Ledger's hardware cryptocurrency wallet was hacked by a 15-year-old hacker

The last few years have been very successful for the cryptosphere. The course gradually grew (up to January of this year), those who bought some types of cryptocurrency, grew rich by leaps and bounds. And it is clear that this wealth must be stored somewhere so that no one steals it. But where? You will not carry the “number” to the bank, so there are only two options - either on a “hot” wallet, your own or the stock exchange, or on a hardware “cold” one.
Of the latter, the most reliable are the wallets of the company Ledger, whose headquarters are located in France. According to the manufacturers, their wallets can not be hacked. Neither by selecting a password, nor by replacing the firmware, with anything. And indeed, for many years the protection remained impenetrable, users were very pleased. But this week everything has changed.
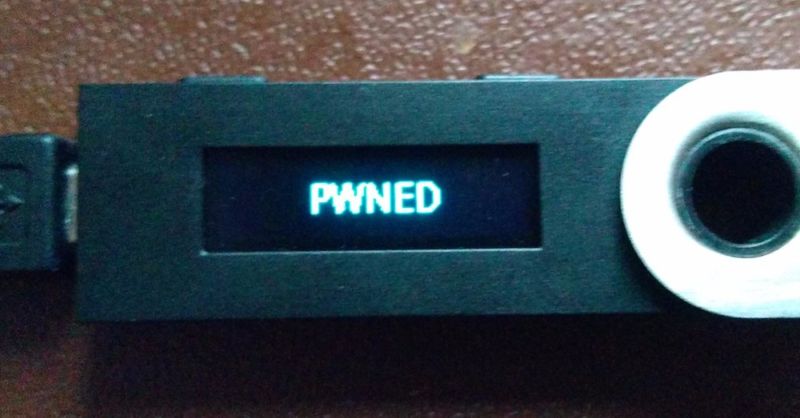
The wallet protection was cracked by a 15-year-old teen who was able to bypass the protection and demonstrate the hacked wallet. The teenager’s name is Salim Rashid, and he initially published all the information on his blog . He was able to show a proof-of-concept attack using the example of the Ledger Nano S model, which costs about $ 100.
The program code is very small, only 300 bytes. But on the other hand, it allows an attacker to generate an address for the "iron" wallet with access passwords known to the cracker. The attacker may even then transfer all this data to a new iron wallet to recover private keys that the old wallet stores for the specified address.
The problem is that Ledger Nano S is sold on eBay, which means used devices. And if they are properly modified, then the attacker will be able to do all that is described above. At the same time, representatives of the company had previously stated that buyers can easily acquire and use used wallets without fear of anything bad.
Opportunities that hacking opens up to all sorts of bad personalities are difficult to underestimate.. For example, the amount of payment sent from a compromised wallet can be changed. And the address to which the payment is sent, you can also replace any other. And that is not all. As it turned out, the code created by the hacker (here the term is used in a positive sense, since the teenager clearly did not do anything wrong) works on the older model of the iron wallet Ledger Blue, its value reaches $ 200. His company is positioning as the most reliable protection of all. It seems that the positioning is erroneous.
It is worth noting that Rashid discovered the problem back in November by sending information to the company. After the release of the update for flashing the wallet, Ledger representatives stated that the vulnerability was not critical, but it was fixed anyway. As for the statement of "non-critical", the company had in mind that third-party wallets connected to the hardware are detected by the Ledger software, so this is a problem, but not fatal.
For Ledger Blue, as the head of the Ledger information security department, Charles Guilleume, says, the probability of hacking is altogether negligible. Sales of such devices are direct, there are no used gadgets, so there is no particular reason to fight with theoretical vulnerability.
But is the threat really relevant?
The teenager who discovered the vulnerability is going to check whether the company really did everything in its power to make the Nano S safe. Even if this is true, according to Rashid, in the future there is no guarantee that someone will not apply the modified code that he developed himself. Not in the sense that the code is publicly available, not at all. It means that another person will be able to create something similar. Once he has thought of one, then another person can also do it.
An interesting point is the microcontroller, which is responsible for the security of the gadget in Blue and Nano S, ST31H320, is unable to work with the connected displays, USB-connections or other high-speed channels for receiving / transmitting data. In order to add the ability to connect the system to a PC, another chip was chosen, the STM32F042K6 microcontroller. He works here as a proxy.
The security microcontroller, which the company Ledger calls Secure Element, interacts with the second chip, which the company designated as MCU. So he performs all the necessary tasks to interact with the periphery, including USB, OLED-display, and also handles button presses. The exploit developed by Rashid allowed to replace the original firmware of the device with a modified firmware. In this case, the MCU sent the security chip information that the gadget is still working with the original software.
An independent researcher named Matt Green from Johns Hopkins University studied all the data provided by Rashid. And he also doubts that the firmware update released by Ledger will completely solve the problem with the vulnerability.
“Ledger is trying to solve a complex task that can be called fundamental. What they need to do is check the firmware, its interaction with the processor. At the same time, the security chip cannot “read” the code processed by the processor. That is why a workaround was chosen that still allowed both chips to work together. At the same time, it is impossible to verify whether the information transmitted by one chip to the other is true, ”Green says.
The complexity of solving this problem contrasts sharply with the company's assurance that it will be possible to solve all security problems once and for all. In each box with a wallet is a leaflet with text that convinces the user of the complete invulnerability of the gadget. Manufacturers claim that the security chip prevents any interference with the software or hardware of the device.
15-year-old hacker was able to prove that this is not entirely true. And now the company will have to prove that it is she who is right, and the danger to the owners of iron wallets Ledger no longer threatens.
