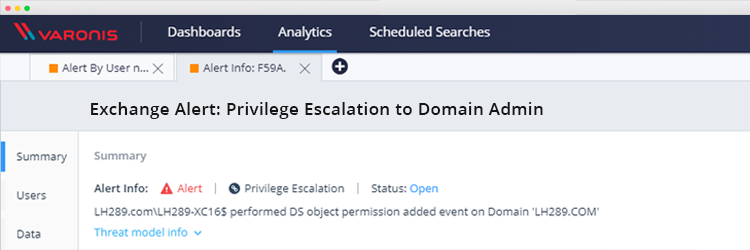
Exchange Vulnerability: How to Detect Elevation of Privilege to a Domain Administrator
- Transfer
A vulnerability discovered in Exchange this year allows any domain user to gain domain administrator rights and compromise Active Directory (AD) and other connected hosts. Today we will tell you how this attack works and how to detect it.
Here's how this attack works:
Subsequently, an attacker could, for example, run DCSync to obtain hashed passwords for all users in a domain. This will allow him to implement various types of attacks - from attacks on the golden ticket to the transmission of the hash.
The Varonis research team has studied this attack vector in detail and prepared a guide for our customers to detect it and at the same time check if they have already been compromised.
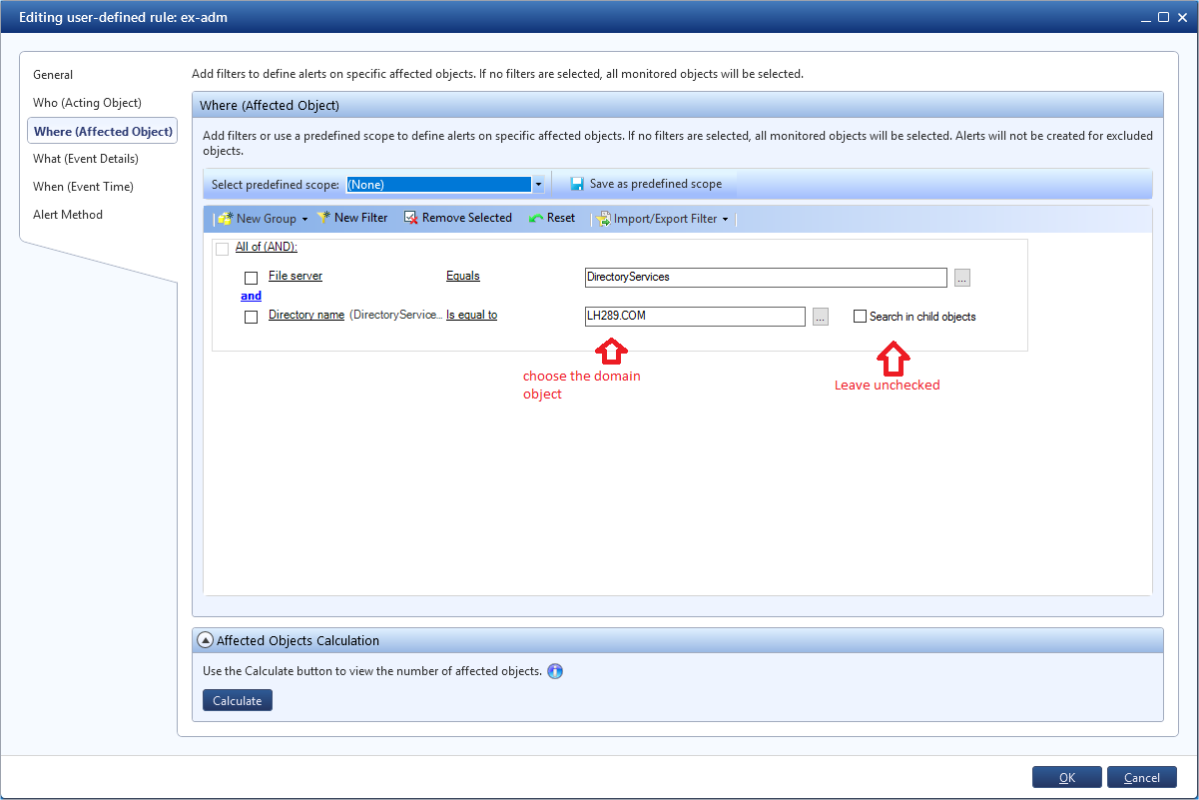
In DatAlert, create a custom rule to track changes to specific object permissions. It will work when adding rights and permissions to the object of interest in the domain:
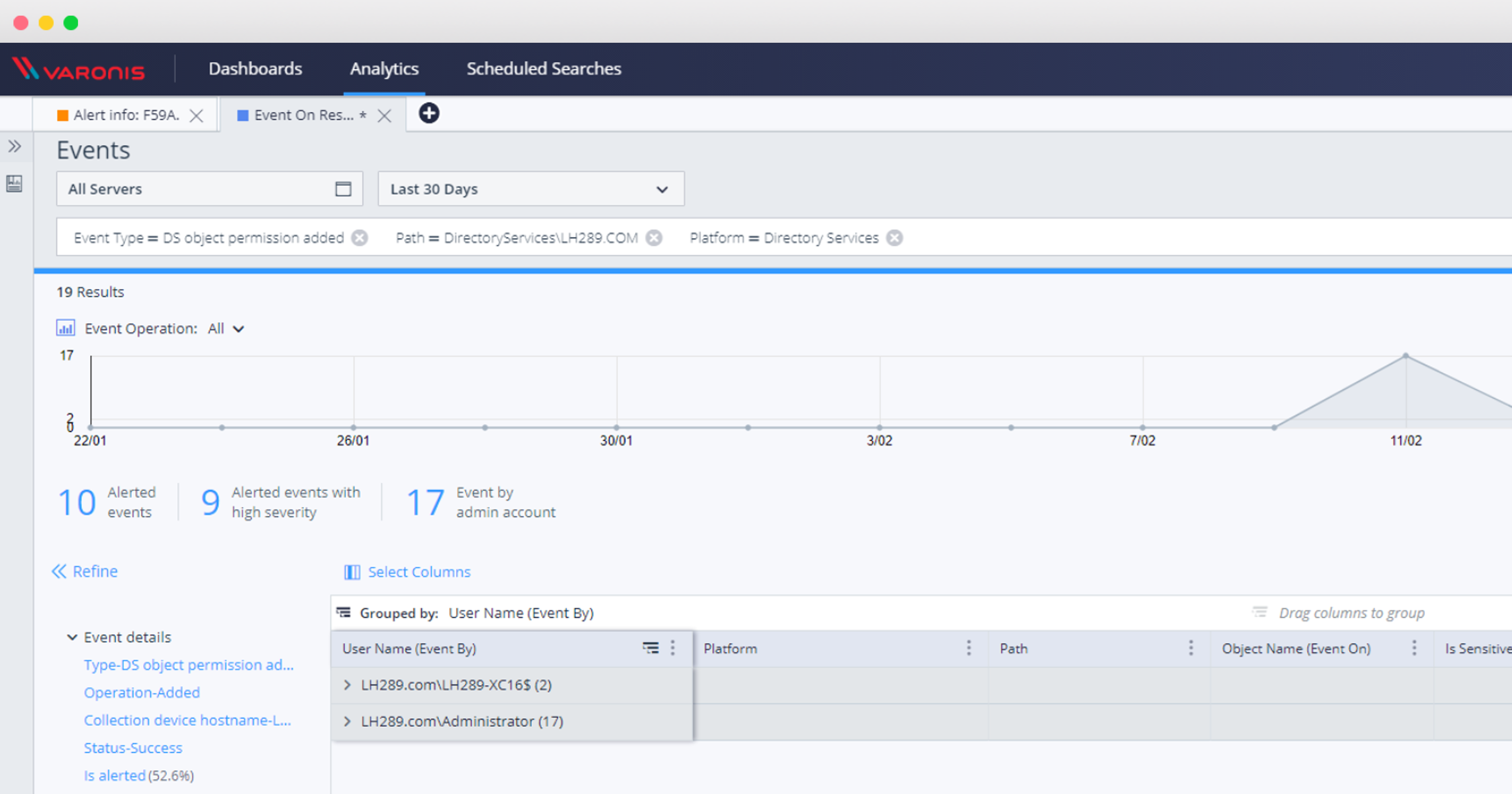
Changing permissions on an AD object is a rare occurrence, so anything that caused this warning needs to be investigated. It would also be nice to test the appearance and contents of the report before launching the rule itself into battle.
This report will also show if you have already been compromised by this attack:
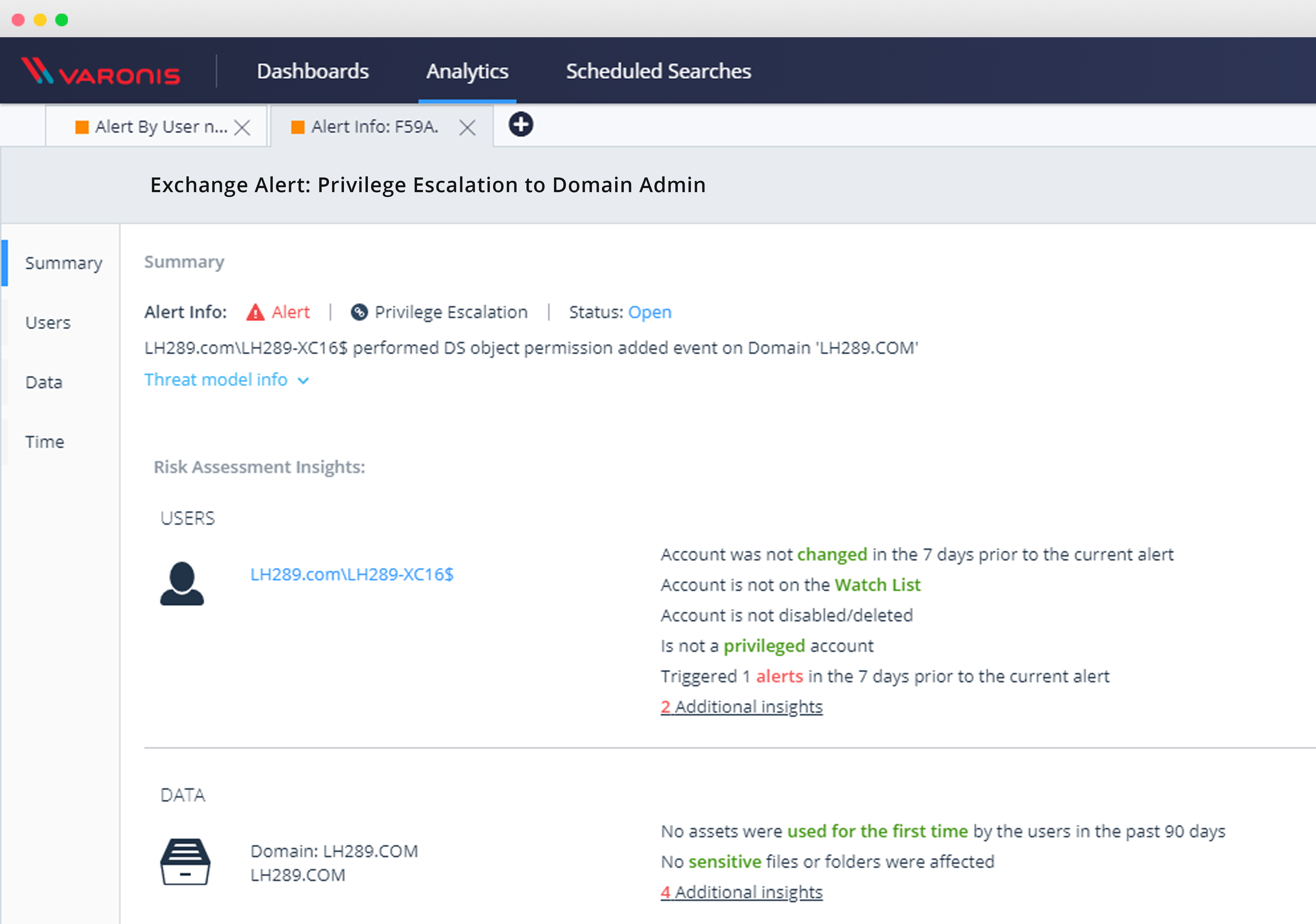
After activating the rule, you can investigate all other privilege escalation events using the DatAlert web interface:
After configuring this rule, you can monitor and protect against these and similar types of security vulnerabilities, and investigate events with AD directory service objects and see if you are at risk from this critical vulnerability.

Here's how this attack works:
- An attacker takes possession of the account of any domain user with an active mailbox in order to subscribe to the push notification function from Exchange
- An attacker uses NTLM relay to trick an Exchange server: as a result, the Exchange server connects to the compromised user’s computer using the NTLM over HTTP method, which the attacker then uses to authenticate to the domain controller using LDAP with the Exchange account information
- As a result, an attacker uses these Exchange account privileges to elevate his privileges. This last step can also be performed by a hostile administrator who already has legitimate access to make the necessary change of rights. By creating a rule to detect this activity, you will be protected from this and similar attacks.
Subsequently, an attacker could, for example, run DCSync to obtain hashed passwords for all users in a domain. This will allow him to implement various types of attacks - from attacks on the golden ticket to the transmission of the hash.
The Varonis research team has studied this attack vector in detail and prepared a guide for our customers to detect it and at the same time check if they have already been compromised.
Domain privilege escalation detection
In DatAlert, create a custom rule to track changes to specific object permissions. It will work when adding rights and permissions to the object of interest in the domain:
- Specify a rule name
- Set the category as “Privilege escalation”
- Set the value for the resource type to All Resource Types
- File Server = DirectoryServices
- Set the domain you are interested in, for example, by name
- Add a filter to add permissions on an AD object
- And do not forget to leave the option "Search in child objects" unchecked

And now, the report: Domain Object Rights Change Detection
Changing permissions on an AD object is a rare occurrence, so anything that caused this warning needs to be investigated. It would also be nice to test the appearance and contents of the report before launching the rule itself into battle.
This report will also show if you have already been compromised by this attack:

After activating the rule, you can investigate all other privilege escalation events using the DatAlert web interface:

After configuring this rule, you can monitor and protect against these and similar types of security vulnerabilities, and investigate events with AD directory service objects and see if you are at risk from this critical vulnerability.
