And who did this? Automate information security audit

Source
It is believed that there are three approaches to the diagnosis of information security: audit, vulnerability assessment and penetration tests. Let's talk about audit and vulnerability assessment. Under the cut, we will consider the issues that need to be addressed within the framework of the audit, and the Quest Software toolkit for detecting, preventing and investigating information security incidents based on machine learning (Change Auditor Threat Detection), collecting logs from infrastructure objects (InTrust), and auditing the current configuration (Enterprise Reporter) and output of audit data for all listed systems in one interface (IT Security Search).
An IT security audit determines whether the information system and its maintenance meet customer expectations and company standards. From our point of view, the audit system should have the following capabilities:
- identify and identify normal and atypical activity;
- construct queries and filter data in an array of events to obtain the necessary information;
- escalate events to a group of responsible;
- have pre-configured reports that can identify atypical activity.
The peculiarity of working with infobes, which we often see, is the performance of an audit on the residual principle. That is, the audit of changes is performed by the department, which is also loaded with other tasks. The first problem arises from this -
The use of built-in audit tools
There is not enough time to find and configure others. By built-in tools we mean, for example, Windows snap-ins or special scripts on Power Shell. Of course, with the help of such tools you can only find out about the incident after the fact.
As the organization grows, the number of users and changes grows. There are studies on this subject with specific figures, but even without this it is clear that digital exchange is changing upward every year. The second audit challenge is
The increase in the number of changes due to the growth of infrastructure
The growth may be associated with an increase in the staff or number of customers, but regardless of this, the amount of changes will be proportionally increased.
The audit is seriously influenced not only by internal factors (these are the first two problems), but also by external ones - the requirements of state bodies or corporate policies. And we come to the third audit problem -
Lack of suitable tools to meet the requirements.
In the absence of suitable tools, system administrators either do not control the required changes or do it using improvised means (see problem 1).
And now we move on to a review of tools that can help with the answer to the question: “Who did this?” (In fact, they will help with the answer to a bunch of other questions).
Operational audit of information security events
When we come to some companies for installation meetings, we see an audit system based on Power Shell. Scripts are usually supported by a single Windows administrator. This is not a serious problem until the dismissal of this employee. After his departure, the question arises: who will continue to support and develop this. The new administrator (if he has sufficient competence) usually writes these scripts again. And these are not isolated cases.
Change Auditor is a tool for online audit of changes in the Microsoft environment and on disk arrays, which does not require knowledge of a single person.
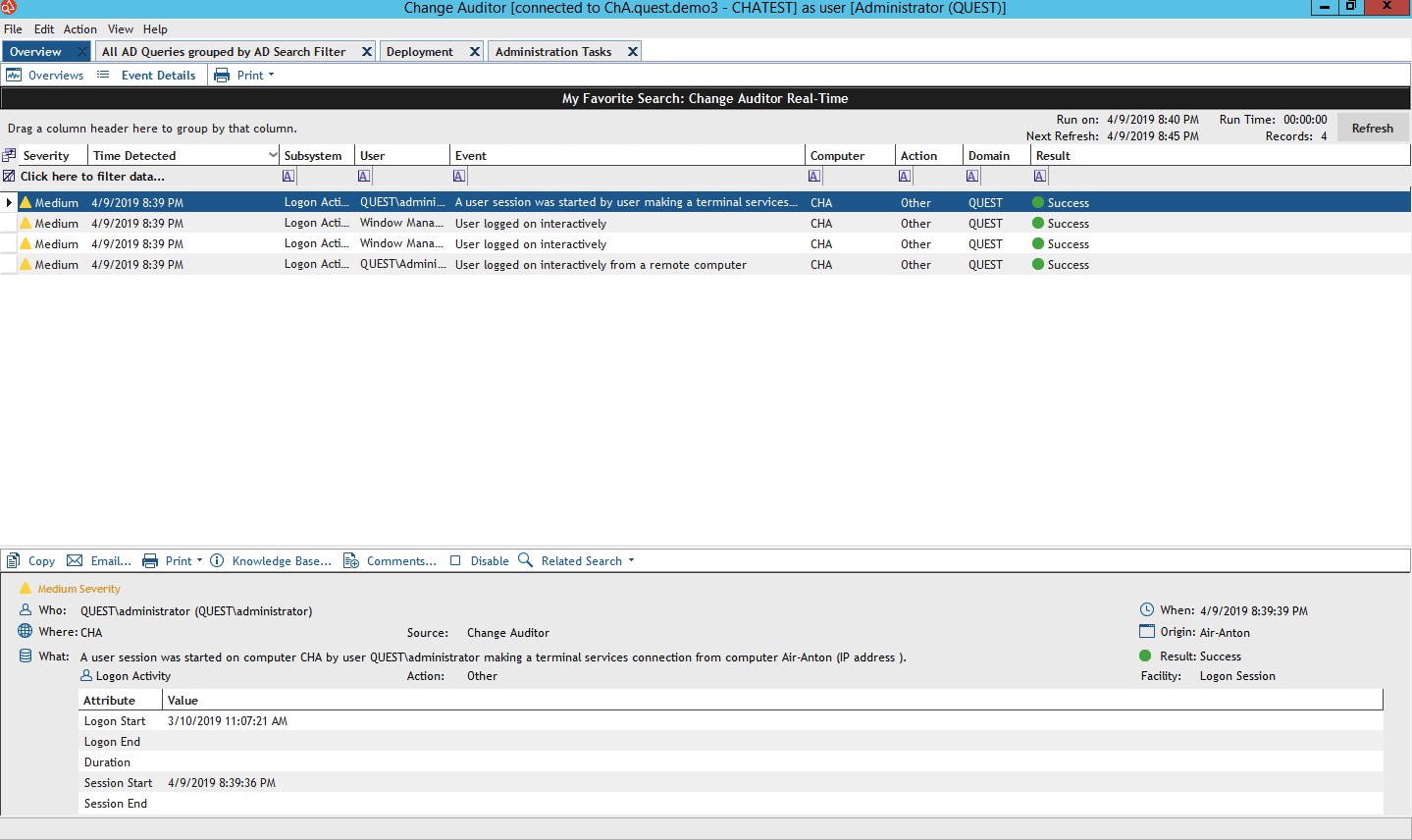
Audit supported: AD, Azure AD, SQL Server, Exchange, Exchange Online, Sharepoint, Sharepoint Online, Windows File Server, OneDrive for Business, Skype for Business, VMware, NetApp, EMC, FluidFS. Suitable for hybrid environments. There are predefined reports for compliance with GDPR, SOX, PCI, HIPAA, FISMA, GLBA standards.
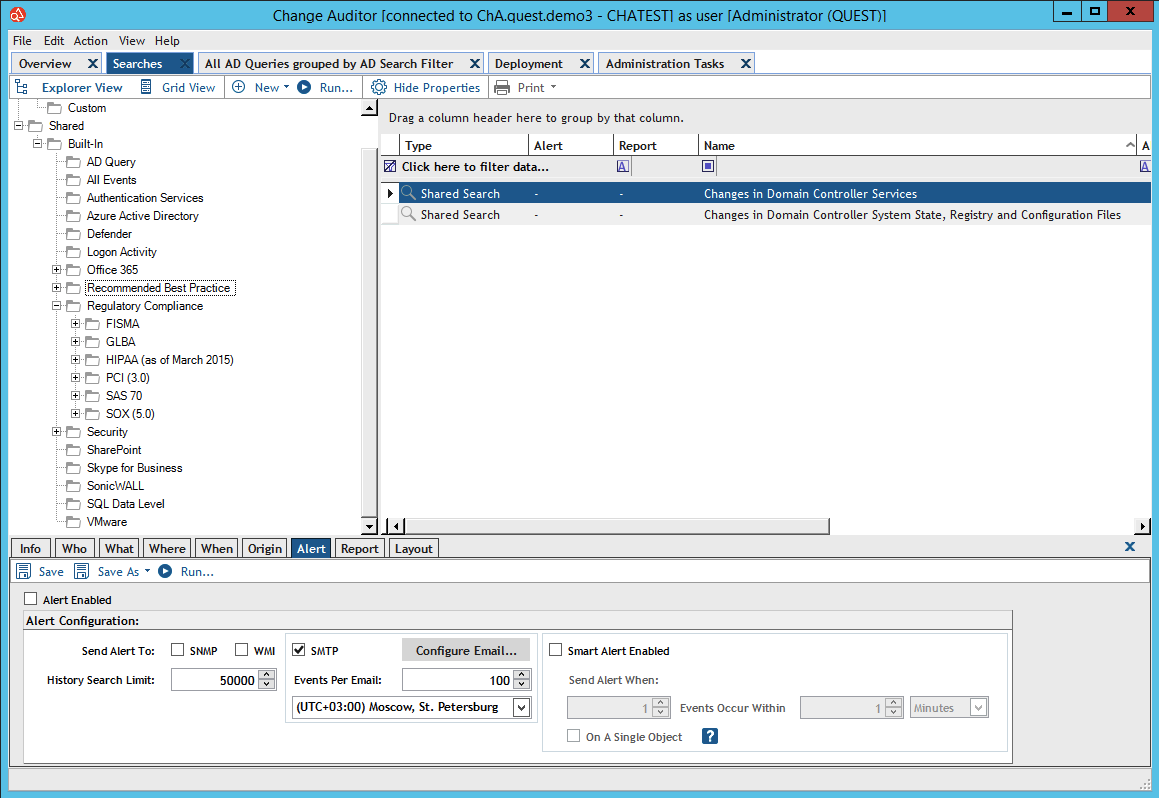
In addition to auditing, Change Auditor can block changes. For example, prohibit adding new users to the AD group or prohibit changing the file / folder.
Change Auditor has an additional analytics module - Threat Detection.
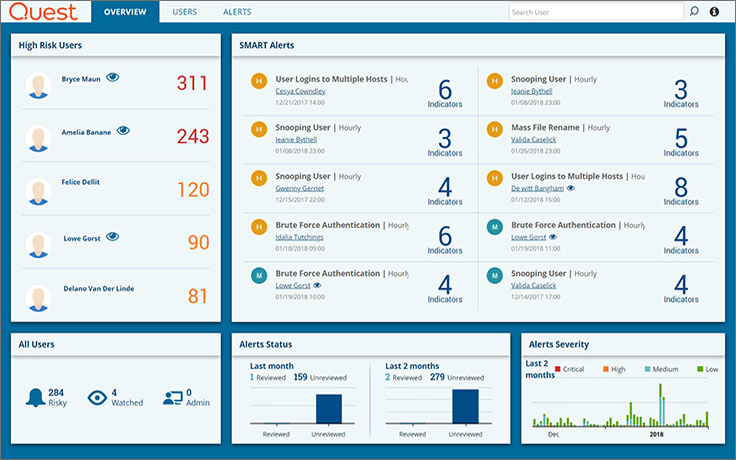
Powered by machine learning (ML) and user behavior analysis (UEBA). It receives events from Change Auditor over the past 30 days and reveals atypical user behavior: entering from an unusual place or at an unusual time, unsuccessful password entry several times in a row on a domain controller, entering a forbidden file resource, etc. The module analyzes events in several dimensions and reports anomalies.
Audit infrastructure configuration
For those who have long wanted to clean up their Windows infrastructure, but still can’t get their hands on it. Enterprise Reporter, a reporting tool, retrieves object data from AD, Azure AD, SQL Server, Exchange, Exchange Online, Windows File Server, OneDrive for Business and Azure resources (virtual machines, network security groups and other objects) and builds beautiful reports.
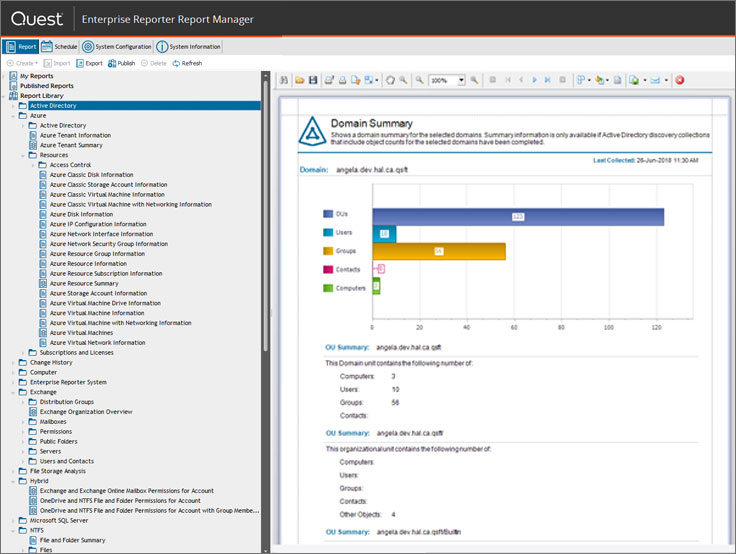
The main value of the product is the existing set of reports, which allows you to see vulnerabilities immediately after installation. For example, at one of our customers, we found users in domain administrator groups with the password expiration option disabled.
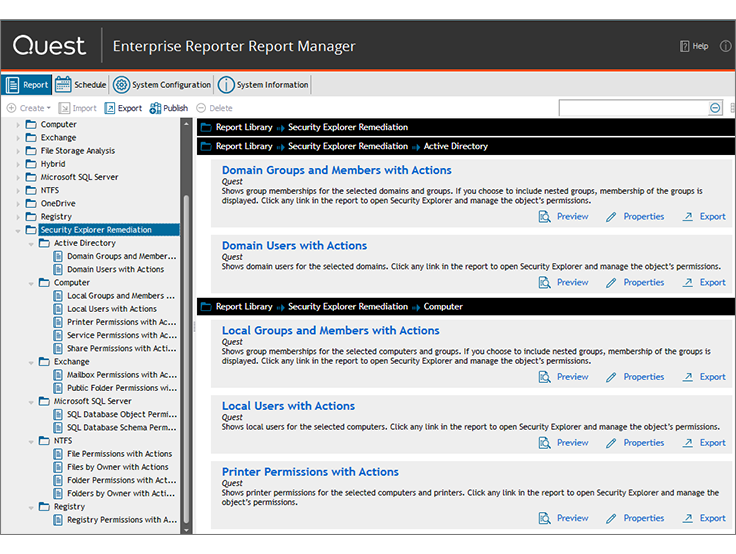
From ready-made reports:
- Users who have not been logged in for the past 30 days
- users with an expired password;
- privileged group users who have not been logged in for the last 30 days;
- Windows services that do not work under local system accounting;
- Software installed on servers with the domain controller role;
- Hotfixes installed on servers
- Security settings on servers
- nested groups and users in nested groups
- Active Directory permissions
- permissions for folders on file storage and others.
Examples of the listed reports can be found on the Quest website in the PDF report (the file opens immediately, registration is not needed). There are predefined reports for compliance with GDPR, SOX, PCI-DSS, HIPAA, FISMA, GLBA and others. And if you have reporting requirements in your company or want to brand a document - there is a special designer.
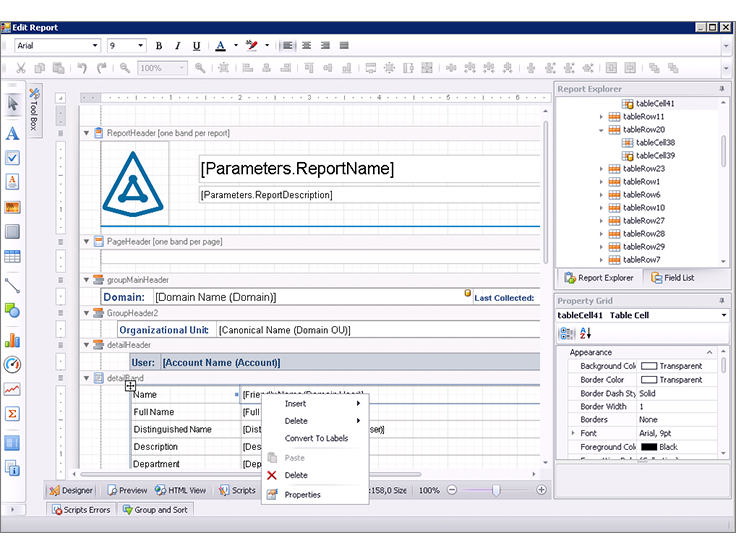
Log collection and analysis
Another source of data on information security events is logs. In them you can find if not everything, then almost everything. After collecting them, it would be nice to normalize and structure them in order to correlate between events, for example, in AD and some text log.
InTrust is a tool for collecting and analyzing logs from heterogeneous sources. It can pick up Windows logs, text logs and syslog from network devices. After collection, all statistics (events) are reduced to the state of the form: when it happened, what happened, where it happened, who performed the action, where the action was taken from.
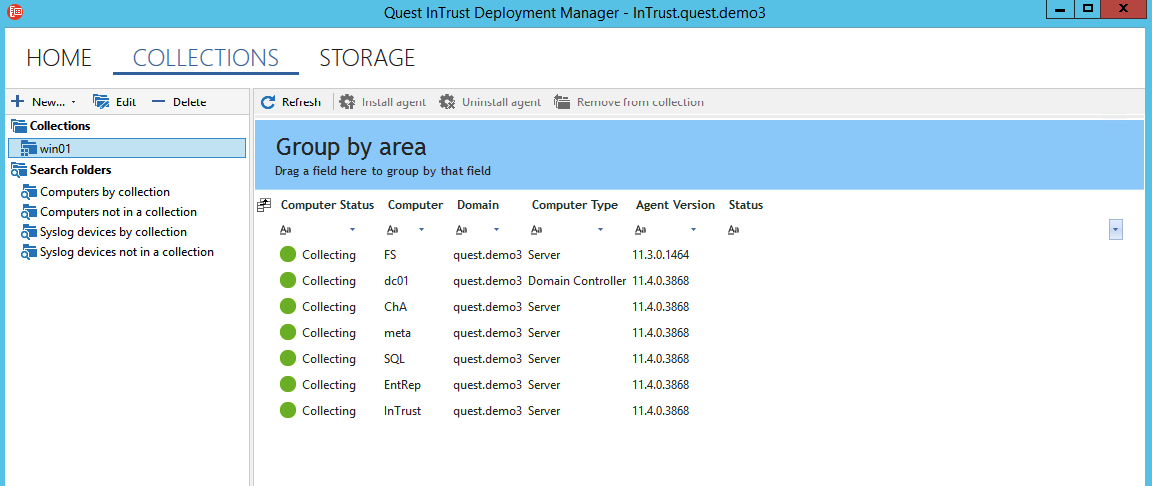
InTrust can handle up to 60,000 events per second from 10,000 sources. Often, collector agents are installed on workstations in order to monitor the events of the Windows eventlog Sysmon (tracking changes in registry values, creating new processes with incorrect hashes and others), PowerShell logs.
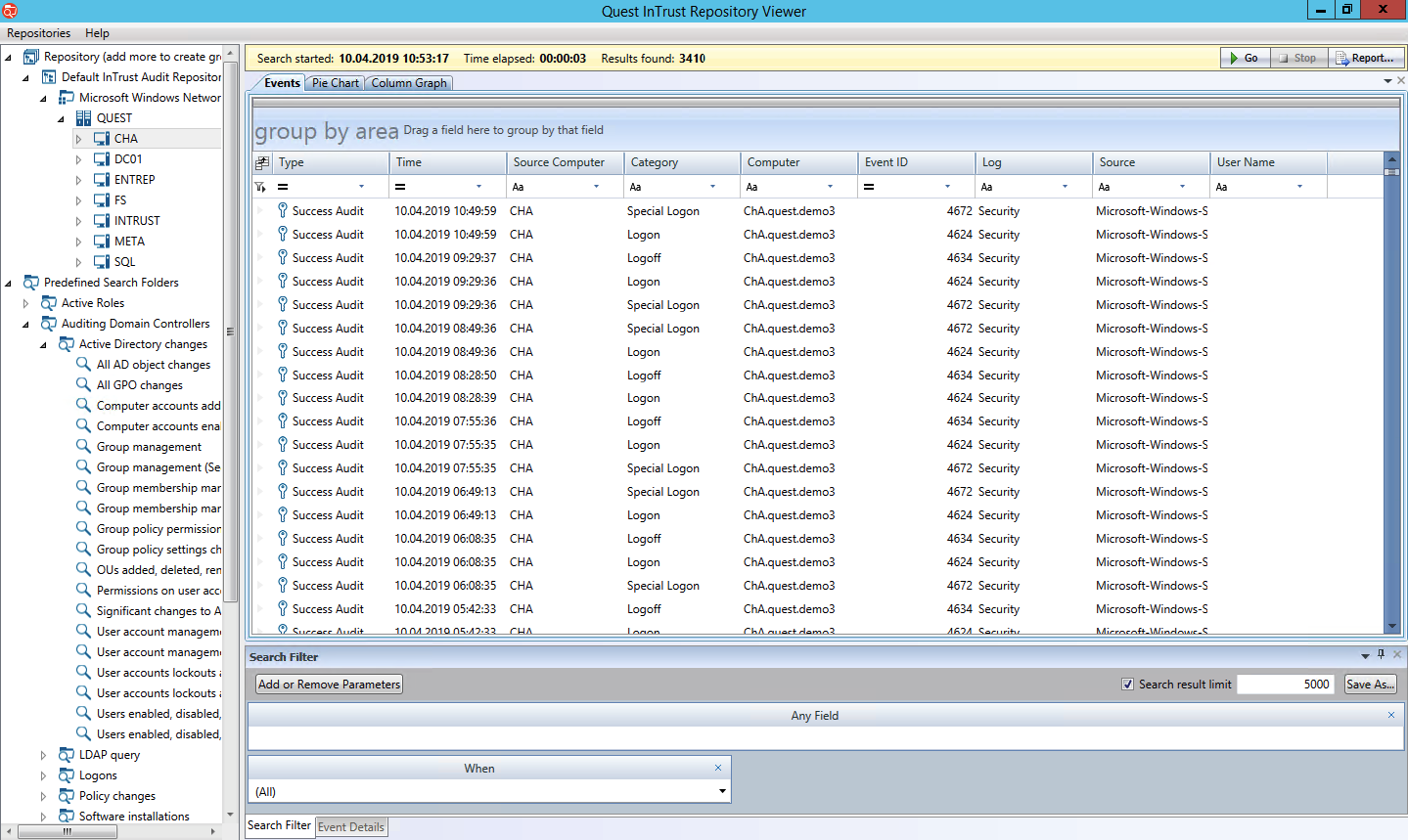
Raw data is stored in the built-in storage with a compression ratio of 20: 1. There are ready-made integrations with some SIEM systems. If you use them, InTrust is a convenient way to save on licenses, as stores raw data in its storage and sends only events to SIEM.
Pool under the umbrella
To make the security concept complete, it is desirable to combine data from all sources and observe what is happening in one window. Additionally, correlate events for lightning-fast detection of the root cause.
IT Security Search - a tool for global full-text search a'la Google according to operational audit, audit of infrastructure configuration and data from the logs. All data is retrieved in real time from connected systems.

You can enter the name of the user, workstation, type of event, or anything else and find events or configurations related by this attribute. When generating queries, you can use logical expressions. It is convenient to build reports from the query results and send them to interested parties on a schedule.
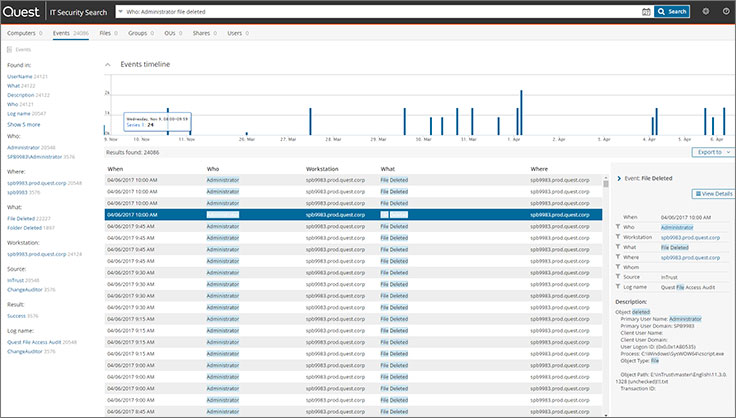
From the IT Security Search interface, you can also roll back changes to AD. That is, for example, you can restore a user deleted by mistake with all its attributes. This is achieved through integration with another Quest product - Recovery Manager for Active Directory.
The main goal of the article is to introduce the Quest product family to audit changes. Those tools that you use now may have a different set of functions (somewhere more, somewhere less). Write in the comments what you have to deal with, what functions have been useful to you and why you chose one or another solution. It is interesting to exchange experiences.
