WhatsApp in the palm of your hand: where and how can you detect forensic artifacts?

If you want to know what types of WhatsApp forensic artifacts exist in various operating systems and where exactly they can be detected, then here you are. With this article, Igor Mikhailov, a specialist in the Group-IB Laboratory of Computer Forensics, opens a series of publications on the WhatsApp forensic investigation and what information can be obtained by analyzing the device.
Just note that different types of WhatsApp artifacts are stored in different operating systems, and if a researcher can extract certain types of WhatsApp data from one device, this does not mean that such types of data can be extracted from another device. For example, if a system unit running Windows is seized, then WhatsApp chats will probably not be found on its disks (except for backup copies of iOS devices that can be detected on the same drives). When removing laptops and mobile devices will have their own characteristics. Let's talk about this in more detail.
WhatsApp artifacts on an Android device
In order to extract WhatsApp artifacts from a device running Android OS, the researcher must have superuser privileges ( 'root' ) on the device under investigation or be able to otherwise extract the physical dump of the device’s memory or its file system (for example, using software vulnerabilities of a specific mobile devices).
Application files are located in the phone’s memory in the section where user data is saved. Typically, this section is named 'userdata' . Subdirectories and program files are located along the path: '/data/data/com.whatsapp/' .
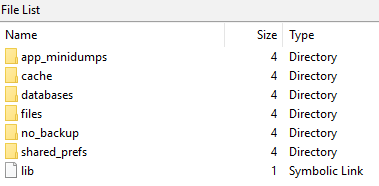
The main files that contain WhatsApp forensic artifacts in the Android OS are the 'wa.db' and 'msgstore.db' databases .
The 'wa.db' database contains a complete list of WhatsApp user contacts, including phone number, display name, timestamps and any other information specified during registration with WhatsApp. The file 'wa.db' is located along the path: '/data/data/com.whatsapp/databases/' and has the following structure:
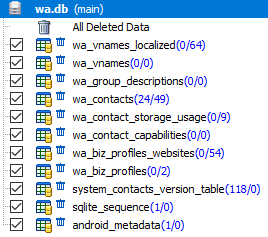
The most interesting tables in the 'wa.db' database for the researcher are:
- 'wa_contacts'
This table contains contact information: contact id in WhatsApp, status information, username displayed, time stamps, etc.
Appearance of the table: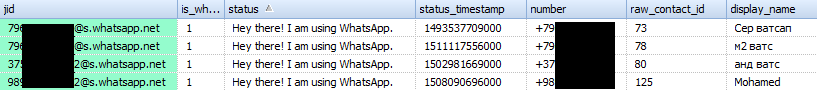 Table structure
Table structureField name Value _id record serial number (in SQL table) jid WhatsApp contact ID, written in the format <phone number> @ s.whatsapp.net is_whatsapp_user contains '1' if the actual WhatsApp user matches the contact, '0' otherwise status contains text displayed in contact status status_timestamp contains a timestamp in Unix Epoch Time (ms) format number phone number associated with the contact raw_contact_id contact serial number display_name contact display name phone_type phone type phone_label label associated with the contact number unseen_msg_count the number of messages that were sent by the contact but were not read by the recipient photo_ts contains a timestamp in Unix Epoch Time format thumb_ts contains a timestamp in Unix Epoch Time format photo_id_timestamp contains a timestamp in Unix Epoch Time (ms) format given_name field value matches 'display_name' for each contact wa_name WhatsApp contact name (displays the name specified in the contact profile) sort_name contact name used in sorting operations nickname WhatsApp contact nickname (displays the nickname specified in the contact profile) company company (the company indicated in the contact profile is displayed) title appeal (mistress / gentleman; the address configured in the contact profile is displayed) offset bias - 'sqlite_sequence'
This table contains information about the number of contacts; - 'android_metadata'
This table contains information about the language localization of WhatsApp.
The database 'msgstore.db' contains information about transmitted messages, such as contact number, message text, message status, timestamps, information about transferred files included in messages, etc. The file 'msgstore.db' is located along the path: '/data/data/com.whatsapp/databases/' and has the following structure:
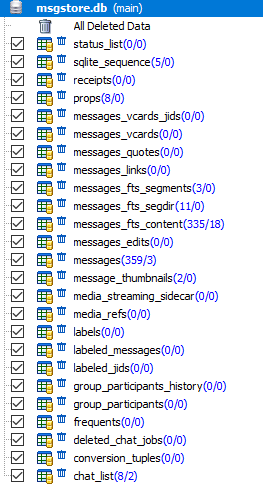
The most interesting tables in the file 'msgstore.db' for the researcher are:
- 'sqlite_sequence'
This table contains general information about this database, for example, total number of messages stored, total number of chats, etc.
Appearance of the table:
- 'message_fts_content'
Contains the text of the transmitted messages.
Appearance of the table: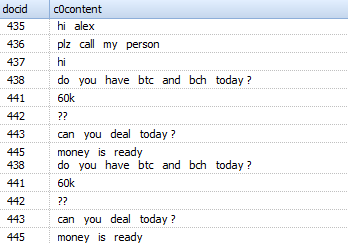
- 'messages'
This table contains information such as contact number, message text, message status, timestamps, information about the transferred files included in the messages.
Appearance of the table: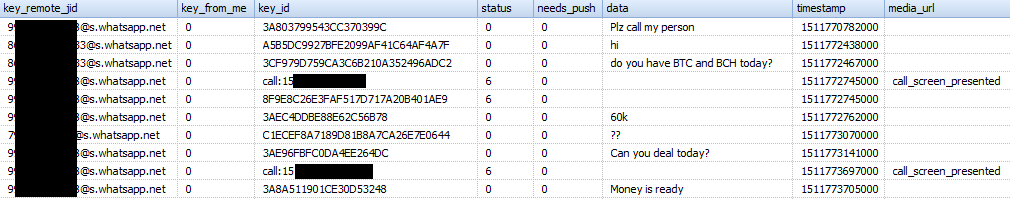 Table structure
Table structureField name Value _id record serial number (in SQL table) key_remote_jid WhatsApp Communication Partner ID key_from_me message direction: '0' - incoming, '1' - outgoing key_id unique identifier of the message status message status: '0' - delivered, '4' - waiting on the server, '5' - received at the destination, '6' - control message, '13' - message opened by the recipient (read) need_push has the value '2' if it is a broadcast message, otherwise it contains '0' data message text (when the parameter 'media_wa_type' is '0') timestamp contains a timestamp in Unix Epoch Time (ms) format, the value is taken from the device’s clock media_url contains the URL of the transmitted file (when the parameter 'media_wa_type' is '1', '2', '3') media_mime_type MIME type of the transferred file (when the parameter 'media_wa_type' is equal to '1', '2', '3') media_wa_type message type: '0' - text, '1' - image file, '2' - audio file, '3' - video file, '4' - contact card, '5' - geodata media_size file transfer size (when the parameter 'media_wa_type' is '1', '2', '3') media_name name of the transferred file (when the parameter 'media_wa_type' is '1', '2', '3') media_caption Contains the words 'audio', 'video' for the corresponding values of the parameter 'media_wa_type' (when the parameter 'media_wa_type' is '1', '3') media_hash base64 encoded hash of the transmitted file, calculated according to the HAS-256 algorithm (when the parameter 'media_wa_type' is '1', '2', '3') media_duration duration in seconds for the media file (when the parameter 'media_wa_type' is '1', '2', '3') origin has the value '2' if it is a broadcast message, otherwise it contains '0' latitude geodata: latitude (when the parameter 'media_wa_type' is '5') longitude geodata: longitude (when the parameter 'media_wa_type' is '5') thumb_image service information remote_recource Sender ID (group chat only) received_timestamp receive time, contains a time stamp in Unix Epoch Time (ms) format, the value is taken from the device clock (when the parameter 'key_from_me' has '0', '-1' or another value) send_timestamp not used, usually has a value of '-1' receipt_server_timestamp time received by the central server, contains a time stamp in Unix Epoch Time (ms) format, the value is taken from the device’s clock (when the parameter 'key_from_me' has '1', '-1' or another value receipt_device_timestamp the time the message was received by another subscriber, contains a time stamp in Unix Epoch Time (ms) format, the value is taken from the device’s clock (when the parameter 'key_from_me' has '1', '-1' or another value read_device_timestamp message opening (reading) time, contains a timestamp in Unix Epoch Time (ms) format, the value is taken from the device’s clock played_device_timestamp message playback time, contains a time stamp in Unix Epoch Time (ms) format, the value is taken from the device’s clock raw_data thumbnail of the transmitted file (when the parameter 'media_wa_type' is equal to '1' or '3') recipient_count number of recipients (for broadcast messages) participant_hash used when sending messages with geodata starred not used quoted_row_id unknown, usually contains the value '0' mentioned_jids not used multicast_id not used offset bias
This list of fields is not exhaustive. For different versions of WhatsApp, some of the fields may or may not be present. Additionally, the fields 'media_enc_hash' , 'edit_version' , 'payment_transaction_id' , etc. may be present . - 'messages_thumbnails'
This table contains information about transmitted images and timestamps. In the 'timestamp' column, the time is in Unix Epoch Time (ms) format. - 'chat_list'
This table contains chat information.
Appearance of the table:
Also, when researching WhatsApp in a mobile device running Android, you need to pay attention to the following files:
- File 'msgstore.db.cryptXX' (where XX is one or two digits from 0 to 12, for example, msgstore.db.crypt12). Contains an encrypted backup of WhatsApp messages (backup of the msgstore.db file ). The file (or files) 'msgstore.db.cryptXX' is located along the path: '/ data / media / 0 / WhatsApp / Databases /' (virtual SD card), '/ mnt / sdcard / WhatsApp / Databases / (physical SD- map)'.
- The file is 'key' . Contains a cryptographic key. It is located along the path: '/data/data/com.whatsapp/files/' . Used to decrypt encrypted WhatsApp backups.
- File 'com.whatsapp_preferences.xml' . Contains information about the WhatsApp account profile. The file is located on the path: '/data/data/com.whatsapp/shared_prefs/' .File Content Snippet
…9123456789 (номер телефона, ассоциированный с аккаунтом WhatsApp) …2.17.395 (версия WhatsApp) …Hey there! I am using WhatsApp. (сообщение, отображаемое в статусе аккаунта) …Alex (имя владельца аккаунта) … - File 'registration.RegisterPhone.xml' . Contains phone number information associated with a WhatsApp account. The file is located on the path: '/data/data/com.whatsapp/shared_prefs/' .File contents
- File 'axolotl.db' . Contains cryptographic keys and other data that is necessary to identify the account owner. It is located along the path: '/data/data/com.whatsapp/databases/' .
- File 'chatsettings.db' . Contains application configuration information.
- The file 'wa.db' . Contains contact details. A very interesting (in the forensic aspect) and informative database. In it, detailed information about deleted contacts can be found.
You should also pay attention to the following directories:
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Images /' . Contains the transferred image files.
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Voice Notes /' . Contains voice messages in .OPUS format files.
- Directory '/data/data/com.whatsapp/cache/Profile Pictures /' . Contains graphic files - images of contacts.
- Directory '/data/data/com.whatsapp/files/Avatars/' . Contains image files - thumbnails of contact images. These files have the extension '.j', but, nevertheless, are image files in JPEG (JPG) format.
- Directory '/data/data/com.whatsapp/files/Avatars/' . Contains image files - image and thumbnail of the image installed as an avatar by the account owner.
- Directory '/data/data/com.whatsapp/files/Logs/' . It contains the program operation log (file 'whatsapp.log') and backup copies of the program operation logs (files with the format names whatsapp-yyyy-mm-dd.1.log.gz).
WhatsApp Log Files:
Magazine fragment
2017-01-10 09: 37: 09.757 LL_I D [524: WhatsApp Worker # 1] missedcallnotification / init count: 0 timestamp: 0
2017-01-10 09: 37: 09.758 LL_I D [524: WhatsApp Worker # 1] missedcallnotification / update cancel true
2017-01-10 09: 37: 09.768 LL_I D [1: main] app-init / load-me
2017-01-10 09: 37: 09.772 LL_I D [1: main] password file missing or unreadable
2017-01-10 09: 37: 09.782 LL_I D [1: main] statistics Text Messages: 59 sent, 82 received / Media Messages: 1 sent (0 bytes), 0 received (9850158 bytes) / Offline Messages: 81 received ( 19522 msec average delay) / Message Service: 116075 bytes sent, 211729 bytes received / Voip Calls: 1 outgoing calls, 0 incoming calls, 2492 bytes sent, 1530 bytes received / Google Drive: 0 bytes sent, 0 bytes received / Roaming: 1524 bytes sent, 1826 bytes received / Total Data: 118567 bytes sent, 10063417 bytes received
2017-01-10 09: 37: 09.785 LL_I D [1: main] media-state-manager / refresh-media-state / writable-media
2017 -01-10 09: 37: 09.806 LL_I D [1: main] app-init / initialize / timer / stop: 24
2017-01-10 09: 37: 09.811 LL_I D [1: main] msgstore / checkhealth
2017-01-10 09: 37: 09.817 LL_I D [1: main] msgstore / checkhealth / back / delete false
2017-01-10 09: 37: 09.818 LL_I D [1: main] msgstore / checkhealth / back / delete false
2017-01-10 09: 37: 09.818 LL_I D [1: main] msgstore / checkdb / data / data / com.whatsapp / databases / msgstore.db
2017-01-10 09: 37: 09.819 LL_I D [1: main ] msgstore / checkdb / list _jobqueue-WhatsAppJobManager 16384 drw = 011
2017-01-10 09: 37: 09.820 LL_I D [1: main] msgstore / checkdb / list _jobqueue-WhatsAppJobManager-journal 21032 drw = 011
2017-01-10 09 : 37: 09.820 LL_I D [1: main] msgstore / checkdb / list axolotl.db 184320 drw = 011
2017-01-10 09: 37: 09.821 LL_I D [1: main] msgstore / checkdb / list axolotl.db-wal 436752 drw = 011
2017-01-10 09: 37: 09.821 LL_I D [1: main] msgstore / checkdb / list axolotl.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.822 LL_I D [1: main] msgstore / checkdb / list msgstore.db 540672 drw = 011
2017-01-10 09: 37: 09.823 LL_I D [1: main] msgstore / checkdb / list msgstore.db-wal 0 drw = 011
2017-01-10 09: 37: 09.823 LL_I D [1: main] msgstore / checkdb / list msgstore.db-shm 32768 drw = 011
2017-01-10 09:37: 09.824 LL_I D [1: main] msgstore / checkdb / list wa.db 69632 drw = 011
2017-01-10 09: 37: 09.825 LL_I D [1: main] msgstore / checkdb / list wa.db-wal 428512 drw = 011
2017-01-10 09: 37: 09.825 LL_I D [1: main] msgstore / checkdb / list wa.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.826 LL_I D [1: main] msgstore / checkdb / list chatsettings.db 4096 drw = 011
2017-01-10 09: 37: 09.826 LL_I D [1: main] msgstore / checkdb / list chatsettings.db-wal 70072 drw = 011
2017-01-10 09: 37: 09.827 LL_I D [1: main] msgstore / checkdb / list chatsettings.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.838 LL_I D [1: main] msgstore / checkdb / version 1
2017-01-10 09: 37: 09.839 LL_I D [1: main] msgstore / canquery
2017-01-10 09: 37: 09.846 LL_I D [1: main] msgstore / canquery / count 1
2017-01 -10 09: 37: 09.847 LL_I D [1: main] msgstore / canquery / timer / stop: 8
2017-01-10 09: 37: 09.847 LL_I D [1: main] msgstore / canquery 517 | time spent: 8
2017-01-10 09: 37: 09.848 LL_I D [529: WhatsApp Worker # 3] media-state-manager / refresh-media-state / internal-storage available: 1,345,622,016 total: 5,687,922,688
2017-01-10 09: 37: 09.758 LL_I D [524: WhatsApp Worker # 1] missedcallnotification / update cancel true
2017-01-10 09: 37: 09.768 LL_I D [1: main] app-init / load-me
2017-01-10 09: 37: 09.772 LL_I D [1: main] password file missing or unreadable
2017-01-10 09: 37: 09.782 LL_I D [1: main] statistics Text Messages: 59 sent, 82 received / Media Messages: 1 sent (0 bytes), 0 received (9850158 bytes) / Offline Messages: 81 received ( 19522 msec average delay) / Message Service: 116075 bytes sent, 211729 bytes received / Voip Calls: 1 outgoing calls, 0 incoming calls, 2492 bytes sent, 1530 bytes received / Google Drive: 0 bytes sent, 0 bytes received / Roaming: 1524 bytes sent, 1826 bytes received / Total Data: 118567 bytes sent, 10063417 bytes received
2017-01-10 09: 37: 09.785 LL_I D [1: main] media-state-manager / refresh-media-state / writable-media
2017 -01-10 09: 37: 09.806 LL_I D [1: main] app-init / initialize / timer / stop: 24
2017-01-10 09: 37: 09.811 LL_I D [1: main] msgstore / checkhealth
2017-01-10 09: 37: 09.817 LL_I D [1: main] msgstore / checkhealth / back / delete false
2017-01-10 09: 37: 09.818 LL_I D [1: main] msgstore / checkhealth / back / delete false
2017-01-10 09: 37: 09.818 LL_I D [1: main] msgstore / checkdb / data / data / com.whatsapp / databases / msgstore.db
2017-01-10 09: 37: 09.819 LL_I D [1: main ] msgstore / checkdb / list _jobqueue-WhatsAppJobManager 16384 drw = 011
2017-01-10 09: 37: 09.820 LL_I D [1: main] msgstore / checkdb / list _jobqueue-WhatsAppJobManager-journal 21032 drw = 011
2017-01-10 09 : 37: 09.820 LL_I D [1: main] msgstore / checkdb / list axolotl.db 184320 drw = 011
2017-01-10 09: 37: 09.821 LL_I D [1: main] msgstore / checkdb / list axolotl.db-wal 436752 drw = 011
2017-01-10 09: 37: 09.821 LL_I D [1: main] msgstore / checkdb / list axolotl.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.822 LL_I D [1: main] msgstore / checkdb / list msgstore.db 540672 drw = 011
2017-01-10 09: 37: 09.823 LL_I D [1: main] msgstore / checkdb / list msgstore.db-wal 0 drw = 011
2017-01-10 09: 37: 09.823 LL_I D [1: main] msgstore / checkdb / list msgstore.db-shm 32768 drw = 011
2017-01-10 09:37: 09.824 LL_I D [1: main] msgstore / checkdb / list wa.db 69632 drw = 011
2017-01-10 09: 37: 09.825 LL_I D [1: main] msgstore / checkdb / list wa.db-wal 428512 drw = 011
2017-01-10 09: 37: 09.825 LL_I D [1: main] msgstore / checkdb / list wa.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.826 LL_I D [1: main] msgstore / checkdb / list chatsettings.db 4096 drw = 011
2017-01-10 09: 37: 09.826 LL_I D [1: main] msgstore / checkdb / list chatsettings.db-wal 70072 drw = 011
2017-01-10 09: 37: 09.827 LL_I D [1: main] msgstore / checkdb / list chatsettings.db-shm 32768 drw = 011
2017-01-10 09: 37: 09.838 LL_I D [1: main] msgstore / checkdb / version 1
2017-01-10 09: 37: 09.839 LL_I D [1: main] msgstore / canquery
2017-01-10 09: 37: 09.846 LL_I D [1: main] msgstore / canquery / count 1
2017-01 -10 09: 37: 09.847 LL_I D [1: main] msgstore / canquery / timer / stop: 8
2017-01-10 09: 37: 09.847 LL_I D [1: main] msgstore / canquery 517 | time spent: 8
2017-01-10 09: 37: 09.848 LL_I D [529: WhatsApp Worker # 3] media-state-manager / refresh-media-state / internal-storage available: 1,345,622,016 total: 5,687,922,688
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Audio /' . Contains received audio files.
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Audio / Sent /' . Contains sent audio files.
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Images /' . Contains received image files.
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Images / Sent /' . Contains sent image files.
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Video /' . Contains received video files.
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Video / Sent /' . Contains uploaded video files.
- Directory '/ data / media / 0 / WhatsApp / Media / WhatsApp Profile Photos /' . Contains image files associated with the owner of the WhatsApp account.
- To save space in the Android smartphone’s memory, some of the WhatsApp data can be stored on the SD card. On the SD card, in the root directory, there is a 'WhatsApp' directory where the following artifacts of this program can be found:

- Directory '.Share' ( '/mnt/sdcard/WhatsApp/.Share/' ). Contains copies of files that have been transferred to other WhatsApp users.
- Directory '.trash' ( '/mnt/sdcard/WhatsApp/.trash/' ). Contains deleted files.
- Directory 'Databases' ( '/ mnt / sdcard / WhatsApp / Databases /' ). Contains encrypted backups. They can be decrypted in the presence of the 'key' file , extracted from the memory of the analyzed device.
Files in the 'Databases' subdirectory :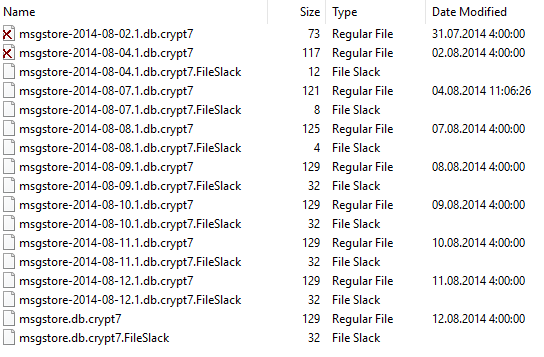
- Directory 'Media' ( '/ mnt / sdcard / WhatsApp / Media /' ). Contains the subdirectories 'WallPaper' , 'WhatsApp Audio' , 'WhatsApp Images' , 'WhatsApp Profile Photos' , 'WhatsApp Video' , 'WhatsApp Voice Notes' , in which the received and transmitted multimedia files (image files, video files, voice messages, photos associated with the WhatsApp account holder profile, wallpaper).
- Directory 'Profile Pictures' ( '/ mnt / sdcard / WhatsApp / Profile Pictures /' ). Contains image files associated with the WhatsApp account holder profile.
- Sometimes the directory 'files' ( '/ mnt / sdcard / WhatsApp / Files /' ) may be present on the SD card . This directory contains files that store program settings and user preferences.
Features of data storage in some models of mobile devices
On some Android mobile devices, WhatsApp artifacts may be stored elsewhere. This is due to a change in the storage space of application data by the system software of the mobile device. So, for example, Xiaomi mobile devices have the function of creating a second workspace (“SecondSpace”). When this function is activated, the location of the data changes. So, if in a regular mobile device running Android OS user data is stored in the directory '/ data / user / 0 /' (which is a link to the usual '/ data / data /' ), then in the second workspace application data is stored in the directory '/ data / user / 10 /' . That is, for example, the location of the file 'wa.db':
- in a regular Android smartphone: /data/user/0/com.whatsapp/databases/wa.db ' (which is equivalent to ' /data/data/com.whatsapp/databases/wa.db ') ;
- in the second workspace of the Xiaomi smartphone: '/data/user/10/com.whatsapp/databases/wa.db' .
WhatsApp artifacts on iOS device
Unlike Android OS, in iOS WhatsApp application data is transferred to a backup copy (iTunes backup). Therefore, extracting data from this application does not require extracting the file system or creating a physical memory dump of the device under investigation. Most of the relevant information is contained in the 'ChatStorage.sqlite' database , which is located along the path: '/private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/' (in some programs this path is displayed as ' AppDomainGroup -group.net.whatsapp.WhatsApp.shared ' ).
The structure of 'ChatStorage.sqlite' :
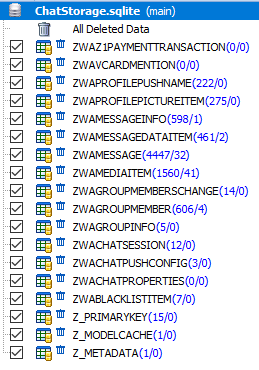
The most informative in the ChatStorage.sqlite database are the tables ZWAMESSAGE and ZWAMEDIAITEM .
Appearance of the table 'ZWAMESSAGE' :
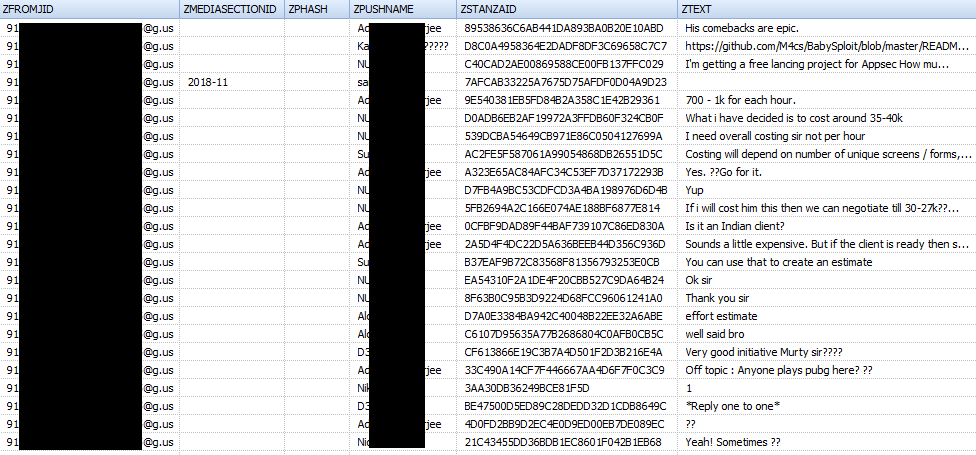
Table structure 'ZWAMESSAGE'
| Field name | Value |
|---|---|
| Z_PK | record serial number (in SQL table) |
| Z_ENT | table identifier, value '9' |
| Z_OPT | unknown, usually contains values from '1' to '6' |
| ZCHILDMESSAGESDELIVEREDCOUNT | unknown, usually contains the value '0' |
| ZCHILDMESSAGESPLAYEDCOUNT | unknown, usually contains the value '0' |
| ZCHILDMESSAGESREADCOUNT | unknown, usually contains the value '0' |
| ZDATAITEMVERSION | unknown, usually contains the value '3', probably a text message pointer |
| ZDOCID | is unknown |
| ZENCRETRYCOUNT | unknown, usually contains the value '0' |
| ZFILTEREDRECIPIENTCOUNT | unknown, usually contains values '0', '2', '256' |
| Zisfromme | message direction: '0' - incoming, '1' - outgoing |
| ZMESSAGEERRORSTATUS | message transfer status. If the message is sent / received, it has a value of '0' |
| ZMESSAGETYPE | message type |
| Zsort | is unknown |
| ZSPOTLIGHSTATUS | is unknown |
| ZSTARRED | unknown not used |
| Zchatsession | is unknown |
| ZGROUPMEMBER | unknown not used |
| ZLASTSESSION | is unknown |
| ZMEDIAITEM | is unknown |
| ZMESSAGEINFO | is unknown |
| ZPARENTMESSAGE | unknown not used |
| ZMESSAGEDATE | OS X Epoch Time Timestamp |
| ZSENTDATE | OS X Epoch Time message sending time |
| ZFROMJID | WhatsApp Sender ID |
| ZMEDIASECTIONID | contains the year and month of sending the media file |
| Zphash | unknown not used |
| ZPUSHPAME | name of the contact who sent the UTF-8 media file |
| ZSTANZID | unique identifier of the message |
| ZTEXT | Message text |
| ZTOJID | Whatsapp ID Recipient |
| OFFSET | bias |
Appearance of the table 'ZWAMEDIAITEM' :
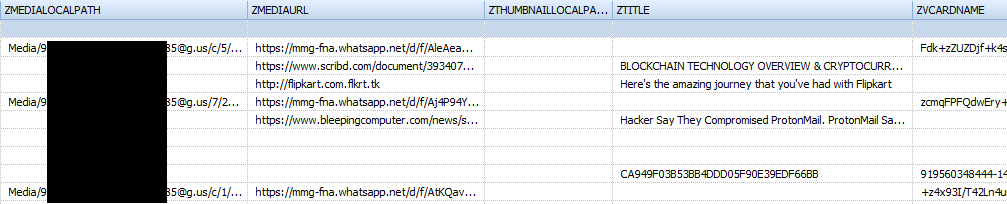
Table structure 'ZWAMEDIAITEM'
| Field name | Value |
|---|---|
| Z_PK | record serial number (in SQL table) |
| Z_ENT | table identifier, value '8' |
| Z_OPT | неизвестно, обычно содержит значения от ‘1’ до ‘3’. |
| ZCLOUDSTATUS | содержит значение ‘4’ если файл загружен. |
| ZFILESIZE | содержит длину файла (в байтах) для загруженных файлов |
| ZMEDIAORIGIN | неизвестно, обычно имеет значение ‘0’ |
| ZMOVIEDURATION | продолжительность медиафайла, для pdf файлов может содержать число страниц документа |
| ZMESSAGE | содержит порядковый номер (номер отличается от того, который указан в колонке ‘Z_PK’) |
| ZASPECTRATIO | соотношение сторон, не используется, обычно имеет значение ‘0’ |
| ZHACCURACY | неизвестно, обычно имеет значение ‘0’ |
| ZLATTITUDE | ширина в пикселях |
| ZLONGTITUDE | высота в пикселях |
| ZMEDIAURLDATE | временная метка в формате OS X Epoch Time |
| ZAUTHORNAME | автор (для документов, может содержать название файла) |
| ZCOLLECTIONNAME | не используется |
| ZMEDIALOCALPATH | имя файла (с указанием пути) в файловой системе устройства |
| ZMEDIAURL | The URL where the media file was located. If the file was transferred from one subscriber to another, it was encrypted, and its extension will be indicated as the extension of the transferred file - .enc |
| ZTHUMBNAILLOCALPATH | path to file thumbnail in device file system |
| ZTITLE | file header |
| ZVCARDNAME | media file hash; when transferring a file to a group, it may contain the sender ID |
| ZVCARDSTRING | contains information about the type of file being transferred (for example, image / jpeg); when transferring a file to a group, it may contain the recipient identifier |
| ZXMPPTHUMBPATH | path to file thumbnail in device file system |
| ZMEDIAKEY | unknown, probably contains the key to decrypt the encrypted file. |
| ZMETADATA | message metadata |
| Offset | bias |
Other interesting 'ChatStorage.sqlite' database tables are:
- 'ZWAPROFILEPUSHNAME' . Corresponds to WhatsApp ID with the name of the contact;
- 'ZWAPROFILEPICTUREITEM' . Correlates WhatsApp ID with contact avatar;
- 'Z_PRIMARYKEY' . The table contains general information about this database, such as the total number of messages stored, the total number of chats, etc.
Also, when researching WhatsApp on a mobile device running iOS, you need to pay attention to the following files:
- File 'BackedUpKeyValue.sqlite' . Contains cryptographic keys and other data that is necessary to identify the account owner. It is located along the path: /private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/ .
- Файл ‘ContactsV2.sqlite’. Содержит информацию о контактах пользователя, такую как ФИО, номер телефона, статус контакта (в виде текста), WhatsApp ID и т.д. Располагается по пути: /private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/.
- Файл ‘consumer_version’. Содержит номер версии установленного приложения WhatsApp. Располагается по пути: /private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/.
- Файл ‘current_wallpaper.jpg’. Содержит текущие обои фона программы WhatsApp. Располагается по пути: /private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/. В старых версиях приложения используется файл ‘wallpaper’, который располагается по пути: '/private/var/mobile/Applications/net.whatsapp.WhatsApp/Documents/'.
- Файл ‘blockedcontacts.dat’. Содержит информацию о заблокированных контактах. Располагается по пути: /private/var/mobile/Applications/net.whatsapp.WhatsApp/Documents/.
- Файл ‘pw.dat’. Содержит зашифрованный пароль. Располагается по пути: ‘/private/var/mobile/Applications/net.whatsapp.WhatsApp/Library/’.
- File 'net.whatsapp.WhatsApp.plist' (or file 'group.net.whatsapp.WhatsApp.shared.plist' ). Contains information about the WhatsApp account profile. The file is located on the path: '/private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/Library/Preferences/' .
The contents of the file 'group.net.whatsapp.WhatsApp.shared.plist'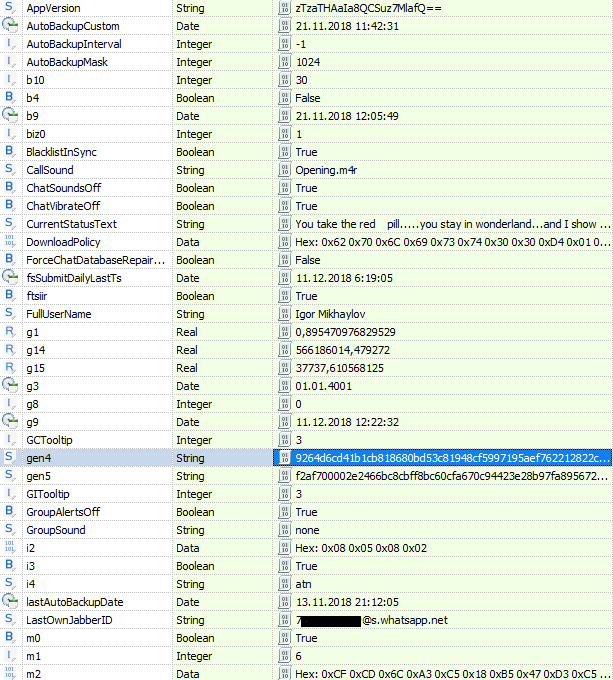

You should also pay attention to the following directories:
- Directory '/private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/Media/Profile/' . It contains thumbnails of contacts, groups (files with the .thumb extension ), avatars of contacts, an avatar of the owner of the WhatsApp account (file 'Photo.jpg' ).
- Каталог ‘/private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/ Message/Media/’. Содержит мультимедиа-файлы и их миниатюры
- Каталог ‘/private/var/mobile/Applications/net.whatsapp.WhatsApp/Documents/’. Содержит журнал работы программы (файл ‘calls.log’) и резервные копии журналов работы программы (файл ‘calls.backup.log’).
- Каталог ‘/private/var/mobile/Applications/group.net.whatsapp.WhatsApp.shared/stickers/’. Содержит стикеры (файлы в формате ‘.webp’).
- Каталог ‘/private/var/mobile/Applications/net.whatsapp.WhatsApp/Library/Logs/’. Содержит журналы работы программы.
Артефакты WhatsApp в Windows
- 'C: \ Program Files (x86) \ WhatsApp \'
- 'C: \ Users \% User profile% \ AppData \ Local \ WhatsApp \'
- 'C: \ Users \% User profile% \ AppData \ Local \ VirtualStore \ Program Files (x86) \ WhatsApp \'
In the directory 'C: \ Users \% User profile% \ AppData \ Local \ WhatsApp \' is located the log file 'SquirrelSetup.log' , which contains information about checking for updates and installing the program.
In the directory 'C: \ Users \% User profile% \ AppData \ Roaming \ WhatsApp \' there are several subdirectories:
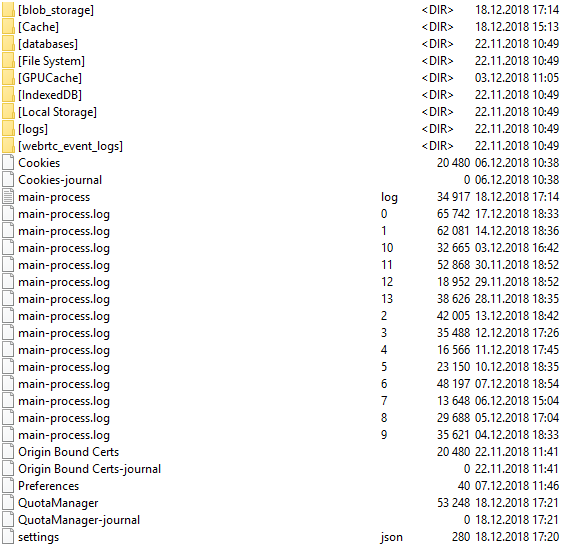
The file 'main-process.log' contains information about the operation of the WhatsApp program.
The subdirectory 'databases' contains the file 'Databases.db' , but this file does not contain any information about chats or contacts.
The most interesting from the forensic point of view are the files located in the 'Cache' directory . Basically, these are files with the names 'f _ *******' (where * is a number from 0 to 9) containing encrypted multimedia files and documents, but among them there are also unencrypted files. Of particular interest are the files 'data_0' , 'data_1' , 'data_2' , 'data_3'located in the same subdirectory. Files 'data_0' , 'data_1' , 'data_3' contain external links to transmitted encrypted multimedia files and documents.
Example information contained in the file 'data_1'

Also, the file 'data_3' may contain image files.
The file 'data_2' contains contact avatars (can be restored by searching the file headers).
Avatars contained in the file 'data_2' :

Thus, the chats themselves cannot be found in the computer’s memory, but you can find:
- multimedia files;
- Documents transmitted using WhatsApp
- Information about the contacts of the account owner.
WhatsApp Artifacts on MacOS
On MacOS, you can find WhatsApp artifact types similar to those found on Windows.
Program files are located in directories:
- 'C: \ Applications \ WhatsApp.app \'
- 'C: \ Applications \ ._ WhatsApp.app \'
- 'C: \ Users \% User profile% \ Library \ Preferences \'
- 'C: \ Users \% User profile% \ Library \ Logs \ WhatsApp \'
- 'C: \ Users \% User profile% \ Library \ Saved Application State \ WhatsApp.savedState \'
- 'C: \ Users \% User profile% \ Library \ Application Scripts \'
- 'C: \ Users \% User profile% \ Library \ Application Support \ CloudDocs \'
- 'C: \ Users \% User profile% \ Library \ Application Support \ WhatsApp.ShipIt \'
- 'C: \ Users \% User profile% \ Library \ Containers \ com.rockysandstudio.app-for-whatsapp \'
- ‘C:\Users\%User profile%\ Library\ Mobile Documents\ <текстовая переменная> WhatsApp\ Accounts’
В этом каталоге находятся подкаталоги, имена которых представляют собой номера телефонов, ассоциированных с владельцем аккаунта WhatsApp. - ‘C:\Users\%User profile%\Library\Caches\WhatsApp.ShipIt\’
В этом каталоге содержится информация об инсталляции программы. - ‘C:\Users\%User profile%\Pictures\Медиатека iPhoto.photolibrary\Masters\’, ‘C:\Users\%User profile%\Pictures\Медиатека iPhoto.photolibrary\Thumbnails\’
В этих каталогах содержатся служебные файлы программы и, в том числе, фотографии и миниатюры контактов WhatsApp. - ‘C:\Users\%User profile%\Library\Caches\WhatsApp\’
В этом каталоге находятся несколько SQLite-баз, которые используются для кэширования данных. - ‘C:\Users\%User profile%\Library\Application Support\WhatsApp\’
В этом каталоге находится несколько подкаталогов: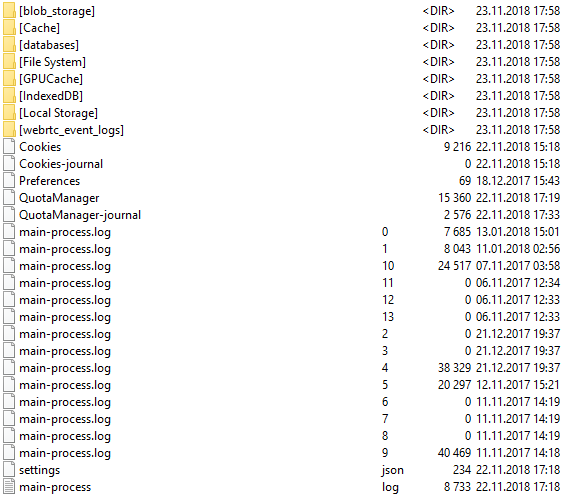
В каталоге ‘C:\Users\%User profile%\Library\Application Support\WhatsApp\Cache\’ находятся файлы ‘data_0’, ‘data_1’, ‘data_2’, ‘data_3’ и файлы с именами ‘f_*******’ (где * — число от 0 до 9). Информация о том, какие сведения содержат эти файлы, описана в разделе «Артефакты WhatsApp в Windows».
В каталоге ‘C:\Users\%User profile%\Library\Application Support\WhatsApp\IndexedDB\’ могут содержаться мультимедийные файлы (файлы не имеют расширений).
Файл ‘main-process.log’ содержит информацию о работе программы WhatsApp.
Источники
- Forensic analysis of WhatsApp Messenger on Android smartphones, by Cosimo Anglano, 2014.
- Whatsapp Forensics: Eksplorasi sistem berkas dan basis data pada aplikasi Android dan iOS by Ahmad Pratama, 2014.
The following articles in this series:
Decryption of encrypted WhatsApp databases
An article that will provide information on how the WhatsApp encryption key is generated, and practical examples are given that show how to decrypt the encrypted databases of this application.
Extract WhatsApp data from cloud storage
An article in which we describe what WhatsApp data is stored in the clouds and describe methods for extracting this data from cloud storage.
WhatsApp Data Extraction: Case Studies
An article that will step by step describe what programs and how to extract WhatsApp data from various devices.
