Social botnets
In the past few years, articles have regularly appeared on the role of social Internet services in the so-called revolutions, which flare up and down in different parts of the third world (one of them is especially notable, which talks about the use of technologies such as Tor, OpenGSM, mesh networking [1]) . As a rule, things did not go further than stating the fact of their use. But in this article, with the help of Wikipedia and common sense, we will try to dig a little deeper and see the amazing similarity between the DDoS attack and the “twitter revolution”, as well as ways to counter them.
Since this article is intended for a wide range of readers, definitions will be given that explain one or another term. Text that is taken from Wikipedia will be in italics.
So, what is a DDoS attack : - an attack performed from a large number of computers on a computer system in order to bring it to failure, that is, the creation of such conditions under which legitimate (legitimate) users of the system cannot gain access to the resources provided by the system, or this access is difficult. The failure of the "enemy" system can be both an end in itself and one of the steps to mastering the system. Typically, attacks involve from several thousand to hundreds of thousands of infected machines.
We pay special attention to such a variety of DDoS attacks as Flood:
Flood(English flood) - an attack associated with a large number of usually meaningless or incorrectly formatted requests to a computer system or network equipment, with the aim of or leading to a failure of the system due to exhaustion of system resources.
But in order to organize such an attack, you first need to create a botnet.
Botnet(eng. botnet from robot and network) is a computer network consisting of a number of devices with bots running - stand-alone software. Most often, a bot as part of a botnet is a program that covertly installs on the victim’s computer and allows an attacker to perform certain actions using the resources of an infected computer. Upon receipt of the command from the "owner" of the botnet, begins to execute the command. In some cases, the executable code is loaded at the command (thus, it is possible to “update” the program).
Executable code is a system of instructions, each of which describes an elementary action.
That is, to create a botnet, you must first infect many computers with a virus.
Computer virus- A variety of computer programs, the distinguishing feature of which is the ability to reproduce (self-replication). In addition to this, viruses can, without the knowledge of the user, perform other arbitrary actions, including those that harm the user and / or computer.
Infection with a computer virus (written to create a botnet) occurs mainly in two ways: either through spam with the virus (under the guise of useful content) or when visiting sites on which the virus is located.
Now consider a simplified DDoS attack scheme.
Step one: An attacker (hereinafter referred to as the Center) creates or purchases a VPN server.
VPN(Engl. Virtual Private Network - virtual private network) - a generic name for technologies that allow one or more network connections over another network. Used for combining into a single secure network several distributed branches of the same organization that exchange data via open communication channels.
Usually, a VPN server, on the one hand, is under the "legal" control of the Center, and on the other, just for this reason it is difficult or impossible to identify its owner.
Step Two: The Center connects to the proxy server via VPN. The purpose of using this chain is to hide the traces of the Center’s involvement in the botnet’s actions.
Proxy server(from the English proxy - “representative, authorized”) - a service in computer networks that allows customers to perform indirect requests to other network services. The proxy server may hide information about the source of the request or the user. In this case, the target server sees only information about the proxy server, but does not have the ability to determine the true source of the request. There are also distorting proxies that transmit false information about the true user to the target server.
Step Three: The Center through the VPN chain - Proxy gives the botnet a command to launch an attack on the selected victim.
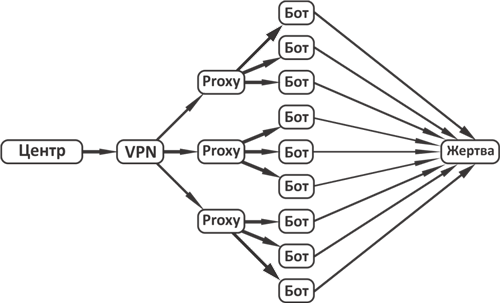
If you have not guessed yet, and here twitter (and other social networks) - look at the diagram above and use other terms.
Center - “Citadel of Democracy”;
VPN- public and human rights organizations, rating agencies, WikiLeaks, etc.
Proxy - the so-called opinion leaders (drugoi, Navalny, Latynina, etc. for every taste and area of interest). Proxy is used in order not to compromise a more expensive VPN and is valuable in that it allows the Center to act as a resident of the country;
A bot is a person infected with a mental virus. In the terminology of tweeter - follower (follower). You can make a proxy from a bot. (It is enough to recall the story with the blogger Sukhumi).
Mental virus, aka Mem- in memetics, a unit of cultural information distributed from one person to another through imitation, learning, etc. Like genes, memes are replicators, that is, objects that copy themselves. For memes, survival depends on the presence of at least one medium, and reproduction depends on the presence of that medium that is trying to spread the essence of the meme. Memes can be modified (combined or separated) to form new memes. A recent example is the “Palace of Putin”.
Infection with the mental virus occurs in the same way as a computer:
Visits to infected sites (Echo of Moscow, kavkazcenter, kasparov.ru, etc.);
The spread of the virus under the guise of useful content (internships, training abroad, British Council programs, etc.). As a rule, this method is used to create not simple bots, but opinion leaders - Proxy.
The 140-character twitter message length limit is due to the SMS message size limit. If you allow the use of longer messages which are essentially commands (the executable code mentioned above), then part of the message will be lost, and this will lead to a decrease in coordination and network efficiency.
Orientation specifically to mobile phones suggests that the service was originally intended for developing countries, where the phone is much more common than the computer and the Internet, and mobile companies are often foreign companies that are easily controlled from the outside. At the same time, since 2005, the struggle against the “digital divide” has been actively carried out, which consists in the supply of cheap computers to the Middle East, Tunisia, Libya. [2] [3] [4] [5] The program is run by Nicholas Negroponte who turned out to be John Negroponte’s brother who is accused of participating in the creation of the “316th Battalion” together with the CIA, whose members abducted, tortured and killed opposition and the objectionable US figures. Wife - Diana Negroponte, a member of the US government-sponsored Freedom House.(VPN) The
economic return on social botnets is colossal and cannot be compared to the funds invested in them. Tens of millions of dollars were invested in the same twitter even without a clear monetization model (legal), but after a few years we see profit - the bank accounts of Egypt, Tunisia, Libya are “frozen” ($ 160 billion) . [6]
Now about the methods of protection against social DDoS attacks. They are the same as when protecting against a computer:
Prevention. Prevention of the reasons prompting certain individuals to organize DoS attacks. Very often attacks are the result of personal resentment, political, religious disagreements, provocative behavior of the victim, etc.
Filtration.Blocking traffic coming from attacking machines. The effectiveness of these methods decreases as you approach the target of the attack and increases as you approach its source.
Elimination of vulnerabilities. It does not work against flood attacks, for which the “vulnerability” is the finiteness of certain resources.
Build resources.
Dispersal. Building distributed and duplicated systems that will not stop serving users, even if some of their elements become unavailable due to an attack.
Evasion. Moving the immediate target of the attack away from other resources, which are often also affected along with the immediate target.
Active response.Impact on the sources, the organizer or the center of the attack control, both technical and organizational-legal nature.
Implementation of equipment to repel DoS attacks. (For example, Russian SORM).
Acquisition of a service for protection against DoS attacks. (Military-political unions).
[1] www.zavtra.ru/cgi/veil/data/zavtra/11/909/print51.html
[2] www.securitylab.ru/news/242122.php?R1=RSS&R2=allnews
[3] hard.compulenta .ru / 337824 /? r1 = yandex & r2 = news & country = Russia
[4] news.ferra.ru/hard/2006/10/16/62912
[5] lenta.ru/news/2010/04/29/olpc
[6] news2.ru/story/312155
Since this article is intended for a wide range of readers, definitions will be given that explain one or another term. Text that is taken from Wikipedia will be in italics.
So, what is a DDoS attack : - an attack performed from a large number of computers on a computer system in order to bring it to failure, that is, the creation of such conditions under which legitimate (legitimate) users of the system cannot gain access to the resources provided by the system, or this access is difficult. The failure of the "enemy" system can be both an end in itself and one of the steps to mastering the system. Typically, attacks involve from several thousand to hundreds of thousands of infected machines.
We pay special attention to such a variety of DDoS attacks as Flood:
Flood(English flood) - an attack associated with a large number of usually meaningless or incorrectly formatted requests to a computer system or network equipment, with the aim of or leading to a failure of the system due to exhaustion of system resources.
But in order to organize such an attack, you first need to create a botnet.
Botnet(eng. botnet from robot and network) is a computer network consisting of a number of devices with bots running - stand-alone software. Most often, a bot as part of a botnet is a program that covertly installs on the victim’s computer and allows an attacker to perform certain actions using the resources of an infected computer. Upon receipt of the command from the "owner" of the botnet, begins to execute the command. In some cases, the executable code is loaded at the command (thus, it is possible to “update” the program).
Executable code is a system of instructions, each of which describes an elementary action.
That is, to create a botnet, you must first infect many computers with a virus.
Computer virus- A variety of computer programs, the distinguishing feature of which is the ability to reproduce (self-replication). In addition to this, viruses can, without the knowledge of the user, perform other arbitrary actions, including those that harm the user and / or computer.
Infection with a computer virus (written to create a botnet) occurs mainly in two ways: either through spam with the virus (under the guise of useful content) or when visiting sites on which the virus is located.
Now consider a simplified DDoS attack scheme.
Step one: An attacker (hereinafter referred to as the Center) creates or purchases a VPN server.
VPN(Engl. Virtual Private Network - virtual private network) - a generic name for technologies that allow one or more network connections over another network. Used for combining into a single secure network several distributed branches of the same organization that exchange data via open communication channels.
Usually, a VPN server, on the one hand, is under the "legal" control of the Center, and on the other, just for this reason it is difficult or impossible to identify its owner.
Step Two: The Center connects to the proxy server via VPN. The purpose of using this chain is to hide the traces of the Center’s involvement in the botnet’s actions.
Proxy server(from the English proxy - “representative, authorized”) - a service in computer networks that allows customers to perform indirect requests to other network services. The proxy server may hide information about the source of the request or the user. In this case, the target server sees only information about the proxy server, but does not have the ability to determine the true source of the request. There are also distorting proxies that transmit false information about the true user to the target server.
Step Three: The Center through the VPN chain - Proxy gives the botnet a command to launch an attack on the selected victim.

If you have not guessed yet, and here twitter (and other social networks) - look at the diagram above and use other terms.
Center - “Citadel of Democracy”;
VPN- public and human rights organizations, rating agencies, WikiLeaks, etc.
Proxy - the so-called opinion leaders (drugoi, Navalny, Latynina, etc. for every taste and area of interest). Proxy is used in order not to compromise a more expensive VPN and is valuable in that it allows the Center to act as a resident of the country;
A bot is a person infected with a mental virus. In the terminology of tweeter - follower (follower). You can make a proxy from a bot. (It is enough to recall the story with the blogger Sukhumi).
Mental virus, aka Mem- in memetics, a unit of cultural information distributed from one person to another through imitation, learning, etc. Like genes, memes are replicators, that is, objects that copy themselves. For memes, survival depends on the presence of at least one medium, and reproduction depends on the presence of that medium that is trying to spread the essence of the meme. Memes can be modified (combined or separated) to form new memes. A recent example is the “Palace of Putin”.
Infection with the mental virus occurs in the same way as a computer:
Visits to infected sites (Echo of Moscow, kavkazcenter, kasparov.ru, etc.);
The spread of the virus under the guise of useful content (internships, training abroad, British Council programs, etc.). As a rule, this method is used to create not simple bots, but opinion leaders - Proxy.
The 140-character twitter message length limit is due to the SMS message size limit. If you allow the use of longer messages which are essentially commands (the executable code mentioned above), then part of the message will be lost, and this will lead to a decrease in coordination and network efficiency.
Orientation specifically to mobile phones suggests that the service was originally intended for developing countries, where the phone is much more common than the computer and the Internet, and mobile companies are often foreign companies that are easily controlled from the outside. At the same time, since 2005, the struggle against the “digital divide” has been actively carried out, which consists in the supply of cheap computers to the Middle East, Tunisia, Libya. [2] [3] [4] [5] The program is run by Nicholas Negroponte who turned out to be John Negroponte’s brother who is accused of participating in the creation of the “316th Battalion” together with the CIA, whose members abducted, tortured and killed opposition and the objectionable US figures. Wife - Diana Negroponte, a member of the US government-sponsored Freedom House.(VPN) The
economic return on social botnets is colossal and cannot be compared to the funds invested in them. Tens of millions of dollars were invested in the same twitter even without a clear monetization model (legal), but after a few years we see profit - the bank accounts of Egypt, Tunisia, Libya are “frozen” ($ 160 billion) . [6]
Now about the methods of protection against social DDoS attacks. They are the same as when protecting against a computer:
Prevention. Prevention of the reasons prompting certain individuals to organize DoS attacks. Very often attacks are the result of personal resentment, political, religious disagreements, provocative behavior of the victim, etc.
Filtration.Blocking traffic coming from attacking machines. The effectiveness of these methods decreases as you approach the target of the attack and increases as you approach its source.
Elimination of vulnerabilities. It does not work against flood attacks, for which the “vulnerability” is the finiteness of certain resources.
Build resources.
Dispersal. Building distributed and duplicated systems that will not stop serving users, even if some of their elements become unavailable due to an attack.
Evasion. Moving the immediate target of the attack away from other resources, which are often also affected along with the immediate target.
Active response.Impact on the sources, the organizer or the center of the attack control, both technical and organizational-legal nature.
Implementation of equipment to repel DoS attacks. (For example, Russian SORM).
Acquisition of a service for protection against DoS attacks. (Military-political unions).
[1] www.zavtra.ru/cgi/veil/data/zavtra/11/909/print51.html
[2] www.securitylab.ru/news/242122.php?R1=RSS&R2=allnews
[3] hard.compulenta .ru / 337824 /? r1 = yandex & r2 = news & country = Russia
[4] news.ferra.ru/hard/2006/10/16/62912
[5] lenta.ru/news/2010/04/29/olpc
[6] news2.ru/story/312155
