D-Link and Changing Information Technologies certificates were used to sign malware.
ESET discovered a new cyber campaign, which uses stolen certificates to sign code. Digital certificates from D-Link Corporation and Changing Information Technologies have been stolen by a highly skilled cyber espionage team focused on East Asia.

We recorded a malicious campaign when our systems marked several files as suspicious. Interestingly, the marked files were digitally signed with a valid certificate from D-Link Corporation. The same certificate was used to sign legitimate D-Link software; most likely this certificate has been stolen.
After confirming the harmfulness of the file, we reported a problem in D-Link, which began its own investigation. As a result, on July 3, the company revoked the compromised digital certificate.
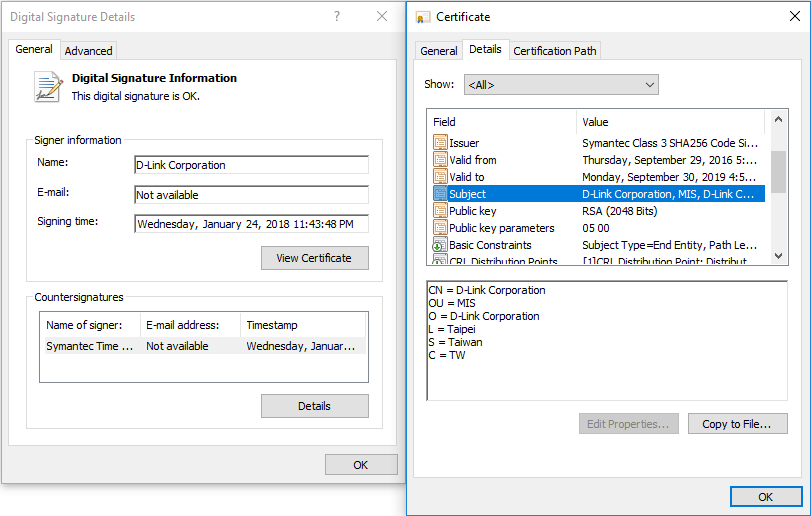
Figure 1. The D-Link digital certificate is used to sign malware.
In the course of the study, we found two families of malware using stolen certificates - a backdoor to remotely control the target device and its associated component to steal passwords. JPCERT recently published a detailed analysis of the Plead backdoor; according to Trend Micro, it is used by the BlackTech cyber spy group .
In addition to the D-Link digital signature Plead samples, we identified samples signed by the Taiwanese security company Changing Information Technology Inc.
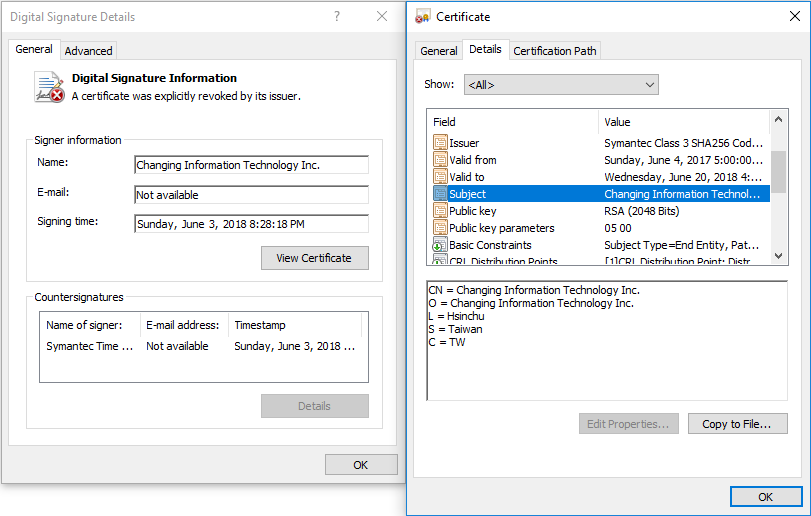
Figure 2. Digital Certificate Changing Information Technology Inc. used to sign malware
Certificate of Changing Information Technology Inc. recalled on July 4, 2017, but the BlackTech group still uses it to sign its malicious tools.
The possibility of compromising several Taiwanese technology companies and reusing their certificates in new attacks demonstrates the high qualification of the cyber group and its interest in the region.
The signed Plead samples are strongly obfuscated using the garbage code, but the purpose of malware is the same for all samples — download from a remote server or open a small, encrypted binary blob from a local disk. It contains an encrypted shellcode that loads the final Plead backdoor module.
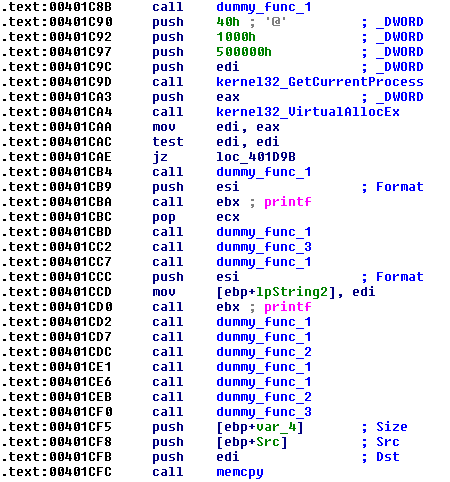
Figure 3. Obfuscated Plead backdoor code
The password theft tool is used to collect saved passwords in the following applications:
- Google Chrome
- Microsoft Internet Explorer
- Microsoft Outlook
- Mozilla Firefox
Using stolen digital certificates is one way to disguise. Certificates help malware look legitimate and therefore bypass protection without arousing suspicion.
Probably the most well-known malware that used several “alien” certificates - Stuxnet , discovered in 2010 and known as the first cyber weapon, focused on critical infrastructure. Stuxnet used digital certificates stolen from RealTek and JMicron, well-known technology companies from Taiwan.
However, this tactic is not exceptional for such large-scale incidents as Stuxnet, as evidenced by the latest discovery.
Detection by ESET products:
Win32 / PSW.Agent.OES trojan
Win32 / Plead.L trojan
Win32 / Plead.S trojan
Win32 / Plead.T trojan
Win32 / Plead.U trojan
Win32 / Plead.V trojan
Win32 / Plead.X trojan
Win32 / trojan Plead.Y
Win32 / Plead.Z trojan
Unsigned samples (SHA-1):
80AE7B26AC04C93AD693A2D816E8742B906CC0E3
62A693F5E4F92CCB5A2821239EFBE5BD792A46CD
B01D8501F1EEAF423AA1C14FCC816FAB81AC8ED8
11A5D1A965A3E1391E840B11705FFC02759618F8
239786038B9619F9C22401B110CF0AF433E0CEAD
signed samples (SHA-1):
1DB4650A89BC7C810953160C6E41A36547E8CF0B
CA160884AE90CFE6BEC5722FAC5B908BF77D9EEF
9C4F8358462FAFD83DF51459DBE4CD8E5E7F2039
13D064741B801E421E3B53BC5DABFA7031C98DD9
C & C-servers:
[.] Amazon.panasocin com
[.] Office.panasocin com
[.] Okinawas.ssl443 org
certificate serial number for the code signature:
D-Link Corporation:
13: 03: 03: E4: 57: 0c : 27: 29: 09: E2: 65: Dd: B8: 59: De: Ef
Changing Information Technology Inc .: 73: 65: ED: E7: F8: FB: B1: 47: 67: 02: D2: 93: 08: 39: 6F: 51
1E: 50: CC: 3D: D3: 9B: 4A: CC: 5E: 83: 98: CC: D0: DD: 53: EA

We recorded a malicious campaign when our systems marked several files as suspicious. Interestingly, the marked files were digitally signed with a valid certificate from D-Link Corporation. The same certificate was used to sign legitimate D-Link software; most likely this certificate has been stolen.
After confirming the harmfulness of the file, we reported a problem in D-Link, which began its own investigation. As a result, on July 3, the company revoked the compromised digital certificate.

Figure 1. The D-Link digital certificate is used to sign malware.
Malicious software
In the course of the study, we found two families of malware using stolen certificates - a backdoor to remotely control the target device and its associated component to steal passwords. JPCERT recently published a detailed analysis of the Plead backdoor; according to Trend Micro, it is used by the BlackTech cyber spy group .
In addition to the D-Link digital signature Plead samples, we identified samples signed by the Taiwanese security company Changing Information Technology Inc.

Figure 2. Digital Certificate Changing Information Technology Inc. used to sign malware
Certificate of Changing Information Technology Inc. recalled on July 4, 2017, but the BlackTech group still uses it to sign its malicious tools.
The possibility of compromising several Taiwanese technology companies and reusing their certificates in new attacks demonstrates the high qualification of the cyber group and its interest in the region.
The signed Plead samples are strongly obfuscated using the garbage code, but the purpose of malware is the same for all samples — download from a remote server or open a small, encrypted binary blob from a local disk. It contains an encrypted shellcode that loads the final Plead backdoor module.

Figure 3. Obfuscated Plead backdoor code
The password theft tool is used to collect saved passwords in the following applications:
- Google Chrome
- Microsoft Internet Explorer
- Microsoft Outlook
- Mozilla Firefox
Why steal digital certificates?
Using stolen digital certificates is one way to disguise. Certificates help malware look legitimate and therefore bypass protection without arousing suspicion.
Probably the most well-known malware that used several “alien” certificates - Stuxnet , discovered in 2010 and known as the first cyber weapon, focused on critical infrastructure. Stuxnet used digital certificates stolen from RealTek and JMicron, well-known technology companies from Taiwan.
However, this tactic is not exceptional for such large-scale incidents as Stuxnet, as evidenced by the latest discovery.
Indicators of compromise:
Detection by ESET products:
Win32 / PSW.Agent.OES trojan
Win32 / Plead.L trojan
Win32 / Plead.S trojan
Win32 / Plead.T trojan
Win32 / Plead.U trojan
Win32 / Plead.V trojan
Win32 / Plead.X trojan
Win32 / trojan Plead.Y
Win32 / Plead.Z trojan
Unsigned samples (SHA-1):
80AE7B26AC04C93AD693A2D816E8742B906CC0E3
62A693F5E4F92CCB5A2821239EFBE5BD792A46CD
B01D8501F1EEAF423AA1C14FCC816FAB81AC8ED8
11A5D1A965A3E1391E840B11705FFC02759618F8
239786038B9619F9C22401B110CF0AF433E0CEAD
signed samples (SHA-1):
1DB4650A89BC7C810953160C6E41A36547E8CF0B
CA160884AE90CFE6BEC5722FAC5B908BF77D9EEF
9C4F8358462FAFD83DF51459DBE4CD8E5E7F2039
13D064741B801E421E3B53BC5DABFA7031C98DD9
C & C-servers:
[.] Amazon.panasocin com
[.] Office.panasocin com
[.] Okinawas.ssl443 org
certificate serial number for the code signature:
D-Link Corporation:
13: 03: 03: E4: 57: 0c : 27: 29: 09: E2: 65: Dd: B8: 59: De: Ef
Changing Information Technology Inc .: 73: 65: ED: E7: F8: FB: B1: 47: 67: 02: D2: 93: 08: 39: 6F: 51
1E: 50: CC: 3D: D3: 9B: 4A: CC: 5E: 83: 98: CC: D0: DD: 53: EA
