What is wrong with the federal law “On Electronic Signatures” (63-FZ), and how to fix it

A drawing machine at work, © axisdraw.com
An electronic signature in Russia first appeared in January 2002, along with the adoption of the first Law on Electronic Digital Signature ( 1-ФЗ ). Then, 9 years later, in April 2011, a new law “On Electronic Signatures” ( 63-FZ ) appeared. After another 8 years, in the beginning of the summer of 2019, chilling publications began to appear in the media about how they steal apartments using electronic signatures , how fraudsters register fictitious companies for unsuspecting citizens , and so on and so forth .
Let’s try to understand the existing problems without unnecessary emotions and think about how to fix them.
Content
- Foreword
- Part 1 - Legislation Issues
- Problem No. 1 - Identification of Clients by Certification Authorities
- Problem No. 2 - Restricting the Use of Electronic Signatures
- Issue 3 - Received Electronic Signature Release Notice
- Problem No. 4 - Rules for Using CIPF
- Problem No. 5 - Standardization of Electronic Signature
- Issue 6 - Old Signatures
- Problem number 7 - "attack back to the future"
- Part 2 - working on bugs
- Afterword
- Additional materials
Foreword
- This article will only focus on enhanced qualified electronic signatures (hereinafter referred to as electronic signature).
- Wherever certification authorities are referred to, they are accredited certification authorities.
- To simplify the perception, the article partially uses “popular” terms instead of strict legal concepts.
Part 1 - Legislation Issues
Problem No. 1 - Identification of Clients by Certification Authorities

© Yandex.Pictures
From the point of view of information security, all the incidents listed at the beginning of the article occurred as a result of insufficient identification by the employees of certification centers of their clients . But why is this happening in organizations that require the FSB license of Russia and accreditation from the Ministry of Communications for their work ?
The answer is simple: certification authorities earn from the number of electronic signatures sold. Tighter customer identification procedures will reduce their profits.
All people want everything to be simple, fast, free and effortless. When such a person contacts the certification center, he wants to instantly receive an electronic signature, so that they would not be stolen, and without any passwords or other nonsense. The person receiving the signature, as a rule, receives it not for himself, but for the director or accountant of the company where he works. In addition to obtaining a signature, a person has a lot of things to do. If a person is told that the power of attorney by which he wants to receive a signature must be notarized, then the person considers this a terrible bureaucracy. Next time, when a person wants to get a new electronic signature, he will try to apply to another, more “client-oriented” certification center.
Thus, we get a situation when it is not profitable to be the right certification center conducting strict customer identification. There will always be another certifying center related to this issue less reverently, which will attract lazy customers.
Issuing fake certificates by cybercriminals is not a problem of any particular certification center, but a systemic crisis of the level of federal legislation. You can say even more - this is a global problem (examples here and here ) of the PKI technology itself , which underlies the law.
Problem No. 2 - Restricting the Use of Electronic Signatures

Electronic signatures, like any other technology, undergo certain development cycles. The current law “On electronic signatures” is the law of the stage of technology popularization (electronic signatures are already used by society, but their penetration is still far from universal). As a consequence of this, the law is more oriented towards mass character than the security of electronic signatures.
The only mechanism for restricting the use of electronic signatures is given in paragraph 4 of Art. 11 63-FZ. It states, in particular, that a qualified electronic signature must be used in accordance with the restrictions specified in the signature key certificate. Unfortunately, this wording does not completely prohibit the issuance and use of an electronic signature, as a result of which citizens who have never issued it suffer from an electronic signature (for example, victims of incidents cited at the beginning of the article).
Particularly acute problem of restrictions on the use of electronic signatures concerns officials.
At the moment, they are forced to sacrifice personal security for the sake of the interests of the employer. This, in particular, is manifested in the fact that the electronic signature issued to them to meet the needs of the company can be used against their personal interests, for example, for illegally re-registering an apartment in Rosreestr.
The problem is compounded by the fact that the number of people who may have access to an electronic signature of an official is difficult to limit and practically does not depend on the will of the owner of the signature. Examples of people who may be made available to an electronic signature of an official include:
- administrators of cryptographic information protection means (CIP), responsible for issuing cryptographic keys, including electronic signature keys;
- IT workers setting up information systems to use electronic signatures;
- auditors conducting an audit of the organization (for example, pentesters);
- employees of state control bodies carrying out control measures in relation to the organization;
- law enforcement officers conducting operational investigative measures against the employer company;
- a team of bankruptcy managers who manage the company if it has initiated bankruptcy proceedings;
- and, sadly, other persons.
Issue 3 - Received Electronic Signature Release Notice

(c) m / f “Troy iz Prostokvashino”
Incidents with the unauthorized use of electronic signatures are in essence very similar to cyber thefts carried out by cybercriminals through the “Internet client-bank” system. In both cases, the attackers, having seized the victim’s authentication information, illegally carried out legally significant actions on her behalf: they removed money from the account, obtained loans, registered one-day firms, etc.
One of the effective ways to reduce the damage from cyber thefts was to provide banks Opportunities for their customers to fight for their own security. Any client using the service of notification on account transactions (for example, SMS-informing) can independently detect an unauthorized operation and block the account to minimize damage.
The current Law on Electronic Signatures does not provide such forms of protection. There are no mechanisms for notifying the owner of the issue of electronic signatures in his name.
Problem No. 4 - Rules for Using CIPF

(c) Yandex.Pictures
The current legislative framework governing the use of electronic signatures contains a security requirement, which, ultimately, could have the opposite effect and set a precedent for challenging signatures. Let's take it in order.
P.p. 2. Clause 4, Article 5 63-ФЗ establishes the requirements for a qualified electronic signature: "electronic signature means are used to create and verify an electronic signature, having confirmation of compliance with the requirements established in accordance with this Federal Law."
The specified requirements for electronic signature are defined in the Order of the Federal Security Service of the Russian Federation of December 27, 2011 N 796. Paragraph 6 of this document states that electronic signature means (and this is a cryptographic information protection measure) should be operated in accordance with PKZ-2005 . There, in turn, it was recorded that electronic signature means (CIP) should be operated in accordance with the rules for using them (technical documentation) .
This immediately raises the question of whether an electronic signature will be considered qualified if it is made using a certified cryptographic information protection certificate, which is not operated in full compliance with the terms of use (technical documentation).
The legislation does not contain a definite answer to this question. Consequently, given the competitiveness of the Russian proceedings, in similar cases, diametrically opposed decisions will be made, which ultimately can lead to a decrease in confidence in the electronic signature, and will make it more vulnerable to attacks of repudiation.
To illustrate this problem, we consider the situation that often arises when qualified certificates of signature keys are received at certification centers. Its essence is that the validity period of the certificate can be determined at 5 years, and the validity period of the private key (extension PrivateKeyUsagePeriod OID 2.5.29.16) at 1 year and 3 months. The question arises whether an electronic signature created for the 3rd year of existence of such a certificate will be recognized as qualified.
Problem No. 5 - Standardization of Electronic Signature

(c) Yandex.Pictures
If you have ever encountered the configuration of computers for the implementation of legally significant electronic document management with the state. organs, you probably remember the hell that arises. Juggling versions of crypto providers, browsers and plugins, as a result of which the system starts to work somehow, does not lend itself to a scientific explanation. This action is more like a shaman’s dance invoking the spirits of a storm, earth and fire at a night fire.
At the same time, the joy of a successful setup is quickly replaced by a terrible depression when it turns out that the employee for whom the setup was performed needs to send reports to another state. organ. And then there is its own cryptographic information protection system, its own keys and, in general, its own. Well, of course, the cherry on the cake is the fact that two certified cryptographic information protection certificates on one computer, in principle, do not get along.
Thus, the lack of standardization and compatibility between cryptographic information protection systems used to generate and verify qualified electronic signatures can be safely added to the problems of the current law.
Decree of the Government of the Russian Federation of 09.02.2012 N 111 “On the electronic signature used by executive authorities and local authorities in organizing electronic interaction among themselves, on the procedure for its use, as well as on establishing requirements for ensuring the compatibility of electronic signature means” does not count, since it applies only to interagency cooperation, and in fact does not give any specifics.
Issue 6 - Old Signatures

(c) Yandex.Pictures
Let's ask ourselves what will happen to a document signed with an electronic signature in 30 years, and in 100 years? Where are the dates from? It's simple: real estate transactions are characterized by long-term ownership of property. That is why 30 years and 100 years is not the limit. For example, Alexander II sold Alaska to America in 1867, that is, 152 years ago.
But back to the electronic signature. From the point of view of technology, its strength is based on the mathematical properties of the cryptographic algorithms underlying it. At the same time, the stability of the algorithms themselves is based only on ignorance of effective methods of hacking them. Far from the fact that these methods are not, or that they will not appear after 37 minutes. For example, in the era of the sale of Alaska, the Vigenenera codeIt was considered invulnerable, and now students are breaking it at the first cryptography laboratories.
The current stack of cryptographic algorithms used for electronic signature in Russia is based on GOST R 34.10-2012 , GOST R 34.11-2012 , GOST 34.12-2015 and an unlimited number of recommendations for standardization and satellite algorithms . What will happen to them in 30 years? It is believed that not everything is great with them right now .
The vulnerability problem in algorithms and electronic signatures is not purely hypothetical. World practice has already faced similar things, for example, the ROCA vulnerability .
Thus, another problem of the law is the lack of regulation aimed at maintaining the long-term legal significance of electronic documents.
Problem number 7 - "attack back to the future"

(c) Alexander Rowe’s film tales
This attack is perhaps an aspen stake in the heart of electronic document management, which uses only an electronic signature to certify documents.
The problem is that, by manipulating the date of formation of the electronic signature, the attacker can achieve both the recognition of a fake signature and the denial of legitimacy.
Example 1 - recognition of a fake signature
There was Yaropolk and he led the artel of overseas stone craftsmen. At the request of his customer, Vsevolod, he decided to simplify the exchange of damned paper and issued himself a qualified certificate of electronic signature.
Yaropolk and Vsevolod agreed that instead of hand-written paper parchments, they will send by e-mail files to each other, compiled in MS Word and electronically signed with CryptoPro software and certified by CryptoARM. On the instructions of the magi, including those who know it, they decided to write the date of signing the documents in electronic files before they are certified.

We wrote all this down on parchment and sealed it with our signatures, calling this document the “Electronic Document Management Agreement”.
How long, how short they worked according to this scheme. But then greed squeezed by a toad heavy chest Vsevolod, casting dark thoughts that he pays Yaropolk too expensive. Bitter thoughts began to plague Vsevolod in different ways: sleep deprivation, but spoiled the mood.
Vsevolod decided with his grief to turn to the local witch doctor, whom Baba Yaga called. That for a fee, Vsevolod generously thought over the private key of electronic signature from Yaropolk to steal. As you know, that key was contained in an overseas device, an egg resembling (USB token), constantly stuck in the back of the computer.
For the plan of his cunning, Vsevolod hired a brown-eyed harlot, so that she spoils Yaropolk’s mind with her amorous spells and bothers to go to the distant kingdom.
While traveling overseas Yaropolk with a harlot had fun, Vsevolod secretly crept into the white stone chambers and a device resembling an egg containing Yaropolk’s key, he pulled it out of the back of the computer and ran away with it.
But Vsevolod did not know that before leaving for his Yaropolk, he asked the guard to put his charms on his chambers. Those spells worked and sent a signal to the city squad. Arriving at the place and not finding the villains of fierce, the warriors of Yaropolk’s servants called in to check if any good was stolen. The clerk of Yaropolk discovered the disappearance of the "egg" of the treasured key containing the electronic signature. Mindful of the covenants of the Magi, he immediately turned to the masters that they had made the “egg” so that they could destroy the “eggs” with their spells. Masters, following the precepts of their ancestors, added Yaropolk’s electronic signature certificate to the list of revoked certificates and ordered that Yaropolk not use the “egg”, even if it is found, and that he would come for a new “egg” to them, get a new electronic signature .
Vsevolod learned all this and became even more sad. He went with heavy thoughts to Baba Yaga for wise advice. Learning about Vsevolod’s grief, Baba Yaga rolled up with an evil laughter and, breaking through, said: “This is not a problem! And you need to do the following:
Vsevolod did just that and through the court took the money from Yaropolk apparently not visible.
Since, according to paragraph 2 of Art. 11 63-ФЗ : “A qualified electronic signature shall be deemed valid ... while observing the following conditions: ... a qualified certificate is valid at the time of signing the electronic document (if there is reliable information about the moment of signing the electronic document) or on the day of verification of the validity of the specified certificate, if the moment of signing the electronic the document is not defined; "the document was fake, compiled by Vsevolod, the judge was qualified as a judge, since he was certified with the signature of Yaropolk, and the date of formation of the signature with the period when the signature was valid coincided. Yaropolk couldn’t challenge this damned date, because according to all the rules of the “Agreement on electronic document management” it was set.
Yaropolk and Vsevolod agreed that instead of hand-written paper parchments, they will send by e-mail files to each other, compiled in MS Word and electronically signed with CryptoPro software and certified by CryptoARM. On the instructions of the magi, including those who know it, they decided to write the date of signing the documents in electronic files before they are certified.

We wrote all this down on parchment and sealed it with our signatures, calling this document the “Electronic Document Management Agreement”.
How long, how short they worked according to this scheme. But then greed squeezed by a toad heavy chest Vsevolod, casting dark thoughts that he pays Yaropolk too expensive. Bitter thoughts began to plague Vsevolod in different ways: sleep deprivation, but spoiled the mood.
Vsevolod decided with his grief to turn to the local witch doctor, whom Baba Yaga called. That for a fee, Vsevolod generously thought over the private key of electronic signature from Yaropolk to steal. As you know, that key was contained in an overseas device, an egg resembling (USB token), constantly stuck in the back of the computer.
For the plan of his cunning, Vsevolod hired a brown-eyed harlot, so that she spoils Yaropolk’s mind with her amorous spells and bothers to go to the distant kingdom.
While traveling overseas Yaropolk with a harlot had fun, Vsevolod secretly crept into the white stone chambers and a device resembling an egg containing Yaropolk’s key, he pulled it out of the back of the computer and ran away with it.
But Vsevolod did not know that before leaving for his Yaropolk, he asked the guard to put his charms on his chambers. Those spells worked and sent a signal to the city squad. Arriving at the place and not finding the villains of fierce, the warriors of Yaropolk’s servants called in to check if any good was stolen. The clerk of Yaropolk discovered the disappearance of the "egg" of the treasured key containing the electronic signature. Mindful of the covenants of the Magi, he immediately turned to the masters that they had made the “egg” so that they could destroy the “eggs” with their spells. Masters, following the precepts of their ancestors, added Yaropolk’s electronic signature certificate to the list of revoked certificates and ordered that Yaropolk not use the “egg”, even if it is found, and that he would come for a new “egg” to them, get a new electronic signature .
Vsevolod learned all this and became even more sad. He went with heavy thoughts to Baba Yaga for wise advice. Learning about Vsevolod’s grief, Baba Yaga rolled up with an evil laughter and, breaking through, said: “This is not a problem! And you need to do the following:
- Start your computer and translate the date three months ago when the key of Yaropolk was still in effect.
- Compose a new document and write in it that Yaropolk took a lot of money from you and undertakes to give it with interest in three months.
- As the date of signing the document, indicate the date that you will have on the computer.
- Sign this document with your electronic signature and the signature of Yaropolk. ”
Vsevolod did just that and through the court took the money from Yaropolk apparently not visible.
Since, according to paragraph 2 of Art. 11 63-ФЗ : “A qualified electronic signature shall be deemed valid ... while observing the following conditions: ... a qualified certificate is valid at the time of signing the electronic document (if there is reliable information about the moment of signing the electronic document) or on the day of verification of the validity of the specified certificate, if the moment of signing the electronic the document is not defined; "the document was fake, compiled by Vsevolod, the judge was qualified as a judge, since he was certified with the signature of Yaropolk, and the date of formation of the signature with the period when the signature was valid coincided. Yaropolk couldn’t challenge this damned date, because according to all the rules of the “Agreement on electronic document management” it was set.
Example 2 - denial of a legitimate signature
Frustrated by the terrible tragedy, worth a lot of money, Yaropolk decided to take revenge on Vsevolod, so much so that with the same coin, so that in fairness.
Yaropolk began to read the scripture containing Law 63-FZ. I read, I read ... and I fell asleep. And he dreamed of a magnificent husband, reminiscent of the face of Oleg Veshchevoy. That husband looked at the battlefield, where hordes of Basurman, who were defeated by their blood and smeared with blood, smeared the holy Russia, and delivered terrible speeches: “Whoever comes to us for what, that’s why ...”. In the morning, Yaropolk woke up in good health, for he now knew what he needed to do.
Yaropolk came to Vsevolod and said the word that, in spite of all the disagreements, the artisans of his family and small children, that they were ill without work, and proposed building white stone chambers together and on. Hearing this, Vsevolod rejoiced incredibly and said that he was not against continuing cooperation, but that he would pay in fairness, that is, two times less than the previous one.
Yaropolk accepted the offer, but said that the “Agreement on electronic document management” should be changed: the words about the date of signing of the documents should be ejected from there. He also added that since there will be half as much money for the work, it is necessary to give him an advance, and in cash, so that he can bring a building stone, and give part of the salary to the craftsmen. For the money received by the receipt, he will make a paperless, certified by electronic signature. They decided on that.
Vsevolod issued an advance to Yaropolk and received an electronic receipt in return.
After that, Yaropolk went to the masters that they made an “egg” with an electronic signature, and asked to make a new “egg”, since he had stolen old people together with his wallet in the gateway. The masters withdrew the old signature, but they gave out the "egg" with the new one.
A week passes, another, and Yaropolk does not even think of starting a job. Vsevolod became enraged and called Yaropolk to ask him for inaction. And Yaropolk says the word, saying that he never received an advance payment, there’s nothing to buy a building stone for. Vsevolod sensed something was amiss, but he again filed a lawsuit against Yaropolk.
During the hearing, Vsevolod presented the judge with a wise electronic receipt, certified by the signature of Yaropolk. To which Yaropolk replied: "The subscription that fake by dashing people is made up that the" egg "stole him."
To resolve the dispute of this complex, the judge asked the masters that the signature was issued to Yaropolk, the date of withdrawal of his signature by electronic, as well as the judge from Vsevolod, the original of the "Agreement on electronic document management".
Since the agreement did not contain words about what should be considered the date of signing the electronic document, and also, taking into account the fact that the parties did not agree on the fact of the signature and, accordingly, the date of its completion, the wise judge decided that the date of electronic signature of the electronic document not reliably determined.
After that he turned toп.2 ст. 11 63-ФЗ: «Квалифицированная электронная подпись признается действительной… при одновременном соблюдении следующих условий:… квалифицированный сертификат действителен на момент подписания электронного документа (при наличии достоверной информации о моменте подписания электронного документа) или на день проверки действительности указанного сертификата, если момент подписания электронного документа не определен».
На основании всего выше сказанного суд пришел к выводу, что электронная подпись под документом не действительна, так как дата подписания документа достоверно не определена, а на момент проверки подписи ее сертификат не действителен.
Yaropolk began to read the scripture containing Law 63-FZ. I read, I read ... and I fell asleep. And he dreamed of a magnificent husband, reminiscent of the face of Oleg Veshchevoy. That husband looked at the battlefield, where hordes of Basurman, who were defeated by their blood and smeared with blood, smeared the holy Russia, and delivered terrible speeches: “Whoever comes to us for what, that’s why ...”. In the morning, Yaropolk woke up in good health, for he now knew what he needed to do.
Yaropolk came to Vsevolod and said the word that, in spite of all the disagreements, the artisans of his family and small children, that they were ill without work, and proposed building white stone chambers together and on. Hearing this, Vsevolod rejoiced incredibly and said that he was not against continuing cooperation, but that he would pay in fairness, that is, two times less than the previous one.
Yaropolk accepted the offer, but said that the “Agreement on electronic document management” should be changed: the words about the date of signing of the documents should be ejected from there. He also added that since there will be half as much money for the work, it is necessary to give him an advance, and in cash, so that he can bring a building stone, and give part of the salary to the craftsmen. For the money received by the receipt, he will make a paperless, certified by electronic signature. They decided on that.
Vsevolod issued an advance to Yaropolk and received an electronic receipt in return.
After that, Yaropolk went to the masters that they made an “egg” with an electronic signature, and asked to make a new “egg”, since he had stolen old people together with his wallet in the gateway. The masters withdrew the old signature, but they gave out the "egg" with the new one.
A week passes, another, and Yaropolk does not even think of starting a job. Vsevolod became enraged and called Yaropolk to ask him for inaction. And Yaropolk says the word, saying that he never received an advance payment, there’s nothing to buy a building stone for. Vsevolod sensed something was amiss, but he again filed a lawsuit against Yaropolk.
During the hearing, Vsevolod presented the judge with a wise electronic receipt, certified by the signature of Yaropolk. To which Yaropolk replied: "The subscription that fake by dashing people is made up that the" egg "stole him."
To resolve the dispute of this complex, the judge asked the masters that the signature was issued to Yaropolk, the date of withdrawal of his signature by electronic, as well as the judge from Vsevolod, the original of the "Agreement on electronic document management".
Since the agreement did not contain words about what should be considered the date of signing the electronic document, and also, taking into account the fact that the parties did not agree on the fact of the signature and, accordingly, the date of its completion, the wise judge decided that the date of electronic signature of the electronic document not reliably determined.
After that he turned toп.2 ст. 11 63-ФЗ: «Квалифицированная электронная подпись признается действительной… при одновременном соблюдении следующих условий:… квалифицированный сертификат действителен на момент подписания электронного документа (при наличии достоверной информации о моменте подписания электронного документа) или на день проверки действительности указанного сертификата, если момент подписания электронного документа не определен».
На основании всего выше сказанного суд пришел к выводу, что электронная подпись под документом не действительна, так как дата подписания документа достоверно не определена, а на момент проверки подписи ее сертификат не действителен.
Часть 2 — работа над ошибками
Государство vs. удостоверяющие центры
Having heard about the problems of the law “On Electronic Signatures”, people first of all propose to abolish certification centers and transfer their functions to the state. One of the main arguments of the supporters of this point of view is that these “sharashkin offices” cannot ensure the security of the services provided and are themselves potential participants in conflicts of interest (they may unlawfully issue a third party signature and use it).
It should be noted that these thoughts are not without logic, but for making informed decisions, other nuances must be taken into account.
Economic aspects of interaction between the state and private business
The state in the era of the digital economy is a provider of infrastructure services that allow the economy to exist and develop. Globalization - the inevitable companion of the digitalization of the economy - will seriously aggravate competition between states. Investments and human capital will be directed to those countries whose public services are most effective.
To win the competition, the state, like business, needs investments. Where to get them?
Raising taxes is not an option, as this will lead to a decrease in the efficiency of state. services: the state will take more for the same work. Where else can I get the money?
The most promising investment options are public-private partnerships.and delegating part of state authority to business. Examples of such interactions include:
Thus, we come to the conclusion that the state must by all means maintain the involvement of private business in the implementation of its functions, be sure to ensure the proper level of their quality. Otherwise, such an interaction is more harmful than good, and it is better to abandon it.
An additional argument in favor of maintaining commercial certification centers as public institutions, oddly enough, is the human factor. The mere fact that a person serves in a government agency and does not work in a private company does not make him more honest and decent.
If a person did not identify the applicant for the issue of an electronic signature as an employee of a commercial certification center, then he will not do this as a civil servant. In order for the process to work, additional efforts are needed: competent labor motivation, ensuring control, etc. All these measures can be successfully implemented both in commercial companies and in government agencies - in general, there is no difference.
To win the competition, the state, like business, needs investments. Where to get them?
Raising taxes is not an option, as this will lead to a decrease in the efficiency of state. services: the state will take more for the same work. Where else can I get the money?
The most promising investment options are public-private partnerships.and delegating part of state authority to business. Examples of such interactions include:
- private security companies to which the state has delegated part of its security functions;
- certification centers to which the state has delegated part of its functions in creating an electronic trust space;
- owners of private video recording cameras of traffic violations, which, on the basis of concession agreements, are allowed to install cameras and earn money on fines for car drivers.
Thus, we come to the conclusion that the state must by all means maintain the involvement of private business in the implementation of its functions, be sure to ensure the proper level of their quality. Otherwise, such an interaction is more harmful than good, and it is better to abandon it.
An additional argument in favor of maintaining commercial certification centers as public institutions, oddly enough, is the human factor. The mere fact that a person serves in a government agency and does not work in a private company does not make him more honest and decent.
If a person did not identify the applicant for the issue of an electronic signature as an employee of a commercial certification center, then he will not do this as a civil servant. In order for the process to work, additional efforts are needed: competent labor motivation, ensuring control, etc. All these measures can be successfully implemented both in commercial companies and in government agencies - in general, there is no difference.
Based on the foregoing, in this article we will proceed from the assumption that commercial certification authorities will continue to issue electronic signatures.
Solution to Problem No. 1 (“Customer Identification by Certification Authorities”)
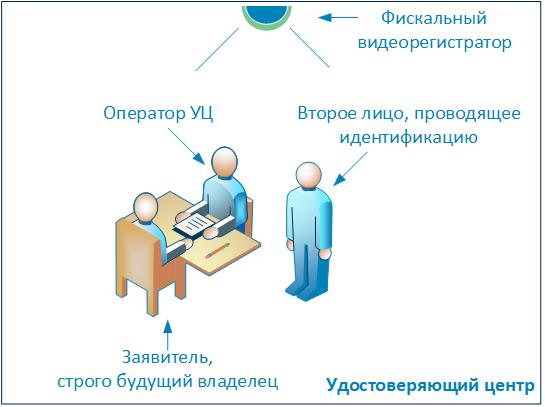
For an ordinary citizen, obtaining an electronic signature is equivalent to receiving a national passport. In fact, these are two almost equivalent identity cards, only the first for the real world, and the second for the “digital” one. Since the value of certificates is equal, then their protection should also be equivalent. In other words, an electronic signature must be issued as strictly as a passport .
But nevertheless, in comparison with the passport, the electronic signature has important differences:
- If a passport is issued for a long period (tens of years), then an electronic signature - for a short one, usually no more than a year and three months.
- Possession of a passport does not require special knowledge. Possession of an electronic signature requires. For example, when using an electronic signature often purely IT issues arise that require operational technical support.
- In order to use a stolen passport or electronic signature, an attacker must overcome their protection system, for example, re-stick a photo in a passport or crack a password on an electronic signature. At the same time, it is possible to determine that the attacker used the stolen passport according to the testimony of eyewitnesses or video surveillance records, but it is practically impossible to establish the fact of unlawful use of an electronic signature.
Passports issued by the Ministry of Internal Affairs of Russia. Following the principle of equal security discussed above, it turns out that it must also issue electronic signatures. However, it is impossible to do this within the existing structure of the Ministry of Internal Affairs of Russia:
- Firstly, because along with state functions (identification, accounting and control of identity cards, ...) the Ministry of Internal Affairs will need to perform purely IT functions: technical support, consultations, etc.
- Secondly, for the Ministry of Internal Affairs it will be necessary to organize the procurement of technical and cryptographic facilities on a massive scale, and this will be huge budget spending.
- Thirdly, the Ministry of Internal Affairs will need to significantly expand the staff, since the number of issued / revoked electronic signatures is significantly more than the same number of passports.
It mentions the Ministry of Internal Affairs of Russia, but the above reasoning will be true for any other state. structures. Like it or not, the state’s costs for transferring the functions of certification centers to any of its bodies will be gigantic. The real economic effect, expressed in reducing losses from economic crimes associated with the use of electronic signatures, is unlikely to be significant.
The best solution to the current problem is seen in improving the procedure for issuing electronic signatures. In particular, the following set of measures is proposed:
- Prohibition of issuing an electronic signature by proxy (passport by proxy cannot be obtained).
- Legislative adoption of a methodology for identifying applicants for electronic signatures, at least including:
- the presence of at least two people identifying the applicants with their own eyes (as in many banks when making deposits or loans);
- the existence of procedures for verifying the identity documents of the applicant for falsification.
- Mandatory recording of the applicant’s identification procedure with a fiscal video recorder (excluding the possibility of falsifying video recordings) and storage of records for 3 years (limitation period) from the date of expiration of the signature key certificate.
The main nuance of this set of measures will be the choice of a second person who identifies the applicant to issue an electronic signature. Consider several options that differ from each other by the expected reliability of identification and implementation costs. The second person to carry out the identification may be:
- Another employee of the certification center . The cheapest option with minimal security.
- Notary . A more expensive option with maximum security without the involvement of civil servants.
- Employee of the Ministry of Internal Affairs of Russia . The most expensive, safest option (if not they then who?).
The implementation of any of the proposed measures will inevitably lead to an increase in the cost of electronic signatures. This, unfortunately, is an inevitable evil.
Strengthening the procedure for identifying applicants for the issuance of electronic signatures, it is necessary to similarly strengthen both the procedures for issuing SIM cards and the procedure for authorizing accounts on the State Services portal.
Solution to problem No. 2 (“restriction of the use of electronic signatures”)

PKI technology does not contain ways to limit the issuance and use of electronic signatures. It was understood that if a person does not need it, then he simply does not draw it up. If the electronic signature was stolen, then its owner immediately contacts the certification center and asks to be blocked. Signing is blocked by adding the certificate of the verification key of the signature to the list of revoked certificates (certificate revocation list, hereinafter - CRL ) with the date and reason for blocking.
At the time of verification of the electronic signature under the document, the date of its formation is analyzed. If this date is later than or equal to the date of blocking, then the signature on such a document is invalid.
Thus, CRL is a central element of PKI technology responsible for trusting issued electronic signatures. There is no opportunity to influence “unreleased” electronic signatures via CRL.
Therefore, to correct the problem considered in the law, PKI technology needs to be further developed. Moreover, these improvements should be carried out taking into account backward compatibility with existing and working electronic document management systems.
If in classical PKI the trust tree grew from the root certification authority, then in the case of state PKI, the state is the central source of trust. It provides a trust infrastructure within which accredited certification authorities exist.
The state in the person of its authorized body should accept applications from citizens (for example, through the MFC or "State Services") containing restrictions on the issuance and restrictions on the use of electronic signatures. The received data should be consolidated in the state information resource - “The Unified Register of restrictions and prohibitions on the use of electronic signatures”.
At the level of the law, certification authorities must be obligated to verify this resource for established restrictions at the time of issuing an electronic signature.
If the registry prohibits the issuance of electronic signatures, then the certification center must refuse to issue applicants. If the registry contains restrictions on the use of electronic signatures, then they must be included in the issued certificate certificate key electronic signature.
About restrictions on the use of electronic signatures need to talk more.
The fact is that, despite the mention of them in paragraph 4 of Art. 11 63-FZ , in fact this mechanism is not working, since the current legislative framework does not contain documents disclosing the principle of its operation.
We will correct this drawback and consider one of the possible options for implementing restrictions on the use of electronic signatures.
The first step we need to develop a model that will describe the restrictions on the use of electronic signatures. The most appropriate for these purposes would be a discretionary access model described using access control lists ( ACLs ).
The access control list for electronic signature should contain a list of areas in which the electronic signature is allowed to be used for certification of documents or in which the signature is prohibited to use. The problem is what to consider these “areas”.
Ideally, this should be information systems within which electronic document management is conducted. But this ideal is unattainable, since it will require the creation and maintenance of a global registry of information systems within the state. If state or municipal information systems can still be taken into account somehow, then the information systems of commercial organizations are not amenable to accounting in principle - many companies themselves do not know which systems work for them.
As an alternative, you can distinguish between the use of electronic signatures at the level of subjects of legal relationships, that is, indicate in the electronic signature itself which companies (as well as individuals or state bodies) can use it and for which not. Legal entities can be identified using data from the Unified State Register of Legal Entities, for example, according to the combination of TIN and OGRN values. An individual can be identified by the combination of TIN and SNILS.
The above mechanism of access control (restrictions from the state registry) is global throughout the trust space formed by the state. The above restrictions must be taken into account by all certification authorities when issuing any electronic signatures.
When applying to the certification center, the applicant may impose additional (private) restrictions that narrow the scope of the use of electronic signatures. This will ensure the issuance of electronic signatures with different areas of action, which will be relevant for the protection of signatures of officials.
Setting global restrictions on the use of electronic signatures should give rise to the recall of all valid electronic signatures, the scope of which is beyond the scope of what is permitted.
Solution to Problem No. 3 (“receiving notice of electronic signature issue”)
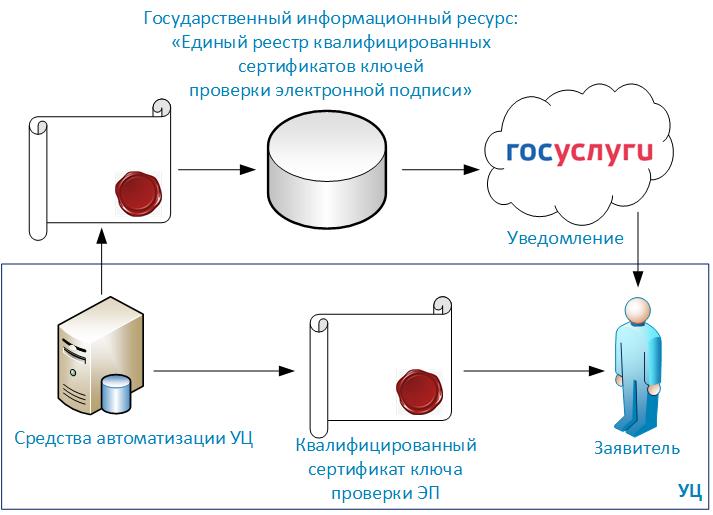
Informing citizens about the issue of electronic signatures on them is perhaps the simplest of all the tasks given in this article. It can be solved as follows:
- Certification authorities, issuing an electronic signature, send a copy of the certificate to the authorized state body.
- The authorized body consolidates all received certificates into the state information resource - “The Unified Register of Qualified Certificates of Electronic Signature Verification Keys”.
- Subjects of law: legal entities or individuals - will be able to find out about the issue of electronic signatures on them from the State Services portal. To improve the efficiency of the portal, you can make improvements to subscribe to notifications for these events.
Of course, not everyone has connected the State Services, but at the same time no one bothers to connect them, all the more there will be a good reason.
Solution to Problem No. 4 (“CPSI Use Rules”)

© Yandex.Pictures
Modern cryptographic information protection tools can provide adequate protection only if a number of strict restrictions are prescribed in the technical documentation. For example, for all cryptographic information protection tools running on a Windows-based computer, the requirement is set to clear the page file at shutdown. Failure to comply with this requirement leads to the risk of theft of electronic signature keys during periods when the computer is turned off.
To implement these requirements or not - entirely in the area of responsibility of the signatory. It is generally impossible to exercise proper state control (since the state is a trust provider) over its compliance with these requirements. But at the same time, if the signature has already been put, then the method of its formation should in no way affect its recognition and status.
Therefore, the legislative framework should be modernized in such a way as to minimize the risk of refusal to sign or change its status due to the action (or inaction) of the signatory. Such changes are long overdue, since the fundamental documents governing the use of cryptographic information protection measures ( PKZ-2005 , FAPSI 152 ) are already obsolete.
Solution to Problem No. 5 (“Standardization of Electronic Signature”)

© Yandex.Pictures
The standardization of electronic signature means should ensure that consumers do not care which standardized cryptographic information protection tool is used.
The standardization should be:
- Architecture and structure of CIPF.
- Прикладные программные интерфейсы (API), используемые для вызова функций СКЗИ и взаимодействия со средой функционирования криптосредства (СФК).
- Форматы ключевой информации, справочников открытых ключей, списков доверенных и отозванных сертификатов, входных и выходных сообщений.
- Ключевые носители.
- Сопутствующие алгоритмы и протоколы.
- Параметры криптоалгоритмов и протоколов.
At the moment, CIPFs are certified in 6 classes: KS1, KS2, KS2, KV1, KV2, KA1. Each class defines only threats that the cryptographic information protection system must confront, but does not establish any compatibility requirements. As a result, two cryptocurrencies, say, of class KC1 are absolutely incompatible with each other.
Accordingly, within the framework of standardization, CIPF profiles of the corresponding classes should be developed, but with restrictions on compatibility and with reference to a specific operating environment. For example, "Standardized cryptographic provider KC1, to work in the Windows 10 operating system."
Solving problems No. 6 (“old signatures”) and No. 7 (“attack back to the future”)

© Yandex.Pictures The
problems of “old” signatures, hacked cryptographic algorithms and fraud with the dates of signing documents cannot be solved only with the help of an electronic signature.
To eliminate these shortcomings, it is necessary to abstract from the banal use of electronic signatures and look at the problem from the point of view of legally significant electronic document management in general.
Here, the protection provided by the services of a trusted third party can be added to the protection provided by the electronic signature. Only with the help of these services it is possible to eliminate the indicated problems.
Examples of trusted third party services include:
- time stamp service, which allows you to reliably set the date of formation of the electronic signature
- служба гарантированной доставки сообщений, позволяющая достоверно установить факт передачи документов между участниками электронного документооборота;
- служба электронного нотариата, реализующая функции нотариуса, но применительно к электронным документам;
- служба архивации и длительного хранения электронных документов, позволяющая обеспечить юридическую значимость документа даже в условиях потери стойкости криптографических алгоритмов, используемых для формирования электронных подписей;
- и др.
Obviously, the use of these services will not be free. Their widespread introduction as mandatory requirements may adversely affect the popularization and mass use of legally significant electronic document management in the country's economy. Here, a differentiated approach is required, in which, depending on the importance of the signed documents, the mandatory use of these services is established. Examples of especially significant documents include documents on real estate transactions, court decisions, legislative acts, etc.
Afterword
So, we met with some of the problems in the current law “On Electronic Signatures”. There are many problems, but even in this article we were not able to consider all of them. We talked about only one, however, the most significant form of electronic signatures - a qualified enhanced electronic signature.
It is important to ask whether electronic signatures do more good than harm.
Subjectively, many citizens are distrusted by electronic signatures, considering that everything that is happening in the digital world can be easily faked. Partly right, but what is the alternative? Handwritten signature and paper documents?
If at the moment it became known about only two cases of theft of apartments using an electronic signature, then the number of similar thefts committed using traditional paper documents will exceed this number by a factor of a thousand.
Our idea of the durability of a handwritten signature is illusory and borders on self-deception. Not only can it be faked by any person with more or less developed fine motor skills of hands, so it can already be reproduced using a machine .
Unfortunately, there is no absolutely stable protection. This is true for both electronic and handwritten signatures.
The more massively the electronic signature will be used, the more often they will try to falsify it (it is illegal to use it). It's unavoidable. But still, the percentage of legitimate use of electronic signatures is significantly ahead of the percentage of illegal, and the positive effect of the law exceeds the negative.
It is important to quickly patch up “holes” in the legislation, constantly raising the bar of costs for cybercriminals to commit a crime. At the same time, the latches themselves must be easy to implement and effective.
Additional materials
- Directory of Russian legislation on information security - the basic laws and regulations governing information security in Russia, including an electronic signature.
- CIPF Threat Model - describes the threats with respect to CIPF and non-repudiation of the electronic signature.
- Natalia Khramtsova’s blog “Who does not go forward, goes back” - a lot of materials on issues of electronic signature and electronic document management.
