Audit in 60 minutes - check employees' resistance to phishing attacks through Sophos Phish Threat for free

Surely many of you were interested in the question: “How many of my colleagues are not aware of phishing attacks?” To clarify this issue, you can get a little confused and raise local utilities, but it is much more efficient to use a ready-made solution.
Action plan:
- request a test version of Sophos Phish Threat ;
- add Sophos IP addresses to the white list;
- select and edit a template for our realities;
- do newsletter;
- look at the statistics;
- We talk with users and the Guide.
A more detailed description can be found under the cut.
At the end of the article - a bonus for those who read to the end;). Decision card for employees - print and distribute to all employees.
Recently, phishing attacks have risen sharply as attackers continue to improve tactics and share successful types of attacks. In particular, they take advantage of the malware on the darknet to increase the efficiency and volume of attacks. In fact, a huge number of organizations currently report at least daily phishing attacks. Here we look at the evolution of phishing in recent years, how it works and how it looks. And as cybercriminals continue to prey on employees using their technologies, we will argue for the importance of multi-level protection against phishing attacks: combining advanced security technologies with phishing-aware employees.
More than annoying spam
Traditionally, phishing has been associated with cybercrime of online banking: scammers send an email, luring you to a website, which is a visual clone of the login page of your bank, where you enter your credentials in a fake form and send them directly to the criminals. But phishing covers much more than just fake banking sites and imaginary links. Phishing is big business. In recent years, the volume of phishing attacks supported by “dark” web services, such as free phishing sets and phishing as a service, has sharply increased. Even an attacker with a small technical background will find it increasingly easy to use advanced malware. As a result, phishing attacks have become a regular part of everyday life.
The main driving force behind phishing attacks is financial gain.A Verizon 2018 data breach study report revealed that:
- 59% of attacks are caused by financial gain. It also includes collecting credentials for resale on the darknet, infecting systems with ransomware, or impersonating managers to convince employees to transfer funds or transfer valuable data.
- 38% of attacks are aimed at gaining unauthorized access to the system. Examples, including gaining access to a company’s network to steal data or gain control of systems.
Currently, most phishing attacks are carried out by organized crime. This has led to the emergence of more effective methods for spreading attacks using phishing services, ready-made phishing kits and new types of attacks that target more valuable assets using social engineering.
Raise employee phishing awareness with Sophos Phish Threat
Using Sophos Phish Threat, you can conduct an audit - emulate a phishing attack and check how employees are exposed to this type of threat. To do this, we request a Trial product and enter the Sophos Central, Phish Threat section.
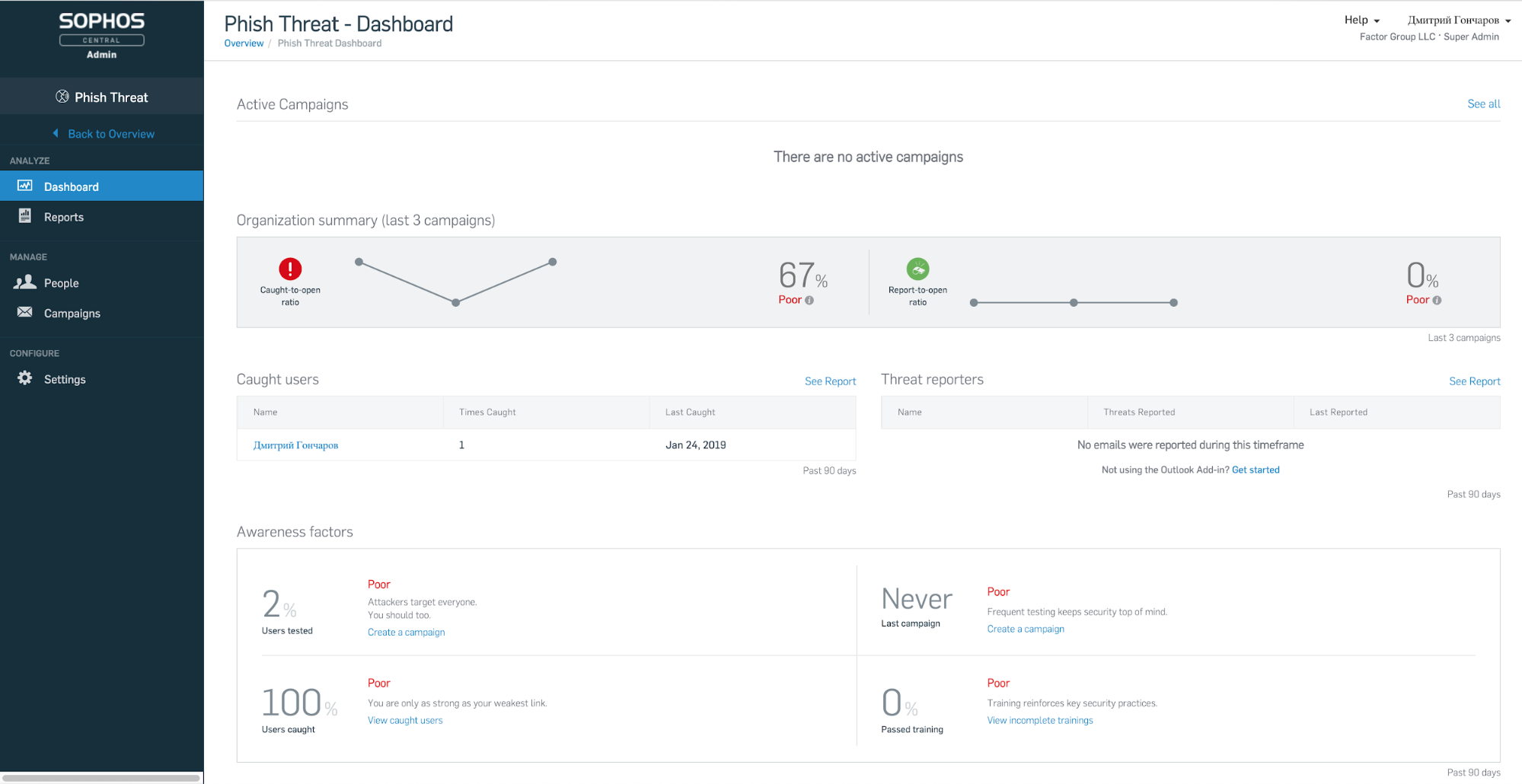
The Dashboard tab displays a summary of the last three phishing attacks in our example. You can see how successful the phishing campaign was and which employees were at risk.
On the Settings tab, we look at the IP addresses from which the mailing will take place.
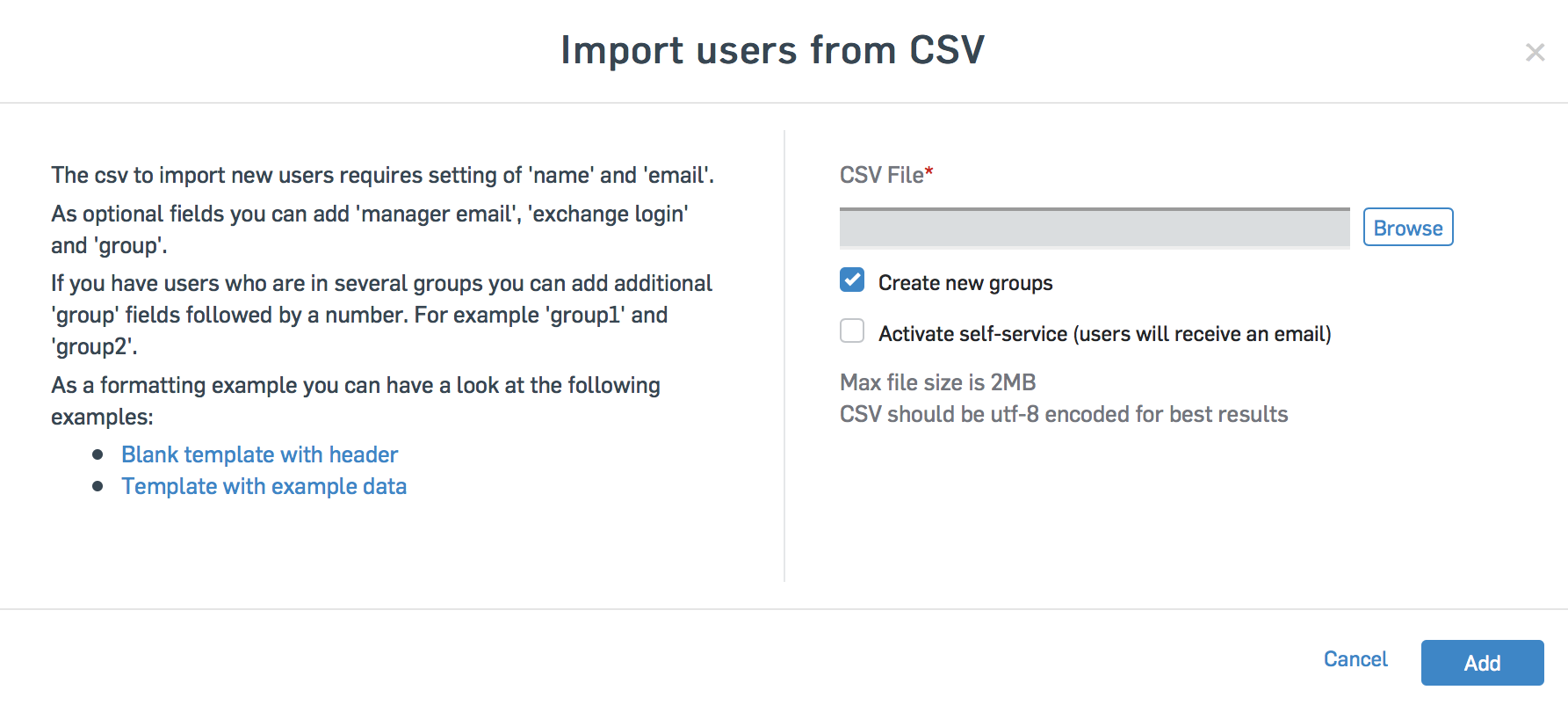
On the People tab, we add the Email addresses of employees. You can do this in several ways: import from a CSV file, manually add, synchronize with Active Directory, synchronize with Azure AD.
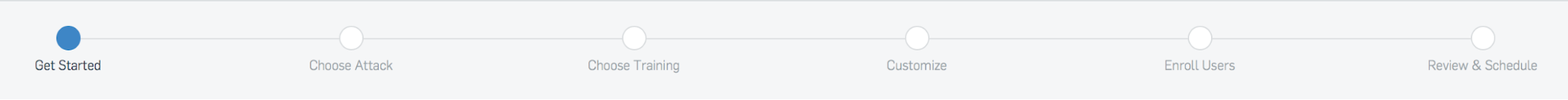
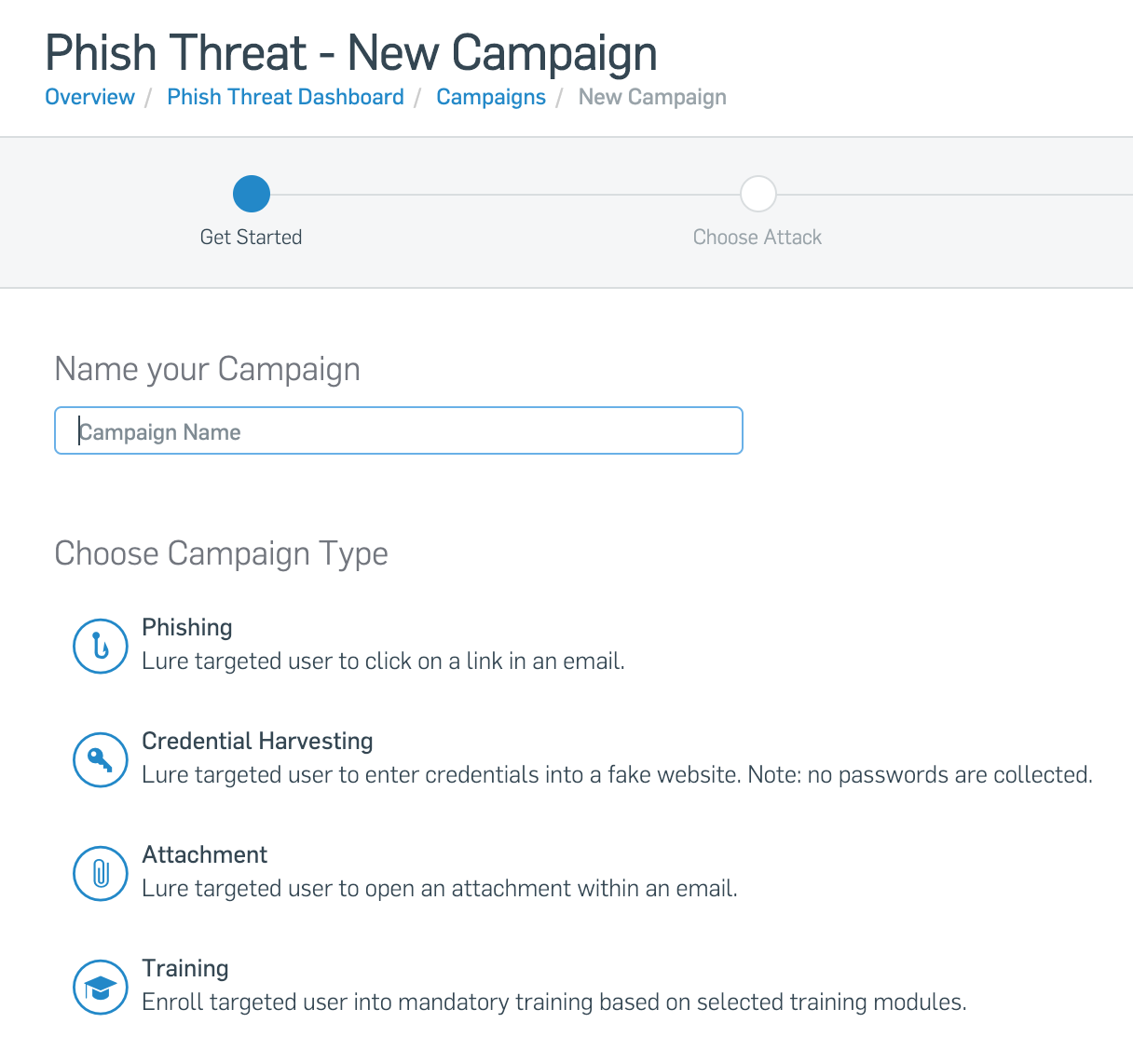
Now let's move on to creating a phishing campaign - the Campaigns tab. The process is divided into stages, from above you can see their progress.
The first step is to select the type of mailing. This can be ordinary phishing, which is aimed at detecting the passage of phishing links. Another form of phishing is credential collection. It aims to identify the possibility of collecting credentials from a phishing site. It should be noted that the entered data is not saved. The third type is phishing with attachments. It reveals the user's opening attachments in an email message.
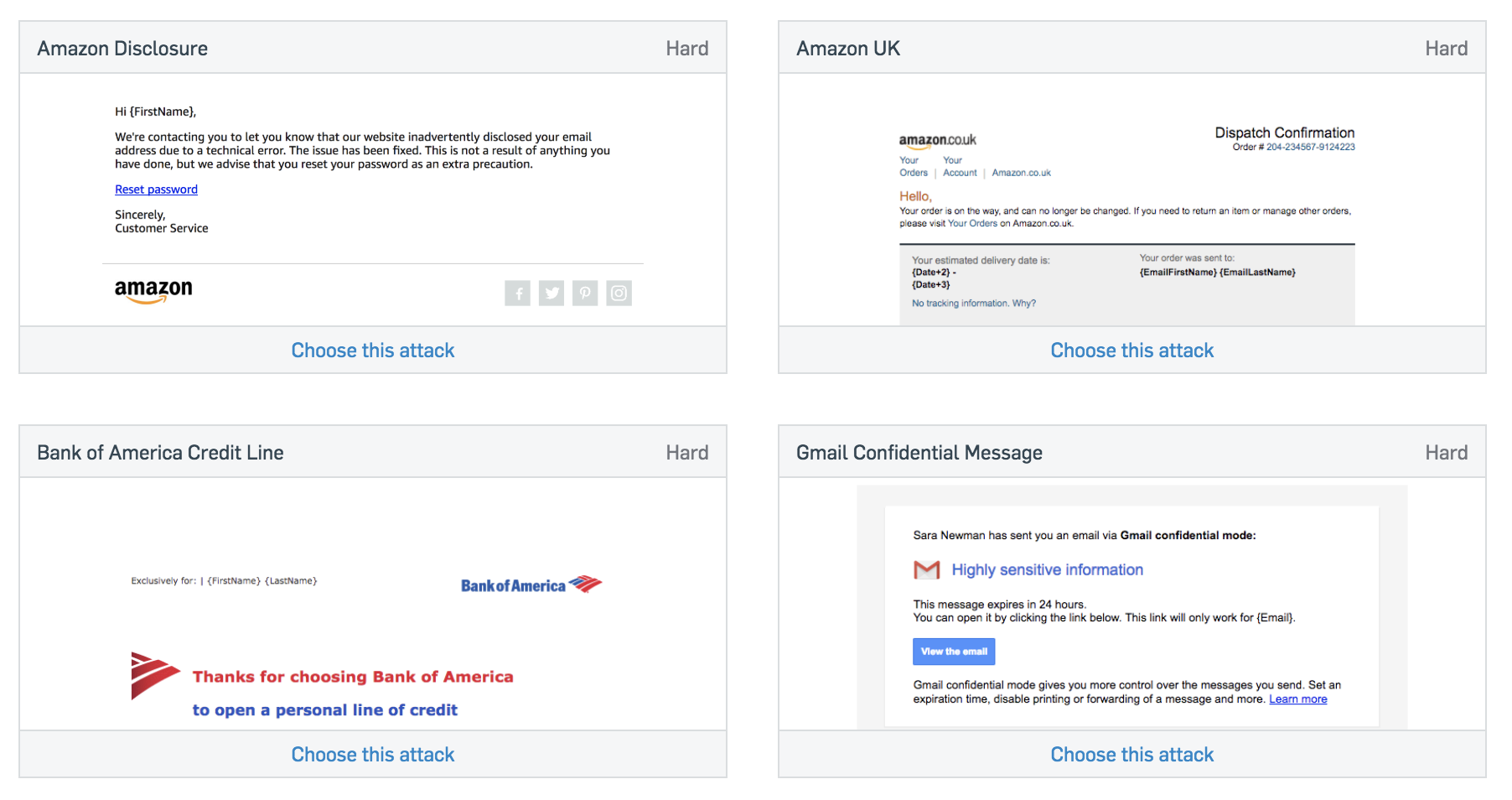
After we have decided on the type of phishing attack, we select a phishing email template. In this regard, Sophos has a wide variety to choose from. SophosLabs analysts track the latest trends in real attacks and regularly update patterns.
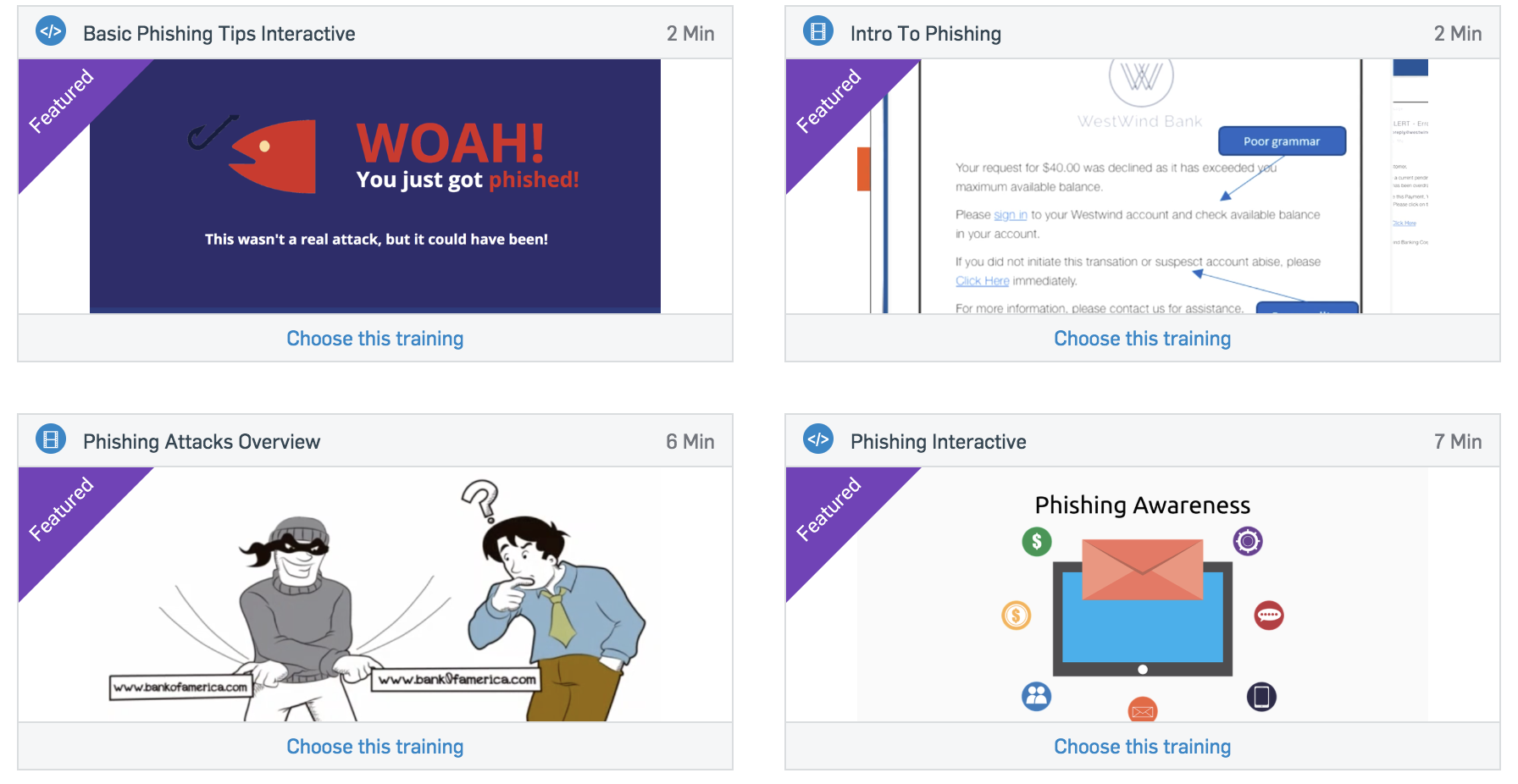
Then you need to choose a training for the user, which will be demonstrated to him as a training material. At the moment, trainings are not available in Russian, so you can use them as a base for creating your own seminars within the company. You can also set the URL for your internal training - for example, in the internal knowledge base.
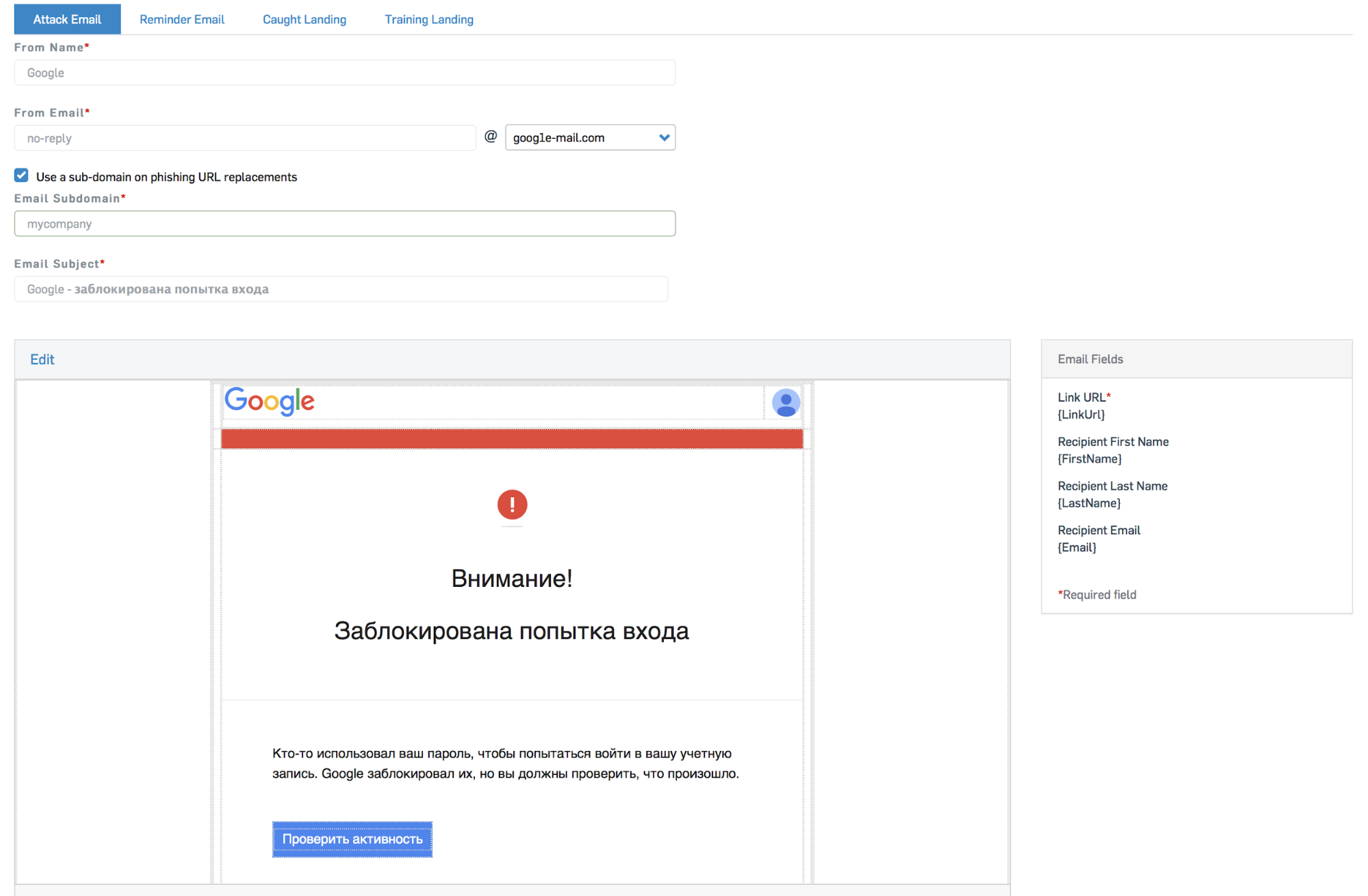
After that, we customize our newsletter. We write down the Name and Email Address, which will be indicated as the sender, we edit the letter template - we can insert the necessary pictures and write the text in any language.
We select users / groups - here we can choose the relevant department for which we prepared a letter template.
Specify the time interval in which the phishing mailing will be carried out. You can send letters to all users at the same time, or you can do it more cunningly - send them gradually, for example, by 20% every 2 hours (total - 5 hours for the entire distribution). This is useful with a large number of users and so that not all users receive the same email at the same time.

We press the treasured Done button and go to drink coffee ...
Audit analysis
After the phishing campaign, we’ll move on to the report.
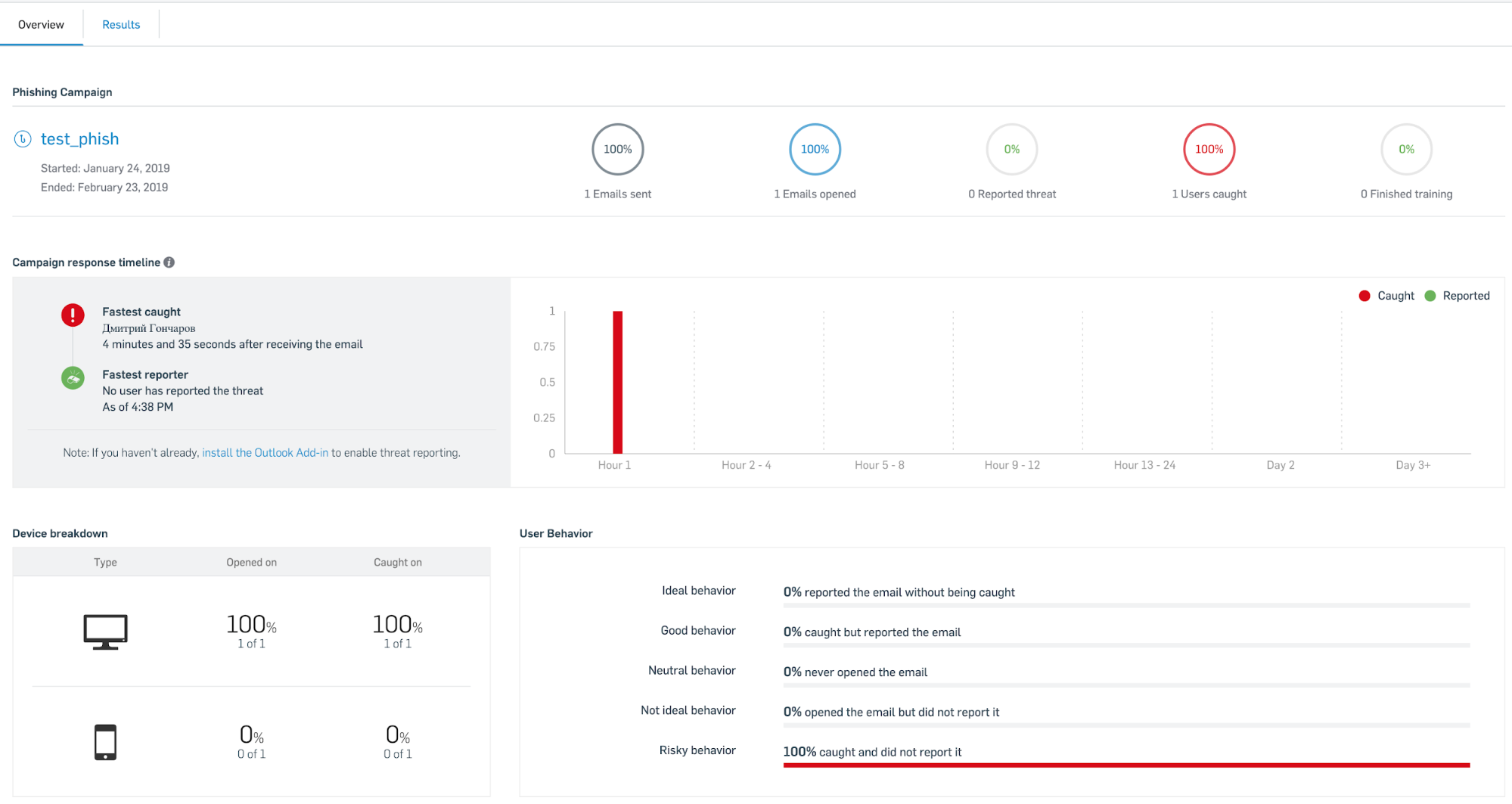
The report displays the types of devices that were attacked, the number of messages sent, open messages, and the percentage of users who were attacked. You can also see which user opened the phishing email faster than anyone else.
Thus, we considered a tool for conducting phishing mailings in companies like Sophos Phish Threat , which is quite flexible in settings, and, among other things, contains training sessions for the prevention of real phishing attacks in the future.
The end user decides whether to open the attachment or follow the link. To help the average user, we have prepared two documents in Russian:
- phishing detection flowchart ;
- check list of phishing control signs - print and hang on the wall.
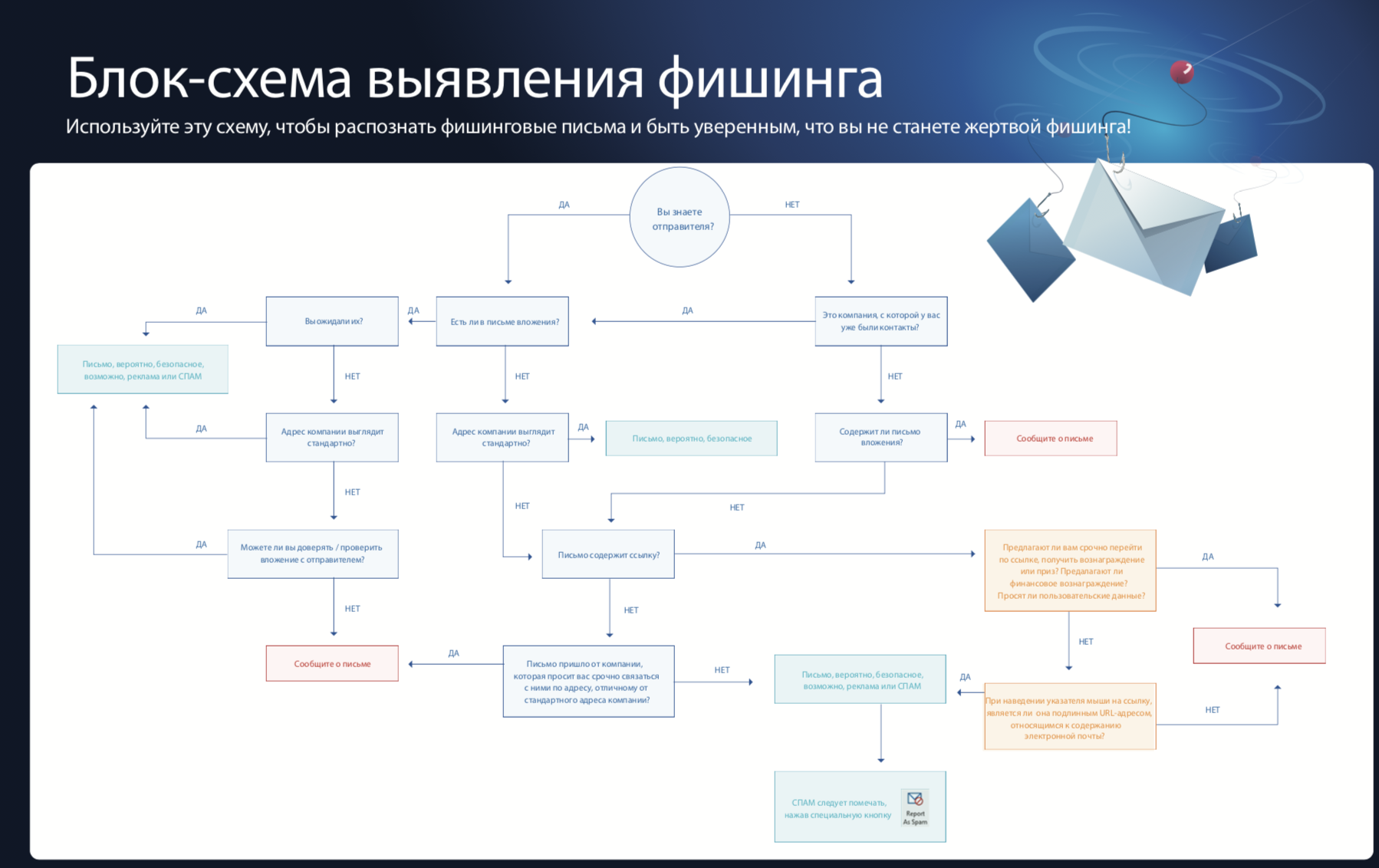
To keep users in good shape, such training should be done on a regular basis. If you are interested in the solution, you can contact us - Factor Group company , Sophos distributor. It is enough to write in free form to sophos@fgts.ru .
Thank you popov-as for helping with this article.
