Overview of Obfuscators for .NET
I dare to assume,% username%, that you know what obfuscation is, why it is needed in the .NET world, and what is the difference between control flow obfuscation and MSIL code encryption.
It is also assumed that you have seen .NET Reflector and are familiar with some kind of symbolic debugger, I will give examples on WinDbg.
I have been dealing with the topic of obfuscators for quite some time, but recently I had to update my knowledge.
Not so long ago, I was faced with the task of choosing a good obfuscator for .NET4. After reviewing a bunch of software, I made a small review where I tried to include the most famous obfuscators.
Under katom more about each.
The entries in the tablet are in alphabetical order so as not to offend anyone.
The code is encrypted using NecroBit (the name of their technology), rumors are circulating on the forums that NecroBit is successfully grunting. Perhaps I just did not find it, because did not make much effort. The code could not be parsed; WinDbg also did not find anything.
Reflector:

Something can be extracted using WinDbg, but the IL-code of the methods is not given.
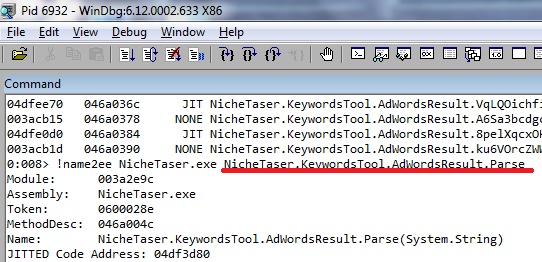
It was recently bought by RedGate. Honestly, I did not understand the choice of RedGate, {sa} does not even know how to encrypt MSIL. After sitting with the debugger, you can figure out the code. I do not recommend using this obfuscator, the price of $ 750 is clearly not consistent with the quality.
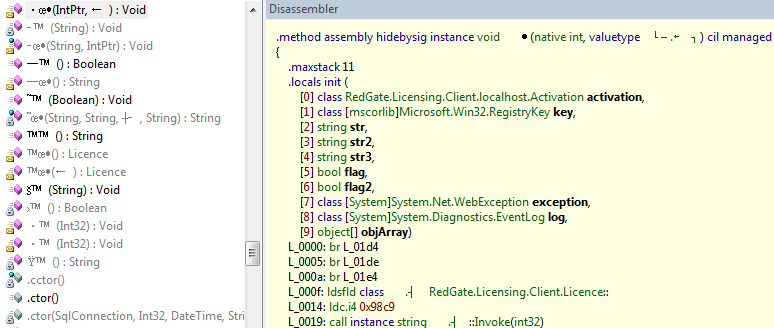
All that this obfuscator does with code is the obfuscation of control flow in something like this: Reflector in C # does not parse the code (although this is easy), but in IL it’s fine:
I downloaded a super example from their site. They promised that Reflector would not open. Reflector, in fact, swore, but opened:

Products of the same class, I believe, are very suitable if you need to protect the code from further refactoring and excessive curiosity.
Babel:
However, WinDbg successfully showed that inside the assembly made by Babel (probably because I had a community version; full, unfortunately, I did not check):

They write on the site that they work with the source, and this results in an obfuscated source. A very interesting approach, but unfortunately, you cannot download the obfuscator itself. Minus - with this approach, MSIL encryption and incorrect instructions are impossible.
The previous version of this obfuscator had many cracks that appeared very quickly. Which suggests that hackers know how this obfuscator works. I did not see the latest version of the crack, but there is a bad problem:
You can use it, but expect surprises.
The assembly turned out to be quite good, but an ambush awaited me - with the assembly came 4 MB DLLs from this obfuscator:

A very well-known product, I was surprised that the resulting applications are so easy to hack:
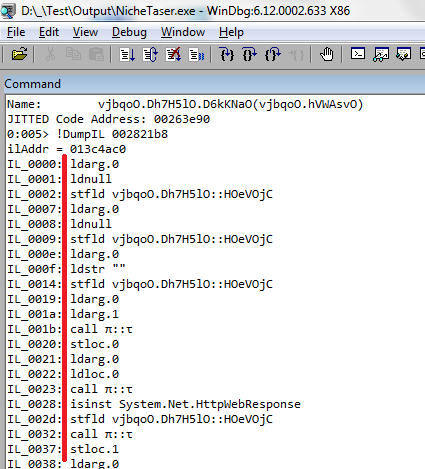
Reflector assembly does not open, it is encrypted. The cant is that the assembly is fully encrypted, and it is decrypted after the application starts. After decryption, no protection in memory:
Obfuscator is free. It's a shame that only simple rename can do it. What can please (I personally am more interested in console or MSBuild versions) is the rather simple process of obfuscation, it all comes down to dragging and dropping the assembly file. Here is the result
Obfuscators are built on a similar principle, they can execute code by introducing precompiled .NET assemblies into the application, which eliminates the possibility of intercepting JIT compilation calls.
The resulting applications can run even without .NET installed on the machine. The size of the resulting application is 10..50 MB, depending on which libraries you will use.
These solutions are very expensive. But, unfortunately, cracks go to PostBuild (even the last one). Probably in well-known circles, there are also ready unpackers.
A definite answer to this question is not given, it all depends on what is a value in your code for you:
None of the above. I use my own obfuscator. This is platform-specific piecewise assembly encryption, similar to .NET Reactor.
The cost of its creation cost about $ 3000- $ 5000. Yes, it is no better than the existing ones, but there is one thing - the principle of obfuscation has not been announced publicly, to feel it is not worthwhile. To crack it, you just need to spend more time.
As they say, think for yourself, decide for yourself ...
It is also assumed that you have seen .NET Reflector and are familiar with some kind of symbolic debugger, I will give examples on WinDbg.
I have been dealing with the topic of obfuscators for quite some time, but recently I had to update my knowledge.
Not so long ago, I was faced with the task of choosing a good obfuscator for .NET4. After reviewing a bunch of software, I made a small review where I tried to include the most famous obfuscators.
General conclusions and reasoning
- Free obfuscators are very weak and suitable only for simple renaming. Only a few of them know about control flow;
- There are very good solutions (control flow, MSIL encryption) costing up to $ 500;
- Adult solutions cost about 5,000, but unfortunately, for many of them there are unpackers. Some of them grunted.
The obfuscator grunted, which means they understood his protection system. In the trash such an obfuscator. - There are solutions “against cattle hackers” - the assembly is fully encrypted and decrypted on the fly. Cracking with a symbolic debugger is such an assembly simple.
Under katom more about each.
The entries in the tablet are in alphabetical order so as not to offend anyone.
| Title and URL | Cost | Control flow | MSIL Encryption | Details ... |
|---|---|---|---|---|
| .NET Reactor | $ 180 | + | + | Encrypts the code, breaking it is quite difficult, but maybe there is an unpacker |
| {SmartAssembly} | $ 795 | + | - | Used by RedGate. Grunted. |
| Aspose.obfuscator | (-) | (-) | (-) | The project is no longer supported. |
| Assemblur | Free | - | - | Studio plugin + console. Almost nothing will be obfuscated |
| Babel | $ 250 | + | ? | Something is encrypting, but in runtime you can run DumlIL, maybe the full version works well |
| Bithelmet | $ 250 | ? | ? | Fell, saying .NET is missing |
| C # Source Code Obfuscator | ? | - | - | It seems to work with .NET sources. An interesting approach, but apart from the description and example, I did not find anything |
| Cilsecure | > $ 1000 | ? | ? | Paid obfuscator, even without a trial. The cat is in the bag. |
| CodeArmor | ? | ? | ? | Another paid obfuscator, very muddy and also without a trial. Support did not respond. |
| CodeVeil | $ 900 | + | + | Known for the fact that it burns in antiviruses. All in all a good thing |
| Codewall | $ 400 | + | + | Sane Obfuscator |
| Decompiler.NET | $ 550 | - | - | 3 years abandoned |
| Deepsea | $ 200 | ± | - | Tends to do a lot of switch. In general, non-usable. |
| DesaWare | $ 1,500 | + | ? | No .NET 4.0 |
| DNGuard HVM | $ 900 | ? | ? | A buggy installer without half the buttons, the first application crashed |
| Dotfuscator | $ 1900 | + | ? | The community version is very meager, and Enterprise is expensive, but maybe it's worth it. |
| dotNetProtector | $ 500 | + | + | Added over 4 MB of his DLLs to the project |
| Eazfuscator.NET | Free | - | - | Simple rename |
| Goliath.NET | $ 115 | + | ± | Reflector assembly does not open, but in WinDbg the whole source is visible |
| Netorbiter | Free | - | - | Funny obfuscator. I made my own proxy, where I completely copied my exe-shnik and added something in addition. |
| Obfuscar | Free | - | - | Simple rename based on Mono.Cecil. .NET 4.0 does not support |
| Obfuscator.NET | $ 200 | ? | ? | The assembly done immediately fell. Even on .NET 3.5. |
| PCguard for .NET | $ 400 | ? | ? | More focused on licensing than obfuscation. The trial was not sent. View would be very interesting. |
| Phoenix protector | Free | (-) | (-) | Even .NET 3.5 does not hold |
| Salamander.NET | $ 800 | - | - | Using the example on the website, the reflector, of course, swears, suspecting an ambush, but disassemble with a bang |
| Sharpbfuscator | Free | - | - | Apparently, the product has long been abandoned. |
| Skater.net | $ 100 | - | - | Strange thing, renamed several methods + searched for old ILDASM. Probably abandoned. |
| Spices.NET | $ 400 | - | ± | Encrypts the entire assembly, which is bad |
| VMWare ThinApp | > $ 5000 | + | + | The resulting application can run even without .NET. Curious contraption |
| Xenocode PostBuild | > $ 1000 | + | + | Obfuscator itself grunts, which leads to not very good thoughts |
More about particularly interesting individuals
.NET Reactor
The code is encrypted using NecroBit (the name of their technology), rumors are circulating on the forums that NecroBit is successfully grunting. Perhaps I just did not find it, because did not make much effort. The code could not be parsed; WinDbg also did not find anything.
Reflector:

Something can be extracted using WinDbg, but the IL-code of the methods is not given.

{SmartAssembly}
It was recently bought by RedGate. Honestly, I did not understand the choice of RedGate, {sa} does not even know how to encrypt MSIL. After sitting with the debugger, you can figure out the code. I do not recommend using this obfuscator, the price of $ 750 is clearly not consistent with the quality.
All that this obfuscator does with code is the obfuscation of control flow in something like this: Reflector in C # does not parse the code (although this is easy), but in IL it’s fine:
L_1 br.s L_4
L_2 br.s L_3
L_3 ret
L_4 push
L_5 ldc.i4.1
L_6 br.s L_2

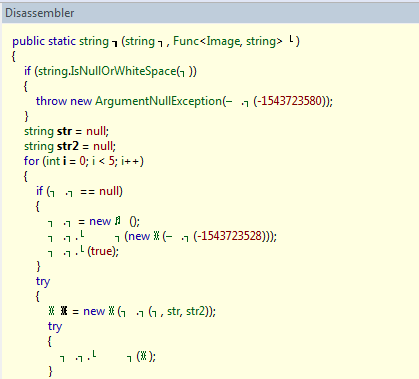
Salamander.NET
I downloaded a super example from their site. They promised that Reflector would not open. Reflector, in fact, swore, but opened:

Babel (one that is not free), CodeWall, dotNetProtector
Products of the same class, I believe, are very suitable if you need to protect the code from further refactoring and excessive curiosity.
Babel:

However, WinDbg successfully showed that inside the assembly made by Babel (probably because I had a community version; full, unfortunately, I did not check):

C # Source Code Obfuscator
They write on the site that they work with the source, and this results in an obfuscated source. A very interesting approach, but unfortunately, you cannot download the obfuscator itself. Minus - with this approach, MSIL encryption and incorrect instructions are impossible.
XHEO CodeVeil
The previous version of this obfuscator had many cracks that appeared very quickly. Which suggests that hackers know how this obfuscator works. I did not see the latest version of the crack, but there is a bad problem:
- Antivirus does not like applications, the obfuscator encrypts the assembly and writes to itself (which pleases, the assembly is encrypted in pieces)
- After this obfuscator, the application must be tested very well, bugs can fall in the most unexpected places.
You can use it, but expect surprises.
dotNetProtector
The assembly turned out to be quite good, but an ambush awaited me - with the assembly came 4 MB DLLs from this obfuscator:

Spices.NET
A very well-known product, I was surprised that the resulting applications are so easy to hack:

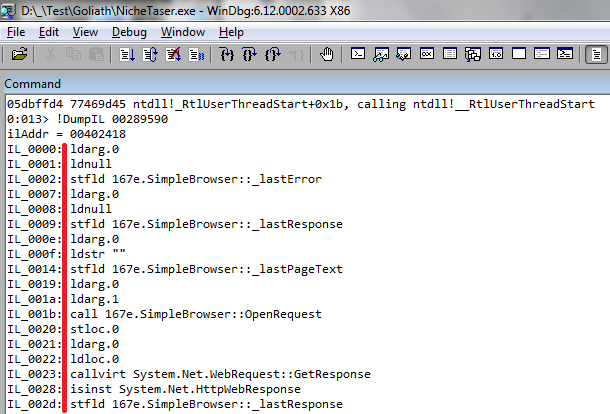
Goliath.NET
Reflector assembly does not open, it is encrypted. The cant is that the assembly is fully encrypted, and it is decrypted after the application starts. After decryption, no protection in memory:

Eazfuscator.Net
Obfuscator is free. It's a shame that only simple rename can do it. What can please (I personally am more interested in console or MSBuild versions) is the rather simple process of obfuscation, it all comes down to dragging and dropping the assembly file. Here is the result

VMWare ThinApp, Xenocode PostBuild
Obfuscators are built on a similar principle, they can execute code by introducing precompiled .NET assemblies into the application, which eliminates the possibility of intercepting JIT compilation calls.
The resulting applications can run even without .NET installed on the machine. The size of the resulting application is 10..50 MB, depending on which libraries you will use.
These solutions are very expensive. But, unfortunately, cracks go to PostBuild (even the last one). Probably in well-known circles, there are also ready unpackers.
What do you choose,% username%?
A definite answer to this question is not given, it all depends on what is a value in your code for you:
- The whole code as a whole - not just one “trick” in the code is important, but the code in its entirety. Encrypt the code with some simple obfuscator, it is better to encrypt MSIL. If all the code is really important, decrypting it completely will be more difficult than writing it again, and no one will do it;
- A separate "trick" - for example, key verification. I would advise you not to give such code to public at all, it is better to cut the functionality in the trial version. In the full version, the key must be checked, but the risk of theft is less. Nevertheless, I would advise using the obfuscator more seriously.
What am I using?
None of the above. I use my own obfuscator. This is platform-specific piecewise assembly encryption, similar to .NET Reactor.
The cost of its creation cost about $ 3000- $ 5000. Yes, it is no better than the existing ones, but there is one thing - the principle of obfuscation has not been announced publicly, to feel it is not worthwhile. To crack it, you just need to spend more time.
As they say, think for yourself, decide for yourself ...
