How a typical ISP (Internet Service Provider) works
Many people ask how the network of the provider is arranged or how to build the network by themselves, in this article I will show how the network is designed and works for me, at a logical level. Although I do not consider my structure to be ideal, it could be done better, but it’s mine :) for the truth “ask 2 providers how to build a network - you will get 3 different options“
Now more about how it works
A typical data transmission network consists from 4 levels, many say that 3 but in fact there are 4
1 level - the border is a network, that is, a junction with other operators, it is a border.
At this level, work is usually carried out with backbone operators who take the Internet and client operators - to whom we give the Internet :) Interaction in 90% of cases estvlyaetsya via dynamic routing protocol BGP
Level 2 - this is the core of the network
. It includes billing, radius server, central switches where everything is stuck, NAT and shapers (with which we cut the strip to the client. You can cut it on the port of the managed switch - but in this case the local resources will be at the tariff speed, we have to provide the same tariff rate to 100Mbps Internet and within their network
interaction between the equipment usually also occurs via dynamic routing protocols such as BGP (in this case, the internal BGP or OSPF), but there are adherents of a statically Route
3 level - is the level of distribution, aggregation
This level usually usually includes managed switches (2nd or 3rd level) of a quarter or district, depending on the internal structure of the network. In my case, level 3 switches are installed and are sometimes supplemented with a level 2 switch, because with a VLAN scheme for a house - do not rake house vlans in the network core
уровень level 4 - access level, access, client access point
These are the same house switches that are in the basements and attics of houses in a drawer. Clients are already connecting to them. In the CIS countries, D-Link DES-3526 is most often used, D-Link 3026 and slowly began to install D-Link DES-3028, for legal entities they usually disdain long and put Cisco Catalyst 2950
Now about how it works for me:
1 ) Level 1 device
As the border routers, 2 Juniper j4350 pieces of iron are used, each of which has its own trunk uplink, interaction with uplinks is carried out using the BGP protocol (i.e. we give uplink networks assigned to our AS (autonomous system) and get from them a complete list of routes in the network Internet (full-view)
2) 2 device level
The second level occurs NAT-ing clients sheypirovanie tariff rates and routing (Internet network or peer)
as NAT-shapers and Erov intelevskih server uses two pla form under the control of FreeBSD (each of them is made and NAT and cutting speeds and each reserves each other). Shaping is done using dummynet and tables (tablearg) and nat using pf
An internal BGP also runs between these routers and border routers (j4350) so that in case of failure of one of the boarders, it quickly switches to the second one and some traffic balancing is also not superfluous.
OSPF protocol runs between routers and level 3 switches for the exchange of intranet and peer-to-peer routes + we will announce a default route from routers to them, i.e. the default route. Router 1 has a metric of 100
Router 2 has a metric of 200, that is, in the event of a failure of one of the routers, all packets will go through the backup (switching interval of about 10 seconds)
3) device of the 3rd level
In my VLAN scheme for a house at the distribution level, I have to keep switches of the 3rd level, which are involved in routing home networks and VLANs.
IGMP snooping works on the switches, all unnecessary multicast is cut off and Broadcast and NetBIOS ports are cut (tcp / udp 135-139, 445)
4) Level 4 device
D-Link DES-3526 switches are on the fourth level, we plan to install DES-3028 , because 4 gigabit ports are often needed. Yes, and according to rumors, 3526 is already EOL
Clients connect directly to the switches, loopback detect is turned on at the subscriber pores (to disable ports with a loop), the maximum number of mac addresses on the port is 5, igmp snooping is turned on, and the entire multicast is filtered except for the ranges 224.200.100.0-224.200.150.255 and 224.0.0.2 , all Broadcasts (except the arp protocol) and the entire NetBIOS are also killed.
And now the logical diagram of this whole thing:
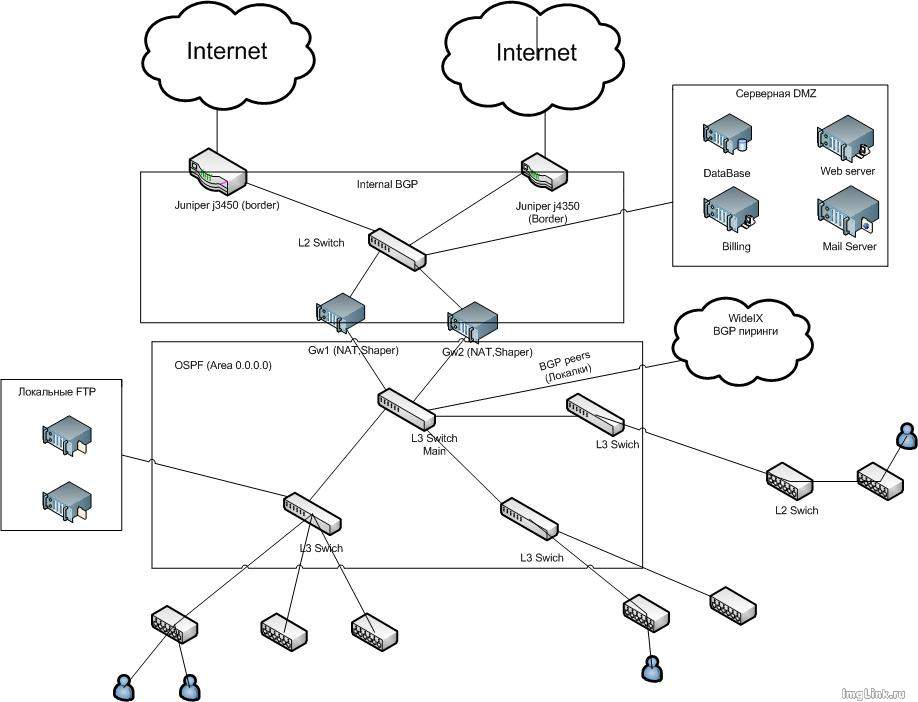
Now more about how it works
A typical data transmission network consists from 4 levels, many say that 3 but in fact there are 4
1 level - the border is a network, that is, a junction with other operators, it is a border.
At this level, work is usually carried out with backbone operators who take the Internet and client operators - to whom we give the Internet :) Interaction in 90% of cases estvlyaetsya via dynamic routing protocol BGP
Level 2 - this is the core of the network
. It includes billing, radius server, central switches where everything is stuck, NAT and shapers (with which we cut the strip to the client. You can cut it on the port of the managed switch - but in this case the local resources will be at the tariff speed, we have to provide the same tariff rate to 100Mbps Internet and within their network
interaction between the equipment usually also occurs via dynamic routing protocols such as BGP (in this case, the internal BGP or OSPF), but there are adherents of a statically Route
3 level - is the level of distribution, aggregation
This level usually usually includes managed switches (2nd or 3rd level) of a quarter or district, depending on the internal structure of the network. In my case, level 3 switches are installed and are sometimes supplemented with a level 2 switch, because with a VLAN scheme for a house - do not rake house vlans in the network core
уровень level 4 - access level, access, client access point
These are the same house switches that are in the basements and attics of houses in a drawer. Clients are already connecting to them. In the CIS countries, D-Link DES-3526 is most often used, D-Link 3026 and slowly began to install D-Link DES-3028, for legal entities they usually disdain long and put Cisco Catalyst 2950
Now about how it works for me:
1 ) Level 1 device
As the border routers, 2 Juniper j4350 pieces of iron are used, each of which has its own trunk uplink, interaction with uplinks is carried out using the BGP protocol (i.e. we give uplink networks assigned to our AS (autonomous system) and get from them a complete list of routes in the network Internet (full-view)
2) 2 device level
The second level occurs NAT-ing clients sheypirovanie tariff rates and routing (Internet network or peer)
as NAT-shapers and Erov intelevskih server uses two pla form under the control of FreeBSD (each of them is made and NAT and cutting speeds and each reserves each other). Shaping is done using dummynet and tables (tablearg) and nat using pf
An internal BGP also runs between these routers and border routers (j4350) so that in case of failure of one of the boarders, it quickly switches to the second one and some traffic balancing is also not superfluous.
OSPF protocol runs between routers and level 3 switches for the exchange of intranet and peer-to-peer routes + we will announce a default route from routers to them, i.e. the default route. Router 1 has a metric of 100
Router 2 has a metric of 200, that is, in the event of a failure of one of the routers, all packets will go through the backup (switching interval of about 10 seconds)
3) device of the 3rd level
In my VLAN scheme for a house at the distribution level, I have to keep switches of the 3rd level, which are involved in routing home networks and VLANs.
IGMP snooping works on the switches, all unnecessary multicast is cut off and Broadcast and NetBIOS ports are cut (tcp / udp 135-139, 445)
4) Level 4 device
D-Link DES-3526 switches are on the fourth level, we plan to install DES-3028 , because 4 gigabit ports are often needed. Yes, and according to rumors, 3526 is already EOL
Clients connect directly to the switches, loopback detect is turned on at the subscriber pores (to disable ports with a loop), the maximum number of mac addresses on the port is 5, igmp snooping is turned on, and the entire multicast is filtered except for the ranges 224.200.100.0-224.200.150.255 and 224.0.0.2 , all Broadcasts (except the arp protocol) and the entire NetBIOS are also killed.
And now the logical diagram of this whole thing:

