TDL4 rootkit evolution or field reports of recent months
We have been closely monitoring TDL4 for a long time, as well as botnets based on this rootkit family. But lately it has been especially interesting to watch the release of corrections from Microsoft to block the methods of loading unsigned drivers for x64 systems used to install Win64 / Olmarik.
Let's start from afar, so on April day X, in addition to all the rest, the KB2506014 patch was released , the task of which was to make several changes to the winloader.exe module for x64 versions of the OS and thus prevent the downloading of unsigned drivers. Prior to installing the patch, BCD (Boot Configuration Data) has three different boot options:
BcdLibraryBoolean_DisableIntegrityCheck– принудительное отключение проверки (чаще всего используется для отладочных целей);
BcdOSLoaderBoolean_WinPEMode – отключение в режиме установки или восстановления ОС
BcdLibraryBoolean_AllowPrereleaseSignatures – разрешить загружать модули имеющие тестовую цифровую подпись
После установки патча остаются только две опции — BcdLibraryBoolean_DisableIntegrityCheck и BcdLibraryBoolean_AllowPrereleaseSignatures, а BcdOSLoaderBoolean_WinPEMode больше не используется в конфигурации политик проверки целостности загружаемых драйверов. В winloader.exe есть специальная функция BlImgQueryCodeIntegrityBootOptions, которая возвращает значение определяющее политику проверок.
The following figure shows the BlImgQueryCodeIntegrityBootOptions procedure after the patch:

As we can see, the BcdOSLoaderBoolean_WinPEMode option is no longer used, and the loading method used in TDL4 then stopped working (for more details on its work, see the research report “The Evolution of TDL: Conquering x64 " ).
However, a relatively new version of the TDL4 bootkit has recently been released, which bypasses this fix too - the ldr16 component was changed in it, which allowed TDL4 to regain the ability to infect x64-bit systems. In addition, malware protection against detection and deletion has been enhanced by improving the low-level kernel-mode event handlers related to the storage device miniport driver object.
After the latest fix from Microsoft, it became impossible to bypass the policy of verifying digital code signing in WinPE mode. The creators of TDL4 had to change the tactics of infection of 64-bit OS. The idea remains the same: change the ld32 or ldr64 components in the kdcom.dll library depending on the bit depth of the infected OS. Instead of switching to WinPE mode, the new version of TDL4 corrects the procedureI_CheckImageHashInCatalog . Using this procedure, the integrity of the modules loaded by winload.exe is checked .
Under normal conditions, when the I_CheckImageHashInCatalog procedure fails to verify the integrity of the module, it returns 0xC0000428 (STATUS_INVALID_IMAGE_HASH) , which prevents the system from booting. The TDL4 bootkit makes changes that result in 0x0000C428 being returned instead of 0xC0000428 . The new value is not an error code (in kernel mode, the most significant bit of error codes is usually set to 1). Thus, the OS does not detect a replacement for the kdcom.dll library.
The following illustration shows the code that fixes the ldr16 component on the fly in winload.exe:

However, this new mechanism, as it turned out, does not work quite stably. On some systems, the OS can detect changes and start a startup recovery, as shown in the following screenshot.
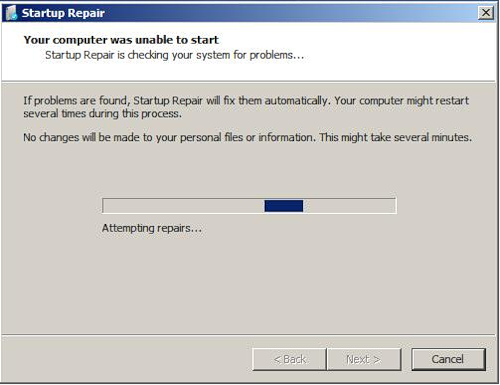
After a forced reboot, the system becomes completely unbootable.
The second enhancement to the new TDL4 version concerned low-level kernel-mode event handlers related to the storage device miniport driver object. Previous versions of the malware captured the driver object related to the lowest-level device object in the storage device stack, as shown in the following diagram:
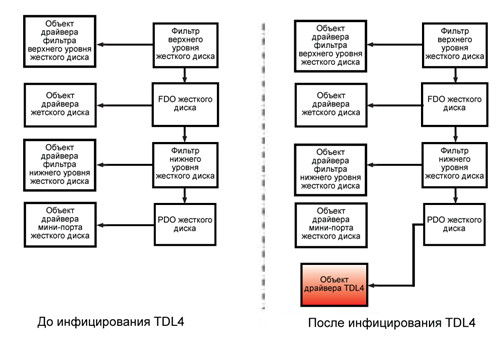
In this case, you can quickly access the object of the miniport device (Hard drive PDO, PDO object of the hard disk) and then go through the list of adjacent device objects to get a pointer to the "real" object of the miniport driver of the hard disk. In the new version of TDL4, the object of the miniport driver of the hard disk is masked in a more sophisticated way:

In this case, the device object of the lowest level in the stack of storage devices is no longer the PDO object corresponding to the hard disk. After such a change, it becomes much more difficult to detect and remove this malware. ESET antivirus products detect the latest TDL4 dropper as Win32 / Olmarik.AMN, and all treatment procedures work correctly.
TDL3 already met in previous generation a similar case when updating from MS dropped infected systems into a blue screen.
Let's start from afar, so on April day X, in addition to all the rest, the KB2506014 patch was released , the task of which was to make several changes to the winloader.exe module for x64 versions of the OS and thus prevent the downloading of unsigned drivers. Prior to installing the patch, BCD (Boot Configuration Data) has three different boot options:
BcdLibraryBoolean_DisableIntegrityCheck– принудительное отключение проверки (чаще всего используется для отладочных целей);
BcdOSLoaderBoolean_WinPEMode – отключение в режиме установки или восстановления ОС
BcdLibraryBoolean_AllowPrereleaseSignatures – разрешить загружать модули имеющие тестовую цифровую подпись
После установки патча остаются только две опции — BcdLibraryBoolean_DisableIntegrityCheck и BcdLibraryBoolean_AllowPrereleaseSignatures, а BcdOSLoaderBoolean_WinPEMode больше не используется в конфигурации политик проверки целостности загружаемых драйверов. В winloader.exe есть специальная функция BlImgQueryCodeIntegrityBootOptions, которая возвращает значение определяющее политику проверок.
The following figure shows the BlImgQueryCodeIntegrityBootOptions procedure after the patch:

As we can see, the BcdOSLoaderBoolean_WinPEMode option is no longer used, and the loading method used in TDL4 then stopped working (for more details on its work, see the research report “The Evolution of TDL: Conquering x64 " ).
However, a relatively new version of the TDL4 bootkit has recently been released, which bypasses this fix too - the ldr16 component was changed in it, which allowed TDL4 to regain the ability to infect x64-bit systems. In addition, malware protection against detection and deletion has been enhanced by improving the low-level kernel-mode event handlers related to the storage device miniport driver object.
After the latest fix from Microsoft, it became impossible to bypass the policy of verifying digital code signing in WinPE mode. The creators of TDL4 had to change the tactics of infection of 64-bit OS. The idea remains the same: change the ld32 or ldr64 components in the kdcom.dll library depending on the bit depth of the infected OS. Instead of switching to WinPE mode, the new version of TDL4 corrects the procedureI_CheckImageHashInCatalog . Using this procedure, the integrity of the modules loaded by winload.exe is checked .
Under normal conditions, when the I_CheckImageHashInCatalog procedure fails to verify the integrity of the module, it returns 0xC0000428 (STATUS_INVALID_IMAGE_HASH) , which prevents the system from booting. The TDL4 bootkit makes changes that result in 0x0000C428 being returned instead of 0xC0000428 . The new value is not an error code (in kernel mode, the most significant bit of error codes is usually set to 1). Thus, the OS does not detect a replacement for the kdcom.dll library.
The following illustration shows the code that fixes the ldr16 component on the fly in winload.exe:

However, this new mechanism, as it turned out, does not work quite stably. On some systems, the OS can detect changes and start a startup recovery, as shown in the following screenshot.

After a forced reboot, the system becomes completely unbootable.
The second enhancement to the new TDL4 version concerned low-level kernel-mode event handlers related to the storage device miniport driver object. Previous versions of the malware captured the driver object related to the lowest-level device object in the storage device stack, as shown in the following diagram:

In this case, you can quickly access the object of the miniport device (Hard drive PDO, PDO object of the hard disk) and then go through the list of adjacent device objects to get a pointer to the "real" object of the miniport driver of the hard disk. In the new version of TDL4, the object of the miniport driver of the hard disk is masked in a more sophisticated way:

In this case, the device object of the lowest level in the stack of storage devices is no longer the PDO object corresponding to the hard disk. After such a change, it becomes much more difficult to detect and remove this malware. ESET antivirus products detect the latest TDL4 dropper as Win32 / Olmarik.AMN, and all treatment procedures work correctly.
TDL3 already met in previous generation a similar case when updating from MS dropped infected systems into a blue screen.
