Stealthphone: Protect your cellphone microphone from unauthorized activation
The rapid growth in sales of mobile phones in recent years and their huge impact on almost all areas of modern civilization, from politics, the military, banking, corporate to private, are simply amazing. Another characteristic feature of the development of mobile phones is the release of smartphones (more than one billion have been released by 2012) with the ability to connect to the Internet. By 2014, 80% of all calls to the World Wide Web will come from smartphones and tablets. Undoubtedly, the intense competition between mobile phone manufacturers was aimed primarily at making mobile phones cheap, outwardly attractive and able to work with numerous applications hosted on the Internet to please consumers and to increase demand. There are no miracles in engineering and technology. Ultimately, the struggle for leadership in the production of mobile phones has led to a significant reduction in their security in the storage and transmission of information. This is what the hackers took advantage of. According to Symantec, the world's damage from hackers in 2011 amounted to $ 400 billion (According to Symantec ).
A considerable part of this income was obtained due to the insufficient security of mobile phones, especially when they are used in the banking sector. Another reason was that recently, in connection with the global war on terrorism and other crimes related to high technology, including information, the government has sharply increased control over the mass media and, first of all, over mobile communications on the Internet . Intelligence agencies began to use various ways to obtain the information they need from virtually any electronic device. Recently, the Director of the CIA D. Petraeus called the new technologies, widely distributed among ordinary citizens, “transformational”, which have a huge impact on the work of intelligence. He said that new online devices are a treasury of data for his department. With the advent of “smart homes”, geo-referenced data (from photos on social networks, smartphones, navigators, etc.), the CIA can receive a lot of useful data in real time: from a person’s location to secretly shooting a cellphone or laptop with a camera. D. Petraeus said home appliances "are changing our minds about secrecy, personal information and secrecy." There is no doubt that such global control of information systems will significantly weaken the information security of citizens who use them. I will give an example. The German authorities admitted that they used a special program (the so-called Bundes Trojan) to monitor their citizens. The program was downloaded to a computer to an unsuspecting user and allowed it to load new malware, steal passwords, capture images on the built-in camera, or remotely turn on the microphone built into the computer. Interestingly, this software was developed by a private German company. After the scandal, the German government decided to continue to carry out such developments only at state-owned enterprises. But who can guarantee now that this Bundes Trojan did not fall into the hands of hackers? One can cite many such examples and make the sad conclusion that the public services of many countries, expanding the control of information of their citizens, are forced to open “loopholes” in the information protection of communication systems of citizens. Sooner or later, hackers who are currently armed with technical means of almost the same level as some of the special services can take advantage of this. That that hackers and terrorists have special weapons in their arsenal to collect and intercept information is also explained by the fact that many dictatorial regimes purchase the most advanced interception and control systems from the world's best manufacturers. And then, as a result of numerous “Arab” and other similar revolutions, a significant part of these funds falls into the hands of terrorists and hackers. Not for nothing that US President George W. Bush said in a statement to Congress that terrorists can wiretap any of our phones and intercept electronic communications.
Therefore, today, no one doubts the fact that none of the traditional methods can guarantee the security of personal information when using the Internet. This was acknowledged by the creators of the worldwide information network, Bob Kahn and Vint Cerf. In particular, in one of his interviews, Bob Cannes said: “I should have paid more attention to issues of identification and authenticity - where the email was sent from, with which device I’m now in touch. These things play a crucial role. ” In his opinion, today it is no longer possible to make the Internet safe and it is required to create a completely new information exchange network.
Users access the Internet from smartphones based on various operating systems and platforms, which entails the penetration of viruses spread through the Internet into the device. As a rule, in most cases, such viruses spread under the guise of useful software applications, the installation of which is confirmed by the user.
In particular, according to a study by Juniper Networks, installing free applications for the Android operating system, which is so popular in Russia, often carries a serious risk to the security and safety of personal information. Being installed on a smartphone, many mobile applications can perform functions that the user may not be aware of: location tracking, access to the user's contact list, secret initiation of sending SMS messages, turning on the camcorder and making a phone call. Juniper Networks experts established that in the case of Android OS, only 1 out of 40 (2.64%) free applications requests permission to send text messages without notifying the user, 5.53% of free applications have permission to access the device’s camera, 6 ,“Free Android apps often secretly make calls, use the camera” according to “The Register” of 11/01/2012 ). In the case of embedding the possibility of making a secret outgoing call into the memory of a mobile phone, the microphone of the mobile device turns into a "bug" used to covertly listen to conversations near the mobile phone. The possibility of visual detection by the user of this process without special equipment is excluded, since the device may, for example, be turned off or in standby mode.
As a typical example, reflecting the vulnerability of personal information of citizens when they use a mobile phone, the following can be cited.
The US FBI has begun using a new method for tracking suspects, remotely turning on the microphone of a mobile phone and turning it into a portable device to listen to conversations that are being held by its owner or the people around him. This technology, dubbed the “roving bug”, will soon be widely used, since any recently made phone has an integrated tracking device that allows you to eavesdrop and establish someone’s location with an accuracy of several feet ( “The FBI will get through the switched off mobile phone "source Utro.ru ).
Currently, the fact of tapping mobile phones and intercepting SMS is becoming a decisive factor for a court to indict. In the United States, the founder of the Galleon Group hedge fund, Raj Rajaratnam, who was convicted of illegal stock trading, was sentenced to seven years. The Galleon case was the first investigation of an insider crime, for the disclosure of which prosecutors recorded telephone conversations. "The successful use of Raj Rajaratnam’s conversation records in the court will change the rules of the Wall Street game. Investigators will now begin to apply this method more actively to other white-collar workers, and the company will take protective measures," says Kenneth Herzinger, a lawyer.
It is not surprising that hackers or criminals can take advantage of the “hole” in protecting the mobile phone’s microphone to collect incriminating evidence about the people they need, and first of all the law enforcement officers who are fighting them. Moreover, it is not so difficult to technically carry out such an “event” and is inexpensive.
All of the above facts confirm the need to protect the microphone of the mobile phone from unauthorized inclusion.
Technological solutions presented on the market and aimed at ensuring the confidentiality of negotiations and protecting against secret removal of information from the microphone of a mobile phone, do not fully or fully comply with information security requirements.
Users are offered hardware solutions that create acoustic interference to hide the information signal. We are talking about acoustic noise generators and acoustic safes for a mobile phone.
In the case of using an acoustic noise generator to protect the microphone of a mobile phone from unauthorized inclusion, it should be understood that the acoustic noise generator protects only from external voice recorders and cannot protect the microphone of a mobile phone when the user speaks to it. That is, the acoustic noise generator can be used only on condition that the phone is not used for a call. In addition, the noise produced by such generators also does not contribute to the comfort of negotiations, and its incorrect setting can lead to a violation of confidentiality and, as a result, hacker receiving information.
Acoustic safes, offered to ensure the security of information, also have serious drawbacks. Their cost is often very high, in addition, they, like acoustic noise generators, can protect their owner only if his mobile phone is in this acoustic safe.
In connection with the above, the use of noise interference generators and acoustic safes is unacceptable
for protection against unauthorized removal of information from the microphone of a mobile phone during a conversation on it.
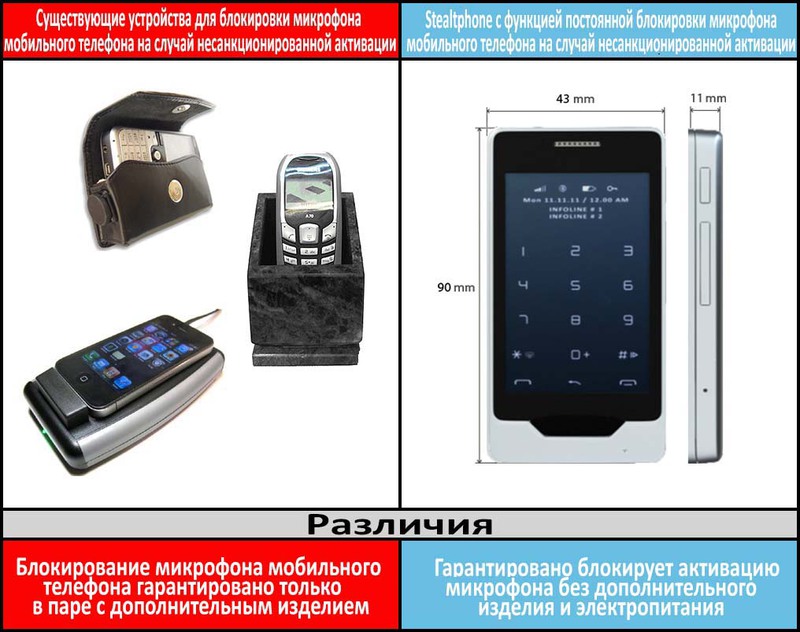
The way to protect the microphone of a mobile phone from unauthorized switching on, developed by Ancort, is a unique technology, which has no analogues in the world.
Unlike acoustic noise generators and acoustic safes, Ancort specialists created a solution that guarantees the security of voice information and confidentiality during negotiations when using a mobile phone.
The indisputable advantage of the Stealthphone technological solution created by Ancourt is the reliable protection of the microphone of the mobile phone from unauthorized data collection when it is in call mode. In addition, the microphone security of the standby mobile phone is ensured. The Stealthphone solution is based on the fact that the conversation is carried out through a microphone located directly in the Stealthphone device, which is connected via Bluetooth to a mobile phone. In this case, the mobile phone performs the function of transmitting an encrypted voice signal in the form of a digital sequence of signals. At the same time, the mobile phone performs the functions of a speech-like interference generator and an acoustic safe, which can be used as a regular case from a mobile phone,
Thus, the Stealthphone technological solution allows the user to ensure the microphone security of their mobile phone against unauthorized switching on both in standby mode and during a call. In addition, a number of additional features are offered, the description of which can be found on the company's website www.stealthphone.ru .
A considerable part of this income was obtained due to the insufficient security of mobile phones, especially when they are used in the banking sector. Another reason was that recently, in connection with the global war on terrorism and other crimes related to high technology, including information, the government has sharply increased control over the mass media and, first of all, over mobile communications on the Internet . Intelligence agencies began to use various ways to obtain the information they need from virtually any electronic device. Recently, the Director of the CIA D. Petraeus called the new technologies, widely distributed among ordinary citizens, “transformational”, which have a huge impact on the work of intelligence. He said that new online devices are a treasury of data for his department. With the advent of “smart homes”, geo-referenced data (from photos on social networks, smartphones, navigators, etc.), the CIA can receive a lot of useful data in real time: from a person’s location to secretly shooting a cellphone or laptop with a camera. D. Petraeus said home appliances "are changing our minds about secrecy, personal information and secrecy." There is no doubt that such global control of information systems will significantly weaken the information security of citizens who use them. I will give an example. The German authorities admitted that they used a special program (the so-called Bundes Trojan) to monitor their citizens. The program was downloaded to a computer to an unsuspecting user and allowed it to load new malware, steal passwords, capture images on the built-in camera, or remotely turn on the microphone built into the computer. Interestingly, this software was developed by a private German company. After the scandal, the German government decided to continue to carry out such developments only at state-owned enterprises. But who can guarantee now that this Bundes Trojan did not fall into the hands of hackers? One can cite many such examples and make the sad conclusion that the public services of many countries, expanding the control of information of their citizens, are forced to open “loopholes” in the information protection of communication systems of citizens. Sooner or later, hackers who are currently armed with technical means of almost the same level as some of the special services can take advantage of this. That that hackers and terrorists have special weapons in their arsenal to collect and intercept information is also explained by the fact that many dictatorial regimes purchase the most advanced interception and control systems from the world's best manufacturers. And then, as a result of numerous “Arab” and other similar revolutions, a significant part of these funds falls into the hands of terrorists and hackers. Not for nothing that US President George W. Bush said in a statement to Congress that terrorists can wiretap any of our phones and intercept electronic communications.
Therefore, today, no one doubts the fact that none of the traditional methods can guarantee the security of personal information when using the Internet. This was acknowledged by the creators of the worldwide information network, Bob Kahn and Vint Cerf. In particular, in one of his interviews, Bob Cannes said: “I should have paid more attention to issues of identification and authenticity - where the email was sent from, with which device I’m now in touch. These things play a crucial role. ” In his opinion, today it is no longer possible to make the Internet safe and it is required to create a completely new information exchange network.
Users access the Internet from smartphones based on various operating systems and platforms, which entails the penetration of viruses spread through the Internet into the device. As a rule, in most cases, such viruses spread under the guise of useful software applications, the installation of which is confirmed by the user.
In particular, according to a study by Juniper Networks, installing free applications for the Android operating system, which is so popular in Russia, often carries a serious risk to the security and safety of personal information. Being installed on a smartphone, many mobile applications can perform functions that the user may not be aware of: location tracking, access to the user's contact list, secret initiation of sending SMS messages, turning on the camcorder and making a phone call. Juniper Networks experts established that in the case of Android OS, only 1 out of 40 (2.64%) free applications requests permission to send text messages without notifying the user, 5.53% of free applications have permission to access the device’s camera, 6 ,“Free Android apps often secretly make calls, use the camera” according to “The Register” of 11/01/2012 ). In the case of embedding the possibility of making a secret outgoing call into the memory of a mobile phone, the microphone of the mobile device turns into a "bug" used to covertly listen to conversations near the mobile phone. The possibility of visual detection by the user of this process without special equipment is excluded, since the device may, for example, be turned off or in standby mode.
As a typical example, reflecting the vulnerability of personal information of citizens when they use a mobile phone, the following can be cited.
The US FBI has begun using a new method for tracking suspects, remotely turning on the microphone of a mobile phone and turning it into a portable device to listen to conversations that are being held by its owner or the people around him. This technology, dubbed the “roving bug”, will soon be widely used, since any recently made phone has an integrated tracking device that allows you to eavesdrop and establish someone’s location with an accuracy of several feet ( “The FBI will get through the switched off mobile phone "source Utro.ru ).
Currently, the fact of tapping mobile phones and intercepting SMS is becoming a decisive factor for a court to indict. In the United States, the founder of the Galleon Group hedge fund, Raj Rajaratnam, who was convicted of illegal stock trading, was sentenced to seven years. The Galleon case was the first investigation of an insider crime, for the disclosure of which prosecutors recorded telephone conversations. "The successful use of Raj Rajaratnam’s conversation records in the court will change the rules of the Wall Street game. Investigators will now begin to apply this method more actively to other white-collar workers, and the company will take protective measures," says Kenneth Herzinger, a lawyer.
It is not surprising that hackers or criminals can take advantage of the “hole” in protecting the mobile phone’s microphone to collect incriminating evidence about the people they need, and first of all the law enforcement officers who are fighting them. Moreover, it is not so difficult to technically carry out such an “event” and is inexpensive.
All of the above facts confirm the need to protect the microphone of the mobile phone from unauthorized inclusion.
Technological solutions presented on the market and aimed at ensuring the confidentiality of negotiations and protecting against secret removal of information from the microphone of a mobile phone, do not fully or fully comply with information security requirements.
Users are offered hardware solutions that create acoustic interference to hide the information signal. We are talking about acoustic noise generators and acoustic safes for a mobile phone.

In the case of using an acoustic noise generator to protect the microphone of a mobile phone from unauthorized inclusion, it should be understood that the acoustic noise generator protects only from external voice recorders and cannot protect the microphone of a mobile phone when the user speaks to it. That is, the acoustic noise generator can be used only on condition that the phone is not used for a call. In addition, the noise produced by such generators also does not contribute to the comfort of negotiations, and its incorrect setting can lead to a violation of confidentiality and, as a result, hacker receiving information.
Acoustic safes, offered to ensure the security of information, also have serious drawbacks. Their cost is often very high, in addition, they, like acoustic noise generators, can protect their owner only if his mobile phone is in this acoustic safe.
In connection with the above, the use of noise interference generators and acoustic safes is unacceptable
for protection against unauthorized removal of information from the microphone of a mobile phone during a conversation on it.
The way to protect the microphone of a mobile phone from unauthorized switching on, developed by Ancort, is a unique technology, which has no analogues in the world.
Unlike acoustic noise generators and acoustic safes, Ancort specialists created a solution that guarantees the security of voice information and confidentiality during negotiations when using a mobile phone.
The indisputable advantage of the Stealthphone technological solution created by Ancourt is the reliable protection of the microphone of the mobile phone from unauthorized data collection when it is in call mode. In addition, the microphone security of the standby mobile phone is ensured. The Stealthphone solution is based on the fact that the conversation is carried out through a microphone located directly in the Stealthphone device, which is connected via Bluetooth to a mobile phone. In this case, the mobile phone performs the function of transmitting an encrypted voice signal in the form of a digital sequence of signals. At the same time, the mobile phone performs the functions of a speech-like interference generator and an acoustic safe, which can be used as a regular case from a mobile phone,
Thus, the Stealthphone technological solution allows the user to ensure the microphone security of their mobile phone against unauthorized switching on both in standby mode and during a call. In addition, a number of additional features are offered, the description of which can be found on the company's website www.stealthphone.ru .
