CSRF vulnerabilities on an example of HabraHabr
There is no vulnerability anymore - it was fixed long before the appearance of this topic.
Very often, many web developers forget about the existence of this hacking method, and some do not even know about it.
Unfortunately, such vulnerabilities are found even in such large systems as HabraHabr.
It all started with the fact that my karma was quickly leaked to -16 units due to a completely normal, in my opinion, comment. I felt offended, because I registered on this resource to write topics interesting to everyone, and now I can not do this.

I leafed through the tape, looking through the topics, and thought about how good it is for their authors, who quickly gain rating and glow in the rays of glory. Without any hope, I poked at the arrow to put a plus sign on the topic. As it’s not hard to guess, I got an error like “Your karma is not enough to vote.”
I immediately noticed that the page is not updating, which means that AJAX is used.
I immediately remembered the little-known CSRF, or as they are also called XSRF vulnerabilities.
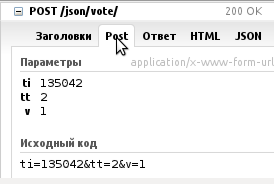
I began to look at FireBug where and how requests are sent. First of all, it was embarrassing that only the grade (for or against), the type of record (topic) and id were transmitted. No additional fields like hash or token were passed.
Perhaps the impatient reader has already decided that I found an elementary, obvious to every hole? No matter how! All my attempts to fake a request led to the same thing:

At first I decided that I was mistaken somewhere. But no, I sent a request to the right address and passed all the parameters in the right way. But when the HabraHabr script did it, it got a response status of 200, and I got 404.
I began to carefully check the HTTP headers, and then it caught my eye:
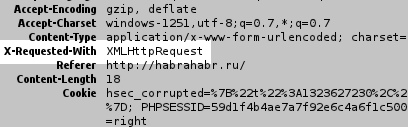
What is this strange header that was not in my request?
A little google, I found out that this header is passed by default when AJAX'e, and when you request from the form, by itself, is not passed.
I could not make an AJAX request, because Habr is on other domain and the browser just would not let me in there. And then I remembered about the FlashPlayer that I abandoned a long time ago. Quickly googling, I cried out cheers !
Yes, comrades, this browser add-on so beloved by many can send any requests to any domain if ... If there is a correct crossdomain.xml file in the root of this domain .
Do you believe in fate? Me not. But I was just shocked when I found this treasured file in the root of HabrHabr, which allowed me to send requests to the 80th port from any domain !
I chose ActionScript version 2, firstly, because I knew it better, and secondly, because you can also bring users of the old FlashPlayer with you to the ship (starting from version 7).
Everything, now it's up to the small. If you have your own site, then without hesitation fill the code there and put it in an iframe.
If you don’t have a website, then thinking about an agreement with Profit, we agree with the owner of a large VK application and fill in the code for it. Coverage of 50% of users is guaranteed.
That's it, now any user, if he did not vote for your topic earlier, puts you + without knowing it.
In addition, you can vote not only for topics, but also for comments, questions and Karma!
Breaking sites is not very good. For this they can do ata-ta-ta in the back seat.
In the case of this vulnerability, I quickly wrote a letter to the support service and the vulnerability was closed (fixing crossdomain.xml).
Very often, many web developers forget about the existence of this hacking method, and some do not even know about it.
Unfortunately, such vulnerabilities are found even in such large systems as HabraHabr.

How it all started
It all started with the fact that my karma was quickly leaked to -16 units due to a completely normal, in my opinion, comment. I felt offended, because I registered on this resource to write topics interesting to everyone, and now I can not do this.

I leafed through the tape, looking through the topics, and thought about how good it is for their authors, who quickly gain rating and glow in the rays of glory. Without any hope, I poked at the arrow to put a plus sign on the topic. As it’s not hard to guess, I got an error like “Your karma is not enough to vote.”
Looking for vulnerabilities
I immediately noticed that the page is not updating, which means that AJAX is used.
I immediately remembered the little-known CSRF, or as they are also called XSRF vulnerabilities.
I began to look at FireBug where and how requests are sent. First of all, it was embarrassing that only the grade (for or against), the type of record (topic) and id were transmitted. No additional fields like hash or token were passed.
Not so simple
Perhaps the impatient reader has already decided that I found an elementary, obvious to every hole? No matter how! All my attempts to fake a request led to the same thing:

At first I decided that I was mistaken somewhere. But no, I sent a request to the right address and passed all the parameters in the right way. But when the HabraHabr script did it, it got a response status of 200, and I got 404.
I began to carefully check the HTTP headers, and then it caught my eye:

What is this strange header that was not in my request?
A little google, I found out that this header is passed by default when AJAX'e, and when you request from the form, by itself, is not passed.
I could not make an AJAX request, because Habr is on other domain and the browser just would not let me in there. And then I remembered about the FlashPlayer that I abandoned a long time ago. Quickly googling, I cried out cheers !
Yes, comrades, this browser add-on so beloved by many can send any requests to any domain if ... If there is a correct crossdomain.xml file in the root of this domain .
Do you believe in fate? Me not. But I was just shocked when I found this treasured file in the root of HabrHabr, which allowed me to send requests to the 80th port from any domain !
We write an exploit
I chose ActionScript version 2, firstly, because I knew it better, and secondly, because you can also bring users of the old FlashPlayer with you to the ship (starting from version 7).
var req:LoadVars = new LoadVars();
req.addRequestHeader("X-Requested-With","XMLHttpRequest");
req.addRequestHeader("Referer","http://habrahabr.ru/"); // на всякий случай
req.decode("ti=666&tt=2&v=1"); // вместо 666 id вашего топика
req.send("http://habrahabr.ru/json/vote/", "_blank", "POST");
What to do with an exploit?
Everything, now it's up to the small. If you have your own site, then without hesitation fill the code there and put it in an iframe.
If you don’t have a website, then thinking about an agreement with Profit, we agree with the owner of a large VK application and fill in the code for it. Coverage of 50% of users is guaranteed.
That's it, now any user, if he did not vote for your topic earlier, puts you + without knowing it.
In addition, you can vote not only for topics, but also for comments, questions and Karma!
As a keepsake
Breaking sites is not very good. For this they can do ata-ta-ta in the back seat.
In the case of this vulnerability, I quickly wrote a letter to the support service and the vulnerability was closed (fixing crossdomain.xml).
