In Office 365 Outlook found undocumented APIs with detailed logs of user activity
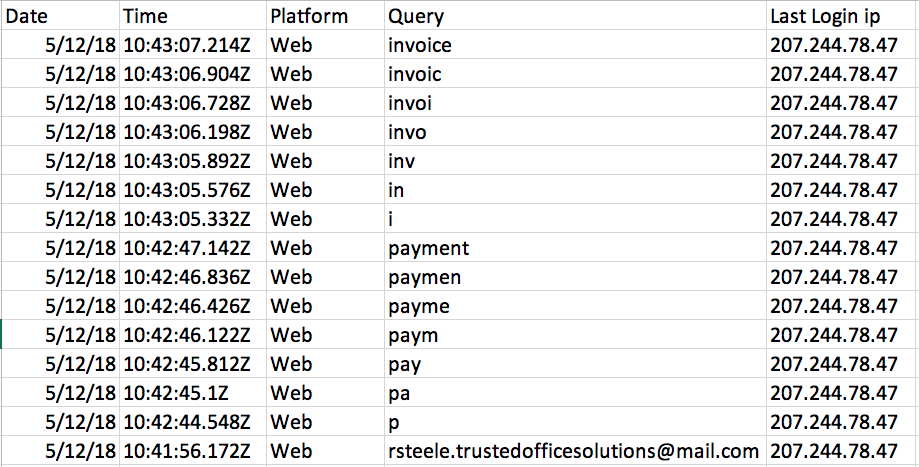
Detailed logs of Office 365 Outlook, extracted by the program Magic-Unicorn-Tool : the attacker is looking for an invoice (payment invoice). The first letter of the search query is entered at 10: 42: 44.548, the last one at 10: 43: 07.214. Information about the activity is stored in the logs for six months.
It has been rumored for a long time that Office 365 has a built-in secret tool for recording user activity. In June 2018, these rumors were fully confirmed. It all started with a video published by Anonymous , and then experts from CrowdSrtike posted a detailed report .
Microsoft introduced the Activities API into the email client not for any malicious purposes, but for digital forensic tasks, that is, investigating corporate mail burglary incidents and other data leaks. For this purpose, a detailed log of activity is conducted for six months even if the user has disabled logging .
The epidemic of hacking email accounts
Hacking corporate email accounts worldwide has become so widespread that some experts call it an epidemic . Criminals gain access to spreadsheets with social security numbers, detailed information on financial invoices and trade secrets. They are looking for information about bank transfers and stealing money, taking advantage of the lack of a digital signature on documents . Various types of fraud through the compromise of business mail are described in the CrowdStrike brochure .
For example, in early June, the FBI conducted an international operation and detained 74 people in several countries that were engaged in this business.
When the fact of hacking becomes known, it is important to understand: to what data the hacker got access, what he saw and what information he copied. Has confidential data leaked? Investigation of incidents is hampered by the fact that journaling in Office 365 is turned off by default. In the absence of any real information, the company is legally obliged to publicly announce a data leak with all the ensuing consequences - reputational costs, fines, etc.
But now it has become known that the Office 365 has a Activities API with detailed logging, and many such scandals could have been avoided if companies knew about this API. Perhaps, access to these secret logs was obtained only by certain privileged clients. There is informationthat some companies that specialize in digital forensics knew about the secret Office 365 audit tool last year, or even earlier. Someone considered their statements as marketing bravado, but this turned out to be true. Surprisingly, the Activities API does exist, and Microsoft really hid the presence of such an important and useful tool, called in professional circles “Magic Unicorn” (Magic Unicorn), hence the name of the program for self-analysis of logs, which is mentioned below. The attacker scans the messages containing the invoice and the form W-9. Detailed logs extracted by the program Magic-Unicorn-Tool

CrowdStrike Investigation
CrowdStrike described in detail how Office 365 journaling works for all users by default. The function consists of a web API that retrieves Office 365 Outlook activity through Exchange Web Services (EWS). Access to the API is open to anyone who knows the endpoint and the specific HTTP header.
Undocumented Activities APIs are a subset of all three versions of Outlook REST API (1.0, 2.0 and beta). As with the other subsets, the call to the API must be authenticated using OAuth 2.0 or basic authentication.
The end point is as follows:
https://outlook.office.com/api/v2.0/{user_context}/ActivitiesAll requests are sent as HTTP GET packets, which must necessarily include the following HTTP header:
Prefer: exchange.behavior="ActivityAccess"Requests without this header will be returned
HTTP 400 Bad Request. The title is also required
Authorization:Authorization: Bearer <access token>Requests without this header will return a response
HTTP 403 Unauthorized. For testing purposes, an OAuth 2.0 access token can be generated in the Oauth sandbox . It is valid for 60 minutes.
The simplest call to the API is the request for the ten most recent activities.
GET https://outlook.office.com/api/v2.0/me/ActivitiesAn example of the response from the API in JSON format shows the standard properties of activities:
{
"value": [
{
"Id":"WOGVSAiPKrfJ4apAPcBksT2en7whzDz4NIbUs3==",
"ActivityCreationTime":"2010-04-01T12:34:56.789Z",
"ActivityIdType":"ReadingPaneDisplayStart",
"AppIdType":"Outlook",
"ClientVersion":"15.00.0000.000",
"ClientSessionId":"679126f3-02de-3513-e336-0eac1294b120",
"ActivityItemId":"NjKG5m6OmaCjGKq6WlbjIzvp94czUDg30qGopD==",
"TimeStamp":"2010-04-01T12:34:56.789Z",
"TenantId":"679126f3-02de-3513-e336-0eac1294b120",
}
]
}Through the API, you can request activities not only for yourself, but also for other users, if permission is obtained via Shared Mailbox or Application Permission:
GET https://outlook.office.com/api/v2.0/Users('victim@contoso.com')/ActivitiesThe Activities API supports several query parameters:
$orderby: Sort results by specified expression$filter: filter results by date and / or type of activity$select: select properties to return$top: maximum number of activities returned$skip: the number of skipped activities in the results
At the moment, CrowdStrike has identified 30 types of activities, but in reality there may be more. Here are the most useful:
Delete: delete letterForward: letter redirectionLinkClicked: click on the link in the letterMarkAsRead: message marked as readMarkAsUnread: message marked as unreadMessageDelivered: the letter is delivered to the mailboxMessageSent: email sent from mailboxMove: letter movedOpenedAnAttachment: open applicationReadingPaneDisplayEnd: cancel selection for a letter in the view paneReadingPaneDisplayStart: select selection for writing in the view paneReply: response to the letterSearchResult: generating search resultsServerLogon: authorization event
There are other interesting types of activities that are useful in the investigation of incidents:
SenderSmtpAddress, Recipients, Subject, SentTime, InternetMessageId, ClientIP, UserAgentand others. CrowdStrike specialists have published a Python module that extracts information about the Office 365 Outlook Activities API and writes the data to a CSV file.
Magic-Unicorn-Tool
The Magic-Unicorn-Tool program parses the Activities API logs acquired by the aforementioned Python module. At the moment, it is able to parse and display the following information:
- Search queries in the mailbox, while viewing messages and / or authorized sessions.
- Authorization events (Logon and ServerLogon), date, time, IP address and browser type.
- All mail activity delivered and marked as read letters.
- Search events recorded with session ID with reference to the last authorization event.
- Reading the panel.
- View attachments.
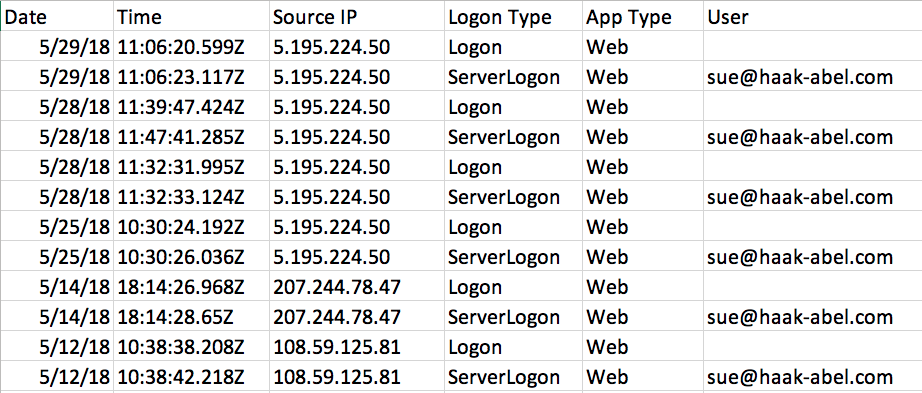
Logging into your account from different IP-addresses
Magic-Unicorn-Tool is distributed without a code signature , but with open source.
Implementing tools like the Activities API without the knowledge of users raises a number of practical and ethical issues for the entire digital forensic industry. By default, logging is disabled on Office 365 accounts. It is not included in the standard ProPlus and E1 plans. For the audit of company accounts, they are forced to pay extra money, and due to the lack of logs (as they thought), many companies suffered losses. At the same time, the details of the Activities API logs are much higher than those of documented logging methods, such as Unified Audit Log .
Digital Forensics Specialists from LMG Securitycall for the adoption of standards for logging activity and impose it as a mandatory burden on cloud providers, as now the mandatory load is the fire alarm system in data centers.
The adoption of standards is required so that providers not only keep logs, but also provide them in a standard form for clients and audit companies, rather than keeping them secret for selected clients, as part of a more expensive tariff plan or as a separate paid service.
GMO GlobalSign Russia PROMOTION for Habr subscribers

You can get additional information by contacting GlobalSign manager by phone: +7 (499) 678 2210, or fill out the form on the website, specifying the promo code CS002HBFR.
