Using OpenVAS Vulnerability Scanner
Vulnerability scanners are software or hardware tools used to diagnose and monitor network computers, allowing you to scan networks, computers, and applications for possible security problems, evaluate and fix vulnerabilities. (Wikipedia).
Well-known commercial scanners are Nessus, GFI LANguard, XSpider.
Unlike others, OpenVAS is free, works without any restrictions and can be useful both to network administrators and IS specialists to identify current problems of its infrastructure.
OpenVAS is based on a constantly updated collection of NVT security tests (of which there are already more than 30,000), as well as a connection to the CVE database, which describes known vulnerabilities. Execution of NVT tests reveals the vulnerability, and CVE provides a description of the problem and ways to solve it.
Let's get started.
1. The choice of iron.
Everything is simple here, if you have to scan often large ranges of addresses, then the more powerful the iron, the better. You can increase the number of parallel flows for processing network addresses, and the scanning itself for each host will be faster.
2. Installation.
Here I choose the least problematic way for me to install from packages.
We go to the address.
www.openvas.org/install-packages.html
We select the necessary distribution kit and install.
In my case, it is CentOS and atomicorp repository. The script itself will download all the dependencies, conduct an initial update of the vulnerability database and prescribe the necessary settings. In the process, you will be asked to come up with a username and password for access to Openvas.
3. Use.
We go to the localhost address : 9392 enter the username and password and we are in the Greenbone Security Assistant management console.
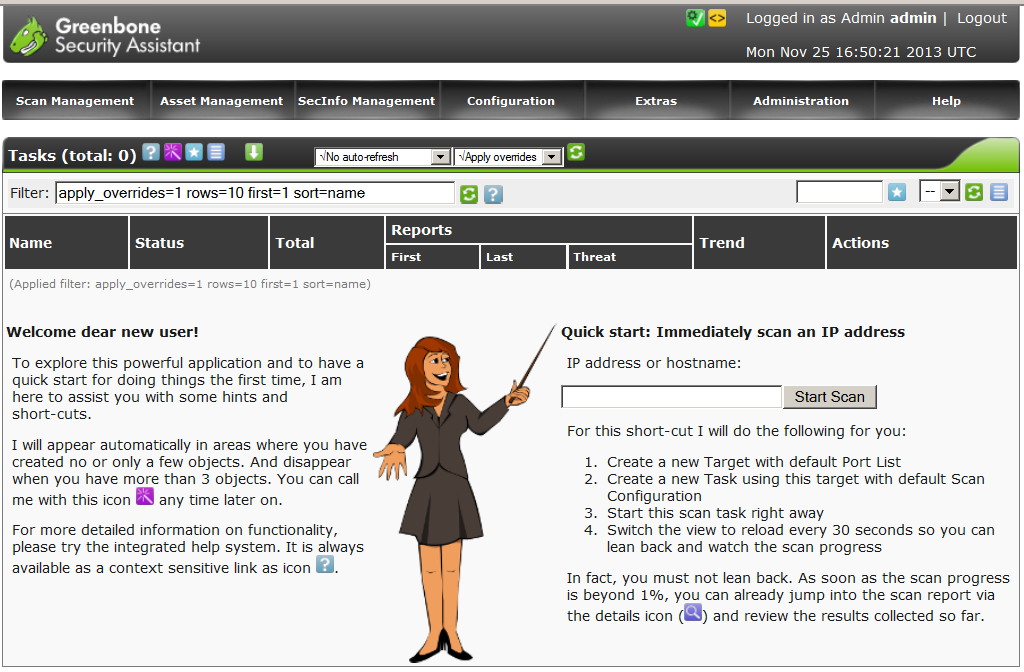
The following is an example of working with Openvas to scan the range of the internal network. The main settings are sharpened for the optimal scan speed of each host.
3.1 Select a scan configuration.
We go to the Configuration - Scan Configs section.
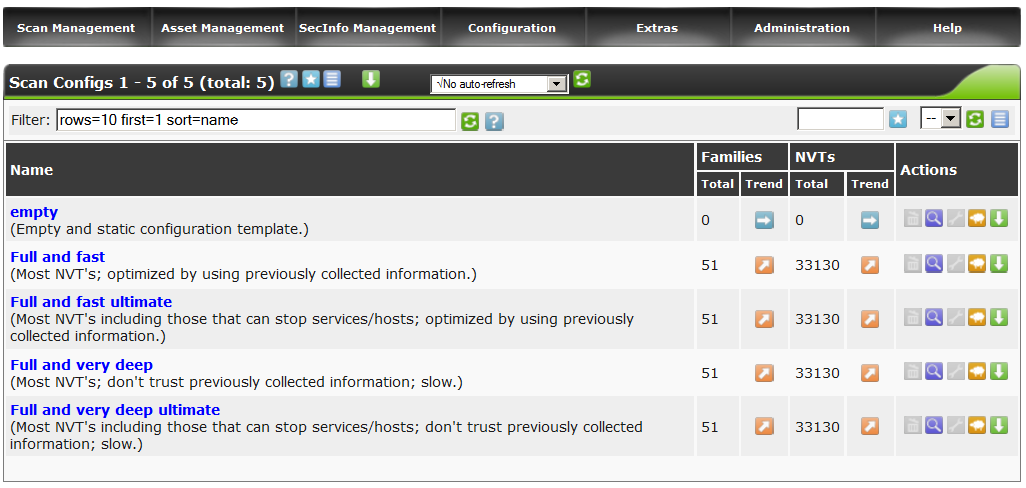
We see 4 standard policies and 1 empty.
Politicians are divided into 2 groups - fast and deep.
The fundamental difference is that deep does not take into account the work of each previous verification script and the collection of information starts anew.
According to my tests, this significantly increased the scan time of each host, in the absence of a significant result. Therefore, for greater speed, select the Full and fast ultimate policy and clone it by clicking on the sheep’s icon .
.
Now, for the clone, we have the editing options available and by clicking on the wrench icon , take a look inside.
, take a look inside.
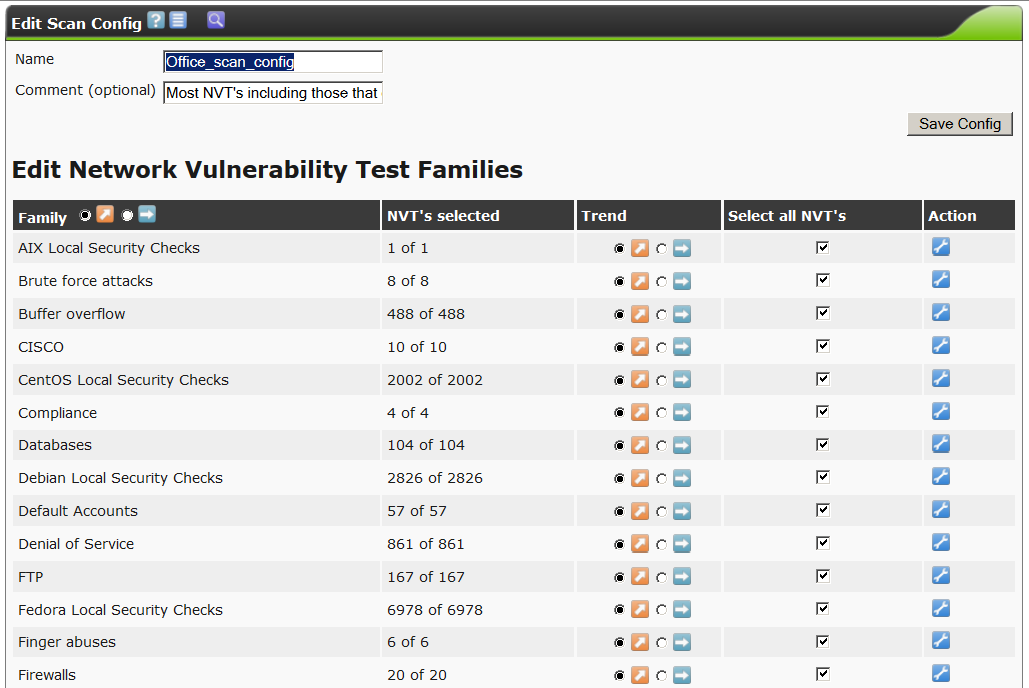
There are a great many options, several hundred on the screen, only the very beginning. All options are grouped by subsections of NVT tests for various types of operating systems and network equipment, according to the settings of various plug-in utilities such as nmap, nikto, etc.
Call our new policy Office_scan_config.
Go down below.
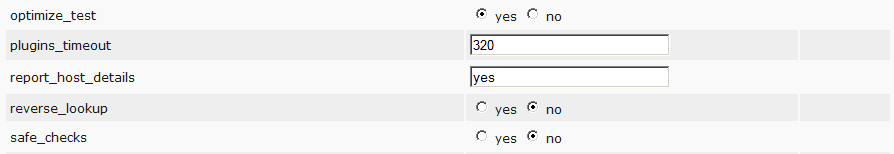
I draw attention to the following points.
safe_check – disconnection will allow the launch of potentially dangerous NVT tests, the execution of which can cause the test host to crash. Use carefully.
optimize_test– the switch which sets to use fast or deep scanning.
Next, we go down to the PingHost points and set the switches, as in the screenshot.
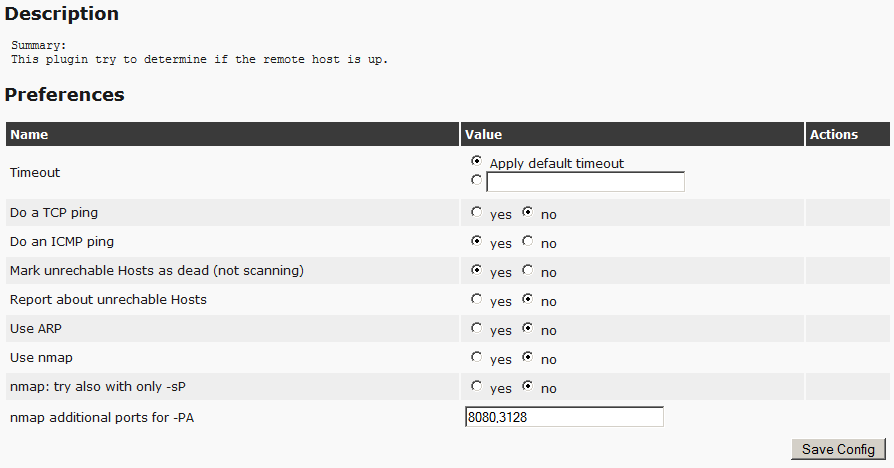
This will immediately eliminate empty addresses and not waste scanner time on them. The remaining items do not touch.
Do not forget to save the accepted changes.
3.2 We register an account for conducting local checks.
If this item is configured, Openvas will go to each machine, scan the installed software, local security settings and throw alerts, in case of problems.
Naturally, this will increase the scan time.
If not configured, Openvas will be limited to remote checks.
We go to the Configuration –Credentials section.
Create a new entry by clicking on the star icon .
.
Let's say we have a windows network in the domain, there is a user sec_check, with local administrator rights on the necessary machines, then it will look like this.
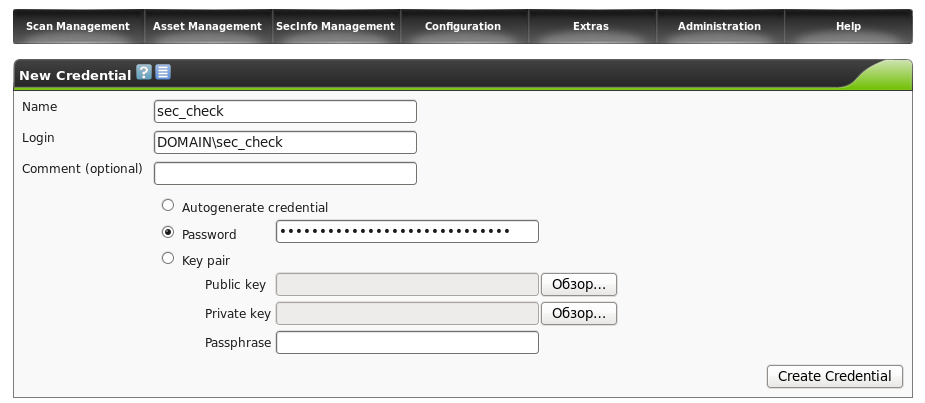
Save and move on.
3.3 Set scan goals.
Next, we need to score the range of addresses for scanning and determine the set of ports that Openvas will check.
We go to the Configuration –Target section. Create a new goal by clicking on the star icon. Give her the name office.

Here, in principle, everything is clear, in the SMB section, we connected a previously created user to conduct local checks.
In the PortList section, the desired range of ports is connected, in this case the set of popular ports offered by Nmap. The choice in favor of this range, is again made in favor of optimization, so as not to shovel all 65 thousand.
In the Hosts section, specify the ip range.
3.4 Launch!
We go to the ScanManagement - Task section. Create a new task by clicking on the star icon.
We sequentially select previously created configurations and click on the CreateTask button.
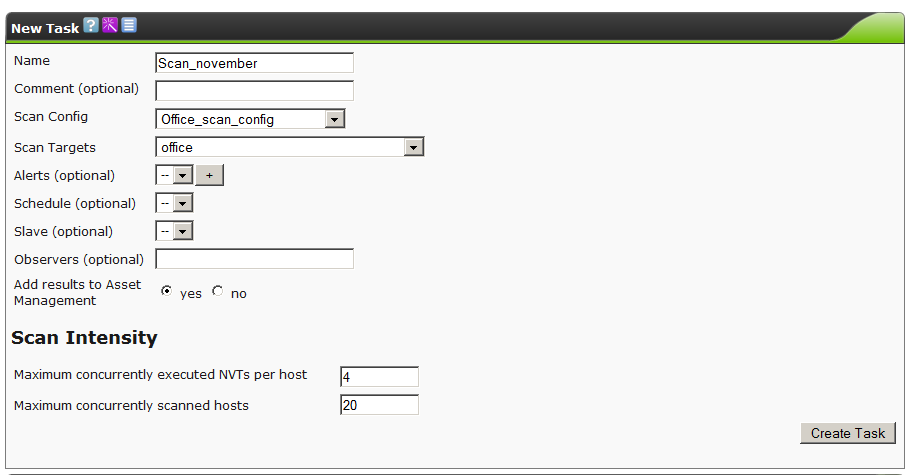
We are starting.
We’re going to drink tea. Depending on the network saturation and server capacity, the process can take up to several hours.
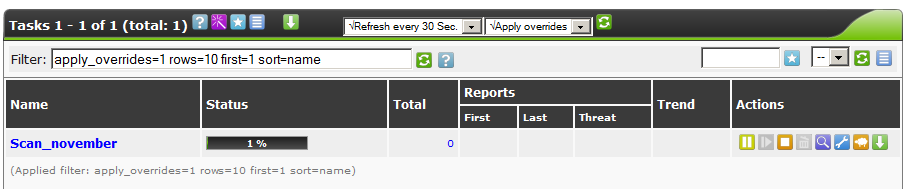
At the end of the process, we can click on the magnifying glass icon and view all the problems found.
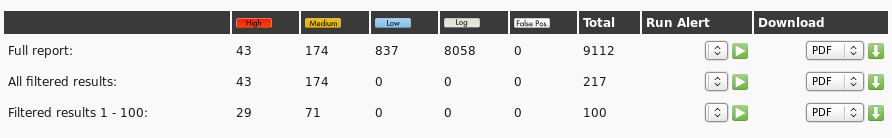
Typical alert.

4. Updates.
From time to time it is necessary to pump up current information about vulnerabilities and tests revealing them.
This is done either from a browser in the Administration section. (alternately in all 3 sections: nvt, scap, cert)
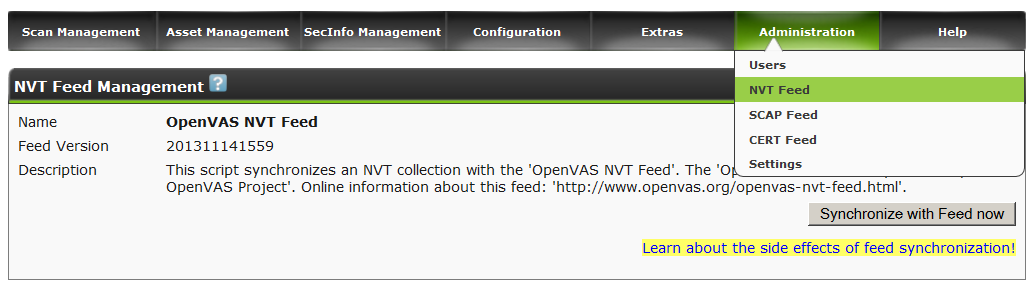
Either from the command line, in sequential commands.
openvas-nvt-sync
openvassd
openvasmd --rebuild
openvas-scapdata-sync
openvas-certdata-sync
killall openvassd
/etc/init.d/openvas-scanner restart
/etc/init.d/openvas-manager restart
/etc/init.d/openvas-administrator restart
/etc/init.d/greenbone-security-assistant restart
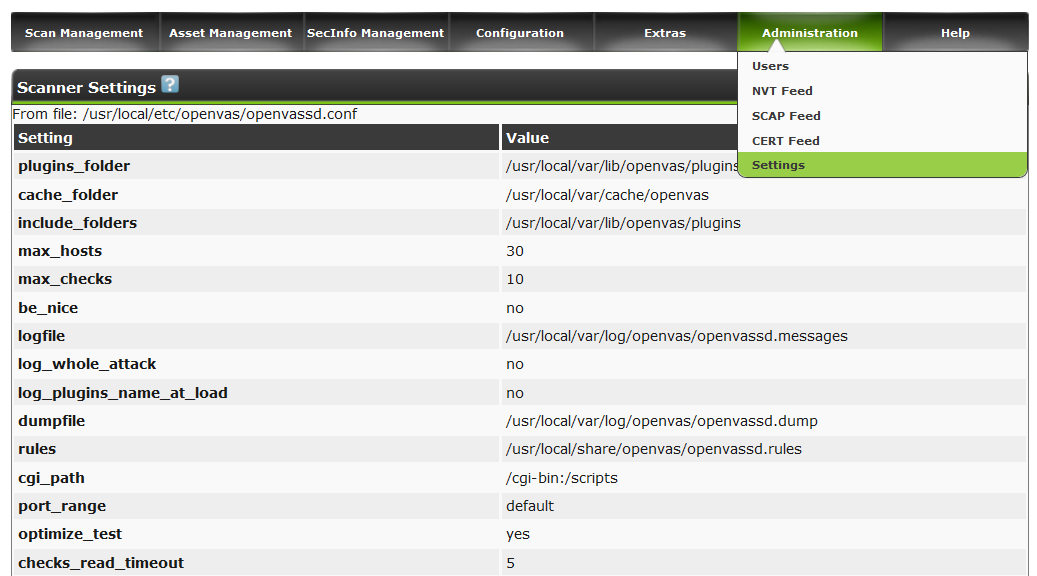
Owners of a powerful hardware, can look into the Settings section and set a larger number of parallel threads.
Useful tricks in the Greenbone Security Assistant. can be found here
www.greenbone.net/learningcenter/index.html
Success in use.
Well-known commercial scanners are Nessus, GFI LANguard, XSpider.
Unlike others, OpenVAS is free, works without any restrictions and can be useful both to network administrators and IS specialists to identify current problems of its infrastructure.

OpenVAS is based on a constantly updated collection of NVT security tests (of which there are already more than 30,000), as well as a connection to the CVE database, which describes known vulnerabilities. Execution of NVT tests reveals the vulnerability, and CVE provides a description of the problem and ways to solve it.
Let's get started.
1. The choice of iron.
Everything is simple here, if you have to scan often large ranges of addresses, then the more powerful the iron, the better. You can increase the number of parallel flows for processing network addresses, and the scanning itself for each host will be faster.
2. Installation.
Here I choose the least problematic way for me to install from packages.
We go to the address.
www.openvas.org/install-packages.html
We select the necessary distribution kit and install.
In my case, it is CentOS and atomicorp repository. The script itself will download all the dependencies, conduct an initial update of the vulnerability database and prescribe the necessary settings. In the process, you will be asked to come up with a username and password for access to Openvas.
3. Use.
We go to the localhost address : 9392 enter the username and password and we are in the Greenbone Security Assistant management console.

The following is an example of working with Openvas to scan the range of the internal network. The main settings are sharpened for the optimal scan speed of each host.
3.1 Select a scan configuration.
We go to the Configuration - Scan Configs section.

We see 4 standard policies and 1 empty.
Politicians are divided into 2 groups - fast and deep.
The fundamental difference is that deep does not take into account the work of each previous verification script and the collection of information starts anew.
According to my tests, this significantly increased the scan time of each host, in the absence of a significant result. Therefore, for greater speed, select the Full and fast ultimate policy and clone it by clicking on the sheep’s icon
 .
. Now, for the clone, we have the editing options available and by clicking on the wrench icon
 , take a look inside.
, take a look inside. 
There are a great many options, several hundred on the screen, only the very beginning. All options are grouped by subsections of NVT tests for various types of operating systems and network equipment, according to the settings of various plug-in utilities such as nmap, nikto, etc.
Call our new policy Office_scan_config.
Go down below.

I draw attention to the following points.
safe_check – disconnection will allow the launch of potentially dangerous NVT tests, the execution of which can cause the test host to crash. Use carefully.
optimize_test– the switch which sets to use fast or deep scanning.
Next, we go down to the PingHost points and set the switches, as in the screenshot.

This will immediately eliminate empty addresses and not waste scanner time on them. The remaining items do not touch.
Do not forget to save the accepted changes.
3.2 We register an account for conducting local checks.
If this item is configured, Openvas will go to each machine, scan the installed software, local security settings and throw alerts, in case of problems.
Naturally, this will increase the scan time.
If not configured, Openvas will be limited to remote checks.
We go to the Configuration –Credentials section.
Create a new entry by clicking on the star icon
 .
. Let's say we have a windows network in the domain, there is a user sec_check, with local administrator rights on the necessary machines, then it will look like this.

Save and move on.
3.3 Set scan goals.
Next, we need to score the range of addresses for scanning and determine the set of ports that Openvas will check.
We go to the Configuration –Target section. Create a new goal by clicking on the star icon. Give her the name office.

Here, in principle, everything is clear, in the SMB section, we connected a previously created user to conduct local checks.
In the PortList section, the desired range of ports is connected, in this case the set of popular ports offered by Nmap. The choice in favor of this range, is again made in favor of optimization, so as not to shovel all 65 thousand.
In the Hosts section, specify the ip range.
3.4 Launch!
We go to the ScanManagement - Task section. Create a new task by clicking on the star icon.
We sequentially select previously created configurations and click on the CreateTask button.

We are starting.
We’re going to drink tea. Depending on the network saturation and server capacity, the process can take up to several hours.

At the end of the process, we can click on the magnifying glass icon and view all the problems found.

Typical alert.

4. Updates.
From time to time it is necessary to pump up current information about vulnerabilities and tests revealing them.
This is done either from a browser in the Administration section. (alternately in all 3 sections: nvt, scap, cert)

Either from the command line, in sequential commands.
openvas-nvt-sync
openvassd
openvasmd --rebuild
openvas-scapdata-sync
openvas-certdata-sync
killall openvassd
/etc/init.d/openvas-scanner restart
/etc/init.d/openvas-manager restart
/etc/init.d/openvas-administrator restart
/etc/init.d/greenbone-security-assistant restart
Owners of a powerful hardware, can look into the Settings section and set a larger number of parallel threads.

Useful tricks in the Greenbone Security Assistant. can be found here
www.greenbone.net/learningcenter/index.html
Success in use.
