GreenSQL: SQL Server Injection Protection
Sometimes it becomes necessary to use client-server software that implements the necessary functionality, but is extremely vulnerable to SQL injection. These are mainly websites, network applications and other services that are accessible to a wide range of users, including cybercriminals. For various reasons, it is not always possible to prevent SQL injections at the application level - the source code may be closed, or, in the case of open source, not enough knowledge to make changes to it, or this operation is expensive.
In this case, GreenSQL will help ensure application security - a firewall or proxy for SQL servers. The GreenSQL service is located between your application and the SQL server, accepts sql queries from the application and, depending on its reliability, either redirects them to the target SQL server or rejects them.

GreenSQL supports Microsoft SQL 2000/2005/2008, MySQL 4.x / 5.x, PostgreSQL 7.x / 8.x and is cross-platform. Among the officially supported platforms are Microsoft Windows Server 2003/2008, Ubuntu, CentOS. 32-bit and 64-bit systems are supported.
As for the cost, there are several modifications of the program - free Express, Lite and Pro with a monthly payment. The main difference between paid and free versions, if you omit technical support and automatic updates, is the ability to modify requests on the fly and work with secure SSL connections.
Each version of GreenSQL supports several modes of operation.
Risk Based - IPS / IDS implements a basic algorithm for identifying potentially dangerous SQL queries. Those. GreenSQL performs semantic analysis of the query and, by indirect indications, determines the degree of its reliability. Calculation of the degree of danger is carried out taking into account the following parameters:
Required blocked requests can be added to the allowed list (whitelist).
Database Firewall is an active protection mode that allows only requests from the whitelist list to be skipped.
Learning Mode - a learning mode during which all requests (or rather, query templates) fall into the list of allowed (whitelist). Thus, in the training mode, you can run your application in the tail and mane so that it collects the database of “clean” requests, and then turn on the “combat” mode with blocking all unknown requests (Database Firewall + Active protection).
GreenSQL starts as a service (daemon). Settings are managed via the web interface located at 127.0.0.1 : 5000.
The default login / password is admin / pwd.
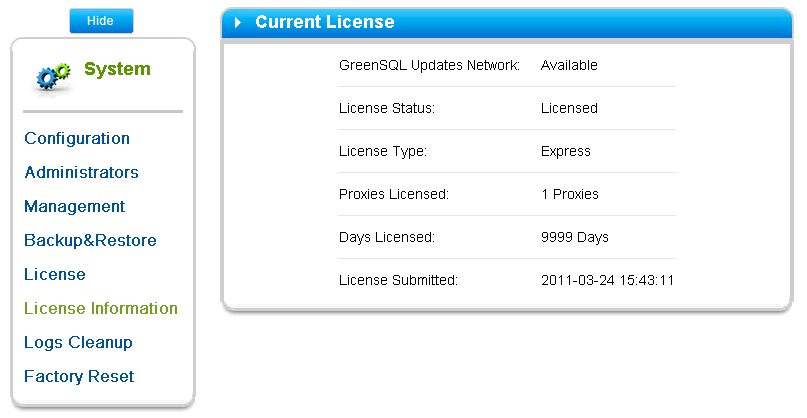
After authorization, you will be taken to the application statistics page. Go to the System> License section, and specify the license key that you will find in the letter with the download link (registration is required on the developer's site for download ).
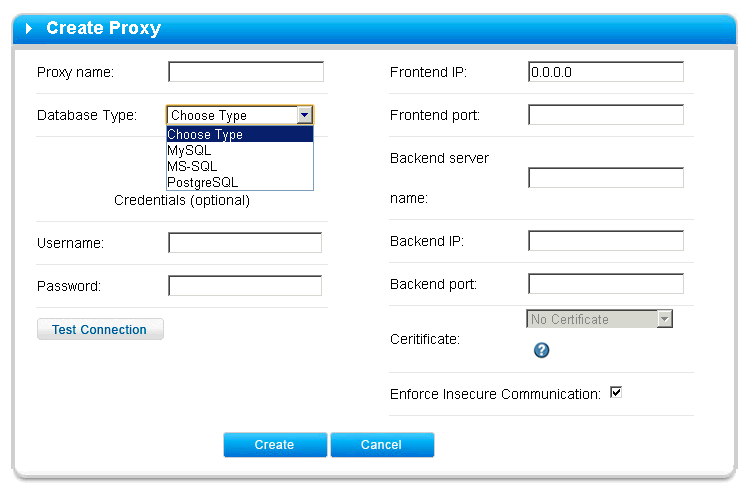
To get started, you need to create a proxy. In the free version you can create only one proxy. To create, go to Databases> Create proxy.
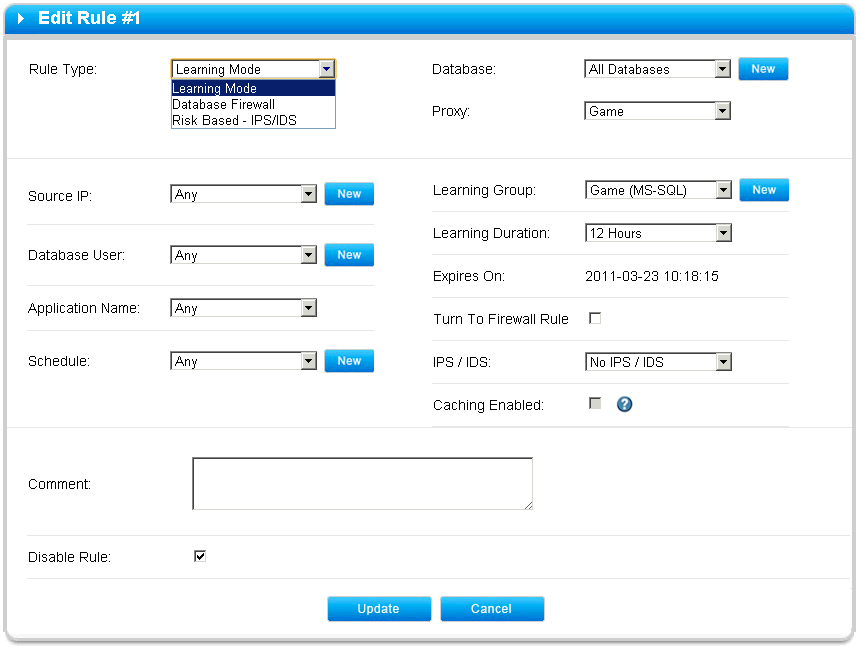
After creating the proxy, it will be launched on the specified port. Now you just need to set the rules for the proxy (Policy) to start using GreenSQL in your application. In principle, already at this stage you can try to configure your application to work with GreenSQL, however, it will work in a "transparent" mode.
Now you can try to configure your application to use GreenSQL.
Performance test taken from the official GreenSQL website . The essence of the test is that through Apache Bench several measurements were made in 400 hits and 10 competitive queries. The test result is shown in the image.

GreenSQL comes with good usage documentation. Here I did not try to translate it, but rather, outlined the general purpose and settings of the basic functionality of the program. Previous versions of GreenSQL (up to 1.2, current - 1.5) were distributed under the GPL.
Official sites www.greensql.com , www.greensql.net
In this case, GreenSQL will help ensure application security - a firewall or proxy for SQL servers. The GreenSQL service is located between your application and the SQL server, accepts sql queries from the application and, depending on its reliability, either redirects them to the target SQL server or rejects them.

GreenSQL supports Microsoft SQL 2000/2005/2008, MySQL 4.x / 5.x, PostgreSQL 7.x / 8.x and is cross-platform. Among the officially supported platforms are Microsoft Windows Server 2003/2008, Ubuntu, CentOS. 32-bit and 64-bit systems are supported.
As for the cost, there are several modifications of the program - free Express, Lite and Pro with a monthly payment. The main difference between paid and free versions, if you omit technical support and automatic updates, is the ability to modify requests on the fly and work with secure SSL connections.
Each version of GreenSQL supports several modes of operation.
Risk Based - IPS / IDS implements a basic algorithm for identifying potentially dangerous SQL queries. Those. GreenSQL performs semantic analysis of the query and, by indirect indications, determines the degree of its reliability. Calculation of the degree of danger is carried out taking into account the following parameters:
- operations that change the structure of tables
- queries to service tables and databases
- queries using file system access
- administrative queries, e.g. SHOW TABLES, SHOW CREATE TABLE
- comparison operations that always return TRUE, for example, 1 = 1, field = field
- comments inside the request
- using OR in the request
- operations on tables containing personal information, for example, users, accounts, payments
- sending an empty password in the request, for example, password = ``, pwd = '', passw = ''
Required blocked requests can be added to the allowed list (whitelist).
Database Firewall is an active protection mode that allows only requests from the whitelist list to be skipped.
Learning Mode - a learning mode during which all requests (or rather, query templates) fall into the list of allowed (whitelist). Thus, in the training mode, you can run your application in the tail and mane so that it collects the database of “clean” requests, and then turn on the “combat” mode with blocking all unknown requests (Database Firewall + Active protection).
Program settings
GreenSQL starts as a service (daemon). Settings are managed via the web interface located at 127.0.0.1 : 5000.

The default login / password is admin / pwd.
After authorization, you will be taken to the application statistics page. Go to the System> License section, and specify the license key that you will find in the letter with the download link (registration is required on the developer's site for download ).

To get started, you need to create a proxy. In the free version you can create only one proxy. To create, go to Databases> Create proxy.

- Proxy name - proxy name for identification inside GreenSQL
- Database type - type of protected DBMS
- Username and Password - login and password for authorization in the DBMS. It is optional, but their indication helps with further configuration to select database objects from the list, and not enter manually
- Frontend IP - on which IP the proxy will work (actual in case of several network connections on the machine). 0.0.0.0 means work on all network interfaces
- Frontend Port - on which port the proxy will work. It is this port that must be used in your application to connect to the DBMS
- Backend server name - the name of the protected DBMS. It can be anything, it is necessary for identification inside GreenSQL (I write localhost)
- Backend IP - IP address on which the protected DBMS is running (for example, 127.0.0.1)
- Backend port - the port on which the protected DBMS is running (usually, for MySQL - 3306, for MSSQL - 1433, for PostgreSQL - 5432)
After creating the proxy, it will be launched on the specified port. Now you just need to set the rules for the proxy (Policy) to start using GreenSQL in your application. In principle, already at this stage you can try to configure your application to work with GreenSQL, however, it will work in a "transparent" mode.

- Rule type - Rule type (Learning mode, Database firewall, Risk based). Depending on which type is selected, the fields for filling are changed.
- Database - the name of the protected database in the DBMS
- Proxy - the proxy to which the rule applies.
- IPS / IDS (Mode) - is common to all types of rules.
- No IPS / IDS - do not use automatic attack detection
- Active protection - block potentially dangerous requests
- Monitoring - log and not block potentially dangerous requests
Now you can try to configure your application to use GreenSQL.
Performance
Performance test taken from the official GreenSQL website . The essence of the test is that through Apache Bench several measurements were made in 400 hits and 10 competitive queries. The test result is shown in the image.

GreenSQL comes with good usage documentation. Here I did not try to translate it, but rather, outlined the general purpose and settings of the basic functionality of the program. Previous versions of GreenSQL (up to 1.2, current - 1.5) were distributed under the GPL.
Official sites www.greensql.com , www.greensql.net
