How IT specialists and security guards protect themselves: real cases with Cisco Connect, BlackHat, RSAC and MWC
In a wide circle of people far from modern technologies, it is considered that IT and, even more so, information security specialists are paranoid who, under the influence of professional education, are reinsured and protect themselves with dozens of different protections, often overlapping each other for greater reliability. Alas, the reality is a bit different and today I would like to show what is usually hidden from a wide view. The discussion will focus on the results of monitoring the Internet activity of visitors to various major international and national events on modern information technologies and information security. Cisco is often the technology partner of conferences and exhibitions such as RSA in San Francisco, BlackHat in Singapore, Mobile World Congress in Barcelona, and the organizer of its own event, in different countries, then called Cisco Live, then Cisco Connect. And everywhere we use our monitoring technologies which I would like to share.

I will start with the Russian Cisco Connect, which takes place once a year in Moscow, and where Cisco presents its new products, telling about the experience of using them to solve various business and IT tasks. More than 2 thousand people attend this conference, who mainly belong to the category of engineers and leading specialists responsible for the operation of their infrastructures, which number from a few hundred to tens and hundreds of thousands of nodes. These specialists come to the Cisco Connect conference and, along with obtaining new knowledge, continue to be in touch with their supervisors or subordinates, responding to work mail or accessing various Internet resources in search of an answer to emerging questions. In other words, Cisco Connect visitors are actively using mobile devices (tablets, smartphones and laptops) and Cisco Internet access. The last time, in the spring, we decided to integrate our wireless infrastructure for Internet access with the DNS monitoring system - Cisco Umbrella.
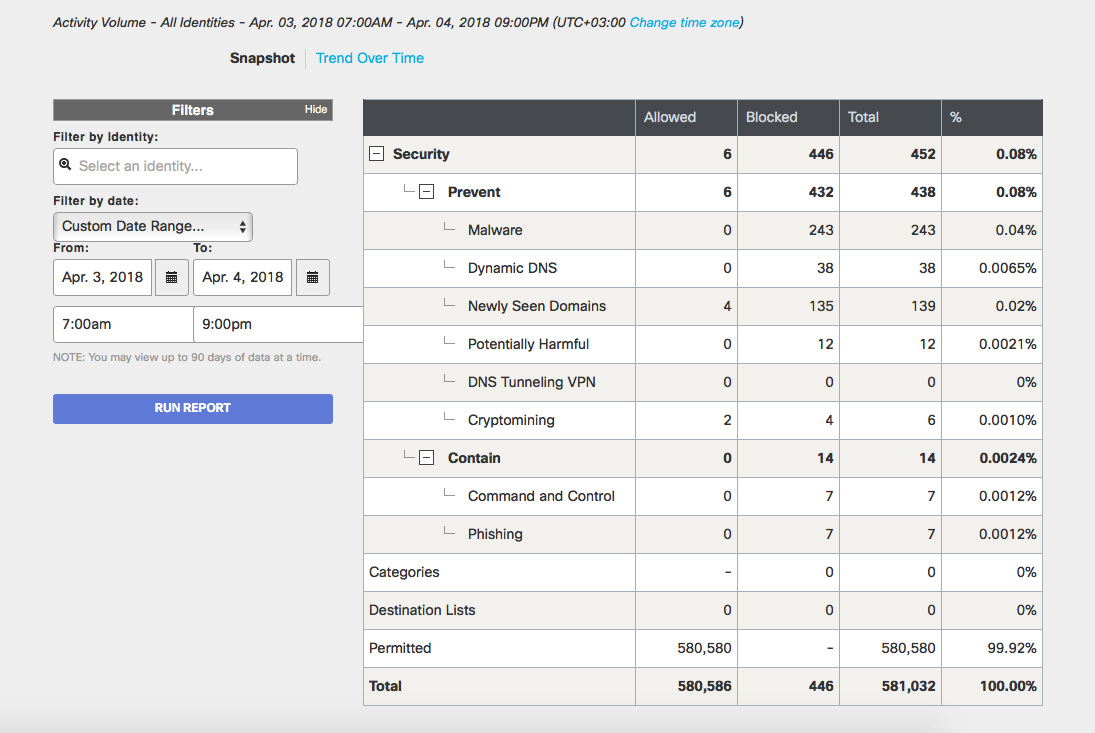
We did not estimate how many Cisco Connect participants used the provided wireless Internet access, and how many used 3G / 4G access provided by their mobile operator. But during the two days of the conference from 7 am April 3 to 9 pm on April 4, about 600 thousand DNS queries passed through the Cisco Umbrella service. This is not so much on the scale of the entire service, which handles about 120-150 billion requests per day. 0.08% of this number of requests had a brightly harmful focus and were blocked.
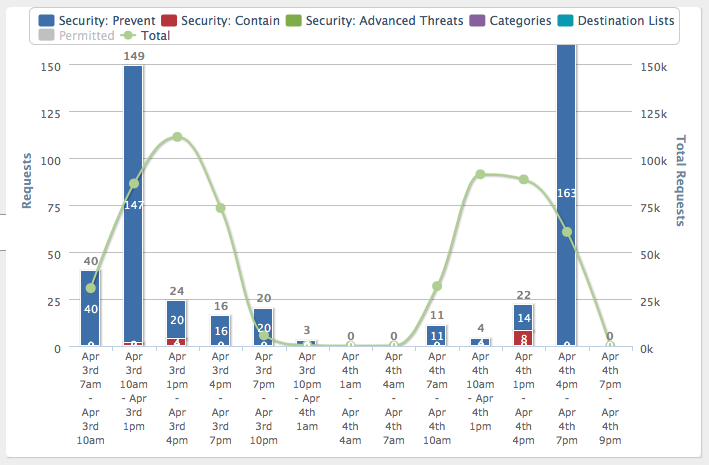
Interestingly, if on the first day about half of all malicious requests were recorded by us in the first half of the day (from 10 am to 1 pm), when there were plenary reports, then on the second day the activation of all the bad started after 4 pm, when The conference was coming to an end and the participants were preparing for a cultural program - a small buffet and participation in the concert. Low activity during the rest of the time indicates that Cisco Connect participants actively listened to the speeches of specialists from Cisco and its partners and were not distracted by surfing the Internet and working on mobile devices.
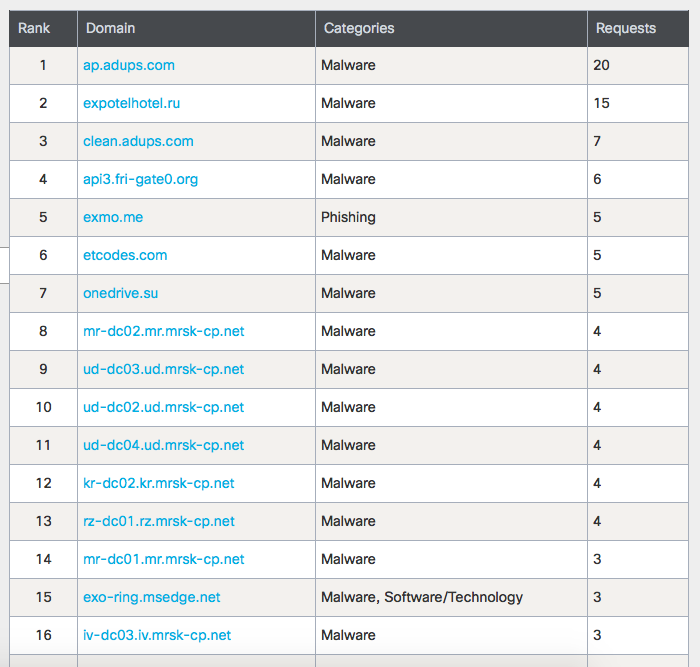
According to statistics, most of the blocked access attempts were associated with malicious code.
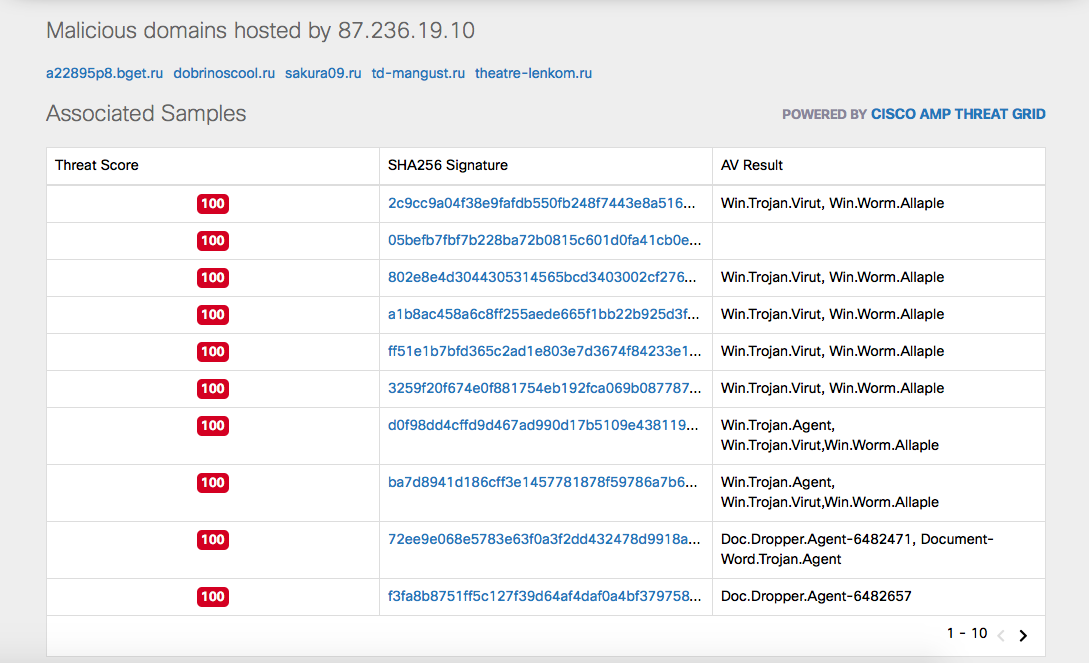
By itself, the Cisco Umbrella service cannot tell whether the visited resource is infected or not. Malicious samples associated with a domain say only that they communicate in some way with a blocked domain or IP address. For example, due to the spread of malicious code from this domain. Or because the malicious code accessed this domain as a kill switch (this is how the WannaCry acted). Or because of the use of the domain as a command server. In any case, this is a reason for additional investigation.
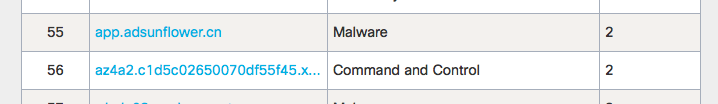
As for the command servers, we recorded such attempts.
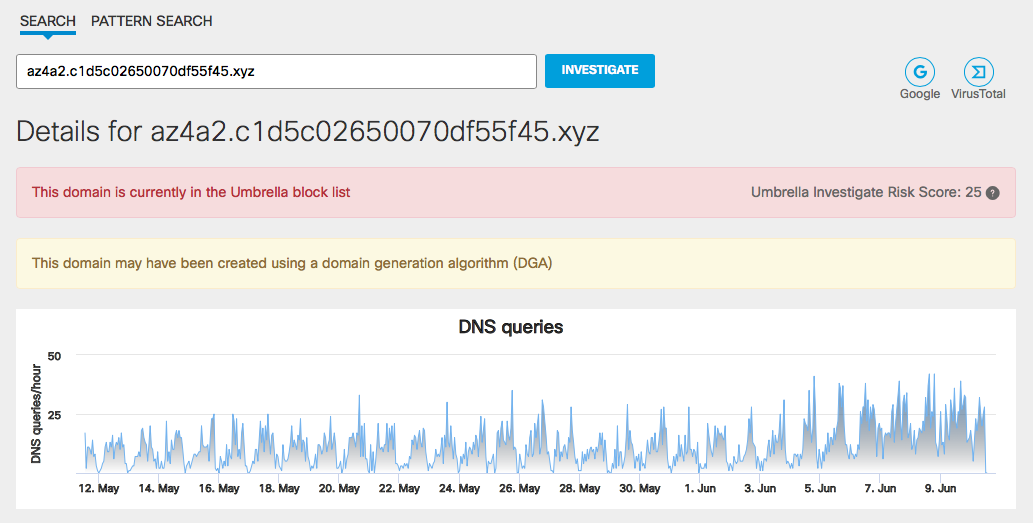
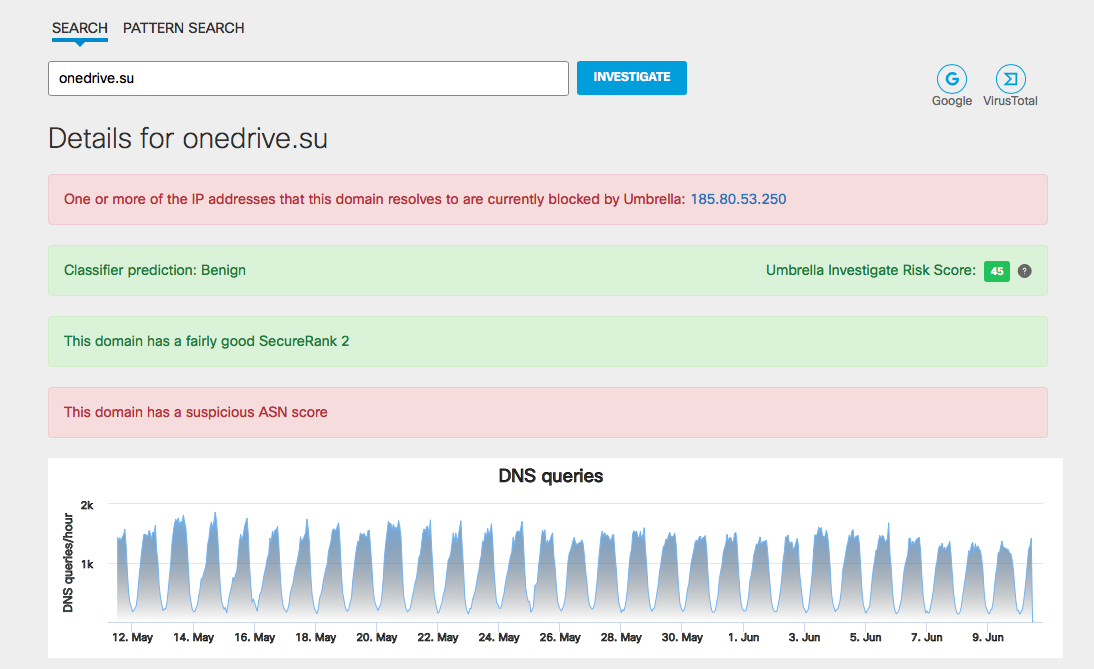
I’ll draw your attention to the fact that attackers actively exploit a topic relatedwith the use of clone domains or domains whose names are similar to the real ones. So it was during Cisco Connect, when we recorded attempts to access the onedrive [.] Su.
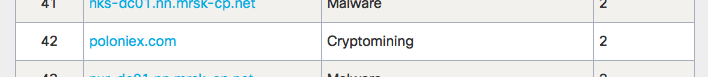
Finally, several attempts were related to the activity of crypto miners. This is another frontier zone, which requires additional investigation, since it cannot be said in advance whether mining in this case is legal (if someone decided to make some money) or the user's computer is being used in a hidden and improper way. I already wrote about various ways to detect mining using Cisco solutions - since then we have only strengthened our capabilities in this area.

It can be noted that compared to other IT and IB events, Cisco Connect is not so big (although in Russia it is one of the largest). But even in 2000-odd visitors, almost 250 attempts were made to interact with domains associated with malicious code, which is quite a lot for an audience that should perfectly understand the danger of this threat and be able to deal with it. Let's see what we were able to detect as part of the monitoring of the Wi-Fi environment at the world's largest exhibition on cyber security - RSAC, which was held in April this year in San Francisco. She was visited by 42 thousand people. Cisco, together with RSA, provided RSA SOC (for the fifth time), whose task was to prevent attacks on the Moscone Center wireless infrastructure (exhibition and conference venue).
Interestingly, at a much larger event than Cisco Connect, the number of malicious domains was comparable to 207. But we used crypto-mining domains used within RSAC using the Cisco Umbrella an order of magnitude more - 155. The most active were the following:
Paradoxically, at the world's largest information security event, where the entire industry gathers light (or most of it), users still continued to use unencrypted HTTP connections and download files through them, including bills, air tickets, commercial offers, materials for investors, etc. This is what we noted as the main problem during the weekly monitoring. It seemed that the RSA participants felt at home at the conference and did not care much about their safety. But all this information could be used to organize phishing - a large amount of valuable information was open for interception.
The presentation for a briefing with investors in general turned out to be an interesting situation. It contained quite valuable information from one of the RSA sponsors - we had to urgently look for them at the exhibition, make a tour to SOC, so that they could be convinced of the dangers of their actions on the spot and find out if the information available to the media and analysts is unsecured.
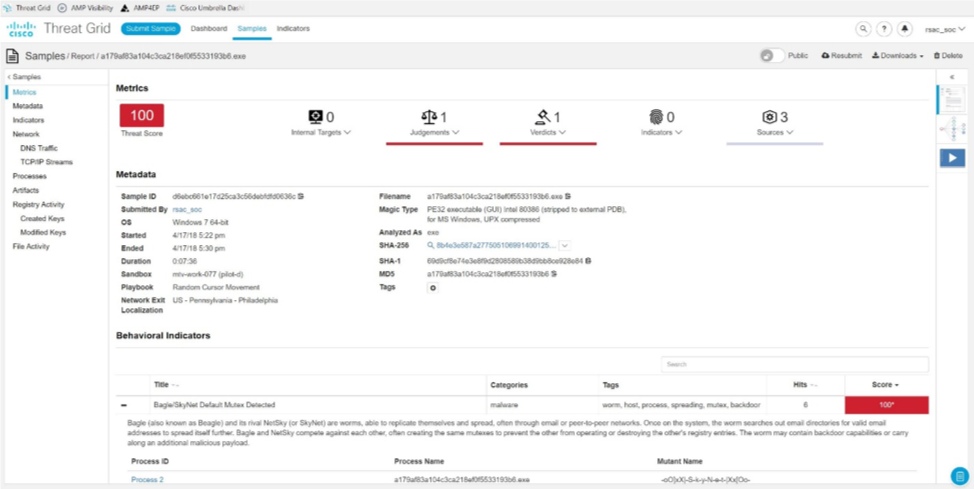
In just 5 days of the conference, RSA SOC recorded about 1,000 malicious files, among which were such as the version of the SkyNet worm.
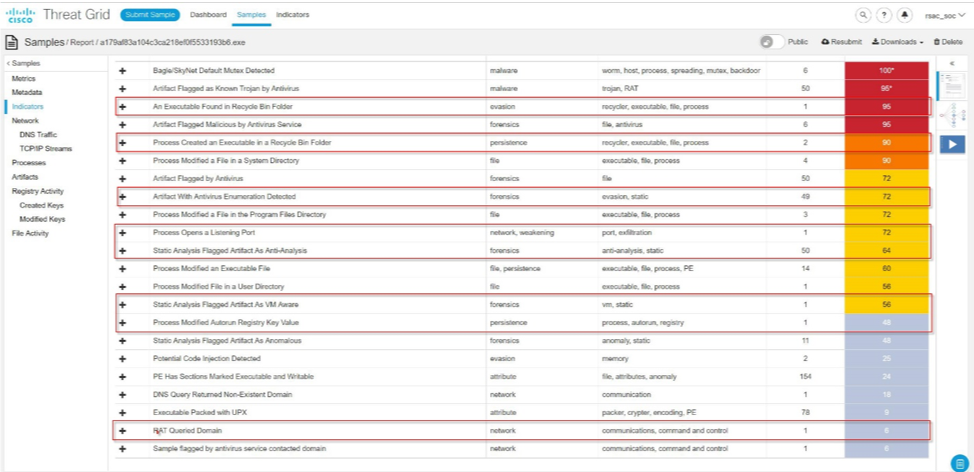
There were also interactions with command servers (there were 24 such attempts),

as well as phishing clone sites. For example, cragslist [.] Org, which mimics the well-known electronic ad site Graiglist, launched in San Francisco in the 90s and very popular among Americans.
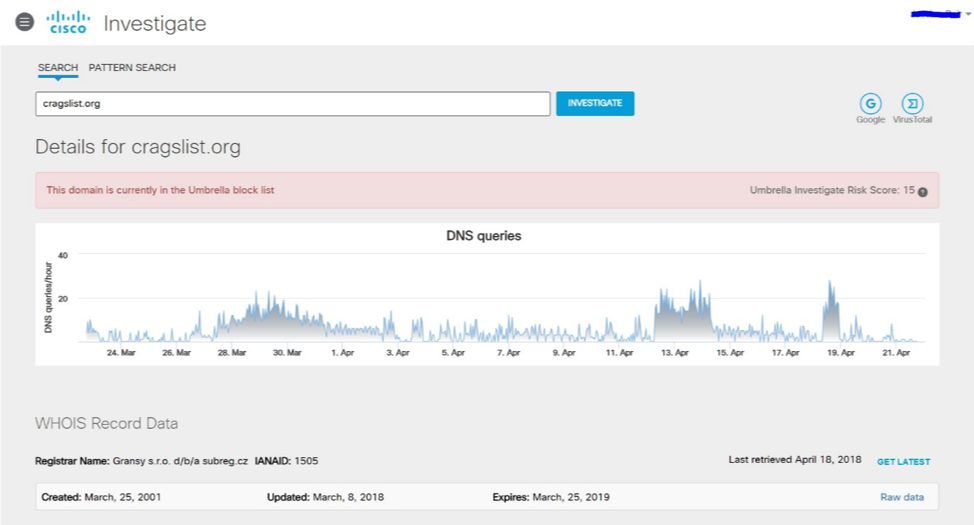
Fake site and attracted them, although he was registered in the Czech Republic.
What has changed at RSAC over the past year? The activity of crypto miners increased (especially Monero) and mobile malware appeared. But the carelessness of users remained at the same level - 30-35% of e-mail was transmitted in an unencrypted form using outdated POP and IMAPv2 protocols. And while other applications mainly used encryption, it was weak and built on vulnerable cryptographic protocols, for example, TLS 1.0. In addition, many applications, for example, home video surveillance, dating sites (full of travel security personnel :-), smart houses, even though they used authentication, the authentication data was transmitted in the clear! A paradox.
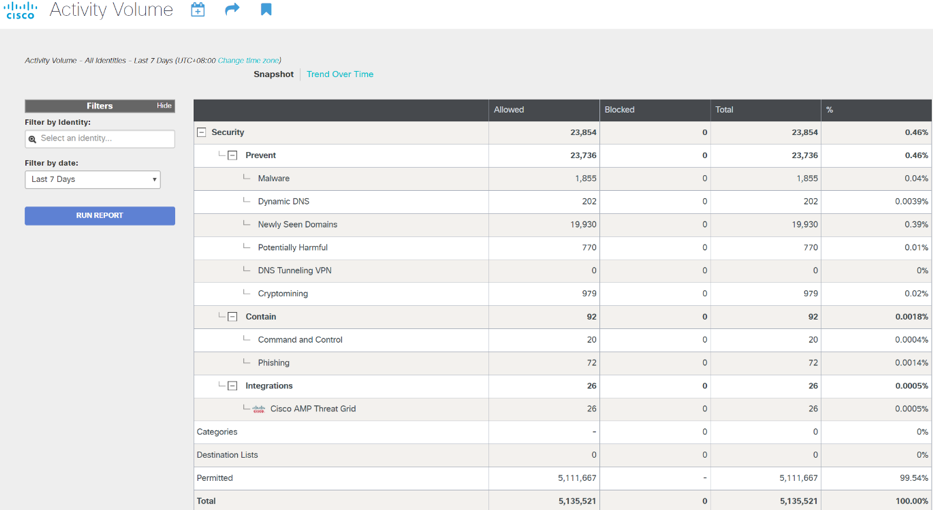
A slightly different picture was at the Mobile World Congress in Barcelona in the first quarter of this year, which was visited by 107 thousand people. To monitor the wireless network, we used our Cisco Stealthwatch analysis system. Encryption of Web traffic was used in 85% of cases (in Singapore BlackHat this value reached 96%).
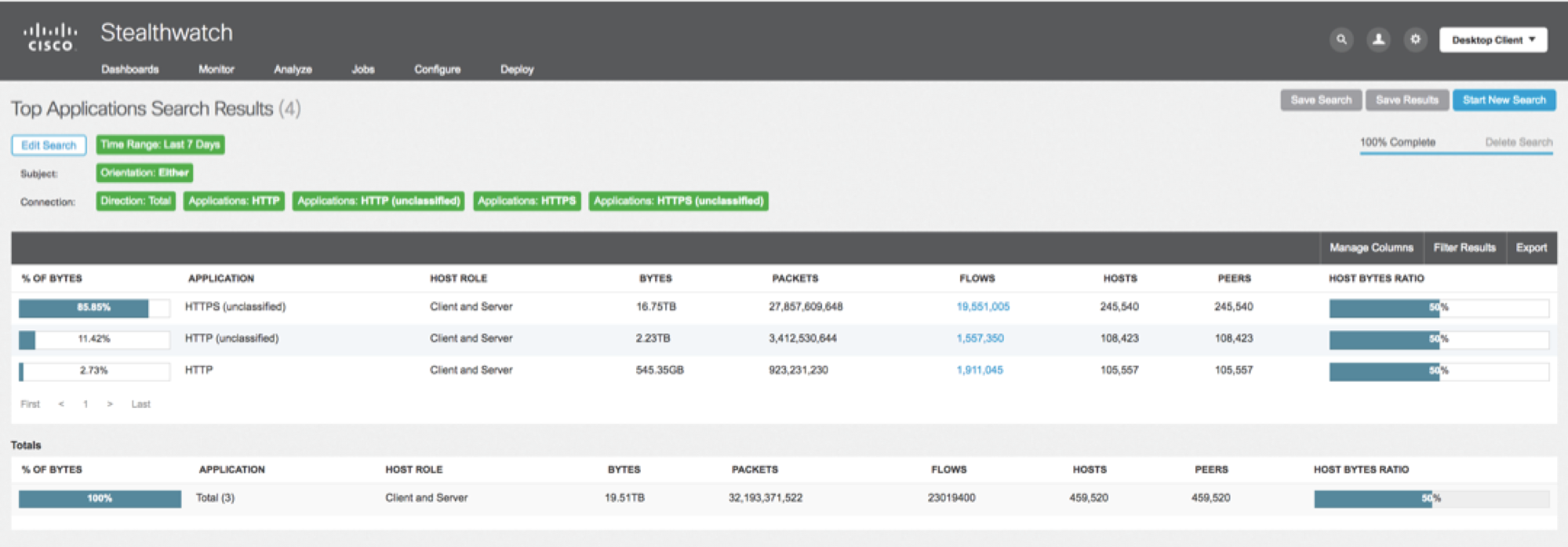
Analyzing Netflow, in two days (February 26 and 27) we recorded 32,000 security events, of which 350 could be defined as serious incidents:
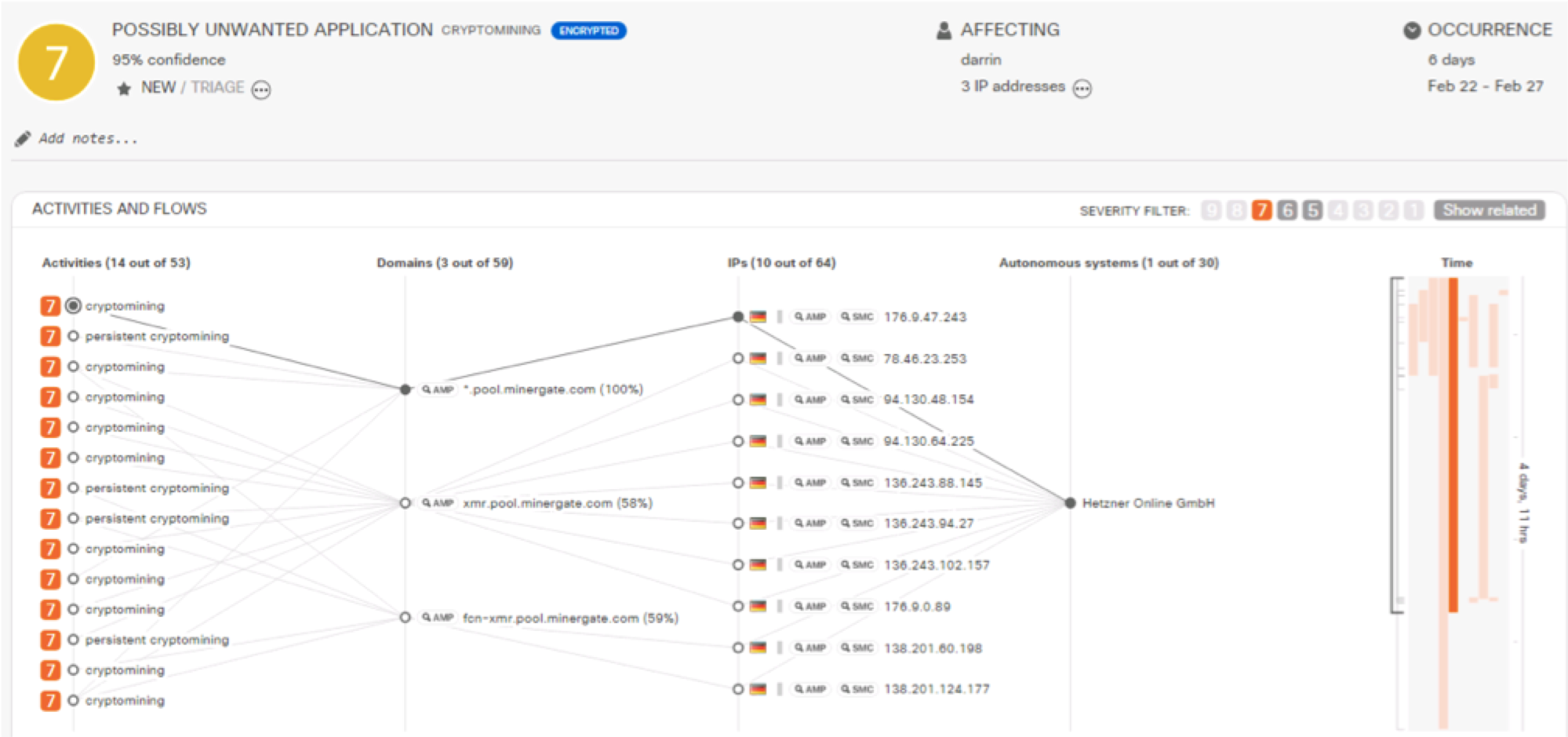
Some malware used PowerShell to communicate with HTTPS command servers. In general, malware is increasingly using encrypted connections (an increase of 268% over the past six months). We analyzed them using Encrypted Traffic Analytics technology built into Cisco Stealthwatch, which allows detecting malicious activity in encrypted traffic without decrypting or decrypting it.
I’ll finish the article about what is happening behind the scenes of information security and IT events, where specialists also fall under the distribution of intruders and cybercriminals, like ordinary users, with a story about how we monitored security in Singapore’s Black Hat, which took place in March 2018. This time we were part of the NOC, responsible for the security of the Asian information security event. But like RSAC, the same set of solutions was used — Cisco ThreatGrid for analyzing files, Cisco Umbrella for analyzing DNS, and Cisco Visibility for threat intelligence. Since many reports, labs, demonstrations and trainings required access to malicious sites and files, we did not block them, but only watched them. In general, the picture was similar to that described above, but I would like to tell about one interesting case.
On the first day of the conference, we recorded an unusual activity — over 1000 DNS queries to the www.blekeyrfid [.] Com domain in 1 hour. Additional investigation revealed that all activity was from one PC and only during the conference.
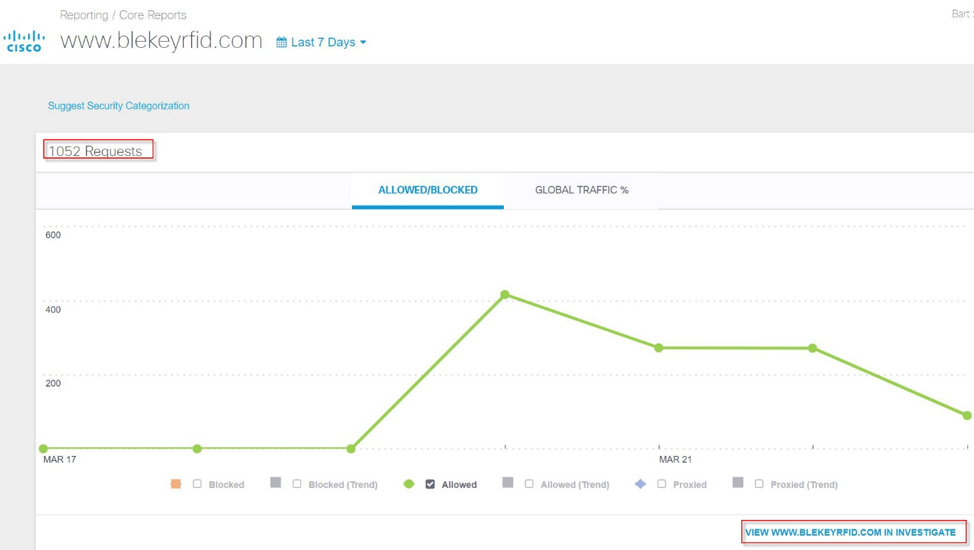
Moving from the Cisco Umbrella console to the Cisco Umbrella Investigate Investigation Tool, we began to learn what this domain is. The IP on which the domain was located was blacklisted by Umbrella. Access to such sites was acceptable for Black Hat Asia conference participants. However, we have blocked access to it from conference assets.
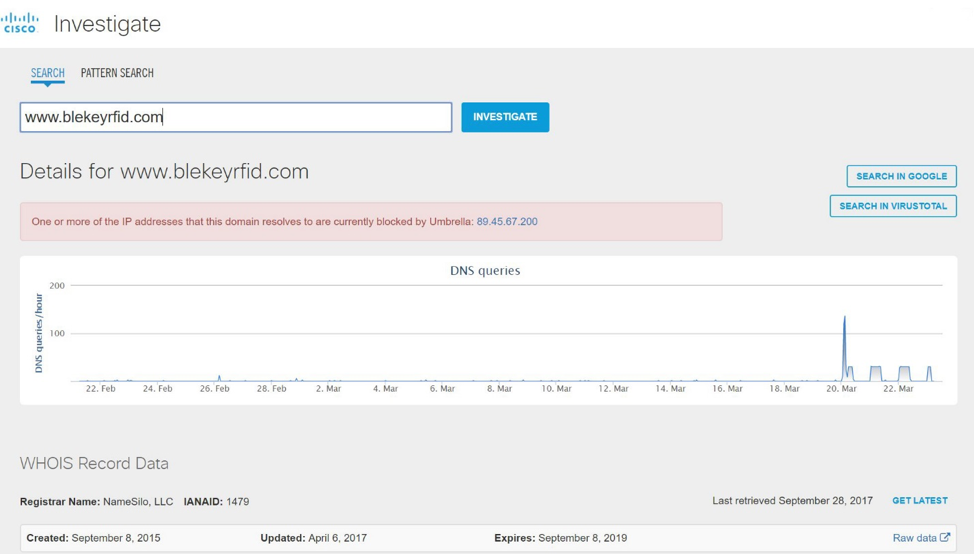
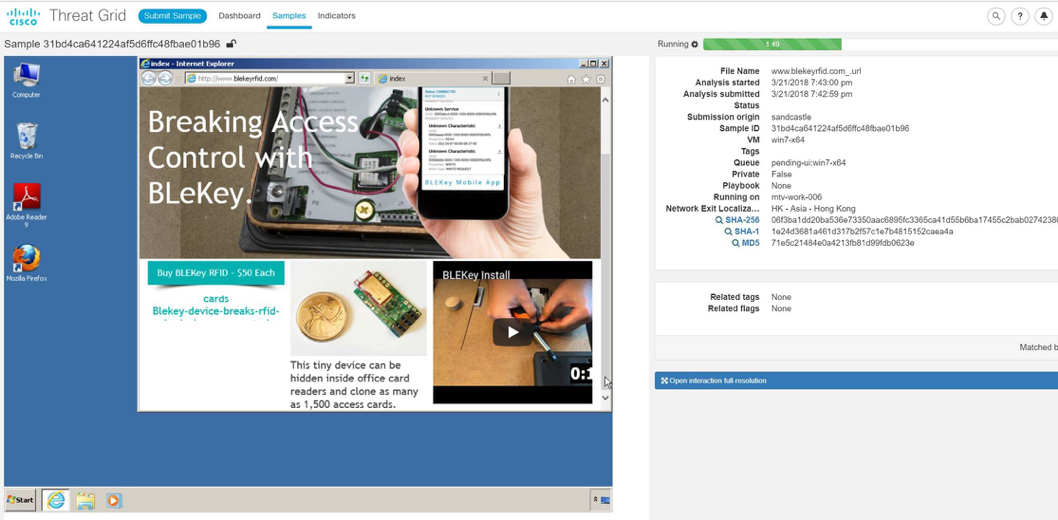
An investigation using ThreatGrid revealed that this domain advertised solutions for spoofing access control systems. Further information was passed on to the organizers, who had themselves carried out an appropriate investigation whether this activity was legal or not.
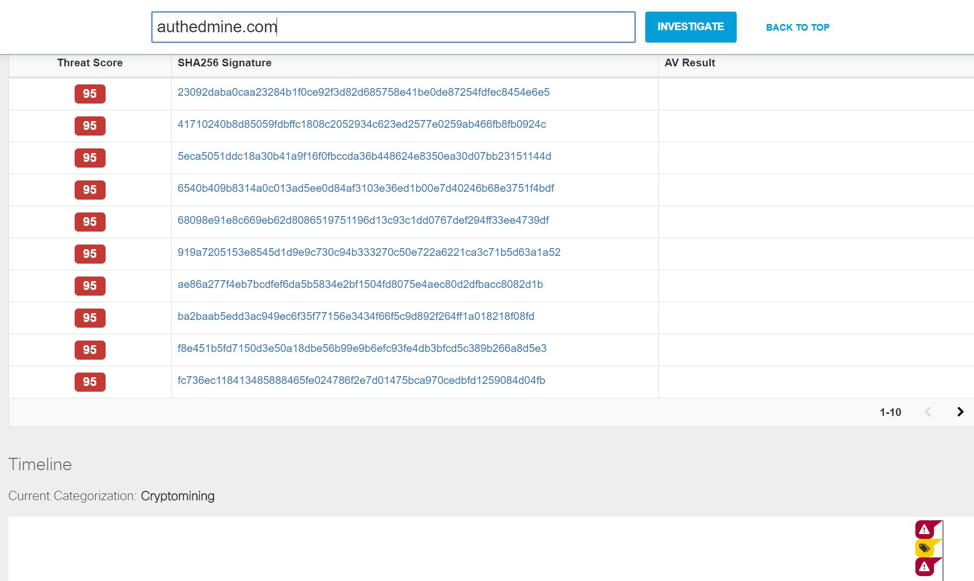
But the most common security event at Black Hat Asia has become crypto miners. For the first time we recorded such activity on the 2017 European Black Hat. In Singapore, it became just some kind of scourge. Most of the traffic from the conference led to the domain authedmine [.] Com, which is associated with coinhive [.] Com.

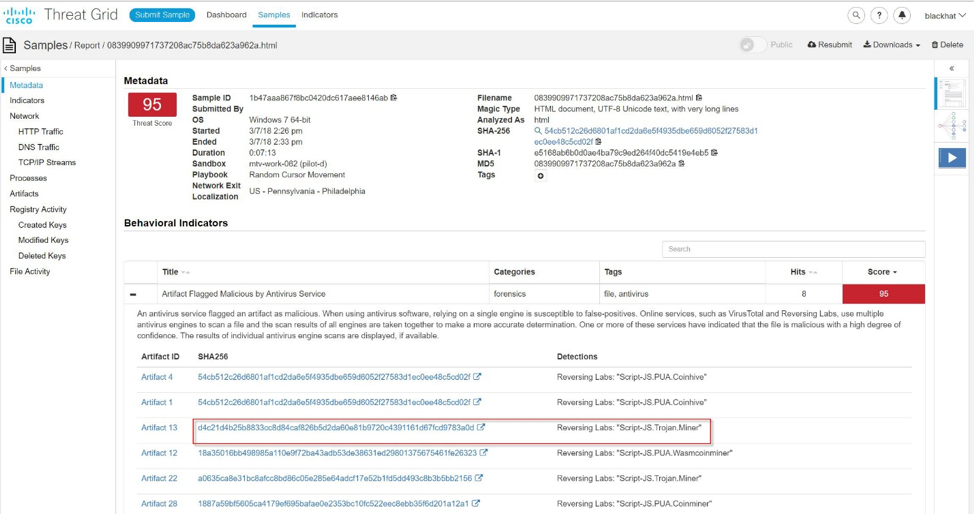
Analysis of this domain in Cisco Umbrella Investigate has shown that there are many malicious samples associated with it, which we analyzed in Cisco ThreatGrid.
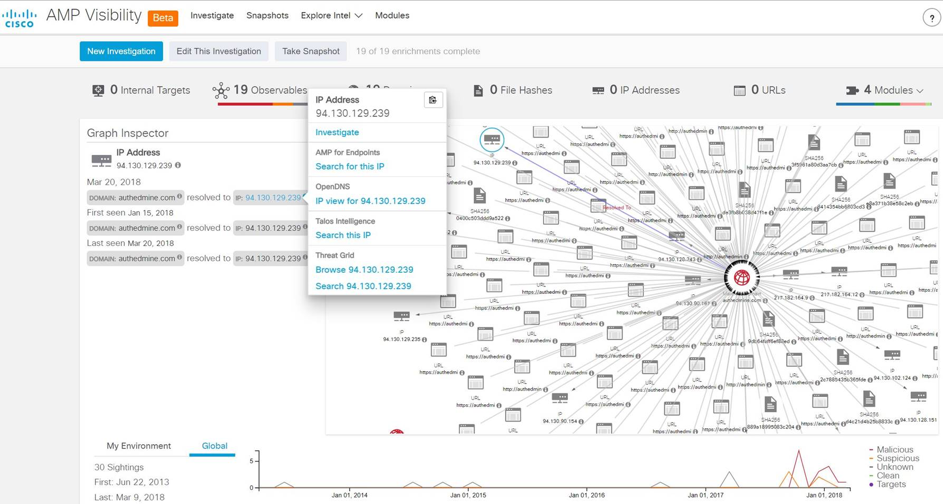
Thanks to a recently released new Cisco Visibility solution, we were able to better understand the architecture of the attackers and the relationship between IP addresses, artifacts, URLs and malicious samples.
Usually crypto-mining is implemented in two ways:
The owners of authedmine [.] Com state (as the analysis in ThreatGrid shows) that they use the first option.
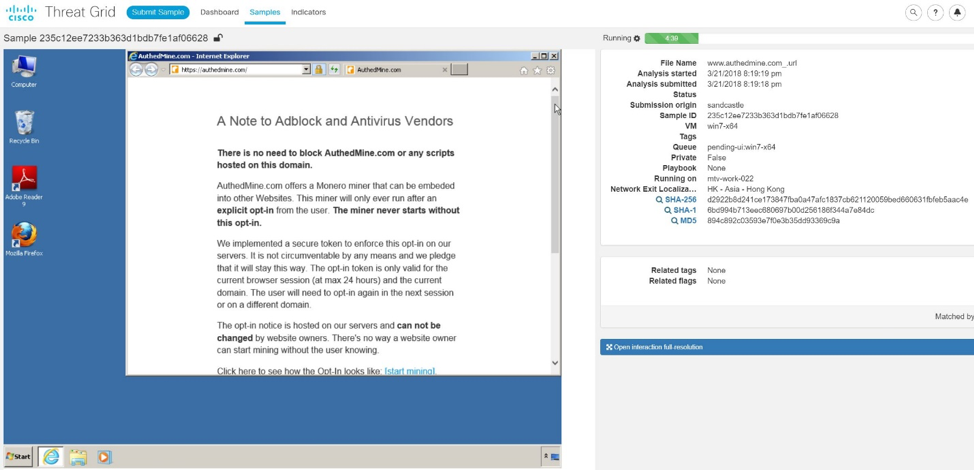
However, on the site itself, the .js script is used for mining (the method commonly used in the second variant), which is uploaded to Temporary Internet Files without the user's consent.

Using integrated and global threat intelligence data, we see that this script is used as an artifact in other samples that we analyzed using Cisco ThreatGrid.
Other mining domains were recorded:
What conclusions would I like to draw in concluding this review of our efforts to monitor various IT and IT activities in 2018:
PS: Very soon, in August, we will once again monitor the safety of Black Hat in Las Vegas and will definitely share with Habr's readers the results of our work.

I will start with the Russian Cisco Connect, which takes place once a year in Moscow, and where Cisco presents its new products, telling about the experience of using them to solve various business and IT tasks. More than 2 thousand people attend this conference, who mainly belong to the category of engineers and leading specialists responsible for the operation of their infrastructures, which number from a few hundred to tens and hundreds of thousands of nodes. These specialists come to the Cisco Connect conference and, along with obtaining new knowledge, continue to be in touch with their supervisors or subordinates, responding to work mail or accessing various Internet resources in search of an answer to emerging questions. In other words, Cisco Connect visitors are actively using mobile devices (tablets, smartphones and laptops) and Cisco Internet access. The last time, in the spring, we decided to integrate our wireless infrastructure for Internet access with the DNS monitoring system - Cisco Umbrella.
We did not estimate how many Cisco Connect participants used the provided wireless Internet access, and how many used 3G / 4G access provided by their mobile operator. But during the two days of the conference from 7 am April 3 to 9 pm on April 4, about 600 thousand DNS queries passed through the Cisco Umbrella service. This is not so much on the scale of the entire service, which handles about 120-150 billion requests per day. 0.08% of this number of requests had a brightly harmful focus and were blocked.

Interestingly, if on the first day about half of all malicious requests were recorded by us in the first half of the day (from 10 am to 1 pm), when there were plenary reports, then on the second day the activation of all the bad started after 4 pm, when The conference was coming to an end and the participants were preparing for a cultural program - a small buffet and participation in the concert. Low activity during the rest of the time indicates that Cisco Connect participants actively listened to the speeches of specialists from Cisco and its partners and were not distracted by surfing the Internet and working on mobile devices.

According to statistics, most of the blocked access attempts were associated with malicious code.

By itself, the Cisco Umbrella service cannot tell whether the visited resource is infected or not. Malicious samples associated with a domain say only that they communicate in some way with a blocked domain or IP address. For example, due to the spread of malicious code from this domain. Or because the malicious code accessed this domain as a kill switch (this is how the WannaCry acted). Or because of the use of the domain as a command server. In any case, this is a reason for additional investigation.

As for the command servers, we recorded such attempts.


I’ll draw your attention to the fact that attackers actively exploit a topic relatedwith the use of clone domains or domains whose names are similar to the real ones. So it was during Cisco Connect, when we recorded attempts to access the onedrive [.] Su.

Finally, several attempts were related to the activity of crypto miners. This is another frontier zone, which requires additional investigation, since it cannot be said in advance whether mining in this case is legal (if someone decided to make some money) or the user's computer is being used in a hidden and improper way. I already wrote about various ways to detect mining using Cisco solutions - since then we have only strengthened our capabilities in this area.



It can be noted that compared to other IT and IB events, Cisco Connect is not so big (although in Russia it is one of the largest). But even in 2000-odd visitors, almost 250 attempts were made to interact with domains associated with malicious code, which is quite a lot for an audience that should perfectly understand the danger of this threat and be able to deal with it. Let's see what we were able to detect as part of the monitoring of the Wi-Fi environment at the world's largest exhibition on cyber security - RSAC, which was held in April this year in San Francisco. She was visited by 42 thousand people. Cisco, together with RSA, provided RSA SOC (for the fifth time), whose task was to prevent attacks on the Moscone Center wireless infrastructure (exhibition and conference venue).

Interestingly, at a much larger event than Cisco Connect, the number of malicious domains was comparable to 207. But we used crypto-mining domains used within RSAC using the Cisco Umbrella an order of magnitude more - 155. The most active were the following:
- authedmine [.] com
- coinhive [.] com
- minergate [.] com
- www [.] cryptokitties [.] co
- api.bitfinex [.] com
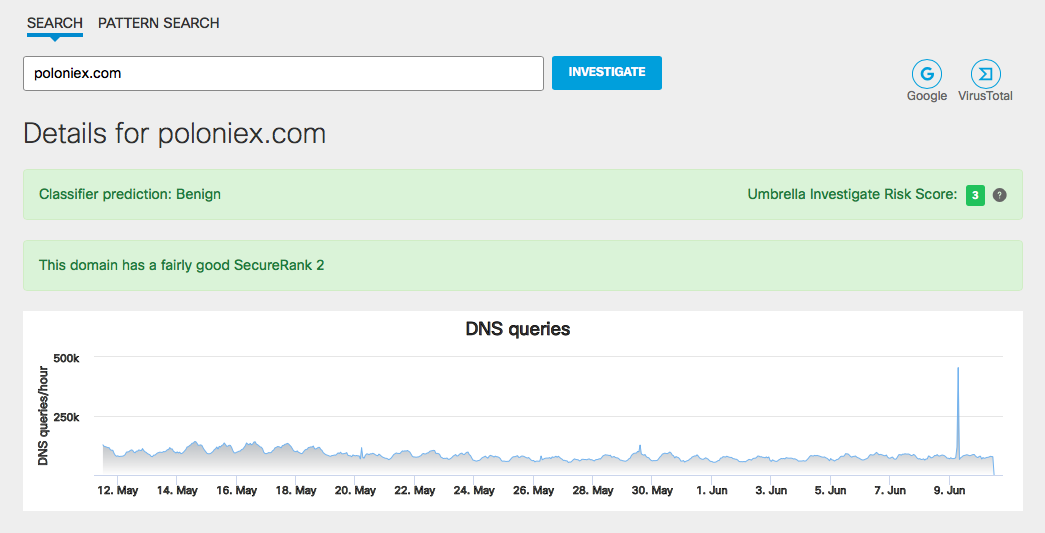
- poloniex [.] com (this one was also fixed on Cisco Connect)
- www [.] coinbase [.] com
- api.coinone.co [.] kr
- binance [.] com
- gemius [.] pl
Paradoxically, at the world's largest information security event, where the entire industry gathers light (or most of it), users still continued to use unencrypted HTTP connections and download files through them, including bills, air tickets, commercial offers, materials for investors, etc. This is what we noted as the main problem during the weekly monitoring. It seemed that the RSA participants felt at home at the conference and did not care much about their safety. But all this information could be used to organize phishing - a large amount of valuable information was open for interception.

The presentation for a briefing with investors in general turned out to be an interesting situation. It contained quite valuable information from one of the RSA sponsors - we had to urgently look for them at the exhibition, make a tour to SOC, so that they could be convinced of the dangers of their actions on the spot and find out if the information available to the media and analysts is unsecured.

In just 5 days of the conference, RSA SOC recorded about 1,000 malicious files, among which were such as the version of the SkyNet worm.


There were also interactions with command servers (there were 24 such attempts),

as well as phishing clone sites. For example, cragslist [.] Org, which mimics the well-known electronic ad site Graiglist, launched in San Francisco in the 90s and very popular among Americans.

Fake site and attracted them, although he was registered in the Czech Republic.

What has changed at RSAC over the past year? The activity of crypto miners increased (especially Monero) and mobile malware appeared. But the carelessness of users remained at the same level - 30-35% of e-mail was transmitted in an unencrypted form using outdated POP and IMAPv2 protocols. And while other applications mainly used encryption, it was weak and built on vulnerable cryptographic protocols, for example, TLS 1.0. In addition, many applications, for example, home video surveillance, dating sites (full of travel security personnel :-), smart houses, even though they used authentication, the authentication data was transmitted in the clear! A paradox.
A slightly different picture was at the Mobile World Congress in Barcelona in the first quarter of this year, which was visited by 107 thousand people. To monitor the wireless network, we used our Cisco Stealthwatch analysis system. Encryption of Web traffic was used in 85% of cases (in Singapore BlackHat this value reached 96%).

Analyzing Netflow, in two days (February 26 and 27) we recorded 32,000 security events, of which 350 could be defined as serious incidents:
- crypto miner activity
- Trojans for Android (Android.spy, Boqx, infected with firmware)
- malicious code SALITY
- malware actively scanning SMB services
- OSX Malware Genieo
- Conficker worms
- Revmob
- AdInjectors
- a number of mobile devices based on Android were infected
- unauthorized protocols such as Tor and BitTorrent.

Some malware used PowerShell to communicate with HTTPS command servers. In general, malware is increasingly using encrypted connections (an increase of 268% over the past six months). We analyzed them using Encrypted Traffic Analytics technology built into Cisco Stealthwatch, which allows detecting malicious activity in encrypted traffic without decrypting or decrypting it.

I’ll finish the article about what is happening behind the scenes of information security and IT events, where specialists also fall under the distribution of intruders and cybercriminals, like ordinary users, with a story about how we monitored security in Singapore’s Black Hat, which took place in March 2018. This time we were part of the NOC, responsible for the security of the Asian information security event. But like RSAC, the same set of solutions was used — Cisco ThreatGrid for analyzing files, Cisco Umbrella for analyzing DNS, and Cisco Visibility for threat intelligence. Since many reports, labs, demonstrations and trainings required access to malicious sites and files, we did not block them, but only watched them. In general, the picture was similar to that described above, but I would like to tell about one interesting case.
On the first day of the conference, we recorded an unusual activity — over 1000 DNS queries to the www.blekeyrfid [.] Com domain in 1 hour. Additional investigation revealed that all activity was from one PC and only during the conference.

Moving from the Cisco Umbrella console to the Cisco Umbrella Investigate Investigation Tool, we began to learn what this domain is. The IP on which the domain was located was blacklisted by Umbrella. Access to such sites was acceptable for Black Hat Asia conference participants. However, we have blocked access to it from conference assets.

An investigation using ThreatGrid revealed that this domain advertised solutions for spoofing access control systems. Further information was passed on to the organizers, who had themselves carried out an appropriate investigation whether this activity was legal or not.

But the most common security event at Black Hat Asia has become crypto miners. For the first time we recorded such activity on the 2017 European Black Hat. In Singapore, it became just some kind of scourge. Most of the traffic from the conference led to the domain authedmine [.] Com, which is associated with coinhive [.] Com.

Analysis of this domain in Cisco Umbrella Investigate has shown that there are many malicious samples associated with it, which we analyzed in Cisco ThreatGrid.

Thanks to a recently released new Cisco Visibility solution, we were able to better understand the architecture of the attackers and the relationship between IP addresses, artifacts, URLs and malicious samples.

Usually crypto-mining is implemented in two ways:
- explicit - the user explicitly agrees to participate in mining and makes efforts so that his antivirus and other security software do not block the crypto miner
- implicit - the user does not know that the browser open to them mines cryptocurrency, I use computer resources.
The owners of authedmine [.] Com state (as the analysis in ThreatGrid shows) that they use the first option.

However, on the site itself, the .js script is used for mining (the method commonly used in the second variant), which is uploaded to Temporary Internet Files without the user's consent.

Using integrated and global threat intelligence data, we see that this script is used as an artifact in other samples that we analyzed using Cisco ThreatGrid.

Other mining domains were recorded:
- www [.] cryptokitties [.] co
- bitpay [.] com
- www [.] genesis-mining [.] com
- ws010 [.] coinhive [.] com
- www [.] cryptomining [.] farm
- www [.] ledgerwallet [. [com
- ethereum [.] miningpoolhub [.] com
- miningpoolhub [.] com
- push [.] coinone.co [.] kr
- ws [.] coinone.co [.] kr
- getmonero [.] org
- widgets [.] bitcoin [.] com
- index [.] bitcoin [.] com
- api [.] nanopool [.] org
- wss [.] bithumb [.] com
- api [.] bitfinex [.] com

What conclusions would I like to draw in concluding this review of our efforts to monitor various IT and IT activities in 2018:
- Even information security or IT specialists who are supposed to be able to defend themselves according to their positions do not always do this correctly.
- At conferences on information security and IT, many experts are careless and can not only connect to a fake access point, but also use unprotected protocols to authenticate on various resources or to work with e-mail, opening up interesting and dangerous opportunities for attackers.
- Mobile devices are an interesting target for intruders. The situation is aggravated by the fact that such devices are usually poorly protected and are not under the shadow of the perimeter ITU, IDS, DLP, access control systems and e-mail security. Infecting such devices and coming to work with them can entail much more sad consequences than incompatible with the user mining.
PS: Very soon, in August, we will once again monitor the safety of Black Hat in Las Vegas and will definitely share with Habr's readers the results of our work.
