Unusual Duet - Passwords and Mnemonic Images
What does the system ask of you when you turn on your computer or unlock the phone, or insert a card into an ATM, or enter a page on a social network? The system requires your password. This stage of data protection, for which we ourselves are responsible for the most part, is very common in our time. And the harder the password, the harder it is to pick it up, and therefore the harder it is for an attacker to get your data. However, not all users approach the creation of passwords with all the necessary seriousness. Today we will talk about the study of passwords-passwords. Why phrases passwords for us are not constant, what options of such systems were in the past, and how scientists suggest to popularize a similar variant of protection? This and much more we will find out today. Go.
Background
Anecdotal “date of birth”, “wedding day”, “name of your favorite book character”, etc. for a very long time were the most common passwords, but certainly not the most difficult.
A small lyrical digression. I recently revised the film "Keepers" (2009). Toward the end of the film, the main characters sneak into the villain's office to get information. But access to the computer is password protected. What to do? Turn around and leave? No, it's just a password, which can be easier.
Remark: this office is located in the building of the Pyramid Corporation, and on the table of the villain next to such an important PC are books about Egypt, local gods and pharaohs.

The very moment from the movie "Keepers" (2009)
So, the hero begins to pick up a password using scientific method, but to no avail. Then he looks at the very books and sees Ramesses II. Of course, this was the password. Heroes receive information, and the plot moves on. And now the question - really the main antagonist of the picture, Adrian Weidt, who is considered the most intelligent on the planet, could not come up with a more complicated password and not leave it right on his desktop? All this is cinema conventions, but this does not diminish my bewilderment.
Regrettably, but the fact is that many people have passwords of this very level of complexity. Although there are login systems that “force” the user to create a password that meets certain requirements: at least 8 characters, at least 1 capital letter, at least 1 digit, and so on. However, you see, watson and Watson99 are not that different. There are those users who take their data much more seriously, and therefore their passwords can be at first glance a messy set of characters. I had a colleague whose password consisted of 15-20 characters, and he typed it as if he wanted to play the song “In the Cave of the Mountain King” on the keyboard.
From the lyrics and funny examples get down to business.
There is a password “spwaop”, which is harder to remember than the date of your birth, but not so much. Such passwords protect the data much better, since they complicate the hacking process by the method of selection, when the hacker tries all possible options. For a simplified example, let's take three numbers - 123. Suppose a password consists of these numbers, but in what order? Options: 123, 132, 213, 231, 312, 321. A total of 6 options, therefore, it will not be difficult to choose the right one. If you add one digit - 1 2 3 4, then there will already be 24 options, which complicates the selection process.
However, there is a problem - the human factor. The researchers found that the spread of complex passwords is hampered by the users themselves. Many people think that such passwords are too difficult to remember. If your data is important to you, please remember some 6-8 characters - say you and you will be right. However, against the opinions of the masses no arguing. Therefore, the scientists decided to develop a methodology that became the basis of the entry system that allows a person to create complex passwords and, most importantly, helps to remember this password.
I myself am skeptical of this kind of research. They can be considered a waste of time and resources, but any research, any experiment or experience has the right to exist. Moreover, rejecting their ambiguous attitude to the problem of “laziness to remember the password”, it is still curious how the system itself, developed by researchers, works.
Prior to this development, there were many predecessors whose phrase-password systems were implemented to varying degrees, but did not find popularity among users due to complexity, low security, weird password-creation process, etc.
For example, there was a system Diceware (1995). In the system dictionary there were 7,776 words that formed the phrase-password and not all were English. The principle of selection was based on the use of dice by the user. Here is an example from the official Diceware site :
Suppose you want a 6-word passphrase, which we recommend for most users. You will need to roll the dice 6x5, i.e. 30 times. Let's say the following numbers fell out:What problems are associated with this method of generating passwords? It is quite obvious that few will be willing to throw the bones, write down, then search and match the numbers with the words in order to simply create a password for yourself. The second problem was the words themselves. From the example above, you can understand that this is not a phrase, but simply a random set of words. As a result, you can remember this, but not without effort. Even after a few years after the appearance of the Diceware system, a survey showed that users rated it at 1.71 points out of a possible 5.
1, 6, 6, 5, 1, 5, 6, 5, 3, 5, 6, 3, 2, 2, 3, 5, 6, 1, 6, 6, 5, 2 , 2, 4, 6, 4, 3, 2, 6.
Now write down all the numbers in groups of 5 shots:
1 6 6 6 5
1 5 6 5 3
5 6 3 2 2
3 5 6 1 6
6 5 2 2 4
6 4 3 2 6
Compare the 6 numbers obtained with those corresponding to the word in the list, and you will receive:
1 6 6 6 5 cleft
1 5 6 5 3 cam
5 6 3 2 2 synod
3 5 6 1 6 lacy
6 5 2 2 4 yr
6 4 3 2 6 wok
Your passphrase: cleft cam synod lacy yr wok
Another study showed that passphrase passwords are easier to remember without reducing the number of words in them, but by reducing the words themselves. As they say, if you need an analogue of the symbol “C”, then why do you need the word “counterclockwise” for this, if the simple “cat” is also suitable. This means that a password of 3 long words and a password of 6 short words will be of the same degree of difficulty, but the latter is easier to remember.
Despite all the shortcomings, Diceware still gained popularity in certain circles and is used to this day.
The main task of modern researchers is to create a system that will combine all the advantages of predecessors, but try to avoid their problems and shortcomings.
System Basics
To create a new system, it was decided to combine certain features of the predecessors:
- specialized dictionary and phrase template;
- creating user mnemonic * pictures;
- masking of the entered data.
Mnemonics * - various methods and techniques to increase the degree of memorization of a particular information.For a start, the VOA Special English Word List dictionary , which was created in 1959, was used. He was aimed at people for whom English is not their first language.
Simplicity of words does not guarantee that the user will like these words. However, giving the opportunity to infinitely generate phrases means lowering the degree of security. Therefore, the program simply gives the user 4 random phrases from which he can choose one that he likes.
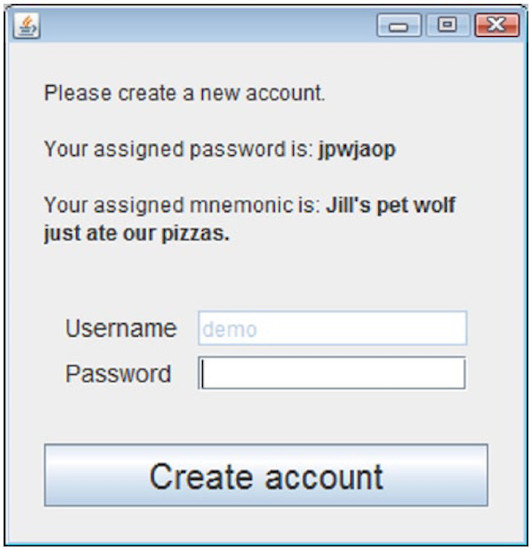
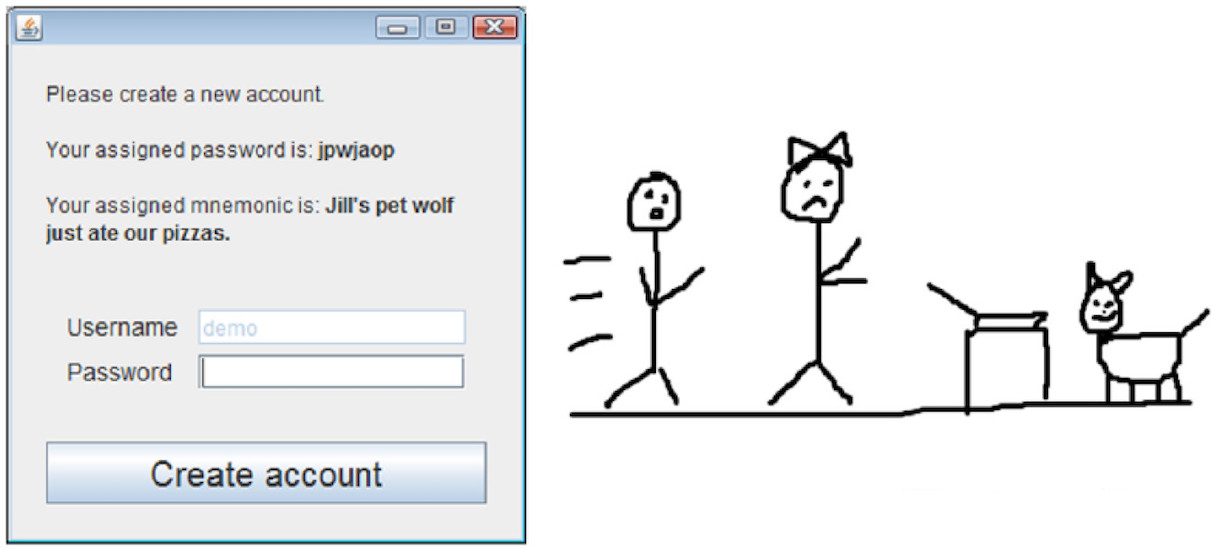
Image number 1: the program gives the user a phrase, the first letters of each word correspond to the characters in the user's password.
Another small, but useful introduction was the explanatory dictionary. In order to be sure that the user fully understands the meaning of the word in the password phrase, when you hover over it, an interpretation is given.
The most unusual, but very effective from the point of view of mnemonics, was the introduction of a simple graphical editor. The user, based on the password phrase he received, could create a drawing that should help him remember the password. Very non-standard, I agree. However, any visualization process, especially if the visualized equivalent of the phrase is created by the user, will allow you to better remember the password.

Image number 2: a graphical representation of the password phrase. Agree, if you show only a picture, then you can hardly recreate the password itself. This is only possible for someone who knows the password.
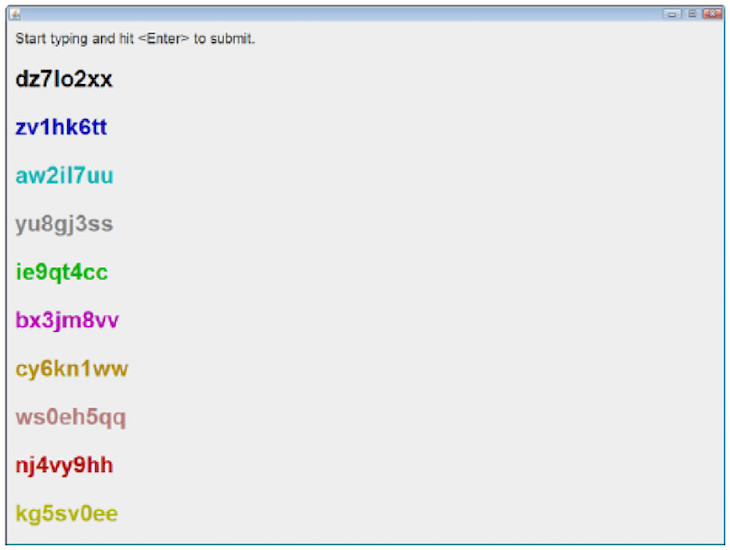
Image number 3: password masking.
Password masking is primarily needed as protection against casual witnesses who may have seen how you create a password. The most common way is “ * ” ( asterisks ), which appear in the password entry field instead of the characters themselves. In this study, another concealment option was introduced into the system, which operates according to the principle of “hide in a visible place.” As you can see from image number 3 there is a list of passwords, only one of them is correct, and the rest are fake. Such a method, as statistics have shown, is no worse than standard masking with asterisks (****).
At the same time there is a small feature. Fake passwords are composed of a list of words that are not used in this password. When an attacker tries to enter a password at random, the system detects an attempt to enter a "fake" and blocks, sending logs and a warning about an attempted hacking to a full user. The question arises - what if the user just made a mistake? The fact is that a password entry error and an attempt to enter a fake password are extremely unlikely to coincide. Unfortunately, there are no more accurate and reasoned explanations from researchers. Perhaps the system is not blocked when entering the initial characters of the fake password, but only when entering the entire password. But this is just my guess.
The researchers also added error correction to the system. Since the dictionary is not particularly large, such corrections are made accurately and do not lead to inaccuracies when entering the passphrase. At the same time, the error correction script works with a real password and with fake, which allows you to maintain the security level of the system.
System Requirements The
degree of complexity of the system was set as 40 bits of entropy. To increase the degree of security, it is enough to apply the key expansion technique when the original weak password is run through an algorithm that makes the password size too large for brute force (full brute force search).
Informational entropy * - a measure of uncertainty or unpredictability of systems.The system of passwords has 4 options. Below are screenshots and a description of each of them.
Option I:
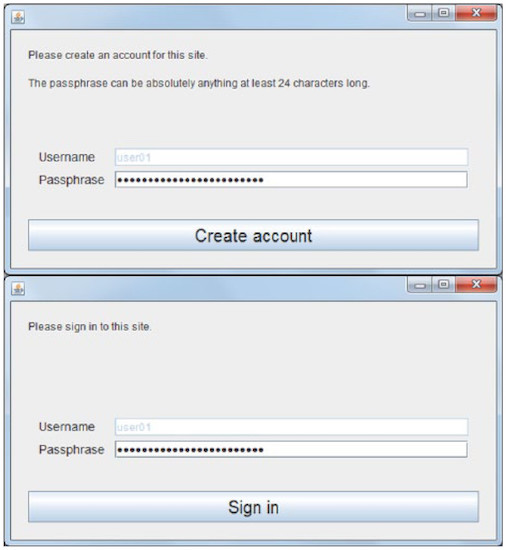
The phrase generated by the user should consist of at least 24 characters (including spaces). No other requirements. Mnemonic is not used, and password masking is standard (******).
24 characters = 1 character x 4 bits + 7 characters x 2 bits + 12 characters x 1.5 bits + 4 characters x 1 bit = 40.0 bits of entropy.
Option II:
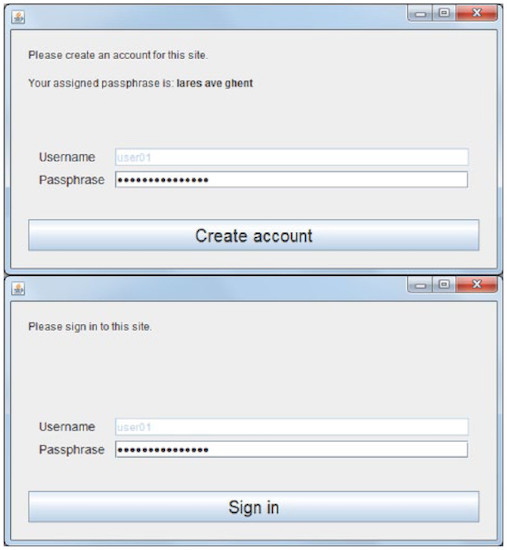
The phrase is generated by the system and consists of 3 words randomly selected from several lists (Diceware8k, Beale's alternate list and 1Password expanded English Diceware list). The total number of words is 10326. Mnemonic is not used, and password masking is standard (******).
3 words x log 210326 word variations = 40.0 bits of entropy.
Option III:
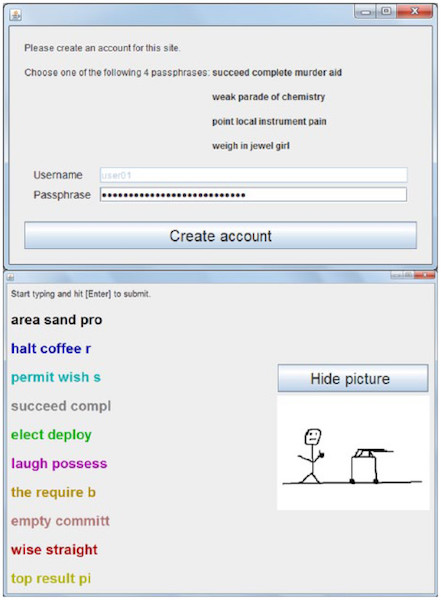
The phrase is selected from four options proposed by the system, each of which consists of 4 words. As a base of words used Special English list, 1450 words. Applied the interpretation of words. It is possible to create mnemonic images in the editor, which are shown at the time of entry. Included error correction. A password masking is carried out using the fake method.
4 words x log 2 1450 variants of words - log 2 4 variants of phrases = 40.0 bits of entropy.
Option IV:
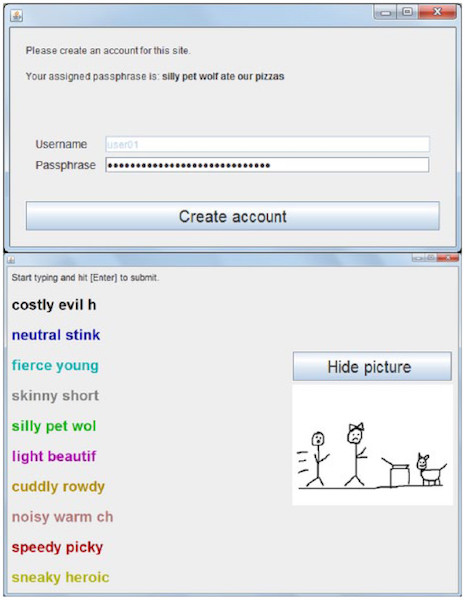
The phrase is generated by the system and consists of 6 words. It is possible to create mnemonic images in the editor, which are shown at the time of entry. Included error correction. A password masking is carried out using the fake method.
log 2 (151 x 151 x 155 x 61 x 78 x 66) possible combinations = 40.0 bits of entropy.
So the system is theoretically ready. Now you need to check it in practice.
Practical tests
For the test, the researchers collected a group of people - 52 people (28 men and 24 women), whose age varied from 20 to 61.
4 variants of the system were distributed among the participants by means of a Latin square * .
Latin square * is a table filled with elements of a set so that in each row and column elements do not repeat.After a brief familiarization with the purpose of the study, each of the participants had to create a phrase-password and a mnemonic image within 5 minutes. After that, the participant filled out the NASA-TLX and SUS profiles .
<b> NASA-TLX </ b> - NASA Task Load Index. (Example questionnaire)

<b> SUS </ b> - System usability scale. (Example questionnaire)

The next step was to use the generated passphrases. Participants had to log in to 4 accounts (4 login options) they had previously created. The number of attempts was limited to five. After each entry, participants again filled out NASA-TLX and SUS profiles. They also had to assess the degree of security and the overall quality of one or another variant of the entry system.
A week later, participants who were forbidden to record passwords returned to re-pass the stage with the entrance to the accounts.
Participants also entered the role of spying. They were allowed to spy one after another in the process of creating a mnemonic picture for a passphrase. After which they should have tried to guess the phrase itself.
Test results and debriefing
Analysis of the test results showed that the last two options for the entry system were the most effective. 82% of the subjects successfully coped with the stage of re-entering Special English based accounts. For comparison: only 50% went through the same stage successfully when the system was used, where the user himself created passphrase phrases. For Diceware10k, the indicator is even worse - only 34%. Such a significant leap in the effectiveness of new systems is associated with the use of a typo correction and masking with a fake method.
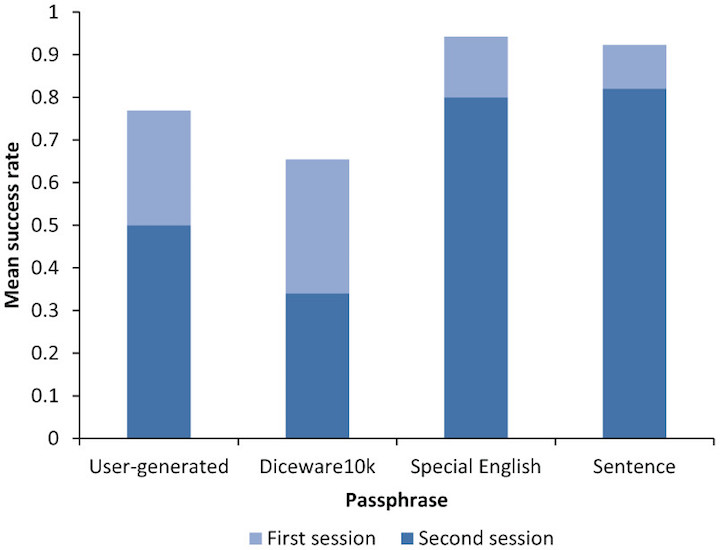
The graph above shows how the performance indicators of a particular system changed: light blue — the first login to the system after creating an account, dark blue — the second entry into the account. As we can see, it is Special English and passphrase passwords as complete sentences that showed the best result.
However, an indicator of 82% is not the ultimate dream for our time, given that we are talking about systems designed to protect data. The researchers claim that they intentionally overestimated the degree of difficulty in performing the tasks for the subjects, whereas in reality everything would have been easier. First, the subjects needed to create 4 passphrases in a row and memorize them, with or without mnemonic help. It was impossible and unnecessary to write down the passwords created, because the subjects received a reward (a $ 20 gift card) not for the best result, but for the participation itself. I agree that such measures are not so clear and cannot guarantee that one of the participants in the test will not memorize their passwords just to show the best result. It was certainly possible to lock all participants in glass rooms without access to the outside world, and then, a week later, check how well the system helps them remember their passwords. But, naturally, it would not be very humane, even for the sake of the purity of the experiment.
In any case, scientists are going to conduct future tests, taking into account the above-described error factors, in order to confirm that their “laboratory” results will only increase in real conditions. So they are confident in their offspring.
Regarding "espionage", the results of all variants of the systems did not differ much. As expected, hiding a password with asterisks and using fake phrases was equally effective measure of protection from “prying eyes”.
Measurements of the degree of protection from machine hacking have shown that the system copes with this task worst of all with user passwords and phrases. On average, 224 selection attempts were spent on breaking the passphrase, which is about 1,000 attempts less than other system options. And the entropy index, like password complexity, was 10 bits less than other options.
An analysis of security against hackers (people, not programs) showed an unexpected result. In this case, the version of user passwords and Diceware10k that was lagging behind in the previous indicators turned out to be the most protected. Here the negative component of the mnemonic assistant emerges. Pictures created by users to improve password memorization, helped the hackers to pick up the desired password and, as a result, to make unauthorized access to the account. However, the coefficient of vulnerability was not so great (from .4 to .6). In other words, if an attacker looks at the process of creating a password that is protected by asterisks, it will be much easier for him to hack an account than if he is repelled only by a mnemonic image.
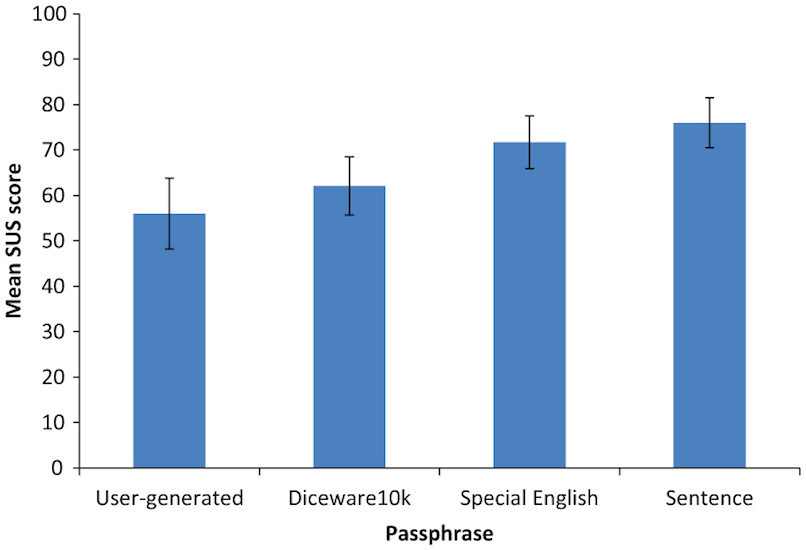
This graph shows how the subjects rated 4 options for the entry system. The best was the option with logical sentences. The worst was the option when the subjects themselves created their own phrases. This is quite remarkable, because it was possible to assume that the creation of a phrase to your taste should increase the degree of memorization, so to speak. However, the indications of the system, in this case the phrases it generated, were better remembered. A completely opposite assessment was expected, because according to statistics collected earlier, the majority of respondents considered the generation of a password by the system itself to be somewhat complicated and annoying. Researchers believe that their system was able to avoid such epithets thanks to the mnemonic helper and script for correcting spelling errors.
For more information about the details of the study I recommend reading the report of scientists.
Epilogue
Despite all the attempts of different groups of researchers and developers, the mass introduction of passwords-passwords is not planned yet. According to them, this is due to a greater extent with the technical implementation of such systems. They suggest that giving the user the ability to independently create a phrase-password means sacrificing security, since the human factor greatly influences the choice of words and the phrase itself as a whole. In other words, many users continue to create simple passwords and passphrase-passwords suffer from this trend no less. If the system generates a passphrase and this is where its relationship with the user at the creation stage of protection is over, this will also cause denial in most people. It is necessary to develop not only new techniques for increasing the security level of passwords, changing their form, introducing new conditions for their creation and so on, but also help the user to keep this password in his head. An exaggerated example: once in the news there was a story about an unlucky man whose credit card was stolen. All savings were withdrawn from her only because he wrote his pin-code on it. Yes, remember 4 numbers and a sentence of 6 words are completely different things, but with a general beginning.
Perhaps the above study will seem absurd or simply inappropriate, but it also has the right to exist. I personally view it through the prism of people with a problem memory, which, surprisingly, the researchers do not mention in their work. After all, many people suffer from memory disorder, and there must be some methods for preserving and recreating information hidden in their minds. That is why I believe that the mnemonic assistant of the entry system is, although not the height of the desired, but also a very interesting and even fun method.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending friends30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
3 months for free if you pay for new Dell R630 for half a year - 2 x Intel Deca-Core Xeon E5-2630 v4 / 128GB DDR4 / 4x1TB HDD or 2x240GB SSD / 1Gbps 10 TB - from $ 99.33 a month , only until the end of August, order can be here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read aboutHow to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?