The official edition of Age of Empires Collector's Edition on DVD uses crack from the network
 The first parts of the game Age of Empires have long become a kind of classic. This game still has a lot of fans. In 2007, the official collector's edition of the game was released, which includes the first and second parts with additions. Moreover, in all countries except the USA, it came out on one DVD instead of four CDs. Then I was already doing a little reverse engineering of this gameand he knew that the original versions of the executable files would not want to work with one common disk, since the code for each part and their add-ons had a label check on the corresponding disk. Obviously, one DVD cannot have four different labels at once, and after buying a Russian DVD edition, I expected to see versions of files recompiled by the developers with a modified code to check for the presence of a disk or without it at all. But everything turned out to be much more interesting.
The first parts of the game Age of Empires have long become a kind of classic. This game still has a lot of fans. In 2007, the official collector's edition of the game was released, which includes the first and second parts with additions. Moreover, in all countries except the USA, it came out on one DVD instead of four CDs. Then I was already doing a little reverse engineering of this gameand he knew that the original versions of the executable files would not want to work with one common disk, since the code for each part and their add-ons had a label check on the corresponding disk. Obviously, one DVD cannot have four different labels at once, and after buying a Russian DVD edition, I expected to see versions of files recompiled by the developers with a modified code to check for the presence of a disk or without it at all. But everything turned out to be much more interesting.All in the worst traditions of pirate anthologies:
- all stylized (original) installers with beautiful graphics are replaced with standard ones;
- part of the original music lies on the DVD in the form of a sloppy rip with file names of the form “01-AudioTrack 01.wav”;
- during the game we don’t hear the original music - no one said to the game that the music should be taken from wav files, and not from the Audio CD, as it was in the original version;
- after installing the latest official updates from the Microsoft website, the game does not recognize the DVD as native and refuses to start.
No one was involved in adapting the game for the DVD edition!
Lost your source code? Did not find a suitable developer for a couple of minor edits and compilation of a new executable file? Or maybe there is a terrible bureaucracy at Microsoft, due to which even small and easily fixable errors are simply declared a feature of the application architecture?
All executable files are installed in decrypted form without SafeDisc (copy protection), which was used on the original CD. Ok, decrypted versions of the executable files from the publisher could well be. But then what about the drive label verification code?
As it turned out, it's all about cracking!
Yes, all the facts indicate that the hacked versions of the executable files for this publication were taken from the Internet and ... a little edited, perhaps to hide this fact.
Consider this with the example of Age of Empires II: The Conquerors 1.0c. Take the original encrypted executable file age2_x1.icd - it looks very well at the entire structure of the PE file, and only some parts of the machine code are encrypted. Using the known SafeDisc removal methods, we get the decrypted file age2_x1.exe . Now we have a reference file. Next, for research, let's take the NoCD network known for this version of the game, apparently created in the bowels of the already defunct Berserkers clan based on a patch from Myth at the end of 2001 (age2_x1_bsk.exe ). Also, from the collection edition DVD, install the English version of The Conquerors (/AOE2CONQ/EN/setup.exe) and take the installed game executable file ( age2_x1_dvd.exe ).
So, let's get down to research.
Compare the files with each other. The first one that catches the eye is the difference in the description of the sections of the exe file:
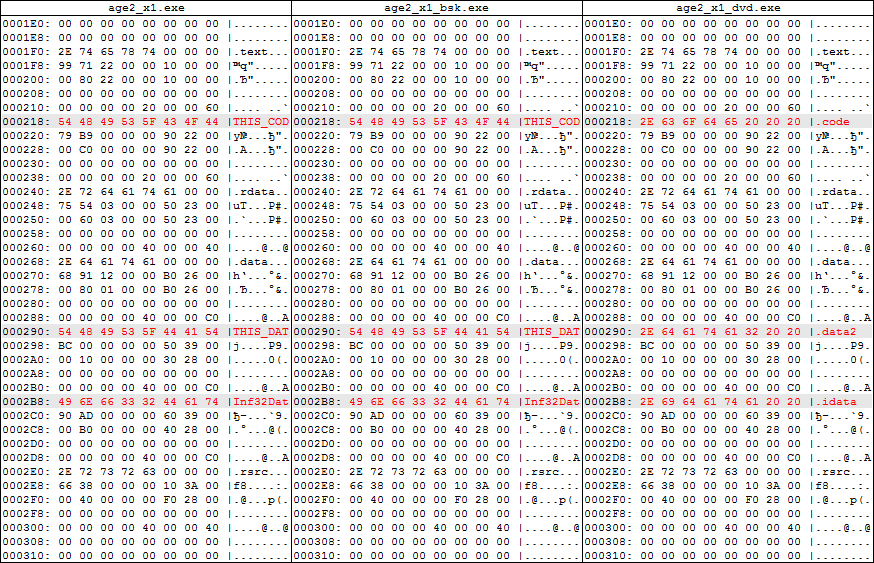
As you know, the names of the sections do not affect the execution of the program in any way and are purely informative. However, usually compilers give all sections familiar names like “.code”, “.data”, etc. But in the original executable file, some sections have atypical names “THIS_COD”, “THIS_DAT” and “Inf32Dat”. Most likely, such specific section names are associated with the use of SafeDisc. In the DVD file, these sections are renamed to the more familiar “.code”, “.data2” and “.idata”, and it is obvious that manually - extra characters are filled with spaces (code
20h), not zeros. That is, obviously, someone opened the executable file in the HEX editor and manually corrected the section names. It is possible to make the executable file look more typical. We also see that in BSK we left some service information for SafeDisc from the encrypted file age2_x1.icd before the beginning of the first section:

And at the end of the file:
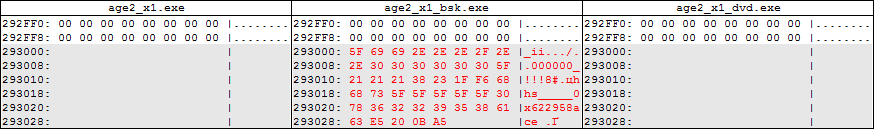
This information is stored in insignificant parts of the file and is not used by the game in any way. As you can see, in the DVD version there is no overhead information indicating that the file was previously protected by SafeDisc. But at the end of each section there is one small clue:

After the SafeDisc decoder is working, at the end of each section a label appears as a sequence of bytes
00 05 43 1F. In the source icd file there are zeros. Since this is the end of a section, this also means nothing to the main program. In the version of the file from BSK, we see that no one deleted them (they do not interfere - and okay). In the DVD version, we see that they also have not gone away.Well and the most interesting - we compare the machine code
Immediately we find the part of the machine code that is responsible for checking for the presence of a CD:

This function begins with an offset
485A0hand I already talked about it in an article about modifying this game . It describes a rather complicated logic of checking for the presence of a disk, but as a result, the function simply returns 0 in case of failure and 1 in case of success. I suggested for the patch to replace the code for all this healthy function with a simple sequence that always returns 1:xor eax, eax
inc eax
retn 4
But BSK approached this matter with a soul. Trained eye without disassembling sees that they replaced a pair of conditional branches
jz (74h)and jnz (75h)on an absolute jmp (EBh)and much more :) And if disassemble this site, we can trace a small miscalculation cracker of BSK - if there is no record with the drive letter in the registry, where the game is installed - the code will return 0, and the game will require you to insert a disc. Well, now the most important thing - in the executable file installed from the official collection DVD, all the machine code matches the byte with the version from BSK, including (a surprise for AoC lovers) several other strange code patches, apparently not related to checking the disk at all ( this remains to be seen):



That is, there is no doubt that the patched file from BSK formed the basis of the executable file for the collector's edition. Strictly speaking, it simply removed the remnants of service information for SafeDisc and changed the names of the sections.
And finally
I want to note that I have in my hands only the official Russian edition of the "New Disc". But there is every reason to believe that in other collector's editions the problem of incompatibility of games with DVDs is solved in a similar way.
With this post, I just wanted to emphasize the comic nature of the situation when even an official publisher is forced to use crackers that were created as if they were “bad uncles” for “bad goals”.
By the way, yes, all files are provided for informational purposes. After studying them, you must remove them.
Thanks for attention.
