Is quantum cryptography really reliable?

For thousands of years, the best minds of mankind have been inventing ways to protect information from prying eyes, but each time there is a way to uncover the secret of the cipher and read secret documents. Another holy grail of cryptographers around the world is quantum cryptography, in which information is transmitted using photons. The fundamental properties of a photon as a quantum particle are such that the measurement of characteristics inevitably changes its state. In other words, it is impossible to secretly intercept information transmitted through a quantum channel, because this will change it. Or is it still possible?
The principles of quantum cryptography
For the first time, the idea of using quantum objects to protect information was expressed by Stephen Wiesner in 1970. He came up with the idea of quantum security banknotes that cannot be faked. A lot of time has passed since then, but no one has come up with a way to place quantum objects on banknotes, however, the idea that Wiesner shared with his former classmate Charles Bennett, a few years later turned into a way of protecting information, called quantum cryptography.
Encryption with a one-time quantum cipher notepad
In 1984, Bennett, together with Gilles Brassard of the University of Montreal, finalized Wiesner's idea for transmitting encrypted messages using quantum technology. They proposed using quantum channels to exchange one-time encryption keys, and the length of such keys should be equal to the length of the message. This allows you to transfer encrypted data in a one-time cipher-notepad mode. This encryption method provides mathematically proven cryptographic strength, that is, it is resistant to cracking with unlimited computational capabilities of the cracker.
We decided to use a photon as a quantum particle for transmitting information. It could be easily obtained using the available equipment (lamps, lasers, etc.), and its parameters were completely measurable. But for the transmission of information, a coding method was required, allowing to obtain zeros and ones.
Unlike conventional electronics, where zeros and ones are encoded in the form of different signal potentials or in the form of pulses of a certain direction, such encoding is impossible in quantum systems. A photon parameter was required, which can be set during its generation, and then measured with the required degree of reliability. This parameter turned out to be polarization.
Simplifying greatly, polarization can be considered as the orientation of a photon in space. A photon can be polarized at angles of 0, 45, 90, 135 degrees. By measuring a photon, only two mutually perpendicular states or bases can be distinguished:
- plus basis - the photon is polarized vertically or horizontally;
- basis “cross” - the photon is polarized at angles of 45 or 135 degrees.
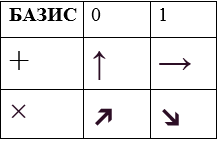
It is impossible to distinguish a horizontal photon from a photon polarized at an angle of 45 degrees.
These photon properties formed the basis of the BB84 quantum key distribution protocol developed by Charles Bennett and Gilles Brassard. When applied, information is transmitted through polarized photons, and the direction of polarization is used as zero or one. The security of the system is guaranteed by the Heisenberg uncertainty principle , according to which two quantum quantities cannot be simultaneously measured with the necessary accuracy: the more accurately one particle characteristic is measured, the less accurately the second one can be measured. Thus, if someone tries to intercept the key during its transmission, legitimate users will know about it.
In 1991, Arthur Eckert developedAlgorithm E91 , in which the quantum distribution of keys was performed using quantum entanglement, a phenomenon in which the quantum states of two or more photons are interdependent. Moreover, if one of the pair of coupled photons has a value of 0, then the second will definitely be equal to 1, and vice versa.
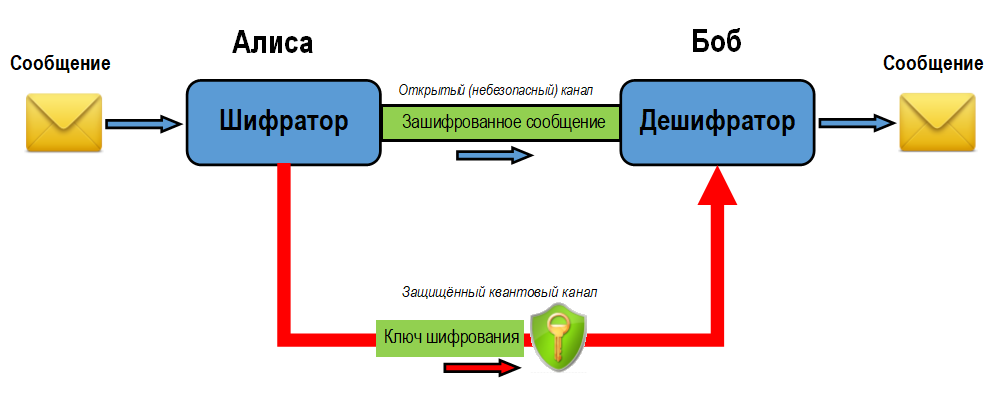
Let's see how the encryption key is generated in a quantum cryptosystem. We assume that the sender of the information is called Alice, the recipient is Bob, and Eve is trying to eavesdrop on their conversation.
According to the BB84 protocol, a secret key is generated as follows:
- Alice generates a random sequence of bits, encoding this information using the corresponding polarizations of the photons and transfers them to Bob using a randomly selected sequence of bases (cross or plus).
- Bob randomly measures the state of each received photon using a randomly selected basis.
- For each photon, Bob, through an open channel, tells Alice in what basis he measured the state of the photon, keeping the measurement result in secret.
- Alice through the open channel tells Bob what measurements should be considered correct. These are the cases for which the transmission and measurement bases coincide.
- The measurement result with matching bases is translated into bits, from which the key is formed.
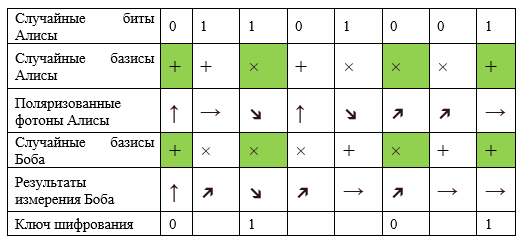
If Eve tries to intercept the secret key, she will need to measure the polarization of the photons. Not knowing the correct basis for each measurement, Eve will receive incorrect data, and the polarization of the photon will change. This error will be immediately noticed by both Alice and Bob.
Since distortions in the quantum system can be introduced not only by a spy, but also by ordinary interference, a way is needed to reliably detect errors. In 1991, Charles Bennett developed an algorithm for detecting distortions in data transmitted through a quantum channel . For verification, all transmitted data is divided into identical blocks, then the sender and receiver in various ways calculate the parity of these blocks and compare the results.
In real quantum cryptosystems, the interaction between subscribers takes place over the optical fiber, when light enters the optical fiber, the polarization is irreversibly broken. Therefore, commercial installations, which we will talk about a little later, use other methods of encoding bits.
For example, ID Quantique uses the phases of light to encode bits:
- Bob generates a light pulse.
- The impulse is divided into two separate impulses, which are sent to Alice.
- Alice randomly changes the phase of one of the received pulses with a delay, choosing one of the bases.
- As in the case of polarization, two bases are used: the first with zero delay or with a delay of 1/2 wavelength, the second with delays of 1/4 or 3/4 wavelength.
- Alice returns impulses to Bob, who randomly selects a delay from the first or second basis and interferes with the impulses.
- If Alice and Bob have chosen the same basis, the phases of the pulses will either completely coincide, or will be out of phase, providing 0 or 1 at the output.
- If the bases are different, the measurement result will be correct in 50% of cases.

Cerberis QKD Key Quantum Distribution System manufactured by ID Quantique. The maximum range of the quantum channel is 50 km, the secret key transmission rate is 1.4 kbit / s. Photo: ID Quantique.
Practical implementation
In 1989, Bennett and Brassard built an installation at the IBM Research Center to test their concept. The setup was a quantum channel, at one end of which was Alice's transmitting apparatus, and Bob's receiving apparatus at the other. The devices were placed on an optical bench about 1 m long in an opaque casing with dimensions of 1.5 × 0.5 × 0.5 m. The system was controlled using a computer into which software representations of legal users and an attacker were downloaded.
Using the installation, it was possible to find out that:
- reception and transmission of quantum information is quite possible even through the air channel;
- the main problem with increasing the distance between the receiver and the transmitter is the conservation of photon polarization;
- preservation of transmission secrecy depends on the intensity of the flashes of light that are used for transmission: weak flashes make it difficult to intercept, but cause an increase in errors for the legal recipient, increasing the intensity of flashes allows you to intercept information by splitting the initial single photon into two.
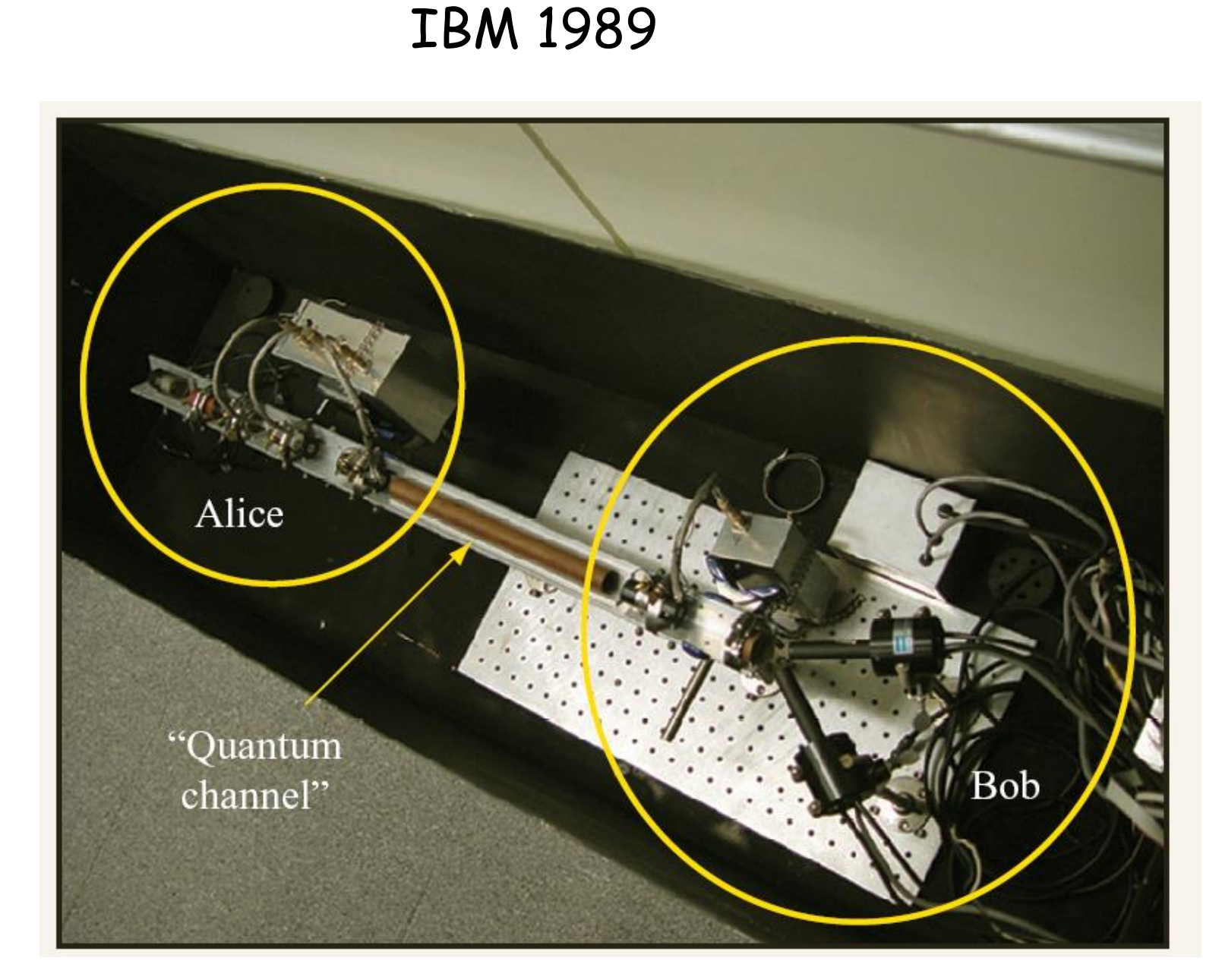 Installation of Bennett and Brassard. Source: IBM Journal of Research and Development (Volume: 48, Issue: 1, Jan. 2004)
Installation of Bennett and Brassard. Source: IBM Journal of Research and Development (Volume: 48, Issue: 1, Jan. 2004)The success of the Bennett and Brassard experiment led other research teams to work on quantum cryptography. From the air channels, they switched to fiber optic, which immediately increased the transmission range: the Swiss company GAP-Optique sold a quantum channel between Geneva and Nion based on a 23 km long fiber channel laid along the bottom of the lake and generated a secret key with the help of which did not exceed 1.4%.
In 2001, a laser LED was developed, which allowed to emit single photons. This made it possible to transmit polarized photons to a greater distance and increase the transmission speed. During the experiment, the inventors of the new LED Andrew Shields and his colleagues from TREL and Cambridge University managed to transmit the key at a speed of 75 kbit / s, although more than half of the photons were lost during transmission.
In 2003, Toshiba joined in the study of quantum cryptography. The company introduced the first system in October 2013, and in 2014 it was possible to achieve stable transmission of quantum keys over standard optical fiber for 34 days. The maximum photon transmission distance without a repeater was 100 km. Checking the operation of the installation over time was important because the level of losses and interference in the channel could change under the influence of external conditions.
Problems of quantum cryptography
The limitations of the first implementations of quantum encryption systems were a small transmission range and a very low speed :
- the length of the quantum channel in the Bennett-Brassard system was 32 cm, and the information transfer rate did not exceed 10 bit / s;
- the Swiss GAP-Optique quantum communication channel was 23 km long, but the data transfer rate was depressingly low - it was also about units of bits per second;
- shortly after GAP-Optique, Mitsubishi Electric Corporation set a new record for the quantum cryptosystem operating range by transmitting a quantum key of 87 km, albeit at a speed of one byte per second.
Restrictions on the distance are due to the fact that photons simply do not survive at large distances due to thermal noise, loss and fiber defects. A high level of interference leads to the fact that the system has to repeat the sending several times in order to correct errors and agree on the final session key. This significantly slows down the transmission speed.
To solve this problem, quantum repeaters are being developed - devices that allow you to restore quantum information without violating its integrity. One way to implement such repeaters is based on the effect of quantum entanglement. But the maximum distance at which it is possible to maintain the effect of entanglement is currently limited to 100 km. Further, the same noises come into play: the useful signal is simply lost in them. And unlike ordinary electromagnetic signals, it is impossible to amplify or filter out photons.
In 2002, an effect was discovered, which was called quantum catalysis. In an experiment conducted by a research group led by Alexander Lvovsky, it was possible to create conditions under which the entanglement of quantum states of light was restored. In fact, scientists have learned to "confuse" photons that have lost quantum confusion due to a long journey in optical fiber. This allows you to get a stable connection over long distances with a slight decrease in transmission speed.
Another problem of quantum cryptography is the need to create a direct connection between subscribers , because only this way of interaction allows you to organize a secure distribution of encryption keys. The cost of quantum systemstoday it amounts to tens and hundreds of thousands of dollars, so the developers of commercial solutions offer quantum key distribution technology in the form of a service, because most of the time the optical channels are idle.
In this case, the session key is formed of two parts: the first - the master key - is formed by the client using traditional cryptography, and the second - the quantum - is generated by the system of quantum key distribution. The final key is obtained by the XOR bitwise operation of these two parts. Thus, even if hackers can intercept or crack the client’s master key, the data will remain safe.
Quantum Cryptography Vulnerabilities
Although the quantum distribution of keys is positioned as invulnerable to cracking, specific implementations of such systems allow a successful attack and steal the generated key.
Here are some types of attacks on cryptosystems with quantum key distribution protocols. Some attacks are theoretical, others are quite successfully used in real life:
- Beam splitter attack - consists in scanning and splitting pulses into two parts and analyzing each of the parts in one of two bases.
- The Trojan Horse attack involves scanning the pulse through an optical multiplexer in the direction of the sending side or the receiving side. The pulse is divided into two parts for synchronization of detection and enters the decoding circuit, while the distortion of the transmitted photons does not occur.
- Coherent attacks that are based on relay tactics. The attacker intercepts the sender's photons, measures their state, and then sends pseudophotons in the measured states to the recipient.
- Incoherent attacks , in which the sender's photons are intercepted and confused with a group of transmitted single photons. Then the status of the group is measured and the changed data is sent to the recipient.
- The attack with blinding avalanche photo detectors , which was developed by the research team of Vadim Makarov, allows the attacker to obtain a secret key so that the recipient does not notice the fact of interception.
- Photon Separation Attack. It consists in the detection of more than one photon in a pulse, its abduction and confusion with the breakdown. The remaining unchanged part of the information is sent to the recipient, and the interceptor receives the exact value of the transmitted bit without introducing errors into the sifted key.
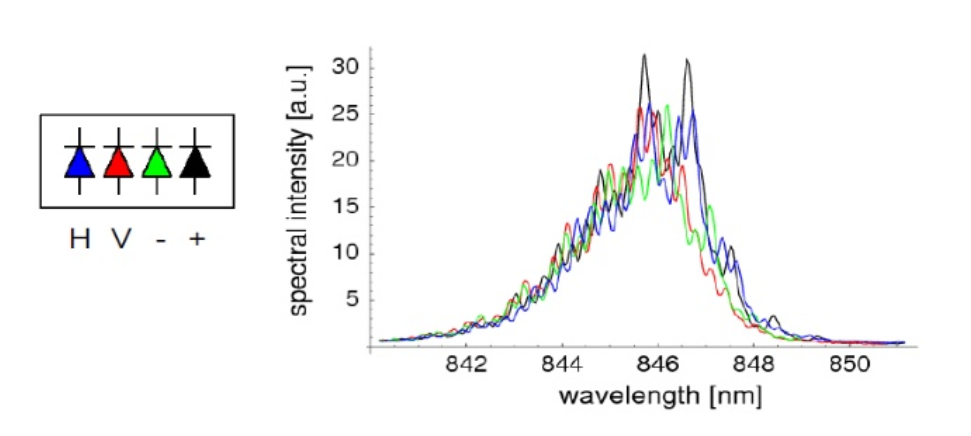
Spectral attack. A source - Spectral attack. If photons are created by four different photodiodes, they have different spectral characteristics. An attacker can measure the color of a photon, not its polarization.
- Attack on random numbers. If the sender uses a pseudo-random number generator, an attacker can use the same algorithm and get a real sequence of bits.
For example, let’s take a look at the attack on the receiver’s detector , developed by Vadim Makarov and a group of colleagues from the Norwegian University of Natural and Technical Sciences. To get the key, the detector of the receiver is blinded by a laser beam. At this time, the attacker intercepts the sender signal. The blinded quantum detector of the receiver begins to work like a regular detector, giving out "1" when exposed to a bright pulse of light, regardless of the quantum properties of the pulse. As a result, the attacker, intercepting "1", can send a light pulse to the receiver’s detector, and he will assume that he received this signal from the sender. In other words, the attacker instead of the quantum sends a classical signal to the recipient, which means that he has the ability to steal information received from the sender, unnoticed.
Makarov's group demonstrated an attack on quantum encryption systems manufactured by ID Quantique and MagiQ Technologies. To prepare a successful hack, commercial systems were used. The development of the attack took two months.
The identified vulnerability, despite its critical nature, does not relate to technology as such, but to the specific features of a particular implementation. The possibility of such an attack can be eliminated by installing a source of single photons in front of the detectors of the receiver and including it at random times. This will make sure that the detector operates in quantum mode and responds to individual photons.
How much does it cost, does it work in reality and who needs it?
When it comes to areas where real secrecy is required, little things such as cost, restrictions on distance and transmission speed are not taken into account.
The demand for quantum cryptography in the military, state and financial sectors has led to the fact that research groups receive serious funding, and the industrial plants they develop are not only sold, but also put into real use.

Quantum Key Distribution System. Source: Toshiba. The
latest examples of commercial systems of quantum cryptographic protection have a range of more than 1000 kilometers, which allows them to be used not only within one country, but also for the organization of secure communications at the interstate level.
The introduction of installations for quantum cryptography in mass production leads to cheaper prices. In addition, manufacturers are developing various solutions in order to increase the availability of quantum cryptography and reduce its cost per subscriber.
For example, the Toshiba quantum key distribution system allows you to connect only two points at a distance of up to 100 km. But at the same time, the device allows 64 subscribers to use quantum cryptography simultaneously.
Despite its limitations, quantum cryptography has an undeniable advantage over traditional cryptography, since it has proven cryptographic strength. However, as practice shows, proven stability is a property of theoretical models, concepts, but not specific implementations. The developed methods of attacks on specific systems of quantum key distribution deprive quantum cryptography of this advantage, since no one can guarantee that the next quantum crypto novelty will not be vulnerable to any attack on third-party channels.
On the other hand, quantum cryptosystems can generate a truly random private key. You can only decrypt data encrypted on this key if you guess the key. This allows you to protect information for many years by choosing a quantum key of sufficient length.
Some facts confirming the promise of quantum cryptography as a technology:
- In 2017, China launched the construction of an unbreakable communications network based on quantum cryptography. By July 2017, the network had more than 200 subscribers from military and government agencies, as well as the financial and energy sectors.
- On December 13, 2017, the Russian company InfoTex introduced the ViPNet Quantum Phone, a device that allows you to connect workstations with installed ViPNet software and encrypt traffic between them using a quantum key distribution.
- In May 2018, Russia successfully conducted the first successful testing of a system of quantum and cryptographic protection of information on a high-speed communication line, suitable for use in large data centers. Tests were conducted by specialists of the c-equipment manufacturing company S-Terra CISP and the Russian quantum center commissioned by Gazprombank.
- In September 2018, Toshiba demonstrated a working quantum cryptography system, which provided an average monthly transmission rate of quantum keys over ordinary optical fiber of 10.2 Mbit / s.
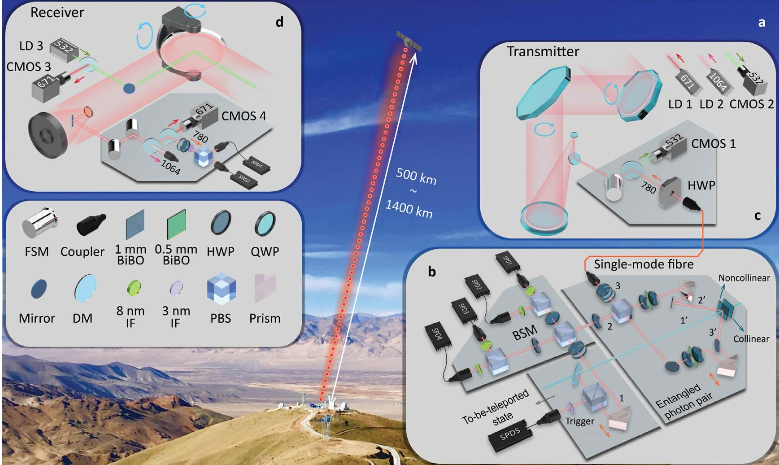
The operation scheme of the Chinese quantum cryptosystem on the Micius satellite. Source: arXiv.org
In May 2018, Toshiba announced the invention of a new quantum key distribution protocol called Twin-Field QKD (Quantum Key Distribution). The protocol allows keys to be transmitted over distances of more than 1000 km without trusted repeaters or quantum repeaters. Its verification on an experimental installation is promised in 2019. The
rapid progress that has been observed in the field of quantum cryptography leaves no doubt that in the next decade the use of this technology will become widespread and will actually turn into a standard. And cryptographers and cryptanalysts will have to prepare for the next round of battle for the protection of information.
Perhaps the next indestructible frontier will be cryptography based on lattice theory (Lattice-based Cryptography), which is invulnerable to quantum computers and can successfully work even on devices with weak processors. In any case, a variety of impenetrable protection options will benefit end users.
