In social networks you can find photos of air tickets and award bonus miles.
Ticket reservation systems do not comply with basic safety rules. Because of this, resourceful hackers can award bonus miles that airlines provide frequent flyers. How to do this is described in detail in the presentation of the renowned expert Karsten Nohl and his colleagues Namagany Nikodievich (Nemanja Nikodijević), which the guys presented at the 33rd annual conference of Chaos Communication Congress (33C3).
This is a global booking system (GDS), which collects information from travel agencies and ticket booking sites with ticket applications, as well as from airlines, hotels and car rental companies.
All information is concentrated in the GDS with the determination of the availability of vouchers / air tickets, their price and reservation. This database stores not only general information about prices and availability, but also personal information about customers who have booked tickets.
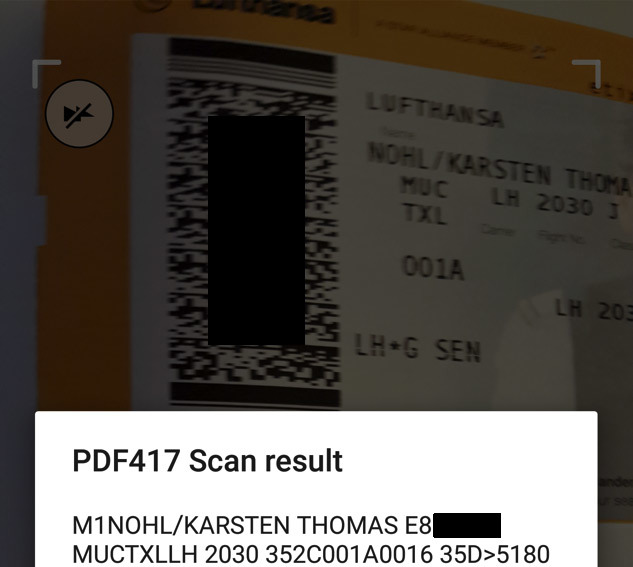
Here is what a typical e-ticket looks like, which is issued by the GDS system to a specific user after registering a reservation. The document is stored in the GDS database.

Reservation Code (PNR) smeared
Now the global market is dominated by three main GDSs: Amadeus (founded in 1987), Saber (founded in 1960) and Galileo (now a unit of Travelport). For example, Lufthabsa and AirBerlin cooperate with the first one, as well as the Expedia travel agent. From the second - American Airlines and Aeroflot. For example, if you book an Exped flight for American Airlines, then it will be stored in both GDS: in both Amadeus and Saber. It is generally difficult to predict in advance in which GDS specifically you can find personal information on a specific user, since there are also hotel reservations, travel agency agents, etc.
Carsten Nol and Namanya Nikodievich investigated the protection of information security in GDS systems and found that it is close to zero. We are talking about the level of security characteristic of electronic systems of the 70s and 80s. These companies began to use "cloud storage" of data even before such a term appeared. Provide reliable cryptographic protection at the time, they could not in principle. Moreover, the system provides a very weak level of access protection. This is due to the fact that too many agents are allowed access to the system: these are airlines, travel agencies, hotels, etc.
Thus, in fact, all GDS employees, as well as employees of all agents, have access to all PNRs. Researchers suggest that various government agencies also have access to PNRs.
For access from the GDS at the base level, you do not even need to set an arbitrary username and password. They are assigned automatically, where the user's last name is set as the login, and the booking code (PNR) is set as the password . It is the code that is printed on electronic tickets and which is smeared on the first screenshot.
And what do we see in numerous photos on Instagram and other social networks? Users carelessly photograph their electronic tickets and publish them in the public domain. Moreover, these codes can be collected even offline, simply by photographing tags on passenger baggage. Secret information (in fact, the password in the system) is simply printed on the printer, glued to the suitcase and put on display.

Sometimes it is encoded in the graphics code for the scanner, but easily recognized.

In the public domain, you can find thousands of such photos with codes from which PNRs are extracted.
What can we get if we know the PNR identifier (six characters) and last name? We can get information about the identity of the user, perhaps more information about the hotel where his room is booked, and about renting a car. Plus information about bonus miles and other airline promotions for frequent flyers. Contact information: telephone, email address, often postal address. Often passport details are available in the GDS, including date of birth.
Hackers with access to the GDS also see payment information - a bank card number and expiration date (exp.date), as well as the user's IP address. This information may be useful in the further process of falsifying an individual.
The report's author notes that the six-digit PNR code can even be picked up by brute force. Entropy is 29.2–28.9 bits.
Airlines also allow you to do a lot if you apply with a well-known PNR. For example, they sometimes allow you to change the date of departure and change the ticket (this will be a surprise to the victim). Some even allow you to change the name in the ticket (this is already a nice bonus). Most companies give out various bonuses for PNR.
Thus, a common scenario emerges. We choose standard surnames, brutforsim PNR, we find suitable tickets. If the airline allows passengers on tickets without checking the passport, then change the date and email address - and we will fly to the right place. If the documents are checked, then we return the ticket, we get bonuses, with their help it buys a new ticket in its name - and we fly for free.
Free miles can be used not only for flights, but also for free accommodation in hotels and get gift certificates. With the help of the latter, it is possible to cash out free miles by exchanging certificates for goods and selling them or renting them back to the store in exchange for cash. So ancient booking systems are able to ensure a comfortable life for more than one hacker.
The report by Carsten Nol and Namanya Nikodievich gives details of the PNRs of various GDSs, valid symbols and other information for bruteforce.
Presentation of Carsten Nol and Namagny Nikodievich at 33C3 ( pdf )
