Gapz and Redyms droppers based on Power Loader code
Power Loader is a bot builder, which in fact are downloaders of other malware families. This builder is also another example of a modularity scheme that is used in the production of malware. We discovered bots based on Power Loader in September 2012. ESET defines as Win32 / Agent.UAW not modified droppers assembled using this builder. Our colleague Alexander Matrosov conducted his own investigation and found out that this builder was used to develop Win32 / Gapz droppers , starting in October 2012 . At the same time, as early as November 2012, malicious code known as Win32 / Redyms, used Power Loader components in his own dropper . The cost of Power Loader in the Russian cybercriminal market was around $ 500 for one builder with a C&C control panel.

(the picture above is the logo of the Power Loader product that one of the resellers used to sell it )
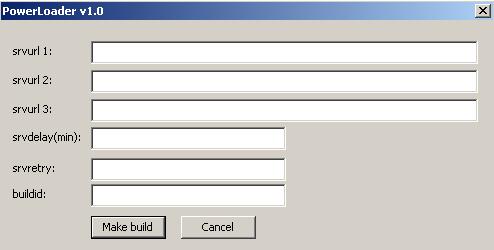
Fig. Build Interface
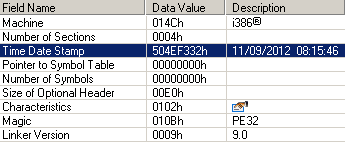
The first version of the Power Loader was compiled in early September 2012. The date of compilation of the file from the PE header is presented below.
Power Loader uses one main URL for C&C and two more reserved URLs. All configuration overhead is stored in the .cfg section of the executable file. This data is presented in text format and is not encrypted.

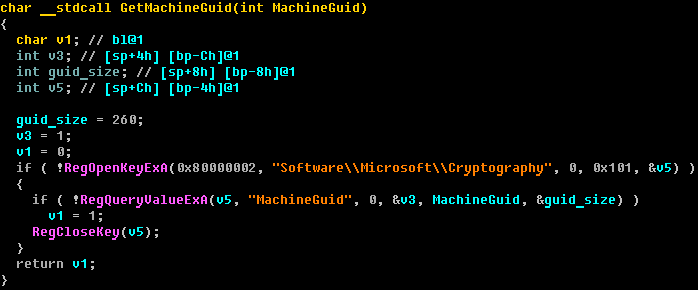
Bot ID - Bot ID is a unique MachineGuid value that is stored in the system registry. This bot identifier is used to create a mutex that signals the presence of malicious code in the system.
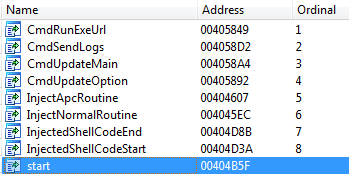
Different dropper families compiled using Power Loader have different export tables after unpacking the original dropper executable files. The export table in the bot created by the first version of the builder looks like this:

In this form, we cannot recognize the code for introducing malicious content into other processes using the HIPS bypass technique that is used in Gapz. But another modification of the malicious code, which was created using a different version of the builder, has special markers for the injected code. The export table in this case is presented below.

In the case of Win32 / Redyms, the export table looks like this:
This method of injecting code into explorer.exe is used to bypass HIPS and is based on the technique of using a trusted process. More information on this was published by us in this post .
Another interesting fact is that Power Loader uses the open source disassembler “Hacker Disassembler Engine” (aka HDE) to inject the code. And this engine is used by the Win32 / Gapz bootkit in one of the modules (shell code). This does not prove that there is one person behind Power Loader and Gapz, but, nevertheless, this is an interesting find. We continue our research and will soon publish even more interesting information.

(the picture above is the logo of the Power Loader product that one of the resellers used to sell it )

Fig. Build Interface
The first version of the Power Loader was compiled in early September 2012. The date of compilation of the file from the PE header is presented below.

Power Loader uses one main URL for C&C and two more reserved URLs. All configuration overhead is stored in the .cfg section of the executable file. This data is presented in text format and is not encrypted.

Bot ID - Bot ID is a unique MachineGuid value that is stored in the system registry. This bot identifier is used to create a mutex that signals the presence of malicious code in the system.

Different dropper families compiled using Power Loader have different export tables after unpacking the original dropper executable files. The export table in the bot created by the first version of the builder looks like this:

In this form, we cannot recognize the code for introducing malicious content into other processes using the HIPS bypass technique that is used in Gapz. But another modification of the malicious code, which was created using a different version of the builder, has special markers for the injected code. The export table in this case is presented below.

In the case of Win32 / Redyms, the export table looks like this:

This method of injecting code into explorer.exe is used to bypass HIPS and is based on the technique of using a trusted process. More information on this was published by us in this post .
Another interesting fact is that Power Loader uses the open source disassembler “Hacker Disassembler Engine” (aka HDE) to inject the code. And this engine is used by the Win32 / Gapz bootkit in one of the modules (shell code). This does not prove that there is one person behind Power Loader and Gapz, but, nevertheless, this is an interesting find. We continue our research and will soon publish even more interesting information.
