US Telecoms to Combat Telephone Spam
Subscriber authentication technology - the SHAKEN / STIR protocol - is gaining momentum in the United States. Let's talk about the principles of its work and the potential difficulties of implementation. / Flickr / Mark Fischer / CC BY-SA

Unwanted robo-calls are the most common cause of consumer complaints to the US Federal Trade Commission. In 2016, the organization recorded five million calls , a year later this figure exceeded seven million.
These spam calls take people more than just time. Automatic calling services are used to extort money. According to YouMail, in September last year, 40% of the four billion robo-calls were made by scammers . During the summer of 2018, New Yorkers lost about three million dollars in transfers to criminals who called them on behalf of the authorities and extorted money.
The problem was brought to the attention of the US Federal Communications Commission (FCC). Representatives of the organization made a statement.in which they demanded that telecommunications companies implement a solution to combat telephone spam. This decision was the SHAKEN / STIR protocol. In March , AT&T and Comcast conducted its joint testing .
Telecommunications operators will work with digital certificates (they are built on the basis of cryptography with a public key), which will allow verification of callers.
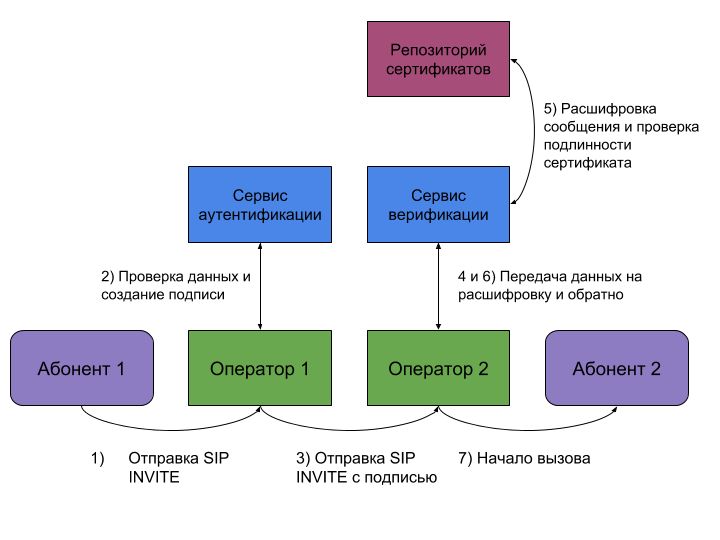
The verification procedure will be as follows. First, the operator of the person making the call receives a SIP INVITE request to establish a connection. The provider authentication service checks the information about the call - location, organization, data about the caller’s device. Based on the results of the verification, the call is assigned one of three categories: A - all information about the caller is known, B - the organization and location are known, and C - only the subscriber’s geographical location is known.
After that, the operator adds a message with a time stamp, call category and a link to the electronic certificate to the INVITE request header. Here is an example of such a message from the GitHub repository of one of the American telecoms:
Next, the request goes to the called party provider. The second operator decrypts the message using a public key, compares the contents with SIP INVITE and verifies the authenticity of the certificate. Only after this, a connection is established between the subscribers, and the "receiving" side receives a notification about who is calling him.
The entire verification process can be depicted in the diagram:
According to experts, the verification of the caller will take no more than 100 milliseconds.
As noted in the USTelecom association, SHAKEN / STIR will give people more control over the calls they receive - it will become easier for them to decide whether to pick up the phone.
But in the industry there is an opinion that the protocol will not become a "silver bullet." Experts say that scammers will simply take advantage of workarounds. Spammers will be able to register a “fake” automatic telephone exchange in the operator’s network in the name of an organization and make all calls through it. In case of blocking the exchange, you can simply re-register.
According to a representative of one of the telecoms, simply verifying a subscriber using certificates is not enough. To stop scammers and spammers, you must allow providers to automatically block such calls. But for this, the Communications Commission will have to develop a new set of rules that will allow to regulate this process. And this issue in the FCC may be addressed in the near future.
Since the beginning of the year, congressmen have been consideringa new bill that will oblige the Commission to develop mechanisms to protect citizens from robotic calls and monitor the implementation of the SHAKEN / STIR standard.

/ Flickr / Jack Sem / CC BY
It is worth noting that SHAKEN / STIR has been implemented in T-Mobile - for some smartphones and plans to expand a number of supported devices - and Verizon - its operator’s clients can download a special application that will alert you to calls from suspicious numbers. Other US carriers are still testing the technology. It is expected that they will complete the tests before the end of 2019.

Problem with calls
Unwanted robo-calls are the most common cause of consumer complaints to the US Federal Trade Commission. In 2016, the organization recorded five million calls , a year later this figure exceeded seven million.
These spam calls take people more than just time. Automatic calling services are used to extort money. According to YouMail, in September last year, 40% of the four billion robo-calls were made by scammers . During the summer of 2018, New Yorkers lost about three million dollars in transfers to criminals who called them on behalf of the authorities and extorted money.
The problem was brought to the attention of the US Federal Communications Commission (FCC). Representatives of the organization made a statement.in which they demanded that telecommunications companies implement a solution to combat telephone spam. This decision was the SHAKEN / STIR protocol. In March , AT&T and Comcast conducted its joint testing .
How the SHAKEN / STIR protocol works
Telecommunications operators will work with digital certificates (they are built on the basis of cryptography with a public key), which will allow verification of callers.
The verification procedure will be as follows. First, the operator of the person making the call receives a SIP INVITE request to establish a connection. The provider authentication service checks the information about the call - location, organization, data about the caller’s device. Based on the results of the verification, the call is assigned one of three categories: A - all information about the caller is known, B - the organization and location are known, and C - only the subscriber’s geographical location is known.
After that, the operator adds a message with a time stamp, call category and a link to the electronic certificate to the INVITE request header. Here is an example of such a message from the GitHub repository of one of the American telecoms:
{
"alg": "ES256",
"ppt": "shaken",
"typ": "passport",
"x5u": "https://cert-auth.poc.sys.net/example.cer"
}
{
"attest": "A",
"dest": {
"tn": [
"1215345567"
]
},
"iat": 1504282247,
"orig": {
"tn": "12154567894"
},
"origid": "1db966a6-8f30-11e7-bc77-fa163e70349d"
}
Next, the request goes to the called party provider. The second operator decrypts the message using a public key, compares the contents with SIP INVITE and verifies the authenticity of the certificate. Only after this, a connection is established between the subscribers, and the "receiving" side receives a notification about who is calling him.
The entire verification process can be depicted in the diagram:

According to experts, the verification of the caller will take no more than 100 milliseconds.
Opinions
As noted in the USTelecom association, SHAKEN / STIR will give people more control over the calls they receive - it will become easier for them to decide whether to pick up the phone.
Read on our blog:
But in the industry there is an opinion that the protocol will not become a "silver bullet." Experts say that scammers will simply take advantage of workarounds. Spammers will be able to register a “fake” automatic telephone exchange in the operator’s network in the name of an organization and make all calls through it. In case of blocking the exchange, you can simply re-register.
According to a representative of one of the telecoms, simply verifying a subscriber using certificates is not enough. To stop scammers and spammers, you must allow providers to automatically block such calls. But for this, the Communications Commission will have to develop a new set of rules that will allow to regulate this process. And this issue in the FCC may be addressed in the near future.
Since the beginning of the year, congressmen have been consideringa new bill that will oblige the Commission to develop mechanisms to protect citizens from robotic calls and monitor the implementation of the SHAKEN / STIR standard.

/ Flickr / Jack Sem / CC BY
It is worth noting that SHAKEN / STIR has been implemented in T-Mobile - for some smartphones and plans to expand a number of supported devices - and Verizon - its operator’s clients can download a special application that will alert you to calls from suspicious numbers. Other US carriers are still testing the technology. It is expected that they will complete the tests before the end of 2019.
What else to read in our blog on Habré:
