OS recovery after ransomware virus
My best friend brought me to see a netbook, which viruses sternly walked on, and asked to help clean the system from the zoo. For the first time I saw firsthand a funny branch in the development of malware: ransomware. Such programs block some of the functions of the operating system and require sending an SMS message to receive an unlock code. The treatment turned out to be not entirely trivial, and I thought that perhaps this story would save some nerve cells for someone. I tried to provide links to all sites and utilities that were needed during the treatment.
In this case, the virus was an Internet Security antivirus program and required sending SMS K207815200 to number 4460. There is a page on Kaspersky Lab’s website that allows generating response codes for ransomware: support.kaspersky.ru/viruses/deblocker
DrWeb has a page with detailed recommendations on combating ransomware: www.drweb.com/unlocker/index/?lng=en
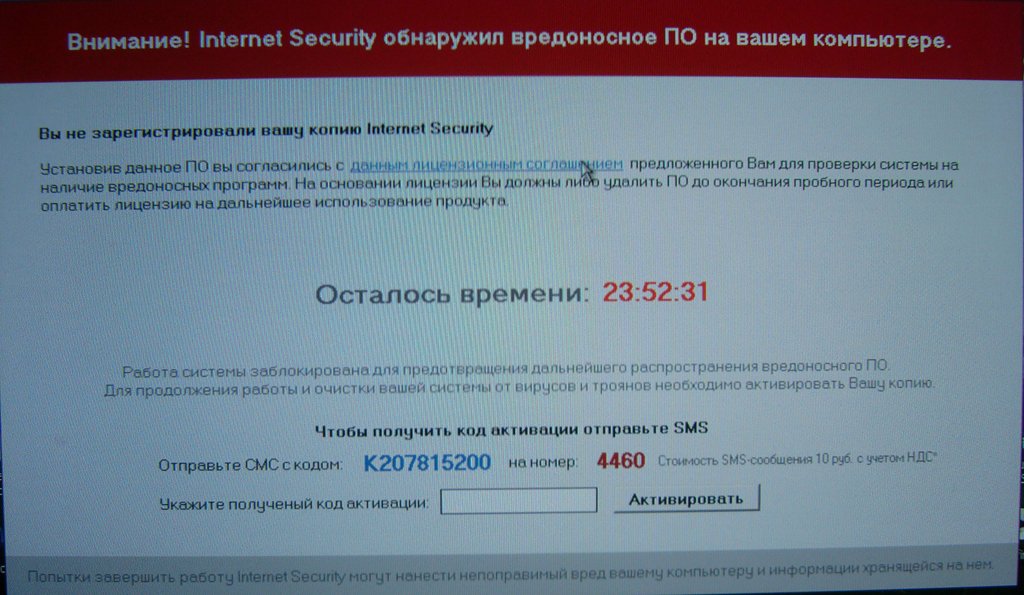
However, after entering the code, the OS functions remained blocked, and the launch of any antivirus program led to the virus window instantly opening. , carefully emulating the work of the antivirus:

Attempts to boot into safe modes led to exactly the same result. It was also complicated by the fact that the passwords for all administrator accounts were empty, and the entrance to the computer via the network for administrators with an empty password was closed by default by policy.
I had to boot from a USB Flash drive (in the netbook, by definition, there is no drive for drives). The easiest way to make a bootable USB drive:
1. Format the drive to NTFS
2. Make the partition active (diskpart -> select disk x -> select partition x -> active)
3. Use the utility \ boot \ bootsect.exe from the Vista / Windows 2008 / Windows 7 distribution: bootsect / nt60 X: / mbr
4. We copy all the distribution files (I had the Windows 2008 distribution on hand) to the usb disk. Everything can be loaded.
Since we do not need to install the OS, but treat viruses, we copy to the disk a set of free healers ( AVZ , CureIt ) and auxiliary utilities (looking ahead, I needed Streams from Mark Russinovich) and Far . We reboot the netbook, in the BIOS we set the boot from USB.
The installation program for Windows 2008 is loaded, we agree with the choice of language, Install now and after that press Shift + F10. A command prompt window appears from which we can launch our anti-virus tools and search for infection on the system drive. Here I ran into difficulty, CureIt dropped the system into the blue screen of death with a curse at the error of working with NTFS, and AVZ, although it worked out, could not find anything. Apparently the virus is very, very fresh. The only clue is the AVZ message that an executable code has been detected in an additional NTSF stream for one of the files in the Windows directory. It seemed strange and suspicious to me, since additional NTFS streams are used in very specific cases and nothing should be stored there on normal machines.
Therefore, I had to download the Streams utility (http://technet.microsoft.com/en-us/sysinternals/bb897440.aspx) from Mark and delete this stream. Its size was 126464 bytes, just like the dll files that the virus laid out on flash drives inserted into the system.
After that, with the help of Far, I scanned the entire system disk for files of the same size and discovered another 5 or 6 suspicious files created in the last 2-3 days. They were deleted in the same way. After that, CureIt was able to work out (apparently it stumbled on additional threads) and successfully cleared two more trojans :)
After the reboot, everything worked, additional runs of anti-virus scanners did not find anything. With AVZ, policies restricting OS features were restored. A strict suggestion was made to a friend about how important it is to use antiviruses, especially since there are many free ones ( Security Essentials , which I use on my home machines, Avast Home Edition , which I also like very much.
Upd: finally got around to move to a thematic blog.
In this case, the virus was an Internet Security antivirus program and required sending SMS K207815200 to number 4460. There is a page on Kaspersky Lab’s website that allows generating response codes for ransomware: support.kaspersky.ru/viruses/deblocker
DrWeb has a page with detailed recommendations on combating ransomware: www.drweb.com/unlocker/index/?lng=en

However, after entering the code, the OS functions remained blocked, and the launch of any antivirus program led to the virus window instantly opening. , carefully emulating the work of the antivirus:

Attempts to boot into safe modes led to exactly the same result. It was also complicated by the fact that the passwords for all administrator accounts were empty, and the entrance to the computer via the network for administrators with an empty password was closed by default by policy.
I had to boot from a USB Flash drive (in the netbook, by definition, there is no drive for drives). The easiest way to make a bootable USB drive:
1. Format the drive to NTFS
2. Make the partition active (diskpart -> select disk x -> select partition x -> active)
3. Use the utility \ boot \ bootsect.exe from the Vista / Windows 2008 / Windows 7 distribution: bootsect / nt60 X: / mbr
4. We copy all the distribution files (I had the Windows 2008 distribution on hand) to the usb disk. Everything can be loaded.
Since we do not need to install the OS, but treat viruses, we copy to the disk a set of free healers ( AVZ , CureIt ) and auxiliary utilities (looking ahead, I needed Streams from Mark Russinovich) and Far . We reboot the netbook, in the BIOS we set the boot from USB.
The installation program for Windows 2008 is loaded, we agree with the choice of language, Install now and after that press Shift + F10. A command prompt window appears from which we can launch our anti-virus tools and search for infection on the system drive. Here I ran into difficulty, CureIt dropped the system into the blue screen of death with a curse at the error of working with NTFS, and AVZ, although it worked out, could not find anything. Apparently the virus is very, very fresh. The only clue is the AVZ message that an executable code has been detected in an additional NTSF stream for one of the files in the Windows directory. It seemed strange and suspicious to me, since additional NTFS streams are used in very specific cases and nothing should be stored there on normal machines.
Therefore, I had to download the Streams utility (http://technet.microsoft.com/en-us/sysinternals/bb897440.aspx) from Mark and delete this stream. Its size was 126464 bytes, just like the dll files that the virus laid out on flash drives inserted into the system.
After that, with the help of Far, I scanned the entire system disk for files of the same size and discovered another 5 or 6 suspicious files created in the last 2-3 days. They were deleted in the same way. After that, CureIt was able to work out (apparently it stumbled on additional threads) and successfully cleared two more trojans :)
After the reboot, everything worked, additional runs of anti-virus scanners did not find anything. With AVZ, policies restricting OS features were restored. A strict suggestion was made to a friend about how important it is to use antiviruses, especially since there are many free ones ( Security Essentials , which I use on my home machines, Avast Home Edition , which I also like very much.
Upd: finally got around to move to a thematic blog.
