Time does not wait: than Windows 10 Timeline can be useful to the criminalist

When investigating incidents and virus attacks to reconstruct events that occur on a user's computer, forensics often use different types of timelines. As a rule, the timeline is a huge text file or table, in which, in chronological order, information is provided about events that occurred on the computer.
Processing media for timeline preparation (for example, using Plaso) is a time-consuming process. Therefore, computer forensics were very happy to learn that in the next update of Windows 10 there was a new functionality - Windows 10 Timeline.
“When I first found out about the new Windows feature, I thought,“ Great! Now you don’t have to waste time generating timelines. ” However, as it turned out, my joy was premature, ”said Igor Mikhailov, a specialist in the Laboratory of Computer Forensics Group-IB. Especially for Habr readers, Igor tells how Windows 10 Timeline - a new type of Windows 10 artifacts - has to do with traditional types of timeline and what information it contains.
Posted by Igor Mikhailov , Specialist, Laboratory of Computer Forensics Group-IB.
As already mentioned, in the April 2018 update in Windows 10, a new functionality appeared, called “Task View” (Windows 10 Timeline, or Timeline for short). It allows you to view the activity of a computer user and quickly return to documents and programs that were previously opened, to videos and pictures that were previously viewed, to websites. In order to open Windows 10 Timeline, click on the following icon:

After that, thumbnails of programs, documents and sites that opened on the current day or some time ago will become available:

Researchers noted two features of the new functionality:
- opening of some applications does not appear in Timeline
- some data from Timeline (earlier data) is transferred to Microsoft Cloud
Thus, the information that can be obtained using the analysis of Windows 10 Timeline differs from the usual types of timelines, which contain more complete information about events that occur on the analyzed computer.
Windows 10 Timeline should not be confused with timelines created by forensic utilities . For example, timelines created by Autopsy, Belkasoft Evidence Center, AXIOM, contain significantly more records about the various actions of the user of the computer under study compared to Windows 10 Timeline.
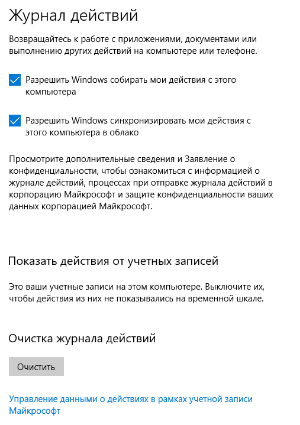
To activate Windows 10 Timeline, a computer user needs to go to the "Settings" section of the operating system, select the "Privacy" category and the "Activity log" subcategory, and then check the boxes opposite:
- allow Windows to collect my actions from this computer
- Allow Windows to sync my actions from this computer to the cloud
Windows 10 Timeline forensic artifact locations
In the Users \% profile name% \ AppData \ Local \ ConnectedDevicesPlatform \ directory , there is a file with the .cpd extension , which contains information about the time of the last Windows 10 Timeline synchronization with the cloud ( CNCNotificationUriLastSynced ) and about the user ID (in the illustration it is 0b5569b899437c21 ).
Catalog view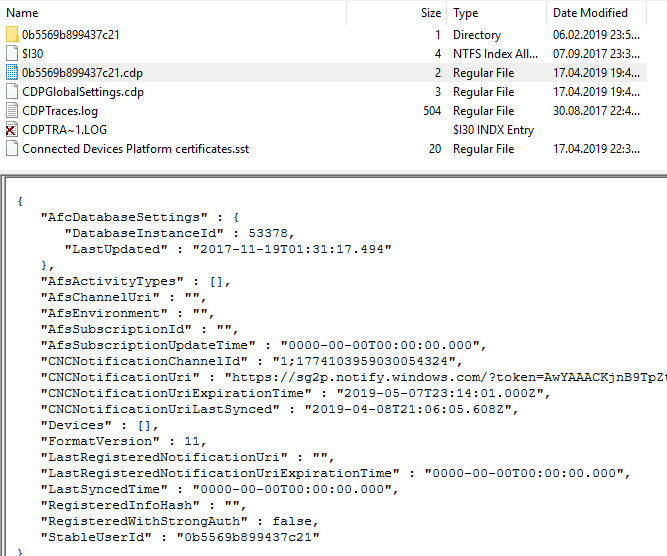

Information about user activity in the Windows 10 Timeline is stored in the ActivitiesCache.db file along the path: \ Users \% profile name% \ AppData \ Local \ ConnectedDevicesPlatform \ L.% profile name% \ .
ActivitiesCache.db File
The ActivitiesCache.db file is a SQLite database (version 3). As with any SQLite database, it is characterized by the presence of two auxiliary files, ActivitiesCache.db-shm and ActivitiesCache.db-wal .

Additional information about deleted records may be contained in unused table space, freelists and wal-files.
Anatomy of Windows 10 Timeline
ActivitiesCache.db contains the following tables: Activity , Activity_PackageId , ActivityAssetCache , ActivityOperation , AppSettings , ManualSequence , Metadata . Of greatest interest to the researcher are the tables Activity_PackageId and Activity ).
Activity_PackageId table

The Activity_PackageId table contains entries for applications that include paths for executable files (for example ... c: \ programdata \ firefly studios \ s tronghold kingdoms \ 2.0.32.1 \ strongholdkingdoms.exe ... ), names of executable files, and also the expiration time for these entries. The values in the Expiration Time column are stored in the Epoch Time format.
Entries in the Activity_PackageId table are stored for 30 days and may contain information about executable files or documents that are already missing on the hard drive under investigation.
Activity table

Table Activity contains the following fields: Id, AppId, PackageIdHash, AppActivityId , ActivityType, ActivityStatus, ParentActivityId, Tag, Group, MatchId, LastModifiedTime, ExpirationTime, Payload, Priority, IsLocalOnly, PlatformDeviceId, CreatedInCloud, StartTime, EndTime, LastModifiedOnClient, GroupAppActivityId, ClipboardPayload , EnterpriseId, OriginalLastModifiedOnClient, ETag.
It contains as many as five timestamp fields: LastModifiedTime, ExpirationTime, StartTime, EndTime, LastModifiedOnClient (this field can be empty - it is filled if the file in question in this table entry has been modified by a computer user).
You can also find paths to executable files in this table: ... "F: \\ NirSoft \\ x64 \\ USBDeview.exe ...
Gary Hunter (pr3cur50r) in the article “Windows 10 Timeline - Initial Review of Forensic Artefacts” indicates that timestamp values are not changed for deleted files. For modified documents, the timestamp values do not change immediately, but within 24 hours.
Study Windows 10 Timeline
The easiest way to view the data contained in the ActivitiesCache.db file is to use the SQLite database viewer. For example, the free DB Browser for SQLite utility.

Moving through the tables in the Browse Data tab, you can view their contents and record information that would be interesting during a specific study.
The second utility we recommend is WxTCmd (Windows 10 Timeline database parser). This utility is run from the command line.

As a result of its work, a csv file is created containing the results of the analysis of the ActivitiesCache.db file .
View of this file open in Excel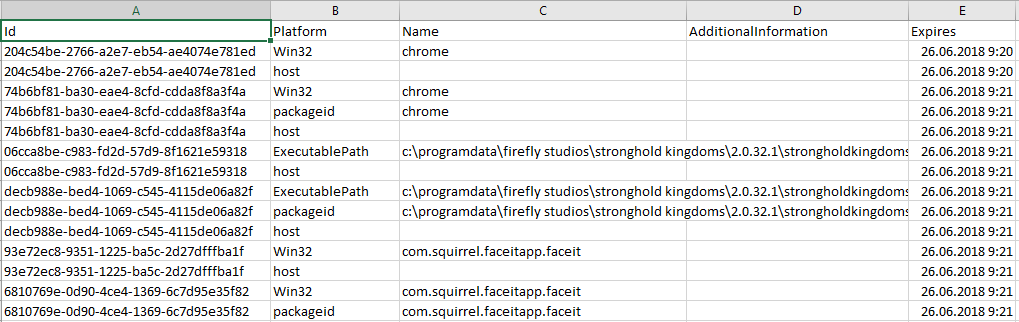

The third utility we recommend is Magnet Forensics ' AXIOM .
In order for the program to analyze this artifact, you must tell the program to do this in the "Select artifacts to include in case" section.
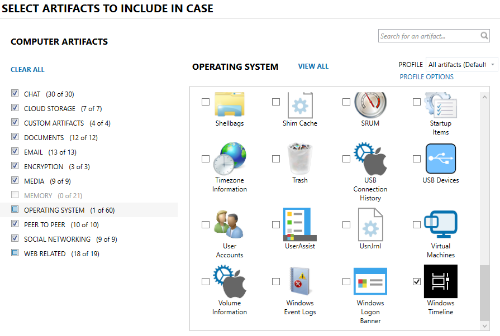
File analysis results can be viewed in Magnet AXIOM Examiner.
Results of extracting data from ActivitiesCache.db by AXIOM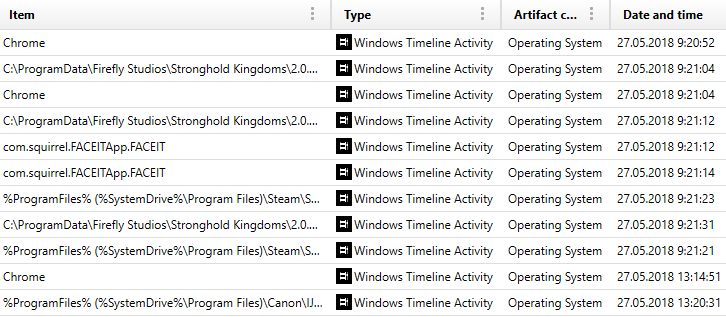

The fourth utility that we recommend for analyzing such files is Belkasoft's Belkasoft Evidence Center .
After adding a data source (hard disk, logical drive, directory or file) in the Add data source window , in the System Files section , select Windows Timeline .

After the data extraction is completed, the Windows Timeline category will appear in the Overview tab , in which the results of data extraction from the ActivitiesCache.db file will be displayed .
What the data retrieval looks like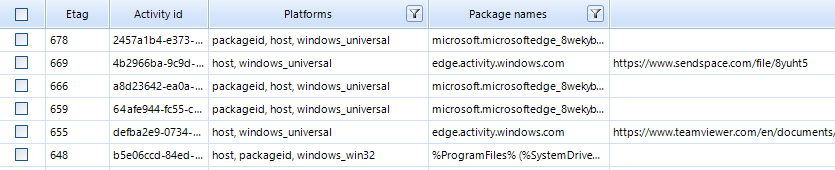

Windows 10 Timeline in Computer Forensics: Putting It into Practice
Data contained in the Windows 10 Timeline can be used to investigate incidents or data leaks.
As an example, we will show a fragment of data from an ActivitiesCache.db file from a computer that was attacked by hackers:
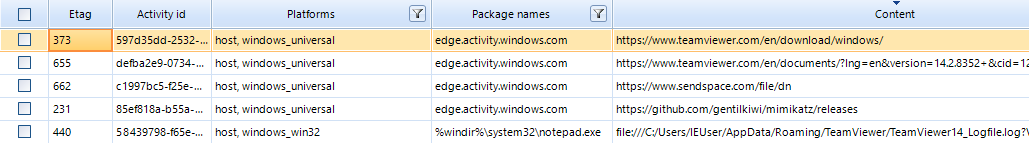
As you can see from the screenshot, the attackers downloaded TeamViewer victims, a file from sendspace.com file sharing service, Mimikatz. An analysis of the events saved in the Windows 10 Timeline shows that the attackers opened Notepad (file notepad.exe ) Teamviewer logs (file TeamViewer14_Logfile.log ) using Notepad . Perhaps in order to delete or modify the information in this file.
Here is another example. Apparently, very unusual files were launched on the computer. Probably someone was trying to collect information about the computer user.

Thus, a new category of artifacts that appeared in Windows 10, namely Windows 10 Timeline, simplifies the researcher’s work when reconstructing events that have occurred on the computer under study in the last 30 days. Also, Windows 10 Timeline can provide additional information about files that were run on the computer under study, including deleted ones. This is especially important when investigating incidents or data leaks.
