdwatcher program , about which we know nothing, is also mentioned here . This is clearly some kind of data mining program that may use VPN key exchange for subsequent encryption analysis.
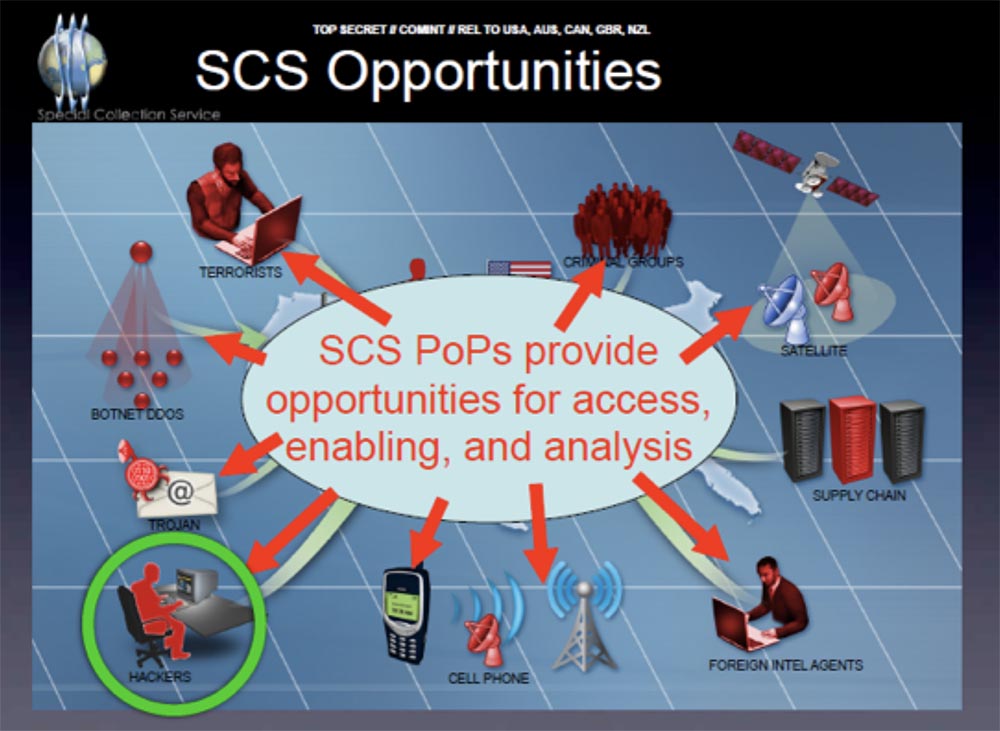
The next slide shows an outline of the SCS surveillance capabilities , and I am very pleased to see the mention of us hackers — I highlighted it in a green circle — in the same company as terrorists, criminal groups, and foreign intelligence agencies, so we run the big business.
Here is another NSA slide, “Black Pearl,” a database of interception points on underwater fiber optic cables that supposedly provide the highest level of connectivity, since this is the foreign endpoint.
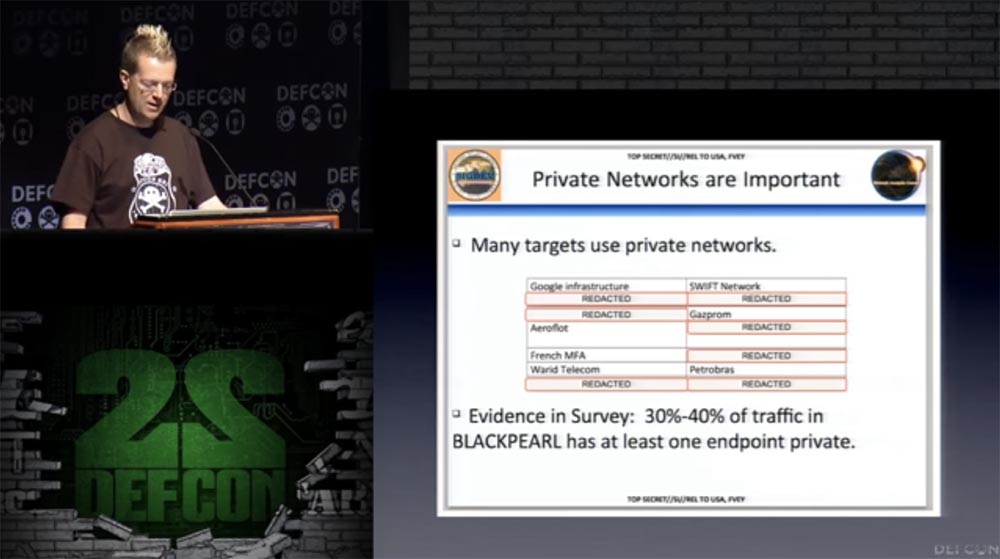 \
\
They can intercept all data, but it is believed that these interception points serve only to collect internal data. This legally justifies a similar surveillance technology. So, again, using VPN- this is what may attract the attention of the special services. Private virtual networks are considered as one of the goals of monitoring the special services, and this is not accidental. However, I do not think that it is necessary to abandon the use of VPN , if this includes you in the list of people who are interested in special services. You can make it harder for them to take countermeasures, but in some cases using a VPN, you should still be careful.
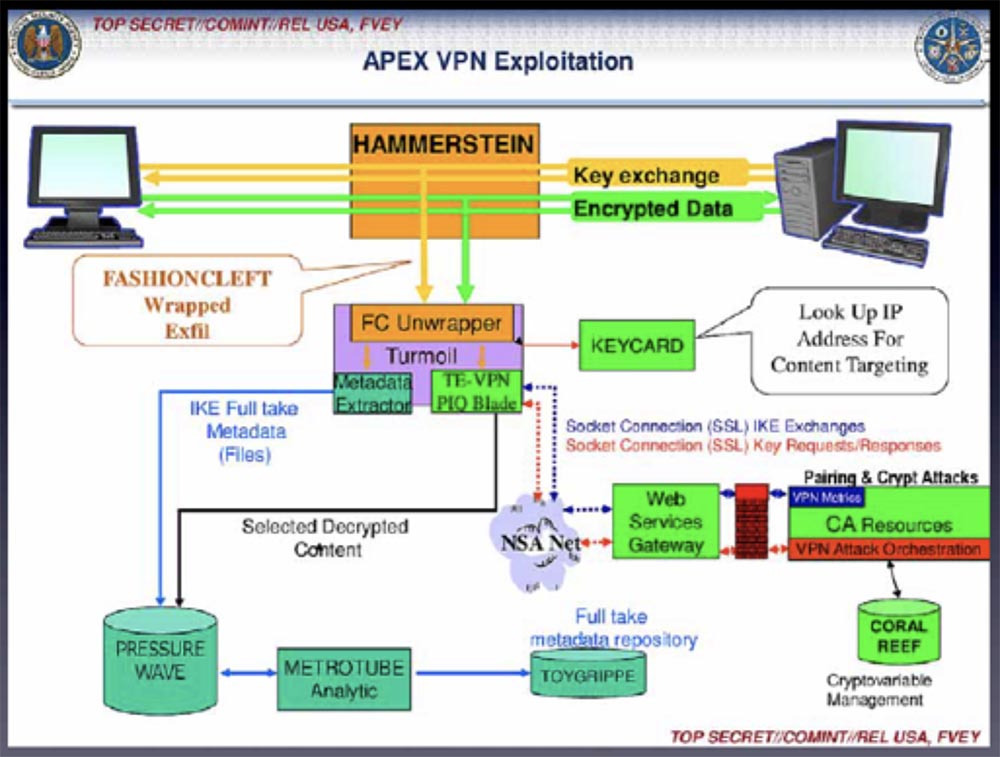
The next slide shows the scheme of the secret program-decoder, which allows you to decrypt the data encryption keys in the virtual network. This program is called Hammersteinuses the man-in-the-middle attack technology. It decrypts Internet traffic by cracking routers and injecting software implants into a private network.
The good news is that their problems are caused by the fact that not all of us are equally vulnerable. But at least some of the spyware programs are cryptographic on PPTP VPN . In 2012, at the DefCon 20 presentation, Moxie Marlinspike, Marsh Ray and David Hotdon talked about the Cloud cracker program for PPTP , which easily hacks VPNs . So VPN still maintains its position in the world of anonymity, but you have to make sure that this network works as it should, and not just rely on its security.
If you're really paranoid, you can jump from one VPN to another every few minutes, some providers offer this service. At the same time you generate really interesting traffic for the NSA , but for wiretapping you create a certain “noise”. But do not screw it up, believing that this jumping proxy server will protect your traffic from all problems. And remember that it leaves a financial footprint that can bring snoops on you if you do not pay for Internet services anonymously.
The following rule: do not screw it up using Tor !

Do not think that Tor encrypts your traffic, it is not. Tordesigned for anonymity, not for encryption. Encryption layers are configured only to protect the routing inside this browser. This does not protect your basic traffic, which also needs to be encrypted. Tor is very, very important. Recently, they started talking about the fact that Thor is broken or that it has federal funding. I do not think that this is true, but we will talk about it now, because I think that what we are doing is really important.
Tor is the main way dissidents go out and talk outside repressive regimes. This is the way ordinary people can search for information and communicate without being monitored or monitored. So it pisses me off when people say that Tor is used only for illegal activities.
So do not screw it up with the "Thor", when doing all sorts of interesting things. A lot of useful traffic passes through it, and even if you are not doing anything “bad”, still use this browser, because this is how you help other people.
People believe that "Thor" is intended only for the bad, so if you have the opportunity, explain to everyone that this is not so. Use hash tags, tweets like "Thor for good" or "Thor forever." The Tor community will appreciate this.
Let's talk a little about the people who have defamed Tor . We all remember these hackers from LulzSec and AntiSec . LulzSec Leader Hector Monsegur, or Sabu, was an FBI informant and sent his group’s attacks to the websites of other countries. 4chan and Nons , trolling on the Internet, injecting vulnerabilities to SQL , DDOS attacks on websites, hacking into user account databases - all this was done under the control of special services.
During the trial of the hacker Anonymous, Jeremy Hammond, he confessed that Sabu, who collaborated with the special services, persuaded him to attack the websites of foreign governments .

The feds controlled the IFC channels available to TOR . They found these channels and waited for someone to break them. Sabuonly once entered the system without using Tor and after a few seconds turned into a informer, because he had nothing left to do, because for such a threat to decades of federal imprisonment. The fact that he received only a few months at the trial confirms that he is a snitch.
But this is not the most interesting. I wonder what happened to Jeremy Hammond. He was identified by information in recorded chat logs from Sabu . The feds registered packet metadata from their Wi-Fi access point, received a chat registry and a trace transcript. Standard listening, right? They checked the Mac address of his computer with the packets going to the Tor login node , matched the network access time.Tor is at his Wi-Fi hotspot with his presence at home, and compared his IP address on the IFC channel . This is a typical attack by the method of correlating traffic, but not of the normal form, which we think about when talking about "Torah". It turns out that Tor has no mechanism to prevent the receipt of circumstantial evidence, which as a result allowed Hammond to go to prison for 10 years. The moral of this story is: using Tor , do not hope that you are completely safe! Such is the moral of Sabu.
Therefore, observe the "hygiene" of being online. Do not simultaneously use two browsers, because you can make a mistake and enter something wrong and in the wrong browser. A good idea is to use a separate computer that connects to the network only through Thor. Use a firewall like PFSence to make sure all your traffic goes through the Tor network , use the IPCheck service to see how your IP address is displayed on the network.
25:00 min.
Conference DEFCON 22. Andrew "Zoz" Brooks. Don't screw it up! Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Henry Toro, in his essay “Civil Disobedience,” wrote: “Unfair laws exist, will we obey them obediently, or will we try to change them, while continuing to obey them, or will we break them right away”?

I was inspired by the fact that I was given the opportunity to talk about this, because the most prominent practitioner in the prosecution of disobedience in our country is the secret police. Such unrepentant criminals, like the former NSA director Michael Hayden, were engaged in telephone wiretaping during Bush’s time, or National Intelligence director James Klepper, who repeatedly lied to Congress - they neglect the law when it is necessary for their own affairs. They tell us that the end justifies the means so that we too can play this game. We are obliged to apply civil disobedience where there is a wrong law that introduces the United States into a state of constant surveillance in the name of the fight against terrorism, which is also related to this country, as public health problems are associated with the bubonic plague of the 14th century. This is worse than a crime, it's just stupid. Therefore, we must not allow the spying state to prevent us from doing the right things.
Think of the DCSS crypto wars, which are designed to protect media tycoons from hackers playing their legally purchased DVDs on laptops running Linux. They came up with a DVD encryption code that was hindering this, which was completely illegal. This is a perfect example of a law that is worse than a criminal one, it is stupid, because it can only hurt people who legitimately use media resources.
Of course, hackers are obliged to shove a stick in the asses of the people responsible for these laws, making illegal T-shirts, ties, games or illegal Minesweeper for Windows (laughter in the hall).

Of course, in our time there are more or less trivial injustices to be disobedient. Starting with violations of the crappy user agreements EULA and ending with the use of technology to counter the truly tyrannical and oppressive regimes that exist on earth today.
"Give a man a mortar" - for this today there is a corresponding application. The fact is that using technology to push the boundaries is what people at this conference are doing. In fact, in most cases, you have no idea whether what you are doing is legal or illegal. No one except the Congressional Research Service dared to state that they did not know the exact number of federal laws in force in the region at a given time. So even a good lawyer will not say whether his client is doing something illegal or not.
Keep in mind that laws in this and other countries are interpreted in terms of historical precedents. It also matters when you are accused of something. Forget about deliberate disobedience, because people constantly break the law without knowing it, so be careful.

Here is one of my favorite examples of DefCon. This slide shows an example of disobedience, but a good one. DefCon is full of such examples.

I think we can agree that breaking into other people's bank accounts is illegal. One of my favorite moments at DefCon was a meeting with a guy who hacked into the database of “Nigerian scammers,” got their bank account details and got some money back from them.
Leakage and drain of information from government agencies and similar types of disobedience are currently in vogue and, I think, useful to society. Much of what has been leaked in the media lately comes down to controlling the Internet. People with much more money and power than those who are present in this room are trying to block it for the lower classes. Disobedience is part of such resistance to the control and pressure of the authorities. Blocking the Internet, the end of the free flow of information, regardless of the wealth of power and whatever that information carries is the end of the Internet.

Therefore, we must refuse to be obedient. If you are going to deliberately disobey, there is only one rule that is worth adhering to, and whoever was on the Hacker Jeopardy team knows these three words very well: “Fuck It Up”! - “Don't screw it up!”
Another reason that inspired me to this presentation was Snowden’s information leaks published last year. I would like to share some thoughts on this and invite the community to take part in the discussion. This is a conversation for all who did not have free time to get acquainted with all these leaks. If everyone present knows what I'm going to say, I will be very happy, but this is probably not the case.
Remember the good old days, when the Internet has not yet switched to the "kitty" humor? Now everyone on the Internet knows what an ASCII goatse is (laughter in the hall). Google even kindly offers this drawing.

But in reality, the good old days were not so good. I do not consider myself to be an old school, because I started to be engaged in our business only in the early 90s. It took a quarter of a century to understand how the early Internet was underestimated, and the changes that occurred, no matter how slow, were useful. You should not listen to those who say that then everything was better. It was definitely worse, because now we have a business model of the entire Internet, we have accumulated stocks of information, there is monitoring and tracking of all the crap.
But the real “game changer” is the repository. This is the NSA data center in Blafdale, Utah. And your “shit” is not just vulnerable, as long as it is transmitted over the network, it will accumulate there forever.
I was seriously pissed off by Keith Alexander when he came to DefCon 20 because he came here and said: “oh, you guys are so smart, right? Then come and work with me! ” He thinks that it is enough to wear jeans and a T-shirt to convince us that he is a good guy, even if his agency is preventing people from being who they are, preventing the birth of a new generation of hackers.

Think if someone walked here, in our community, with a tape recorder in their hands, shoving it all the time in the face while recording, and recording everything you said, then it would be difficult for you to accept this person as part of your community. You will probably completely stop communicating with this person, but this is what is actually happening now - they collect all the information about us so that they can be used against us. We always assumed that they were doing this, and expected something similar from them, but thanks to our friend Snowden, we now know for sure that they did exactly what we expected from them, and even more. "Collect everything and use everything"! - that's what they do.

You must remember that the government always uses reservations. When they say: “we do not do this!”, This means that we force our foreign partners to do this, and then pass on the results to us. When they say: “we do not collect data under this program”, this means that we collect it under another program.
But we now have a million ways to spoil the existing order of things. If everything you do makes you an “interesting” person, they can come back and find other “interesting things” to hang them on you. And technology is not to blame. We find errors all the time, but their number directly depends on the “error” that is between the chair and the keyboard. People say that they have nothing to hide, we have heard this before a million times. But everyone has something to hide, right? Everyone has always had something to hide, now or in the past, and this is the source of many problems. So people who can do all sorts of tricky things should not screw up when faced with two related groups - organized crime and the federal forces.
Consider what is Tradecraftor spy things. Tradecraft means technology and methods, and here I am going to throw a few stones in the garden of our friends from the CIA. I will laugh at them later, but they spend a lot of time thinking about ways that they might not mess up. The best way to analyze the work of the CIA is to review their operational activities, those operations where they screwed up.
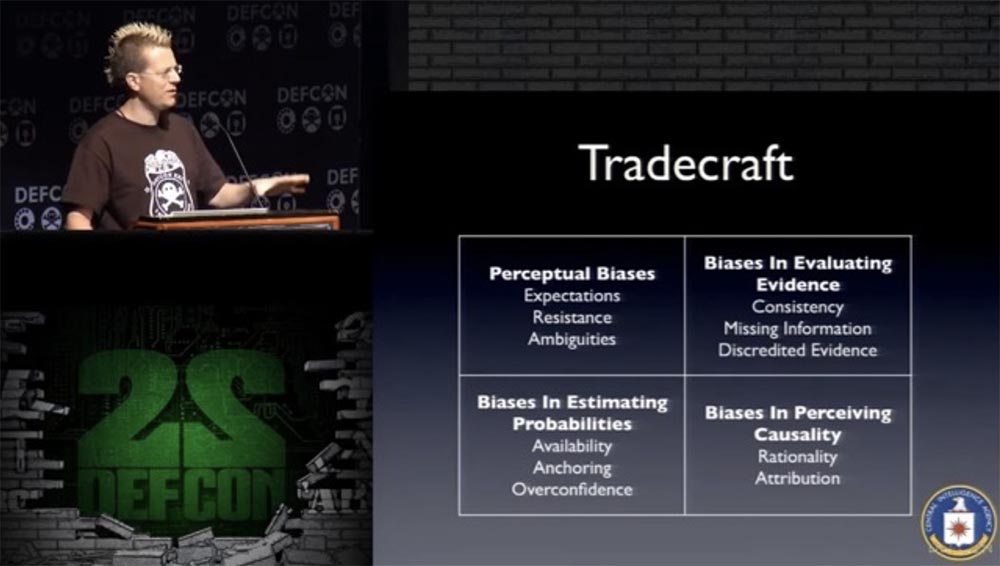
They spend a lot of time analyzing where they failed. You can download and read the Tradecraft manual created by the CIA - the picture on the next slide is taken from there. I will go over the positions shown in this picture:
- Perceptual distortions: expectation, resistance, inaccuracies. This means seeing only what we want to see. I think you can find examples of this behavior by the CIA.
- Bias in the assessment of evidence: consistency, lack of information, discredited evidence. If there is a sequence in something, then small samples are more consistent, but they contain less information. If you rely only on the available probability estimation models, problems arise with a causal relationship — for example, assigning events to a fixed background. Something like "Sunni good, Shiites - bad."
- Bias in assessing probabilities: accessibility, affection, overconfidence.
- Bias in the perception of causality: rationalism, registry.

All these things are reviewed when we analyze our own operations, after having screwed up somewhere. There are a number of activities you can do to counteract bias.
For example, if something interesting happens, this is a great opportunity to switch from analysis to performing a practical operation. The analysis should include the following principles:
- verification of key assumptions at the beginning or when a project is modified;
- checking the quality of information;
- go from the reverse, that is, to use the technique “devil's advocate”, the technique “bounce - weak resistance”, analyze situations like: “what if ...” and try actions familiar to us in penetration testing. Here they are called "Red Team", whose actions are to put themselves in the place of the enemy.
Follow these principles when conducting operations and look for points in their applications.
On the opposite side is the OPSEC. Many people in our society are in favor of operational security. Basically, it means preventing the leakage of information, which can lead to the advantage of the other party. The next slide shows a poster from the time of the Second World War confirming this rule: “Enemy ears are listening!”.

By the way, on the topic of "old school" - if I showed this photo to someone under the age of 25, he would surely ask why this is Gandhi's enemy? The laughter in the hall, in the center of the slide, is not a portrait of Gandhi, but the Emperor of Japan, Hirohito.
I can’t wait until finally everyone will get an education from Wikipedia or IMDB. The government uses your tax dollars to release literature to help you with OPSEC, so you need to carefully check this literature. You need to understand what information is relevant.

The government teaches that the bad guys want to get the information that we own in order to hit us. OPSEC confronts this by helping to look at the world with its own eyes in order to develop measures and ways to confront these bad guys.
The process of operational security is as follows:
- Identification of critical information, access to which is capable of harming us;
- Analysis of threats of theft of this information;
- Analysis of vulnerabilities that allow to carry out the threat;
- Risk assessment;
- The use of countermeasures.
If you find it difficult to see the text on a slide, you can watch it on the DVD disc of this DefCon conference. OPSEC does not end with the operation itself, it covers all of your initial and all subsequent explanations and studies. "Remember this all the time!" This is not something that can be done once and then forget, OPSEC is working 24 hours a day, 7 days a week.
The next slide shows my version of the seven deadly sins, seven things that can make you screw up.

What makes you a candidate for arrest? Confidence that they will never find you. “I use a standalone computer” is all nonsense, you can never rely on one tool.
This is followed by excessive trust. In the states of total surveillance, for example, in East Germany, one in 66 people was a government informant. Do not you think that this ratio is similar to the hacker community? Emmanuel Goldstein estimated that every fifth person was a “informer” in the GDR. This is probably a high frontier, but talk, for example, with Chelsea Manning. I bet she regrets her model of trust in society.
The perception of insignificance of one’s guilt, the conviction that your guilt is insignificant and therefore your “pranks” do not bother anyone. “No one cares if I simply damage this website.” Remember that all this may be recorded in your personal file.
The fourth "sin" is associative guilt. I visited the “wrong” chat, came to the wrong conference, got in touch with the wrong people. You are worried about exposing where you are and where you came from. This is something that the government can consciously use against you. It does not just collect personal information that identifies you, it saves the “fingerprints” of the pages you visited through the browser, the unique identifiers of your mobile devices, and possibly your location in the future.
There are too many documents confirming that this is happening. Those people who really struggle with the state and do serious business know about it. "Your chatter can kill your friends."

Home computers and personal cell phones should never be used for operational purposes pursued by government services. Identity documents must never be transported without an owner. Details of a military operation should never be discussed by telephone or with family members. You can and should even do things you don’t like to do, just as you don’t like to abstain from alcohol. If you commit at least one of these sins - you are caught. Use Tradecraft analysis techniques to avoid mistakes.
One of the tools you can use to stop these damn things is tools. But tools can also make your situation even worse. A computer is a tool that helps you mess things up a billion times faster than you could do it yourself.
They create a false sense of trust. They provoke the sin of self-confidence, and this is the probability of spoiling everything. Stupid to use the tool is even worse than not using it at all. This is one of my favorite pictures - it's not a saw, but a cutter from a stream of water supplied under a pressure of 15,000 PSI. It's just water, but it cuts steel, although it seems so safe.

Here is the first tool - VPN. Don't mess with it! Will you be safe if you use an insecure network? When it comes to tools, ask yourself 2 questions: should I use it and how should I use it? What do you get from VPN ? You get traffic encryption, but only between you and the VPN itself , but not between the VPN and some remote location.

You can confuse your tracks and hide your location from a remote server. The provider may not know exactly where you are. But you can receive from him some kind of request that will establish a connection between you and the VPN. So it really depends on where the “listener” is and how the network provider behaves. This is one hot proxy, so anyone who controls both ends of the network, such as a government agency, can very easily make a traffic correlation and get information about your location. This changes the degree of trust in the VPN provider , with whom you probably have a financial relationship, because it is very easy to track how and to whom you pay for services. Think about it. VPN providersreally very different in relation to the fulfillment of the promise. Many of them say they do not save session logs. You should know their journaling policies, but this will not clarify the whole story to you, especially if they are not located in the United States, because they can start keeping a journal at any time they want. For example, when they receive a prescription from the national security agency, which by law can claim all the data.
Therefore, the fact that they do not record your activity now does not mean that they will not do this in the future if you are interested in the special services.
If you plan to hide behind a VPN , then you better see how the VPN clients differaccording to the degree of "catching you on the hook." Information leaks from them, I saw it with my own eyes. Activate a VPN , run Wire shock or a packet sniffer on another computer and you will see what data is “leaking” from the computer you are going to use for hidden operations.

Do you think all your traffic goes through VPN or not? If these security-related little things require too much effort from you, then “bullying” the Internet is not your business; instead, you should work for the government.
Here is a simple test for laziness. Open SSH connection, start VPNand see how it falls. If the network remains open, your data is still “leaking”.

If existing connections are allowed, the “leaked” data may be associated with your real IP. In addition, many VPN clients are not designed to work with mobile devices. Every time you put your computer into sleep mode, the tunnel is broken and after you wake up the computer, you must restore the connection. When this happens, every damn application on your computer “calls home” and tries to reconnect immediately before the VPN itself reconnects, thereby revealing your IP.
Mail clients - browsers with open tabs just love to reload them. These browsers run java scripts in the background and constantly interact with the server. Therefore, despite the fact that you are using a VPN, you are exposed.
So before closing the VPN, be sure to turn off all these processes and they will not work in the background. Of course, it’s hard to keep this in mind and it’s difficult to perform manual checks, so try to automate this process.
Another thing related to this topic is the use of random MAC addresses . Canadian government was exposed in illegal tracking of people using MAC addressesmobile devices using airport wifi networks. So they could follow the movements of people at different airports. I try to randomize my MAC addresses , but often this is not too inconvenient.
So, should you use VPN ? What are the advantages of a virtual private network and what disadvantages does it have? If you go against the “big guys” that monitor both sides of the VPN , you can simply track your traffic. Even in itself, using a VPN makes you interesting for special services. This image is from the 2008 Top Secret XKeyscore Spyware Guide .

This is not a real-time traffic processor, but a database miner. This is a set of filters for saved stolen data. People often tell me that I must be on their list. Well, yes, I use VPN , especially when traveling, so I'm definitely on some list.
The next slide shows the secret tool CES / SSC / AAD VPN “Surge” , or “VPN - Splash” version of March 2011.

It identifies the network, intercepts and stores VPN data . The Birdwatcher program , about which we know nothing, is also mentioned here . This is clearly some kind of data mining program that may use VPN key exchange for subsequent encryption analysis.
The next slide shows an outline of the SCS surveillance capabilities , and I am very pleased to see the mention of us hackers — I highlighted it in a green circle — in the same company as terrorists, criminal groups, and foreign intelligence agencies, so we run the big business.

Here is another NSA slide, “Black Pearl,” a database of interception points on underwater fiber optic cables that supposedly provide the highest level of connectivity, since this is the foreign endpoint.
 \
\ They can intercept all data, but it is believed that these interception points serve only to collect internal data. This legally justifies a similar surveillance technology. So, again, using VPN- this is what may attract the attention of the special services. Private virtual networks are considered as one of the goals of monitoring the special services, and this is not accidental. However, I do not think that it is necessary to abandon the use of VPN , if this includes you in the list of people who are interested in special services. You can make it harder for them to take countermeasures, but in some cases using a VPN, you should still be careful.
The next slide shows the scheme of the secret program-decoder, which allows you to decrypt the data encryption keys in the virtual network. This program is called Hammersteinuses the man-in-the-middle attack technology. It decrypts Internet traffic by cracking routers and injecting software implants into a private network.

The good news is that their problems are caused by the fact that not all of us are equally vulnerable. But at least some of the spyware programs are cryptographic on PPTP VPN . In 2012, at the DefCon 20 presentation, Moxie Marlinspike, Marsh Ray and David Hotdon talked about the Cloud cracker program for PPTP , which easily hacks VPNs . So VPN still maintains its position in the world of anonymity, but you have to make sure that this network works as it should, and not just rely on its security.
If you're really paranoid, you can jump from one VPN to another every few minutes, some providers offer this service. At the same time you generate really interesting traffic for the NSA , but for wiretapping you create a certain “noise”. But do not screw it up, believing that this jumping proxy server will protect your traffic from all problems. And remember that it leaves a financial footprint that can bring snoops on you if you do not pay for Internet services anonymously.
The following rule: do not screw it up using Tor !

Do not think that Tor encrypts your traffic, it is not. Tordesigned for anonymity, not for encryption. Encryption layers are configured only to protect the routing inside this browser. This does not protect your basic traffic, which also needs to be encrypted. Tor is very, very important. Recently, they started talking about the fact that Thor is broken or that it has federal funding. I do not think that this is true, but we will talk about it now, because I think that what we are doing is really important.
Tor is the main way dissidents go out and talk outside repressive regimes. This is the way ordinary people can search for information and communicate without being monitored or monitored. So it pisses me off when people say that Tor is used only for illegal activities.
So do not screw it up with the "Thor", when doing all sorts of interesting things. A lot of useful traffic passes through it, and even if you are not doing anything “bad”, still use this browser, because this is how you help other people.
People believe that "Thor" is intended only for the bad, so if you have the opportunity, explain to everyone that this is not so. Use hash tags, tweets like "Thor for good" or "Thor forever." The Tor community will appreciate this.
Let's talk a little about the people who have defamed Tor . We all remember these hackers from LulzSec and AntiSec . LulzSec Leader Hector Monsegur, or Sabu, was an FBI informant and sent his group’s attacks to the websites of other countries. 4chan and Nons , trolling on the Internet, injecting vulnerabilities to SQL , DDOS attacks on websites, hacking into user account databases - all this was done under the control of special services.
During the trial of the hacker Anonymous, Jeremy Hammond, he confessed that Sabu, who collaborated with the special services, persuaded him to attack the websites of foreign governments .

The feds controlled the IFC channels available to TOR . They found these channels and waited for someone to break them. Sabuonly once entered the system without using Tor and after a few seconds turned into a informer, because he had nothing left to do, because for such a threat to decades of federal imprisonment. The fact that he received only a few months at the trial confirms that he is a snitch.
But this is not the most interesting. I wonder what happened to Jeremy Hammond. He was identified by information in recorded chat logs from Sabu . The feds registered packet metadata from their Wi-Fi access point, received a chat registry and a trace transcript. Standard listening, right? They checked the Mac address of his computer with the packets going to the Tor login node , matched the network access time.Tor is at his Wi-Fi hotspot with his presence at home, and compared his IP address on the IFC channel . This is a typical attack by the method of correlating traffic, but not of the normal form, which we think about when talking about "Torah". It turns out that Tor has no mechanism to prevent the receipt of circumstantial evidence, which as a result allowed Hammond to go to prison for 10 years. The moral of this story is: using Tor , do not hope that you are completely safe! Such is the moral of Sabu.
Therefore, observe the "hygiene" of being online. Do not simultaneously use two browsers, because you can make a mistake and enter something wrong and in the wrong browser. A good idea is to use a separate computer that connects to the network only through Thor. Use a firewall like PFSence to make sure all your traffic goes through the Tor network , use the IPCheck service to see how your IP address is displayed on the network.
25:00 min.
Conference DEFCON 22. Andrew "Zoz" Brooks. Don't screw it up! Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
