Throw antivirus in the trash
Some perceive the antivirus as an integral part of the operating system and simply do not imagine their existence without a bunch of protective packages from different manufacturers, freely passing infection, but causing terrible brakes and a whole bunch of conflicts, up to falling out in BSOD (blue screen of death :)). the best antivirus is the OS itself! you only need to learn how to use it correctly!
So before you start telling you how to configure the OS from the intrusions of sinister viruses, worms and other infections spreading both through the Internet and through all kinds of media. What will I get after building this security system:
+ restriction of access to the system for running programs;
+ ban on changing system files;
+ ban on changing both system and application programs in memory;
+ ban on implementation in other processes;
+ to differentiate access between users of one computer;
This method of protection has many other small advantages, but this is already a consequence of these four.
I am using OS: Windows XP Professional. This is important, because for example, in the Home Edition there are no tools for managing user groups and security systems.
So, let's start with:
I. First you need to create an administrator account and create (preferably) a password for it (if it has not been created yet). Although during installation, the system creates a built-in account with the name “Administrator” by default, but I immediately create a name for it, for example, “admin”.
I hope that you already have the system installed and you need to create an account:
Go to Start> Settings> Control Panel> User Accounts:
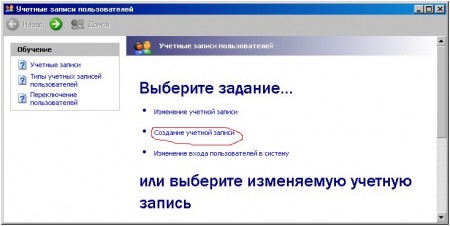
Create an account ...
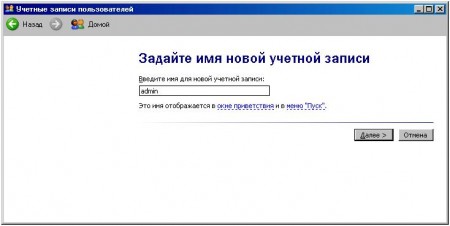
Call it “admin”, for example ...
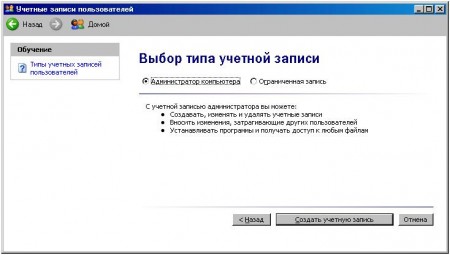
And select the type of account “Computer administrator ".
ATTENTION!!! I had a case when, when creating such an administrator account, all the documents in the “My Documents” folder were lost and I couldn’t return them: '(. Unfortunately this is probably a flaw of the developers, so call me, I can’t help you here. So just in case, copy all your documents from this folder to the backup folder.
So the account has been created. Now put a password on it. Select the created account and click "Create Password":
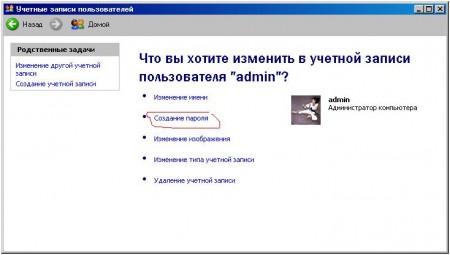
Enter the password. All! We have created an administrator.
Now you need to create an account for us. Those. the one in which we will constantly work:
1. Click again “Create an account”.
2. Enter a name, for example, "user".
3. Set the type of account “Limited account”.
4. If you want, you can put a password on it (if you do not want other users of this computer to log into your account).
The platform is created. In principle, you can stop at this stage if you do not store any very important documents (passwords, reports, important literature), but if there is one, I recommend reading this article to the end.
II. If you read this line, it means that you are not indifferent to the fate of your information accumulated in the computer. So what do I want to do now? :):
+ Create a folder in which all my documents will be stored and access to which I can ONLY get and no one else (even the system will not have access to my folder!);
1. So we exit the current user profile and go to the newly created "user".
2. Go to the drive on which we want to create this folder.
WARNING!!! To create a folder of this type, you must have a disk running the NTFS file system! If the disk has a FAT32 file system, then this option to create a folder will not be available :(. This is due to the different structure of file systems and their application.
If your disk works with NTFS, then rejoice - you can read on :).
3. Now we will configure full access to security properties, as By default, it is simple. Go to Tools> Folder Options ...> View. And uncheck the option “Use simple file sharing”:
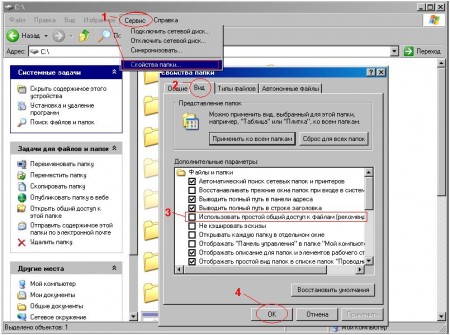
OK.
Now the Security tab has become available to us. To check this, right-click on any folder and select "Properties":
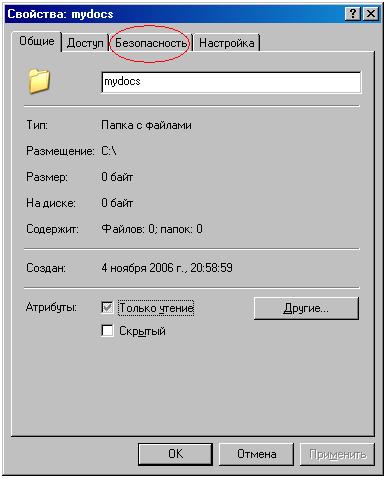
If this tab! all of a sudden! unavailable, it means your disk works with the FAT32 file system or with any other than NTFS.
At this stage, you can safely build what was planned, well, well:
1. Go to the drive of your choice (I have 2 drives C and D working with NTFS. I will create a folder on drive C).
2. Create a folder and call it somehow, well, for example, “mydocs”.
3. Now go to the folder properties. Open the tab "Security". And we see something like this:

Everything that is in the “Security” tab may differ! This is due to where to create the folder. If you create a folder on the disk where your OS is installed (where the WINDOWS. C: \ WINDOWS folder is located). If the folder is created on the disk where the OS is installed, the picture will be like this: FIGURE 1.
If the folder is created on the disk where there is no OS, the picture may be like this: FIGURE 2.
But do not be afraid, there is nothing to worry about.
From now on, let's take a closer look at all the elements of the "Groups or Users" list.
This list shows all users and user groups that have access to this folder. For example, I have these lines:
sergey (SERG \ sergey) - sergey user located on a computer with the name SERG and having a profile called sergey has “Special permissions”.
SYSTEM is a built-in profile for the system that I have "Full access to this folder."
Administrators (SERG \ Administrators) - the Administrators user group located on the SERG computer has the Administrators profile and has Full Control access to the folder.
Users (SERG \ Users)- the Users group of users located on the SERG computer has the Users profile and has this access: Read and Execute (you can read and execute the contents of the folder), List of the contents of the folder (you can see the list of files and subfolders), and Read "(You can read the attributes of files and subfolders).
CREATOR-OWNER - built-in profile for additional security management of the owner of the folder.
Everything - a built-in profile that determines the access level of other users, not only your computer, but also users on the local network.
Fuhhh. Well, at the first stage, this knowledge is enough to create a folder isolated from all users on the computer. Now do the following:
Well, we have finished creating a folder that only you have access to!
Now about the rules for working with such a system:
Install ALL programs without exception in the administrator account.
Methods:
1. Go to your account and install the program.
2. Right-click on the installation file (it can be called: setup.exe, install.exe, in short, it must have the .exe extension), select the menu item “Run as ...” and select / enter the account name in the window that appears. administrator entries and password. T.O. The file is run as a computer administrator with full privileges.
So check out our security system.
Here's what the installation program told me when I started the installation of the ACDSee 8.0 image viewer:
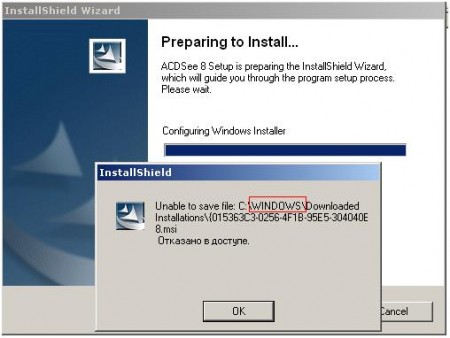
Yyyy :). He tried to write the file to the WINDOWS directory. Oops! :) There it was. Writing something to us is prohibited. It works.
And here is what the installation program told me when I tried to install the program for creating and viewing flash-animation on my own behalf:

Not bad, right? :)
2. Well, we can check the ban on changing system files ourselves if you go to the WINDOWS folder and try to delete that thread. Same thing with the Program Files folder.
3. And here is how it swears :) the system came to me when I tried to delete the system process. You can terminate processes running ONLY on your behalf. Here is an iChat for example, I can finish :):

4. Checking the implementation of the process is complicated. It is necessary to write a program, but believe the word. It is working.
author of the original article: Chris Kaspersky
So before you start telling you how to configure the OS from the intrusions of sinister viruses, worms and other infections spreading both through the Internet and through all kinds of media. What will I get after building this security system:
+ restriction of access to the system for running programs;
+ ban on changing system files;
+ ban on changing both system and application programs in memory;
+ ban on implementation in other processes;
+ to differentiate access between users of one computer;
This method of protection has many other small advantages, but this is already a consequence of these four.
I am using OS: Windows XP Professional. This is important, because for example, in the Home Edition there are no tools for managing user groups and security systems.
So, let's start with:
I. First you need to create an administrator account and create (preferably) a password for it (if it has not been created yet). Although during installation, the system creates a built-in account with the name “Administrator” by default, but I immediately create a name for it, for example, “admin”.
I hope that you already have the system installed and you need to create an account:
Go to Start> Settings> Control Panel> User Accounts:

Create an account ...

Call it “admin”, for example ...

And select the type of account “Computer administrator ".
ATTENTION!!! I had a case when, when creating such an administrator account, all the documents in the “My Documents” folder were lost and I couldn’t return them: '(. Unfortunately this is probably a flaw of the developers, so call me, I can’t help you here. So just in case, copy all your documents from this folder to the backup folder.
So the account has been created. Now put a password on it. Select the created account and click "Create Password":

Enter the password. All! We have created an administrator.
Now you need to create an account for us. Those. the one in which we will constantly work:
1. Click again “Create an account”.
2. Enter a name, for example, "user".
3. Set the type of account “Limited account”.
4. If you want, you can put a password on it (if you do not want other users of this computer to log into your account).
The platform is created. In principle, you can stop at this stage if you do not store any very important documents (passwords, reports, important literature), but if there is one, I recommend reading this article to the end.
II. If you read this line, it means that you are not indifferent to the fate of your information accumulated in the computer. So what do I want to do now? :):
+ Create a folder in which all my documents will be stored and access to which I can ONLY get and no one else (even the system will not have access to my folder!);
1. So we exit the current user profile and go to the newly created "user".
2. Go to the drive on which we want to create this folder.
WARNING!!! To create a folder of this type, you must have a disk running the NTFS file system! If the disk has a FAT32 file system, then this option to create a folder will not be available :(. This is due to the different structure of file systems and their application.
If your disk works with NTFS, then rejoice - you can read on :).
3. Now we will configure full access to security properties, as By default, it is simple. Go to Tools> Folder Options ...> View. And uncheck the option “Use simple file sharing”:

OK.
Now the Security tab has become available to us. To check this, right-click on any folder and select "Properties":

If this tab! all of a sudden! unavailable, it means your disk works with the FAT32 file system or with any other than NTFS.
At this stage, you can safely build what was planned, well, well:
1. Go to the drive of your choice (I have 2 drives C and D working with NTFS. I will create a folder on drive C).
2. Create a folder and call it somehow, well, for example, “mydocs”.
3. Now go to the folder properties. Open the tab "Security". And we see something like this:

Everything that is in the “Security” tab may differ! This is due to where to create the folder. If you create a folder on the disk where your OS is installed (where the WINDOWS. C: \ WINDOWS folder is located). If the folder is created on the disk where the OS is installed, the picture will be like this: FIGURE 1.
If the folder is created on the disk where there is no OS, the picture may be like this: FIGURE 2.
But do not be afraid, there is nothing to worry about.
From now on, let's take a closer look at all the elements of the "Groups or Users" list.
This list shows all users and user groups that have access to this folder. For example, I have these lines:
sergey (SERG \ sergey) - sergey user located on a computer with the name SERG and having a profile called sergey has “Special permissions”.
SYSTEM is a built-in profile for the system that I have "Full access to this folder."
Administrators (SERG \ Administrators) - the Administrators user group located on the SERG computer has the Administrators profile and has Full Control access to the folder.
Users (SERG \ Users)- the Users group of users located on the SERG computer has the Users profile and has this access: Read and Execute (you can read and execute the contents of the folder), List of the contents of the folder (you can see the list of files and subfolders), and Read "(You can read the attributes of files and subfolders).
CREATOR-OWNER - built-in profile for additional security management of the owner of the folder.
Everything - a built-in profile that determines the access level of other users, not only your computer, but also users on the local network.
Fuhhh. Well, at the first stage, this knowledge is enough to create a folder isolated from all users on the computer. Now do the following:
| If the folder is created on the disk where the OS is installed | If the folder is created on a disk where there is no OS |
 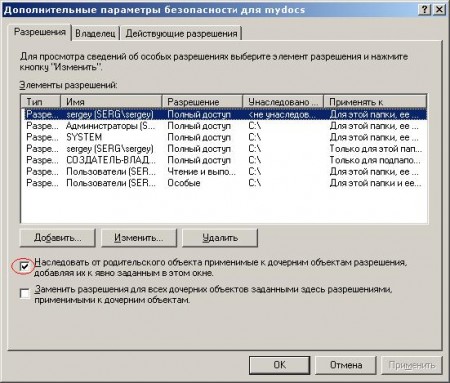 Uncheck the box "Inherit from the parent ...". And click on the “Delete” button in the window that appears:  Now in the “Advanced Security Settings for mydocs” window, click “OK”. Here's what you should get: 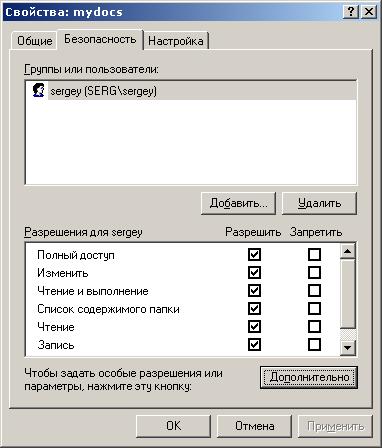 Well, that’s it! :) It seems not so difficult. |  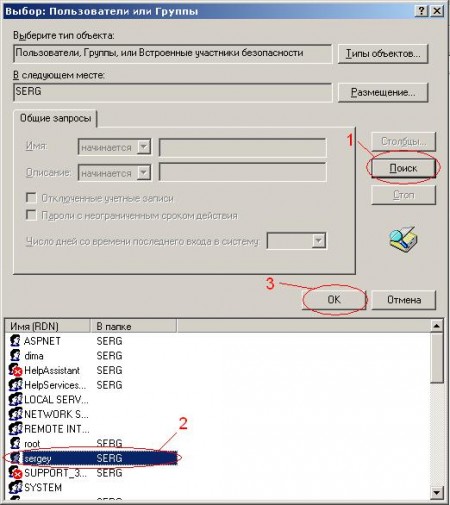 Here we select our profile (Name (RDN)). Find your account name here. If they called uch. record with the name "user", then look for "user". I called my sergey, so I choose sergey.  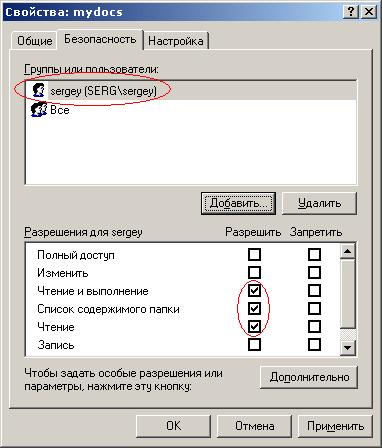 Now we have added the user (I have "sergey") with these permissions. But we need that only we have access to this folder (even the administrator will not be able to access this folder). We do the following:   Here we go to the heart of the security profile for this folder :). Do not be alarmed. I’ll explain what I’m not going to do, because this is the topic of an entire article or two :). Just uncheck the box "Inherit from the parent object applicable to the child ...". The following window will appear: 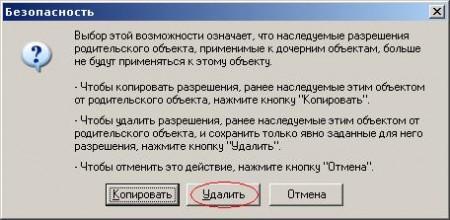 Click "Delete." Now in the "Advanced Security Settings for mydocs" window, click "OK." Here's what you should get: 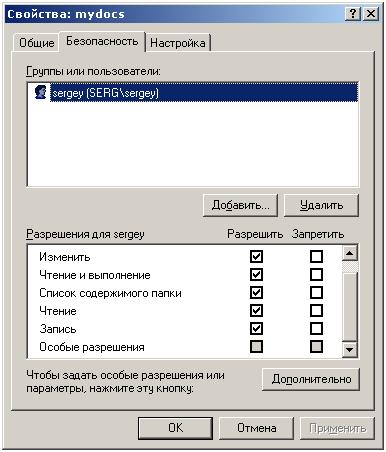 One record should remain. That's all! Fuhhh. Managed :). |
Well, we have finished creating a folder that only you have access to!
Now about the rules for working with such a system:
Install ALL programs without exception in the administrator account.
Methods:
1. Go to your account and install the program.
2. Right-click on the installation file (it can be called: setup.exe, install.exe, in short, it must have the .exe extension), select the menu item “Run as ...” and select / enter the account name in the window that appears. administrator entries and password. T.O. The file is run as a computer administrator with full privileges.
So check out our security system.
Here's what the installation program told me when I started the installation of the ACDSee 8.0 image viewer:

Yyyy :). He tried to write the file to the WINDOWS directory. Oops! :) There it was. Writing something to us is prohibited. It works.
And here is what the installation program told me when I tried to install the program for creating and viewing flash-animation on my own behalf:

Not bad, right? :)
2. Well, we can check the ban on changing system files ourselves if you go to the WINDOWS folder and try to delete that thread. Same thing with the Program Files folder.
3. And here is how it swears :) the system came to me when I tried to delete the system process. You can terminate processes running ONLY on your behalf. Here is an iChat for example, I can finish :):

4. Checking the implementation of the process is complicated. It is necessary to write a program, but believe the word. It is working.
author of the original article: Chris Kaspersky
