Encrypt and re-encrypt LUKS without data loss
Introduction
If you ever thought about encrypting data on disks after you have accumulated a decent amount of them, you were probably upset to read about the need to transfer data before creating an encrypted partition and after. Transferring 500 GB round-trip does not present any particular difficulty, such a volume can be temporarily downloaded even to the cloud, but if we are talking about encrypting 6 hard drives of 4 TB each, the task is noticeably more complicated. For some reason, the ability to encrypt and re-encrypt LUKS volumes without in-place re-encryption is poorly covered on the Internet, although there are two utilities for this: cryptsetup-reencrypt , which has been part of cryptsetup since 2012, and third-party luksipcthat appeared a year earlier. Both utilities perform basically the same thing - they encrypt a partition if it has not been encrypted, or they re-encrypt an existing one with other parameters. For my needs, I took advantage of the first, official.How it works?
Suppose you have a typical disk layout: one partition starts at 1 MiB (alignment for 4 KiB sectors) and ends at the end of the disk.
The LUKS header is located at the beginning, before the encrypted data. The header requires a minimum of 2056 512-byte sectors, i.e. a little more than 1MiB. The space before the start of the partition is clearly not enough for us, so first we need to reduce the size of the file system from its end so that cryptsetup-reencrypt transfers the blocks to the right, to the end of the disk, thereby freeing up space at the beginning of the section for the LUKS header. The final size of the header depends on the key length, the number of slots for passphrases, and other parameters, so I recommend being careful and putting 4 MiB under the heading.
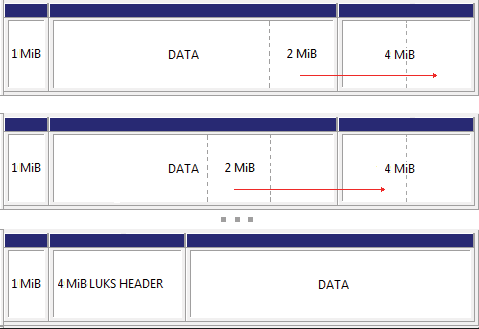
We encrypt!
First, reduce the size of the file system. In the case of ext4, this is done as follows:# e2fsck -f /dev/sdc1
e2fsck 1.42.12 (29-Aug-2014)
Pass 1: Checking inodes, blocks, and sizes
Pass 2: Checking directory structure
Pass 3: Checking directory connectivity
Pass 4: Checking reference counts
Pass 5: Checking group summary information
SAMS15TB: 17086/536592 files (0.4% non-contiguous), 341465037/366284385 blocks
# dumpe2fs /dev/sdc1|grep 'Block count'
dumpe2fs 1.42.12 (29-Aug-2014)
Block count: 366284385
# resize2fs /dev/sdc1 366283361
resize2fs 1.42.12 (29-Aug-2014)
Resizing the filesystem on /dev/sdc1 to 366283361 (4k) blocks.
The filesystem on /dev/sdc1 is now 366283361 (4k) blocks long.
where 366283361 = 366284385-1024 (blocks of 4k), i.e. reduce by 4 MiB
It should be noted that this will not reduce the size of the partition itself, it does not need to be reduced!
It makes sense to run a cryptsetup benchmark . Most likely, AES will be the fastest on your computer, as modern processors accelerate it hardware. On my computer, serpent turned out to be the fastest algorithm.
Getting to the encryption process itself. Attention! According to the assurances of the developers, cryptsetup-reencrypt is experimental software and can kill your data, so make a backup better.
# cryptsetup-reencrypt -c serpent-xts-plain64 -s 256 -N --reduce-device-size 4M /dev/sdc1
WARNING: this is experimental code, it can completely break your data.
Enter new passphrase:
Progress: 0.0%, ETA 1107:23, 168 MiB written, speed 21.5 MiB/s
…The parameter
-Nindicates the need to create a LUKS partition, and --reduce-device-sizeindicates an empty space after the file system. The encryption process is not fast, I have to wait, it took me about 3 days to do everything about everything. Make sure that you start cryptsetup-reencrypt from the directory to which you have write access, so you can stop the encryption process via CTRL + C and continue after if something went wrong.
After encryption is completed, we connect the disk to the device mapper and mount it:
# cryptsetup luksOpen /dev/sdc1 crypt
# mount /dev/mapper/crypt /media/hddThat's all. We received an encrypted drive that did not require data transfer.
