OceanLotus: New Backdoor, Old Schemes
The OceanLotus Group (aka APT32 and APT-C-00) is known for its attacks in East Asia. Last year, a number of studies on the group’s work were published, including CyberReason documents , a FireEye review, and a description of the watering-hole of the Volexity attack . As we can see, the group updates the backdoors, infrastructure and infection vectors.
OceanLotus continues to target companies and government agencies in East Asian countries. According to ESET telemetry, OceanLotus’s priorities are in Vietnam, Laos, Cambodia and the Philippines.
A few months ago, we discovered and analyzed one of their newest backdoors. It implements several tools that make it difficult to analyze and avoid detection - and we will discuss them in a post.

To convince the victim to launch a malicious dropper, the attackers use different methods.
There is a possibility that droppers are distributed via e-mail attachments. We observed the following file names:
-
-
-
-
-
-
-
All of these files have something in common - the launch of a password-protected bait document. It is unclear whether somewhere in the data of the transmitted letter is a password, or the document should not open.
Several fake installers posing as installers or software updates were seen in watering hole campaigns. One example is the repackaged Firefox installer described by 360 Labs on Freebuf (in Chinese).
The other pattern that we saw was called
All described files, whether they were distributed via mail or downloaded when visiting a compromised site, delivered the same backdoor component. In the post we will analyze the sample
The installation and execution process depends on multi-layer obfuscation, namely, component encryption, PE file reconstruction, shell-code loading and side-loading technology (fill). The latter was described in a previous ESET study on the Korplug .
The attack consists of two parts: the dropper and the launcher. Each step of each part of the process will be explained in detail in the corresponding section. The two schemes below provide a brief overview of the overall progress of malware.
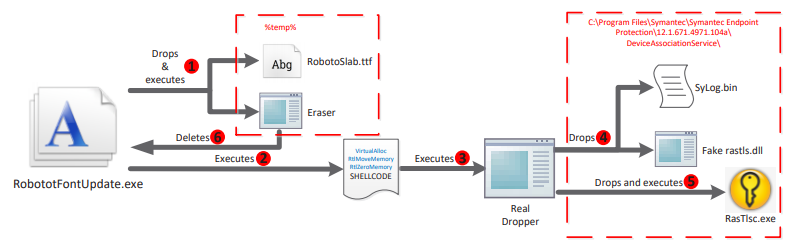
Figure 1. The progress of the dropper
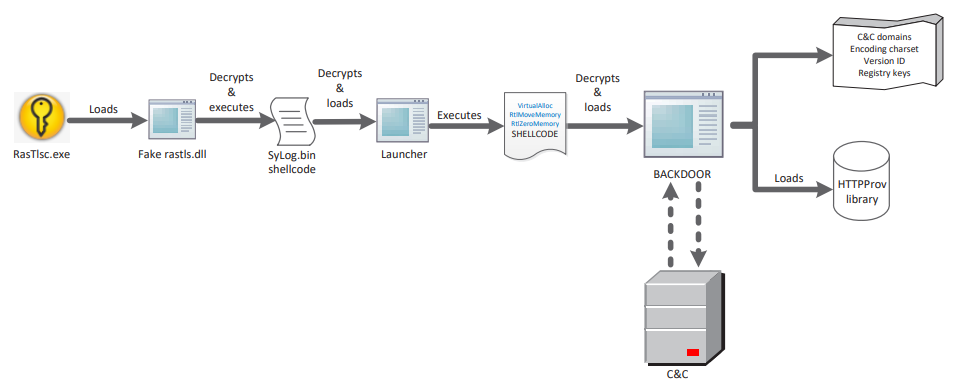
Figure 2. The progress of the backdoor
Almost all of these components are obfuscated. Obfuscation is based on teams of a pair of complementary conditional transition. For each of the forms: JZ / JNZ, JP / JNP, JO / JNO, and so on, each pair makes the transition to the same goal. The sequence is interspersed with garbage code that uses the stack pointer, but does not change the value of the conditional flag. It turns out that the transition takes place within the same branch. This leads to problems in the decompilation process due to the use of positive values of the stack pointer.
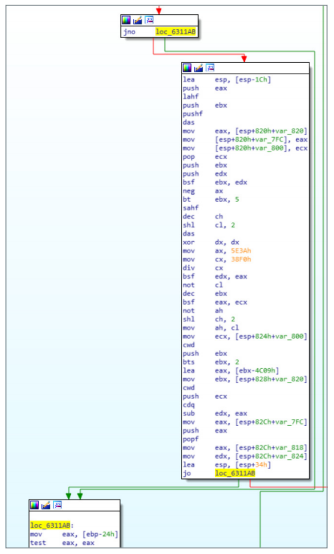
Figure 3. Complementary conditional branch
In addition, some basic program elements add one address to the stack, and then end on a JMP / CALL, while other basic elements add two addresses and end with the RET command. The second addition of an element is the called function, and the first is the address of the next basic program element where the transition will be made. This creates the basic elements of the program without parent objects.

Figure 4. PUSH / JMP
technique As a result of combining the two obfuscation techniques, “beautiful” graphics are obtained:
Figure 5. Obfuscating the execution sequence
Observing the garbage code is quite simple. It can be ignored when analyzing samples, if you know the scheme of application.
In recent months, OceanLotus used several baits. One of them is the fake

Figure 6. RobototFontUpdate font update icon.
When executing, a binary file decrypts its resources (XOR, 128 bytes, hard-coded key) and recovers decrypted data (LZMA). The legitimate RobotoSlab-Regular.ttf
(SHA1:)
The shellcode is executed, decoded from resources. After performing a fake font update, it injects another application whose sole purpose is to remove the dropper. This "erasing" application is implemented in the form
The same shellcode is applied at each stage.
Shell code - custom PE loader. It restores the executable file in memory - decrypts all sections and calculates the necessary movements and other indents. Shellcode uses three functions of the API the Windows:
The function is
The shell code calls the input function in the decrypted PE, and then the export function
This executable file decrypts resources using AES algorithm in CBC mode through Windows API. Hard-coded key has a size of 256 bits. After decryption, the compressed data is unpacked (LZMA algorithm).
If the process is run as an administrator, the malware ensures persistence by creating a service. Otherwise, use the classic registry key Run (
If the dropper code is executed with administrator rights, it tries to write the files listed below to the folder
-
-
-
The path changes from sample to sample, but the scheme is similar. Depending on the rights, the malware resets files to
-
-
-
These paths are used by various Symantec products.
After reaching the persistence and implementation of the executable file, the legitimate file,,
We also observed a version (
The OceanLotus team uses an old and well-known technique in one of the executable files of the Symantec product. The point is to use the process of loading a legitimate and signed .exe library file by writing a malicious library into the same folder. This will make the malicious behavior look legitimate, since these actions are performed during the operation of the trusted executable file.
As mentioned above, a legitimate file is reset and executed
It imports the file
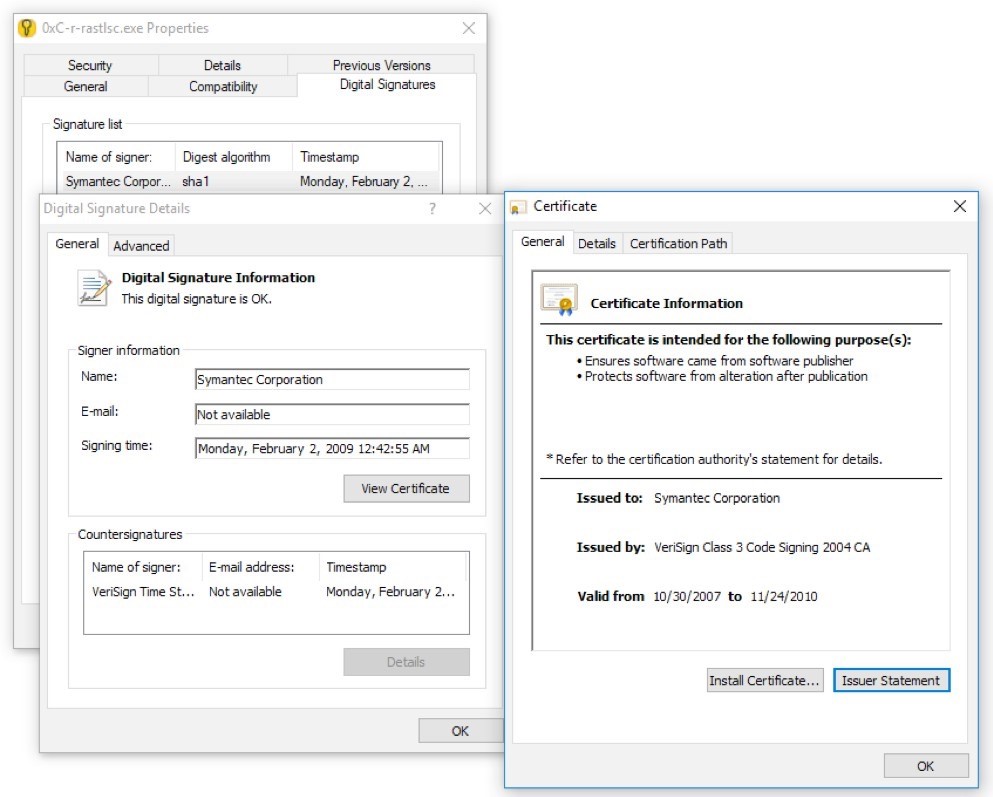
Figure 7. Digital signature rastlsc.exe from Symantec
We also saw a fill using other legitimate and signed executable files, including
Internal dll file name -
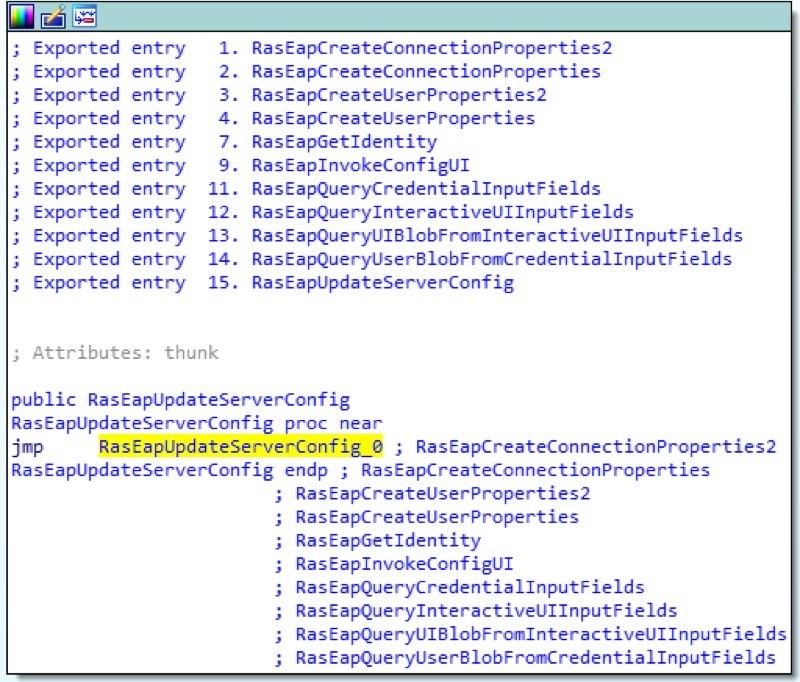
Figure 8. All rasltls.dll exports lead to the execution of a single function.
Export tries to read a file
Option
The following pseudo-code is used to create the shellcode: Below in the picture you can see the listing of the assembler work: Figure 9. Generated shell-code
Shell code decrypts and loads the library
The option
First, the malware tries to download its resources and decrypt them using the RC4 algorithm. The resulting resources contain the data used to configure the backdoor. The configuration format is easy to learn. Using the Kaitai struct and its structure dumper, we get the following:
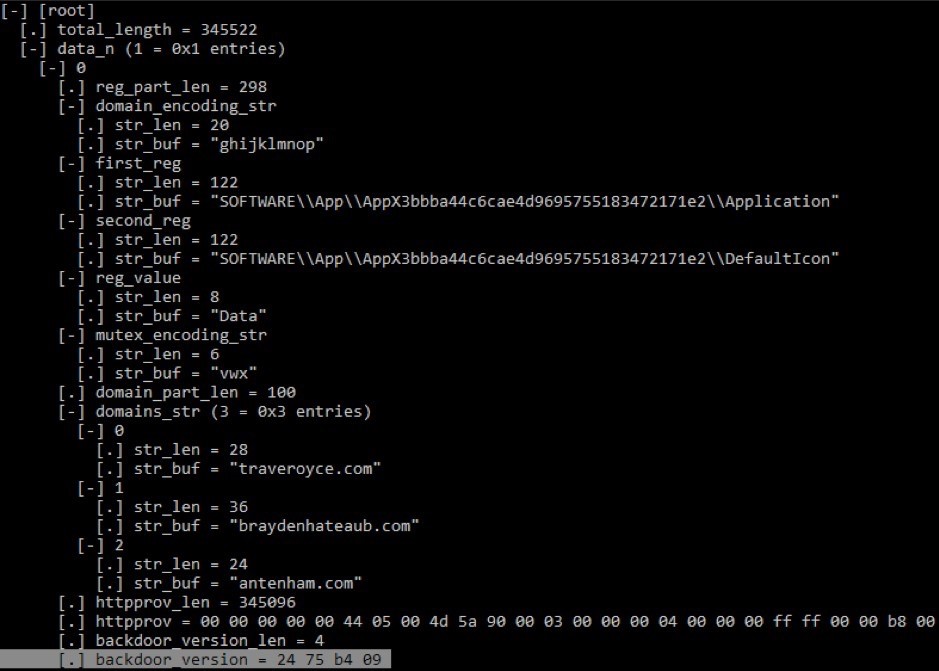
Figure 10. Configuration structure
Note : with the exception of the domain_encoding_str string and the httpprov library, the data changes from sample to sample. The registry keys are almost the same, but they have a similar scheme:
The malicious program gets the first 10 bytes of the username (UTF-16), ckorit them with a three-letter string
The backdoor includes a PE loader that loads the library
The backdoor uses the standard TCP communication port
The malware selects one of the three domains from the configuration and adds a special subdomain, which is generated using two values. The first value is the computer name within the length of 16 bytes. The second is a four-byte version ID. The code in Python 2 below is a coding algorithm: For example, if the computer name and version ID is 0x0a841523, the following domain is generated: You can use the following regular expression for the C & C server label of this backdoor: If the IP address belongs to a specific domain, Malware tries to set TCP connection via port
The communication process is RC4 encrypted and compressed using LZMA. It is possible to decrypt traffic, as the key is added to the beginning of the packets. The format is as follows:
Each key byte is generated by a function
The first time a client connects to the server, a UUID is sent, which is used as a session identifier. The latter is stored in the registry key as binary data:
As we said earlier, the backdoor also contains a library called
After initialization, the registry entry will be created - a team backdoor for later use HTTP to communicate with the server command:
It uses a standard client application:
The main characteristic of this library is a special algorithm for encrypting the universal resource identifier. The resource part of the URI is created using the following pseudo-code: Note : for clarity, the part responsible for checking the string length has been removed from the code.
To obtain an identifier from the generated string, two numbers are added using a special sum-checking algorithm: Adding the library URI generator, we get the following URL:
After obtaining the SESSIONID session ID, the backdoor makes a digital fingerprint of the system. The package is built as follows (indent in the package - description):
0x000 - byte: the value changes in each version
0x001 - 0x01: hard-coded byte
0x002 - bool: elevated privileges
0x003 - dword: ID version
0x007 - string (UTF-16), computer name (. max 0x20)
0x027 - line (UTF-16), user name
0x079 - query result in the register in the
0x179 -% s subsequent line format (% s); is replaced by (
0x279 - physical disk control "input-output" device PhysicalDrive deviceIOControl 0x2D1400 (IOCTL_STORAGE_QUERY_ PROPERTY) (VolSerialNumber)
0x379 - wmi
0x3f9 - Preparation of the current date and time GetSystemTimeAsFileTime
0x400 - bool: unknown
0x401 - dword: obtained after decryption resource
is an example of the digital fingerprint Systems:
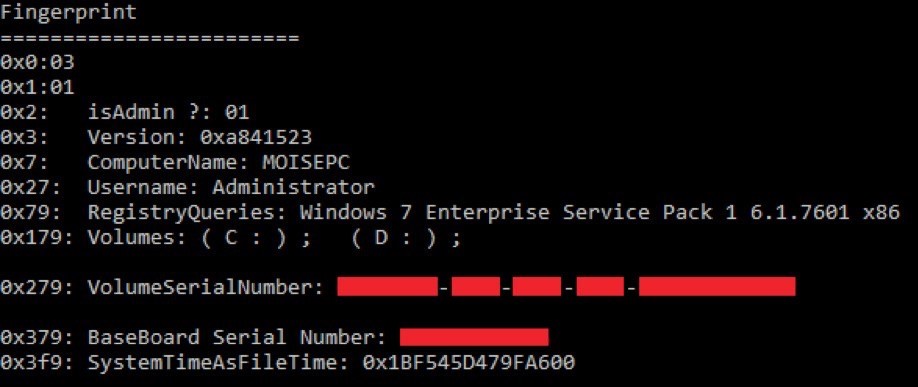
Figure 11. Digital Fingerprint of the System
This is a full-fledged backdoor, which provides its operators with a number of possibilities: manipulations with the file, registry and processes, loading of additional components, obtaining a digital fingerprint of the system. Below are the numbers and descriptions of supported commands:
0 - digital fingerprint
1 - sets the session ID
2 - creates the process and gets the result (using software channels)
3 - sets the connection attempt count
4 - defers the polling time
5 - reads a file or registry key and counts MD5
6 - creates process
7 - creates a file, entry in the registry or stream in memory
8 - writes to registry
9 - polls registry
10 - searches files in system
11 - transfers files to another directory
12 - deletes files from disk
13 - retrieves a list of disks marked in the system using function
14 - creates directory
15 - removes directo riu
16 - reads file from offset
17 - calls the PE loader (transition to communication by
18 - [unknown]
19 - 0: polling the value in the registry; 1: implementation and execution of the program
20 - sets the environment variable
21 - runs the shellcode in the new thread
22 - returns the environment variable
+23 in the new version - restarts itself if the environment variable APPL does not exist
OceanLotus remains highly active and continues to update the toolkit.
The group seeks to hide its activities; to do this, attackers carefully select victims, limit the spread of malicious programs, use several servers in order not to draw attention to a single domain or IP address. Deciphering the injected component and the fill technique (side-loading), despite being widely known, avoids detection, since the work of intruders in this case is disguised as a legitimate application.

OceanLotus continues to target companies and government agencies in East Asian countries. According to ESET telemetry, OceanLotus’s priorities are in Vietnam, Laos, Cambodia and the Philippines.
A few months ago, we discovered and analyzed one of their newest backdoors. It implements several tools that make it difficult to analyze and avoid detection - and we will discuss them in a post.

Spread
To convince the victim to launch a malicious dropper, the attackers use different methods.
Dual extensions and fake application icons (Word, PDF, etc.)
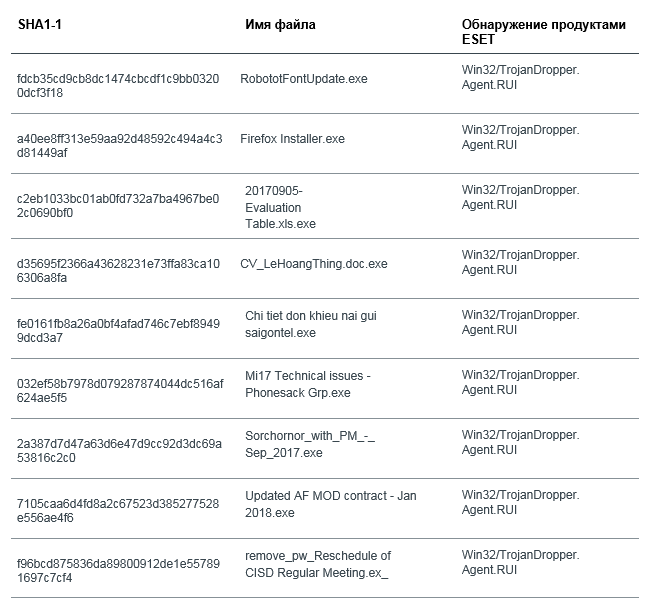
There is a possibility that droppers are distributed via e-mail attachments. We observed the following file names:
-
Mi17 Technical issues - Phonesack Grp.exe(Mi-17 - Russian helicopter model) -
Chi tiet don khieu nai gui saigontel.exe(translated from Vietnamese - “details of the claim sent to Saigontel”, Saigontel — Vietnamese telecommunication company) -
Updated AF MOD contract - Jan 2018.exe-
remove_pw_Reschedule of CISD Regular Meeting.exe-
Sorchornor_with_PM_-_Sep_2017.exe-
20170905-Evaluation Table.xls.exe-
CV_LeHoangThing.doc.exe(fake resumes were also found in Canada) All of these files have something in common - the launch of a password-protected bait document. It is unclear whether somewhere in the data of the transmitted letter is a password, or the document should not open.
Fake installers
Several fake installers posing as installers or software updates were seen in watering hole campaigns. One example is the repackaged Firefox installer described by 360 Labs on Freebuf (in Chinese).
The other pattern that we saw was called
RobototFontUpdate.exe. It probably spread through compromised sites, but we do not have sufficient evidence of this. All described files, whether they were distributed via mail or downloaded when visiting a compromised site, delivered the same backdoor component. In the post we will analyze the sample
RobototFontUpdate.exeand show how it manages to execute the malicious payload in the system.Technical analysis
The installation and execution process depends on multi-layer obfuscation, namely, component encryption, PE file reconstruction, shell-code loading and side-loading technology (fill). The latter was described in a previous ESET study on the Korplug .
Review progress
The attack consists of two parts: the dropper and the launcher. Each step of each part of the process will be explained in detail in the corresponding section. The two schemes below provide a brief overview of the overall progress of malware.

Figure 1. The progress of the dropper

Figure 2. The progress of the backdoor
Almost all of these components are obfuscated. Obfuscation is based on teams of a pair of complementary conditional transition. For each of the forms: JZ / JNZ, JP / JNP, JO / JNO, and so on, each pair makes the transition to the same goal. The sequence is interspersed with garbage code that uses the stack pointer, but does not change the value of the conditional flag. It turns out that the transition takes place within the same branch. This leads to problems in the decompilation process due to the use of positive values of the stack pointer.

Figure 3. Complementary conditional branch
In addition, some basic program elements add one address to the stack, and then end on a JMP / CALL, while other basic elements add two addresses and end with the RET command. The second addition of an element is the called function, and the first is the address of the next basic program element where the transition will be made. This creates the basic elements of the program without parent objects.

Figure 4. PUSH / JMP
technique As a result of combining the two obfuscation techniques, “beautiful” graphics are obtained:

Figure 5. Obfuscating the execution sequence
Observing the garbage code is quite simple. It can be ignored when analyzing samples, if you know the scheme of application.
Dropper
Stage 1. Lure Document
In recent months, OceanLotus used several baits. One of them is the fake
Roboto Slab regularTrueType font update software . Font selection seems a bit strange, as it does not support many East Asian languages. 
Figure 6. RobototFontUpdate font update icon.
When executing, a binary file decrypts its resources (XOR, 128 bytes, hard-coded key) and recovers decrypted data (LZMA). The legitimate RobotoSlab-Regular.ttf
(SHA1:)
912895e6bb9e05af3a1e58a1da417e992a71a324file is written to a folder %temp%and launched using the Win32 API function ShellExecute.The shellcode is executed, decoded from resources. After performing a fake font update, it injects another application whose sole purpose is to remove the dropper. This "erasing" application is implemented in the form
%temp%\[0-9].tmp.exe.Stage 2. Shell Code
The same shellcode is applied at each stage.
Shell code - custom PE loader. It restores the executable file in memory - decrypts all sections and calculates the necessary movements and other indents. Shellcode uses three functions of the API the Windows:
VirtualAlloc, RtlMoveMemoryand RtlZeroMemory. The function is
RtlZeroMemoryused to reset the fields in the PE header. It is impossible to rely on automatic memory dump, because the MZ / PE headers are damaged. The shell code calls the input function in the decrypted PE, and then the export function
DLLEntry.Stage 3. Real Dropper
{103004A5-829C-418E-ACE9-A7615D30E125}.dllThis executable file decrypts resources using AES algorithm in CBC mode through Windows API. Hard-coded key has a size of 256 bits. After decryption, the compressed data is unpacked (LZMA algorithm).
If the process is run as an administrator, the malware ensures persistence by creating a service. Otherwise, use the classic registry key Run (
HKCU\SOFTWARE\Microsoft\ Windows\CurrentVersion\Run;DeviceAssociationService;rastlsc.exe). If the dropper code is executed with administrator rights, it tries to write the files listed below to the folder
C:\Program Files\Symantec\Symantec Endpoint Protection\12.1.671.4971.104a\DeviceAssociationService\, if not - it writes them to the folder %APPDATA%\Symantec\Symantec Endpoint Protection\12.1.671.4971.104a\DeviceAssociationService\: -
rastlsc.exe(SHA1:, 2616da1697f7c764ee7fb558887a6a3279861faccopy of the legitimate Symantec Network Access Control application, dot1xtra.exe) -
SyLog.bin(SHA1:, 5689448b4b6260ec9c35f129df8b8f2622c66a45encrypted backdoor) -
rastls.dll(SHA1:82e579bd49d69845133c9aa8585f8bd26736437b, malicious DLL, the fill of which performs rastlsc.exe) The path changes from sample to sample, but the scheme is similar. Depending on the rights, the malware resets files to
%ProgramFiles%or %appdata%. We also observed: -
\Symantec\CNG Key Isolation\-
\Symantec\Connected User Experiences and Telemetry\-
\Symantec\DevQuery Background Discovery Broker Tasks\These paths are used by various Symantec products.
After reaching the persistence and implementation of the executable file, the legitimate file,,
rastlsc.exeis executed with CreateProcessW. We also observed a version (
{BB7BDEC9-B59D-492E-A4AF-4C7B1C9E646B}.dll) that executes rastlsc.exewith a parameter krv. We will discuss in detail below.Backdoor component: rastlsc.exe fill
The OceanLotus team uses an old and well-known technique in one of the executable files of the Symantec product. The point is to use the process of loading a legitimate and signed .exe library file by writing a malicious library into the same folder. This will make the malicious behavior look legitimate, since these actions are performed during the operation of the trusted executable file.
As mentioned above, a legitimate file is reset and executed
rastlsc.exe. It imports the file
rastls.dll, which in this case has malicious content. 
Figure 7. Digital signature rastlsc.exe from Symantec
We also saw a fill using other legitimate and signed executable files, including
mcoemcpy.exeMcAfee, which loadsMcUtil.dll. This technique was previously used by PlugX, which attracted the attention of Vietnam CERT (in Vietnamese).Stage 1. Filling the library, rastls.dll
Internal dll file name -
{7032F494-0562-4422-9C39-14230E095C52}.dllbut we have seen other versions, for example {5248F13C-85F0-42DF-860D-1723EEAA4F90}.dll. All exported functions lead to the execution of the same function. 
Figure 8. All rasltls.dll exports lead to the execution of a single function.
Export tries to read a file
SyLog.binlocated in the same folder. Other versions tried to open the file OUTLFLTR.DAT. If the file exists, it will be decrypted using the AES algorithm in CBC mode with a hard-coded 256-bit key, and then the compressed data will be unpacked (LZMA compression). Option
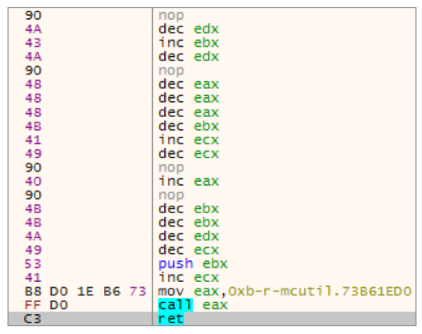
McUtil.dlluses a different technique. At first glance, the main function does not perform anything malicious, but in fact it replaces the .textlegitimate file section.mcoemcpy.exebinary file. It generates a shellcode whose task is to call a function to read the encrypted shellcode of the second stage from the file mcscentr.adf. The following pseudo-code is used to create the shellcode: Below in the picture you can see the listing of the assembler work: Figure 9. Generated shell-code
x = False i = 0
buff = genRandom()
opc1 = [0x58,0x59,0x5a,0x5b]
opc2 = [0x50,0x51,0x52,0x53,0x54,0x55,0x56,0x57]
opc3 = [0x90,0x40,0x41,0x42,0x43,0x44,0x45,0x46,0x47,0x48,
0x49,0x4a,0x4b]
while i < len(buff):
currentChar = buff[i] if currentChar < 0xc8:
buff[i] = opc1[currentChar % len(opc1)]
else:
if x:
buff[i] = opc2[currentChar % len(opc2)]
else:
buff[i] = opc3[currentChar % len(opc3)] x = x == False
i+=1
Stages 2–4. Shell Code Launcher and Shell Code Again
Shell code decrypts and loads the library
{E1E4CBED-5690-4749-819D-24FB660DF55F}.dll. The library loads resources and tries to start the DeviceAssociationService service. The decrypted information also contains the shellcode. The latter decodes the final stage: the backdoor. The option
{92BA1818-0119-4F79-874E-E3BF79C355B8}.dllchecks whether it was rastlsc.exeexecuted with krvas the first parameter. If yes, the task is created and rastlsc.exeexecuted again, but without this parameter.Stage 5. Backdoor
{A96B020F-0000-466F-A96D-A91BBF8EAC96}.dllFirst, the malware tries to download its resources and decrypt them using the RC4 algorithm. The resulting resources contain the data used to configure the backdoor. The configuration format is easy to learn. Using the Kaitai struct and its structure dumper, we get the following:

Figure 10. Configuration structure
Note : with the exception of the domain_encoding_str string and the httpprov library, the data changes from sample to sample. The registry keys are almost the same, but they have a similar scheme:
\HKCU\SOFTWARE\Classes\AppX[a-f0-9]{32}nothing remarkable. The malicious program gets the first 10 bytes of the username (UTF-16), ckorit them with a three-letter string
mutex_encoding_strin UTF-16 and encodes in hexadecimal. The result is used as the name of the mutex. For example, for a user whose name starts with abcand a key in the form vwx, the mutex will be \Sessions\1\BaseNamedObjects\170015001b. The backdoor includes a PE loader that loads the library
HTTPProv.dllinto memory, calls an entry point, and then calls the export function CreateInstance.Communication
The backdoor uses the standard TCP communication port
25123. To obtain the IP address of the server, the backdoor first creates a specific DNS query. The malware selects one of the three domains from the configuration and adds a special subdomain, which is generated using two values. The first value is the computer name within the length of 16 bytes. The second is a four-byte version ID. The code in Python 2 below is a coding algorithm: For example, if the computer name and version ID is 0x0a841523, the following domain is generated: You can use the following regular expression for the C & C server label of this backdoor: If the IP address belongs to a specific domain, Malware tries to set TCP connection via port
letters=domain_encoding_str # “ghijklmnop” hex_pc_name=pc_name.encode(“UTF-16LE”).encode(“hex”) s=’’
for c in hex_pc_name:
if 0x2f < ord(c) < 0x3a:
s+=letters[ord(c) - 0x30]
else:
s+=crandom-pcniggmhggmeggmkggmfggmdggidggngggmjgg.ijhlokga.dwarduong[.]com[ghijklmnopabcdef]{4-60}\.[ghijklmnopabcdef]{8}\.[a-z]+\.[a-z]+25123. Each sample has three different domain names that are used to search for a C & C server. The communication process is RC4 encrypted and compressed using LZMA. It is possible to decrypt traffic, as the key is added to the beginning of the packets. The format is as follows:
[ключ RC4 (4 байтов)][зашифрованная информация]Each key byte is generated by a function
rand. After decrypting and unpacking a packet, the data has the following format: [dw:неизвестно][dw:неизвестно][dw:номер команды][dw:размер данных][dw:неизвестно] [dw:данные]The first time a client connects to the server, a UUID is sent, which is used as a session identifier. The latter is stored in the registry key as binary data:
HKCU\SOFTWARE\Classes\ AppXc52346ec40fb4061ad96be0e6cb7d16a\DefaultIconAs we said earlier, the backdoor also contains a library called
HTTPprov. It is used as an alternative way to communicate with the server. The DLL file sends a POST request via HTTP. It also supports HTTPS and proxy usage of SOCKS5, SOCKS4a and SOCKS4. Library is statically linked to libcurl. After initialization, the registry entry will be created - a team backdoor for later use HTTP to communicate with the server command:
HKCU\SOFTWARE\Classes\ CLSID{E3517E26-8E93-458D-A6DF-8030BC80528B}. It uses a standard client application:
Mozilla/4.0 (с поддержкой; MSIE 8.0; Windows NT 6.0; Trident/4.0). The main characteristic of this library is a special algorithm for encrypting the universal resource identifier. The resource part of the URI is created using the following pseudo-code: Note : for clarity, the part responsible for checking the string length has been removed from the code.
buffEnd = ((DWORD)genRand(4) % 20) + 10 + buff; while (buff < buffEnd){
b=genRand(16);
if (b[0] - 0x50 > 0x50)
t=0;
else
*buf++= UPPER(vowels[b[1] % 5]);
v=consonants[b[1]%21]); if (!t)
v=UPPER(v);
*buff++= v;
if (v!=’h’ && b[2] - 0x50 < 0x50)
*buff++= ‘h’;
*buff++= vowels[b[4] % 5];
if (b[5] < 0x60)
*buff++= vowels[b[6] % 5];
*buff++= consonants[b[7] % 21];
if (b[8] < 0x50)
*buff++= vowels[b[9] % 5];
*buff++= ‘-’;
};
*buff=’\0’;To obtain an identifier from the generated string, two numbers are added using a special sum-checking algorithm: Adding the library URI generator, we get the following URL:
checksum=crc32(buff)
num2=(checksum >> 16) + (checksum & 0xffff) * 2
num1=(num2 ^ 1) & 0xf
URL=GENERATED_DOMAIN+ “/” + num1 + “/” + num2 + “-” + buffHTTPprovhXXp://niggmhggmeggmkggmfggmdggidggngggmjgg.ijhlokga.aisicoin[.]com/ 13/139756-Ses-Ufali-LTeams
After obtaining the SESSIONID session ID, the backdoor makes a digital fingerprint of the system. The package is built as follows (indent in the package - description):
0x000 - byte: the value changes in each version
0x001 - 0x01: hard-coded byte
0x002 - bool: elevated privileges
0x003 - dword: ID version
0x007 - string (UTF-16), computer name (. max 0x20)
0x027 - line (UTF-16), user name
0x079 - query result in the register in the
HKLM\SOFTWARE\Microsoft\Windows NT\ CurrentVersionvalues ProductName, CSDVersion, CurrentVersion, ReleaseId, CurrentBuildNumberand the result of the call IsWow64Process (x86|x64)0x179 -% s subsequent line format (% s); is replaced by (
GetVolumeInformationW:VolumeNameBuffer)VolumePathNames0x279 - physical disk control "input-output" device PhysicalDrive deviceIOControl 0x2D1400 (IOCTL_STORAGE_QUERY_ PROPERTY) (VolSerialNumber)
0x379 - wmi
SELECT SerialNumber FROM Win32_BaseBoard0x3f9 - Preparation of the current date and time GetSystemTimeAsFileTime
0x400 - bool: unknown
0x401 - dword: obtained after decryption resource
is an example of the digital fingerprint Systems:

Figure 11. Digital Fingerprint of the System
This is a full-fledged backdoor, which provides its operators with a number of possibilities: manipulations with the file, registry and processes, loading of additional components, obtaining a digital fingerprint of the system. Below are the numbers and descriptions of supported commands:
0 - digital fingerprint
1 - sets the session ID
2 - creates the process and gets the result (using software channels)
3 - sets the connection attempt count
4 - defers the polling time
5 - reads a file or registry key and counts MD5
6 - creates process
7 - creates a file, entry in the registry or stream in memory
8 - writes to registry
9 - polls registry
10 - searches files in system
11 - transfers files to another directory
12 - deletes files from disk
13 - retrieves a list of disks marked in the system using function
GetLogicalDriveStringW14 - creates directory
15 - removes directo riu
16 - reads file from offset
17 - calls the PE loader (transition to communication by
HTTPprov) 18 - [unknown]
19 - 0: polling the value in the registry; 1: implementation and execution of the program
20 - sets the environment variable
21 - runs the shellcode in the new thread
22 - returns the environment variable
+23 in the new version - restarts itself if the environment variable APPL does not exist
Conclusion
OceanLotus remains highly active and continues to update the toolkit.
The group seeks to hide its activities; to do this, attackers carefully select victims, limit the spread of malicious programs, use several servers in order not to draw attention to a single domain or IP address. Deciphering the injected component and the fill technique (side-loading), despite being widely known, avoids detection, since the work of intruders in this case is disguised as a legitimate application.
Compromise Indicators (IoCs)
Samples
Table 1: dropper

Table 2: Libraries

Network
IP addresses
46.183.220.81
46.183.220.82
46.183.222.82
46.183.222.83
46.183.222.84
46.183.223.106
46.183.223.107
74.121.190.130
74.121.190.150
79.143.87.230