Brutforsim card number, CVV2 and validity period using the Master Bank website
 A little more than a year ago, I already wrote about the vulnerability of Master Bank and VKontakte. After such a time, no one has closed the vulnerability, and the kibizoidus comment seems to be all the more fun .
Well, and we continue. Today we will consider a much more serious vulnerability - the ability to sort out the details of cards using the payment page of the same Master Bank.
Like last time, for convenience, we go to Contact and select payment for advertising with plastic cards:
Next, enter the details of the attacked credit card:
Run, for example, firebug in firefox or the developer tools in chrome and intercept the POST request.
For convenience, we redo it into a URL of the following form: https://web3ds.masterbank.ru/cgi-bin/
A little more than a year ago, I already wrote about the vulnerability of Master Bank and VKontakte. After such a time, no one has closed the vulnerability, and the kibizoidus comment seems to be all the more fun .
Well, and we continue. Today we will consider a much more serious vulnerability - the ability to sort out the details of cards using the payment page of the same Master Bank.
Like last time, for convenience, we go to Contact and select payment for advertising with plastic cards:
Next, enter the details of the attacked credit card:
Run, for example, firebug in firefox or the developer tools in chrome and intercept the POST request.
For convenience, we redo it into a URL of the following form: https://web3ds.masterbank.ru/cgi-bin/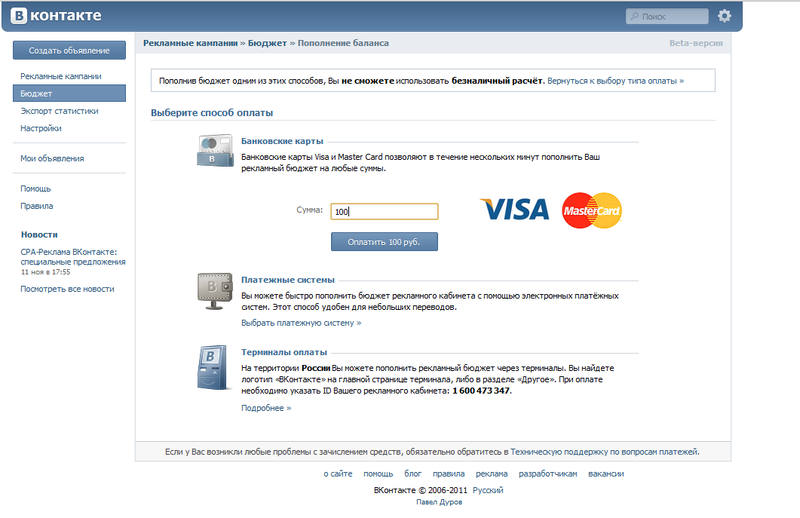

cgi_link? CARD = 4 *************** & EXP = 06 & EXP_YEAR = 12 & CVC2 = 111 & CVC2_RC = 1 & NAME = - & AMOUNT = 100.00 & CURRENCY = RUB & ORDER = 2062445 & DESC = VK% 20RUB & MERCH_NAME =% C2% E2% %2
% % ED% F2% E0% EA % F2% E5 & TERMINAL = 71837464 & TRTYPE = 0 & COUNTRY = & MERCH_GMT = & TIMESTAMP =
20111116002415 & NONCE = & BACKREF = vk & P_SIGN = & FORM_ID = 0BB4A02A05B3580A & MERCH_URL =
http = // vkontakte.ru/payments.php?act=finished_ads&union_id=1600473347&result=unknown&source = masterbank
& expand_type = card & order_id = 2062445 & TIMESHOW = 08657 & PAGE = default-1251 & SEND_BUTTON.x = 43 & SEND_BUTTON.y = 7 & SEND_BUTTON =% CE% F2% EF% F0% E0% E2% E8% F2% FC
Now you can write a simple script using curl and directly search through card numbers, cvv2 and expiration dates (parameters CARD, EXP / EXP_YEAR, CVC2, respectively) for a small amount. At the same time, Master Bank does not block attempts. As the experiment shows, such a link "lives" for several hours, and only then it expires
PS by tradition, Master Bank and WAY4, the alleged vendor of this payment gateway, were notified by e-mail, but none of them reacted
